Friend
Professional
- Messages
- 2,675
- Reaction score
- 987
- Points
- 113
80% ransom is a tempting offer for partners of one of the most dangerous groups.
In a new report, Group-IB notes that from 2024 onwards, the impact of ransomware attacks will only increase. The growing complexity of such attacks is due to the development of the ransomware-as-a-service (RaaS) market, the spread of stolen data on specialized sites, and the increase in the number of affiliate programs.
The most notable ransomware trend was the DragonForce group, which was discovered in August 2023. At first, the hackers used the LockBit 3.0 code leak, and later, in July 2024, they developed their own malware variant based on this leak. Also in the arsenal of the group there is a modified version of Conti with advanced features. A feature of the group is the RaaS model, which allows partners to use ready-made software for attacks, receiving 80% of the ransom.
DragonForce's tactics rely on a double-extortion method: after encrypting the data, they threaten to release the stolen information to the public if the victim does not pay. Since June 2024, the group has launched an affiliate program on the underground RAMP forum, offering tools for attack management and automation, as well as the ability to create unique versions of viruses.
DragonForce actively uses the Bring Your Own Vulnerable Driver (BYOVD) method to disable security processes and avoid detection. Cybercriminals also clear Windows event logs after encrypting data, making it difficult to analyze the incident later.
Between August 2023 and August 2024, the group attacked 82 companies from various fields, among which manufacturing, real estate, and transport are in the lead. Most of the attacks were in the United States (52.4%), the UK (12.2%) and Australia (6%). Among the group's past attacks are hacking the systems of the Ohio State Lottery and the Palau government.
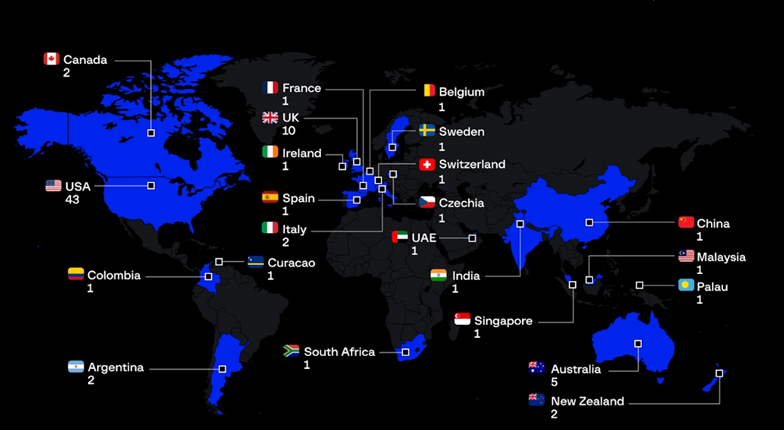
Geography of DragonForce attacks
In addition to LockBit 3.0 and Conti, DragonForce uses other tools: the SystemBC backdoor to gain a foothold, Mimikatz and Cobalt Strike to collect credentials, and Cobalt Strike to roam within the network.
Experts call DragonForce a "serious adversary" because the group targets key industries and uses advanced tools and tactics. At the moment, Group-IB does not link the DragonForce attacks to any specific country or group of individuals, but researchers have previously pointed to the possible origin of the group from Malaysia.
Source
In a new report, Group-IB notes that from 2024 onwards, the impact of ransomware attacks will only increase. The growing complexity of such attacks is due to the development of the ransomware-as-a-service (RaaS) market, the spread of stolen data on specialized sites, and the increase in the number of affiliate programs.
The most notable ransomware trend was the DragonForce group, which was discovered in August 2023. At first, the hackers used the LockBit 3.0 code leak, and later, in July 2024, they developed their own malware variant based on this leak. Also in the arsenal of the group there is a modified version of Conti with advanced features. A feature of the group is the RaaS model, which allows partners to use ready-made software for attacks, receiving 80% of the ransom.
DragonForce's tactics rely on a double-extortion method: after encrypting the data, they threaten to release the stolen information to the public if the victim does not pay. Since June 2024, the group has launched an affiliate program on the underground RAMP forum, offering tools for attack management and automation, as well as the ability to create unique versions of viruses.
DragonForce actively uses the Bring Your Own Vulnerable Driver (BYOVD) method to disable security processes and avoid detection. Cybercriminals also clear Windows event logs after encrypting data, making it difficult to analyze the incident later.
Between August 2023 and August 2024, the group attacked 82 companies from various fields, among which manufacturing, real estate, and transport are in the lead. Most of the attacks were in the United States (52.4%), the UK (12.2%) and Australia (6%). Among the group's past attacks are hacking the systems of the Ohio State Lottery and the Palau government.

Geography of DragonForce attacks
In addition to LockBit 3.0 and Conti, DragonForce uses other tools: the SystemBC backdoor to gain a foothold, Mimikatz and Cobalt Strike to collect credentials, and Cobalt Strike to roam within the network.
Experts call DragonForce a "serious adversary" because the group targets key industries and uses advanced tools and tactics. At the moment, Group-IB does not link the DragonForce attacks to any specific country or group of individuals, but researchers have previously pointed to the possible origin of the group from Malaysia.
Source
