Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Earth Preta is the new face of cyberterrorism in the Asia-Pacific region.
The Earth Preta hacker group has stepped up campaigns against government institutions in the Asia-Pacific region (APR). According to Trend Micro, the attackers have updated their attack methods and used new malware.
One of the key attack tools was the modification of the HYUPAN worm, which spreads through removable media. The worm injects the core malware PUBLOAD, which allows it to control infected devices and execute commands to collect data and transmit it to the attackers' servers.
In the new infection scheme, HIUPAN begins the attack by transferring malicious files to removable media. As soon as the media is connected to a new device, the worm silently infects it, hiding its files from the user. A feature of the new version of HIUPAN is a simplified configuration and easier distribution management. Malicious code is stored in the ProgramData directory, which makes it difficult to detect.

Earth Preta Infection Chain
The main task of the PUBLOAD program is to collect system information and network mapping. The malware executes commands to determine active processes, network connections, and device configuration. To perform these tasks, PUBLOAD uses both standard Windows utilities and its own data exfiltration tools.
In addition to the HIUPAN worm and the PUBLOAD program, two additional tools were used in the new attack. FDMTP is a simple malware downloader that uses encryption to bypass antivirus protection. PTSOCKET is used to transfer files to remote servers using multi-threaded mode, which speeds up the process of data leakage.
The main goal of the attackers is to collect documents of various formats, including .doc, .xls, .pdf, .ppt. Once collected, the files are archived using the RAR program and transferred via the cURL command to the Earth Preta servers. If cURL is not used, PTSOCKET is used for data transfer.
Recent attacks have also included phishing campaigns. The hackers sent victims emails with malicious links that led to the download of the DOWNBAIT loader, which delivered to the devices and executed the PlugX backdoor, providing long-term access to the victim's system.
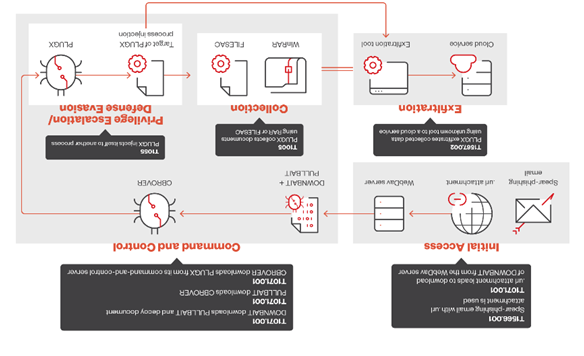
Earth Preta Spear Phishing Scheme
Based on the analysis of phishing emails and lure documents, it was established that the main targets of Earth Preta were government agencies and structures related to defense, foreign policy, and education in the Asia-Pacific countries. Among the victims were institutions from Myanmar, the Philippines, Vietnam, Singapore, Cambodia and Taiwan.
Earth Preta continues to improve its attack tools and methods, which makes their threat relevant to government and corporate structures in the Asia-Pacific region. The use of removable media to distribute malware, phishing emails for bootstraps, and new methods of data exfiltration indicate a high degree of adaptability of the group. Cybersecurity professionals must be prepared for new Earth Preta attacks and actively update protective measures.
Source
The Earth Preta hacker group has stepped up campaigns against government institutions in the Asia-Pacific region (APR). According to Trend Micro, the attackers have updated their attack methods and used new malware.
One of the key attack tools was the modification of the HYUPAN worm, which spreads through removable media. The worm injects the core malware PUBLOAD, which allows it to control infected devices and execute commands to collect data and transmit it to the attackers' servers.
In the new infection scheme, HIUPAN begins the attack by transferring malicious files to removable media. As soon as the media is connected to a new device, the worm silently infects it, hiding its files from the user. A feature of the new version of HIUPAN is a simplified configuration and easier distribution management. Malicious code is stored in the ProgramData directory, which makes it difficult to detect.

Earth Preta Infection Chain
The main task of the PUBLOAD program is to collect system information and network mapping. The malware executes commands to determine active processes, network connections, and device configuration. To perform these tasks, PUBLOAD uses both standard Windows utilities and its own data exfiltration tools.
In addition to the HIUPAN worm and the PUBLOAD program, two additional tools were used in the new attack. FDMTP is a simple malware downloader that uses encryption to bypass antivirus protection. PTSOCKET is used to transfer files to remote servers using multi-threaded mode, which speeds up the process of data leakage.
The main goal of the attackers is to collect documents of various formats, including .doc, .xls, .pdf, .ppt. Once collected, the files are archived using the RAR program and transferred via the cURL command to the Earth Preta servers. If cURL is not used, PTSOCKET is used for data transfer.
Recent attacks have also included phishing campaigns. The hackers sent victims emails with malicious links that led to the download of the DOWNBAIT loader, which delivered to the devices and executed the PlugX backdoor, providing long-term access to the victim's system.

Earth Preta Spear Phishing Scheme
Based on the analysis of phishing emails and lure documents, it was established that the main targets of Earth Preta were government agencies and structures related to defense, foreign policy, and education in the Asia-Pacific countries. Among the victims were institutions from Myanmar, the Philippines, Vietnam, Singapore, Cambodia and Taiwan.
Earth Preta continues to improve its attack tools and methods, which makes their threat relevant to government and corporate structures in the Asia-Pacific region. The use of removable media to distribute malware, phishing emails for bootstraps, and new methods of data exfiltration indicate a high degree of adaptability of the group. Cybersecurity professionals must be prepared for new Earth Preta attacks and actively update protective measures.
Source

