Teacher
Professional
- Messages
- 2,670
- Reaction score
- 783
- Points
- 113
How many users were affected by Discord's supply chain compromise?
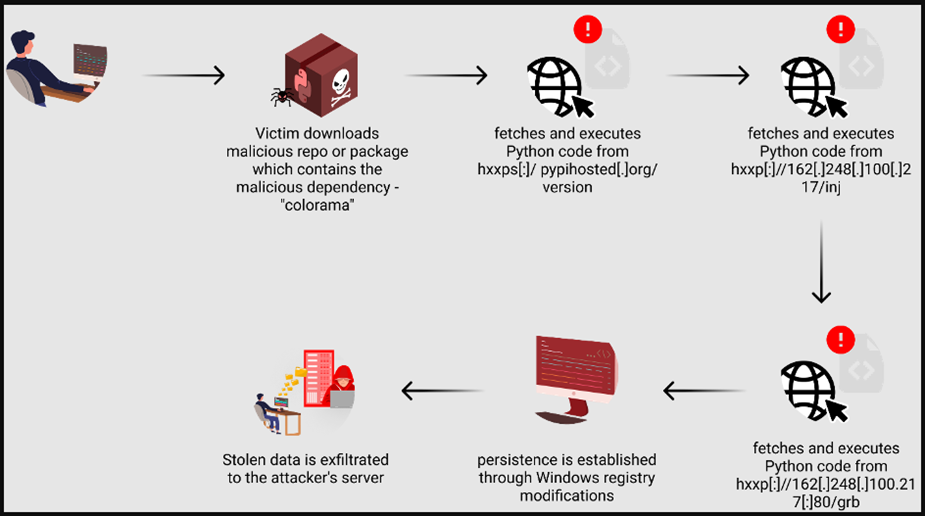
Popular service Top.gg, which helps users find servers and bots for Discord, was hit by a supply chain attack. Attackers injected malicious code into Python packages used by bot developers. The purpose of the attack, apparently, was to steal confidential data. The attack was described by Checkmarx specialists in a technical report.
The attack went in several directions:
The malicious code had extensive data theft capabilities:
The stolen data was sent to the attackers server in several ways:
Via HTTP requests with unique identifiers (hardware ID, IP address);
Through anonymous file sharing sites (GoFile, Anonfiles).
Attack Chain
The exact number of affected users is unknown. However, this attack once again highlights the importance of checking the security of the components used in software development.
Popular service Top.gg, which helps users find servers and bots for Discord, was hit by a supply chain attack. Attackers injected malicious code into Python packages used by bot developers. The purpose of the attack, apparently, was to steal confidential data. The attack was described by Checkmarx specialists in a technical report.
The attack went in several directions:
- Malicious packages uploaded to PyPI: Starting in November 2022, attackers began placing malicious packages disguised as popular tools with attractive descriptions on the PyPI platform.
- Fake mirror of Python packages: In early 2024, attackers created a fake Python package mirror that mimics a real PyPI package file store. The fake mirror hosted infected versions of legitimate packages, such as the popular "colorama".
- Hacking the administrator's account Top.gg: In March 2024, hackers managed to hack the platform administrator's account Top.gg, which has broad access rights to repositories on GitHub. Cybercriminals used their account to add malicious commits to the Top platform's python sdk repository.gg, namely added dependencies on the poisoned version of "colorama" and other malicious repositories to increase their visibility.
The malicious code had extensive data theft capabilities:
- Browser data: usernames, passwords, session history, autofill data, cookies, and credit card data from Opera, Chrome, Brave, Vivaldi, Yandex, and Edge browsers.
- Discord Tokens: Malware could gain unauthorized access to Discord accounts by stealing tokens from the corresponding folders.
- Cryptocurrency wallets: the program scanned the system for the presence of crypto wallet files and sent them to the attackers ' server.
- Telegram Data: Malware attempted to steal Telegram session data for unauthorized access to accounts and correspondence.
- User files: Malware may have stolen files from the desktop, downloads, documents, and recently opened files based on certain keywords.
- Instagram Data: The program used stolen Instagram session tokens to get account information via the Instagram API.
- Keystrokes: The malware recorded user keystrokes, potentially revealing passwords and other sensitive information.
The stolen data was sent to the attackers server in several ways:
Via HTTP requests with unique identifiers (hardware ID, IP address);
Through anonymous file sharing sites (GoFile, Anonfiles).

Attack Chain
The exact number of affected users is unknown. However, this attack once again highlights the importance of checking the security of the components used in software development.
