Friend
Professional
- Messages
- 2,669
- Reaction score
- 943
- Points
- 113
The group is expanding its arsenal of attacks on government and technology companies.
Trend Micro spoke about the new campaign of the APT group Earth Baku, which has expanded its activities in Europe, the Middle East and Africa since the end of 2022. Hackers use public IIS servers and use sophisticated tools to exfiltrate data.
The activities of Earth Baku (APT41) first became known in 2021, but since the end of 2022, Earth Baku has significantly expanded its influence, covering Europe, the Middle East and Africa (MEA). During this time, Earth Baku has not only expanded the geography of its operations, but also updated its tools and tactics, making its attacks even more sophisticated and difficult to detect.
Previously, Earth Baku focused its efforts in the Indo-Pacific region, but now its goals are countries such as Italy, Germany, the United Arab Emirates and Qatar. The investigation also revealed traces of the group's activities in Georgia and Romania. The main targets of the attacks were government agencies, media, telecommunications companies, technology corporations, healthcare and educational institutions.
One of the key features of the new Earth Baku operations is the use of IIS servers as a starting point for penetration into victims ' systems. After gaining access, attackers deploy the Godzilla web shell to maintain control of the compromised server. In the future, the StealthVector and StealthReacher tools will be installed on the server, as well as the new modular SneakCross backdoor.
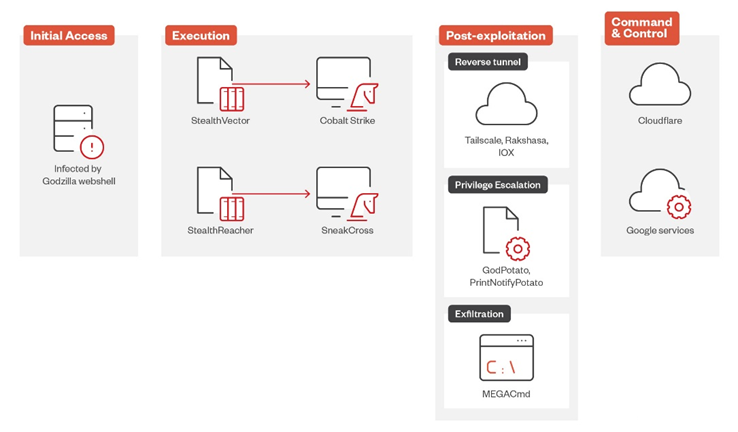
Earth Baku Attack Chain
StealthVector and StealthReacher are loaders that allow you to run malicious components of Earth Baku in stealth mode. In 2023, it was noted that the new version of StealthVector added the AES encryption algorithm (previously used by ChaCha20), as well as implemented code masking mechanisms, which complicates analysis.
StealthReacher is an improved version of StealthVector and is designed to run a SneakCross backdoor that uses Google services as C2 servers, making it much more difficult to detect and block hackers infrastructure.
Thanks to its modular structure, SneakCross can be easily modified and adapted to various attack scenarios. The tool allows cybercriminals to manipulate files, collect system information, probe the network, and even log keystrokes, giving them broad control over compromised systems.
During attacks on compromised systems, Earth Baku uses the following tools:
Hackers use MEGAcmd, a command — line tool for working with the MEGA cloud service, to exfiltrate data. This tool allows you to quickly transfer large amounts of data to remote servers.
Earth Baku's new methods and tools highlight the increasingly complex and advanced nature of the group's operations. Earth Baku is becoming an increasingly serious threat on a global scale. For protection, experts recommend implementing the principle of least privilege, regularly updating systems and applications, and developing proactive incident response strategies. Implementing a 3-2-1 rule backup will help you save data even in the event of a successful attack.
Source
Trend Micro spoke about the new campaign of the APT group Earth Baku, which has expanded its activities in Europe, the Middle East and Africa since the end of 2022. Hackers use public IIS servers and use sophisticated tools to exfiltrate data.
The activities of Earth Baku (APT41) first became known in 2021, but since the end of 2022, Earth Baku has significantly expanded its influence, covering Europe, the Middle East and Africa (MEA). During this time, Earth Baku has not only expanded the geography of its operations, but also updated its tools and tactics, making its attacks even more sophisticated and difficult to detect.
Previously, Earth Baku focused its efforts in the Indo-Pacific region, but now its goals are countries such as Italy, Germany, the United Arab Emirates and Qatar. The investigation also revealed traces of the group's activities in Georgia and Romania. The main targets of the attacks were government agencies, media, telecommunications companies, technology corporations, healthcare and educational institutions.
One of the key features of the new Earth Baku operations is the use of IIS servers as a starting point for penetration into victims ' systems. After gaining access, attackers deploy the Godzilla web shell to maintain control of the compromised server. In the future, the StealthVector and StealthReacher tools will be installed on the server, as well as the new modular SneakCross backdoor.

Earth Baku Attack Chain
StealthVector and StealthReacher are loaders that allow you to run malicious components of Earth Baku in stealth mode. In 2023, it was noted that the new version of StealthVector added the AES encryption algorithm (previously used by ChaCha20), as well as implemented code masking mechanisms, which complicates analysis.
StealthReacher is an improved version of StealthVector and is designed to run a SneakCross backdoor that uses Google services as C2 servers, making it much more difficult to detect and block hackers infrastructure.
Thanks to its modular structure, SneakCross can be easily modified and adapted to various attack scenarios. The tool allows cybercriminals to manipulate files, collect system information, probe the network, and even log keystrokes, giving them broad control over compromised systems.
During attacks on compromised systems, Earth Baku uses the following tools:
- Iox for creating reverse tunnels;
- Rakshasa for multi-level proxying and internal network penetration;
- TailScale for combining infected machines into a single virtual network.
Hackers use MEGAcmd, a command — line tool for working with the MEGA cloud service, to exfiltrate data. This tool allows you to quickly transfer large amounts of data to remote servers.
Earth Baku's new methods and tools highlight the increasingly complex and advanced nature of the group's operations. Earth Baku is becoming an increasingly serious threat on a global scale. For protection, experts recommend implementing the principle of least privilege, regularly updating systems and applications, and developing proactive incident response strategies. Implementing a 3-2-1 rule backup will help you save data even in the event of a successful attack.
Source
