Carding
Professional
- Messages
- 2,871
- Reaction score
- 2,391
- Points
- 113
DoS attack (Denial of Service), or denial of service, is a set of actions by intruders aimed at blocking or slowing down the operation of individual services or an entire information system. In some cases, such an attack leads to resource overuse. For example, if the cloud system is configured to automatically add virtual machines in the event of a service slowdown, then, upon detecting a decrease in response time, the cloud will automatically add new virtual machines, and the attack will not be noticeable to visitors to the resource, but the operator's fees, which are usually tied to the spent resources, may increase.
An alternative definition of DoS is an attack on the exhaustion of scarce resources. However, this situation can also arise in the case of legitimate user activity, if the information system is built incorrectly and a deficit of some resource was artificially created in it - bandwidth, memory, computing capabilities. Such an incident cannot be called an attack, since there is no targeted action by the attacker. At the same time, a DoS attack that exploits a buffer overflow vulnerability and causes the entire information system to fail does not exhaust any scarce resource, but exploits a software bug.
Classification and methods of DoS attacks
The following types of DoS attacks are distinguished:
Target of DoS attacks
The targets of attackers are the resources of companies whose business is strongly connected with the Internet: electronic stores, bank portals. Typically, attackers will extort money to stop a DoS attack - sometimes this ransom is less than the loss of business suspension and damage to reputation. In some cases, a DoS attack serves as a cover for another attack. For example, by stealing a large amount of money from bank customers, an attacker can launch a DoS attack on a remote banking system so that victims cannot check the status of their accounts until the money is withdrawn and hidden.
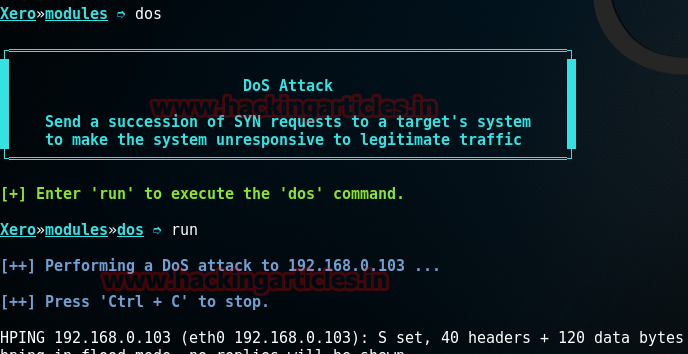
However, in recent years, cases of cyber terrorism have become more frequent, the purpose of which is to disable state information resources. In this case, the payback of the attack is difficult to assess, since the money comes from terrorist structures. As a rule, terrorists attack less protected resources, so it is enough to have minimal protection against a DoS attack - then the criminals will most likely find themselves another victim.
Source of DoS attacks
The reasons that allow attackers to conduct DoS attacks can be very different, but in any case, it all comes down to vulnerabilities in web applications and errors in network configurations. Today's web resources are complex and constantly changing systems, which leads to the appearance of gaps in them - both at the level of application code and at the network level. At a minimum, you need to have tools for installing updates for system software, code analyzers, mechanisms for auditing the configuration of network devices.
Risk analysis
To protect against DoS attacks, the user can use the following protection mechanisms:
It should be noted that DoS attacks become more powerful and sophisticated over time, so the likelihood of being hit by them increases. In this case, a DoS attack, as a rule, begins at the most crucial moment, when the company expects to get the maximum profit. This is why attackers rely on the success of their blackmail. Accordingly, if your business is connected with Internet sales, then you will most likely not be able to stay away from such risks.
An alternative definition of DoS is an attack on the exhaustion of scarce resources. However, this situation can also arise in the case of legitimate user activity, if the information system is built incorrectly and a deficit of some resource was artificially created in it - bandwidth, memory, computing capabilities. Such an incident cannot be called an attack, since there is no targeted action by the attacker. At the same time, a DoS attack that exploits a buffer overflow vulnerability and causes the entire information system to fail does not exhaust any scarce resource, but exploits a software bug.
Classification and methods of DoS attacks
The following types of DoS attacks are distinguished:
- Exploiting the vulnerability. This type of attack requires a hardware or software error, the use of which leads to the destruction of the target system or to a significant slowdown in its work. Sometimes, in such scenarios, it is sufficient to send one network packet to its destination, therefore such an attack is sometimes called a low-speed attack. To protect against it, it is necessary to install patches for system vulnerabilities or WAFs with filtering packets that exploit the vulnerability. It also helps to audit the information system or check it for resistance to stress (stress test).
- Complex queries.This type of attack is directed against web systems built in interpreted languages such as PHP or Python. The fact is that modern application servers are well optimized for mass execution of simple queries, some of which are cached and do not require code execution. However, highly personalized queries, the answers to which do not get into the cache, can create a large load on the system. In the normal mode, there are not very many such requests, and therefore the system copes with them, however, attackers can provoke a large number of them, which will lead to the exhaustion of processor time. Such an attack also does not need a large number of requests, however, it requires special preliminary training and qualification of the attackers, therefore it is very rare.To prevent attacks using complex queries, it is worth conducting an audit of the application code and its architecture, as well as stress tests. Some CMSs have built-in application profiling mechanisms to help identify these bottlenecks; they should also be used at least during test operation.
- Capturing resources. Attacks are quite possible when an attacker in one way or another gains control over a company's resources, for example, its cloud services, and then blackmails by destroying the information accumulated in them. Such attacks can also be classified as DoS, since the result of the implemented threat is the decommissioning of the system. As a rule, the ability to seize resources appears with a weak authentication system, so for administrative accounts (especially in public services), it is worth using strong authentication methods and recording administrative commands with blocking the most dangerous of them.
Target of DoS attacks
The targets of attackers are the resources of companies whose business is strongly connected with the Internet: electronic stores, bank portals. Typically, attackers will extort money to stop a DoS attack - sometimes this ransom is less than the loss of business suspension and damage to reputation. In some cases, a DoS attack serves as a cover for another attack. For example, by stealing a large amount of money from bank customers, an attacker can launch a DoS attack on a remote banking system so that victims cannot check the status of their accounts until the money is withdrawn and hidden.

However, in recent years, cases of cyber terrorism have become more frequent, the purpose of which is to disable state information resources. In this case, the payback of the attack is difficult to assess, since the money comes from terrorist structures. As a rule, terrorists attack less protected resources, so it is enough to have minimal protection against a DoS attack - then the criminals will most likely find themselves another victim.
Source of DoS attacks
The reasons that allow attackers to conduct DoS attacks can be very different, but in any case, it all comes down to vulnerabilities in web applications and errors in network configurations. Today's web resources are complex and constantly changing systems, which leads to the appearance of gaps in them - both at the level of application code and at the network level. At a minimum, you need to have tools for installing updates for system software, code analyzers, mechanisms for auditing the configuration of network devices.
Risk analysis
To protect against DoS attacks, the user can use the following protection mechanisms:
- Code analysis. If a web application is developed independently or to order, then errors may appear in it. To find them, services and programs for analyzing application code are offered. It is recommended that before submitting a written system to the public, check it on such an analyzer and correct the most dangerous errors.
- Updating applications. If the application is third-party, then it is worth using the update installation system. For the operating system, DBMS and application server, updates should always be installed, albeit after checking in a small pilot configuration.
- WAF (Web Application Firewall). Sometimes a DoS attack can be handled by an application layer screen (WAF), which will block exploitation attempts and rogue protocols. It can also block privileged users' attempts to destroy valuable data.
It should be noted that DoS attacks become more powerful and sophisticated over time, so the likelihood of being hit by them increases. In this case, a DoS attack, as a rule, begins at the most crucial moment, when the company expects to get the maximum profit. This is why attackers rely on the success of their blackmail. Accordingly, if your business is connected with Internet sales, then you will most likely not be able to stay away from such risks.
