Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
What does the band have in common with the legendary BlackMatter?
Cybersecurity company Trend Micro has discovered that in 2023, the Kasseika ransomware group joined an increasing number of cybercrime groups using the BYOVD (Bring Your Own Vulnerable Driver) tactic, which allows attackers to disable the processes of antivirus programs to spread malware.
Kasseika is abusing the Martini driver (Martini.sys/viragt64.sys), which is part of TG Soft's VirtIT anti-virus agent system, to disable anti-virus products that protect the target system.
Analysis of the attack showed that Kasseika has similar indicators to the BlackMatter ransomware, including adding pseudo-random strings to file names and formatting a ransom note in the form of README.txt. It was discovered that the attack used most of the BlackMatter source code. This indicates a possible link between the Kasseika group and a larger and more experienced organization with access to the rare BlackMatter source code.
BlackMatter, in turn, originated from DarkSide and was used as the basis for ALPHV (BlackCat). Since BlackMatter's demise in 2021, other ransomware groups have started using similar techniques and tools, while a narrower circle of operators has access to the old code and uses it in new versions of ransomware.
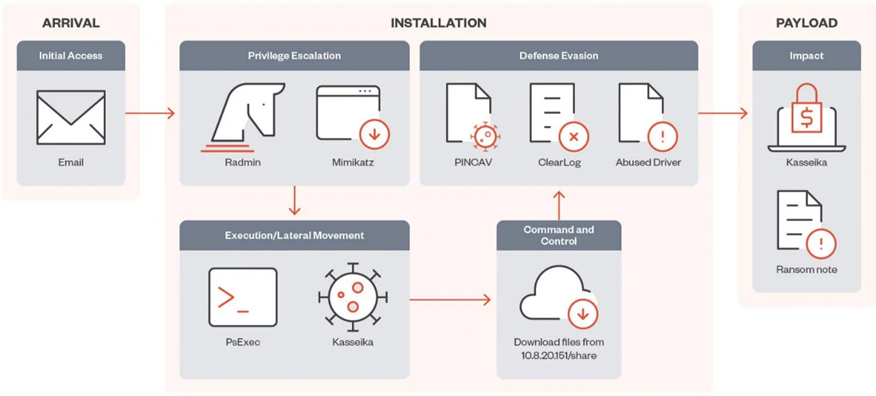
Kasseika Attack Chain
In the case under investigation, Kasseika used targeted phishing to initially access and collect the credentials of one of the target company's employees. The group then used remote administration tools to gain privileged access and navigate the target's network.
Kasseika used the legitimate Windows tool PsExec to execute its malicious files and launch malicious ones remotely .bat files. The batch file checks for a process named "Martini.exe" and completes it to avoid interference. It then downloads the affected driver to the machine Martini.sys. The presence of a driver is crucial in the attack chain-if Martini.sys missing, the malware stops working.
Using the BYOVD attack, that is, using the flaws of the downloaded driver, malware gets the right to terminate 991 processes from a hard-coded list, many of which correspond to antivirus products, security tools, analysis tools, and system utilities.
Eventually Kasseika launches Martini.exe to complete the processes of antivirus programs, and then runs the main binary file of the ransomware program (smartscreen_protected.exe). After that, the " clear.bat " to remove traces of an attack.
Finally, Kasseika uses sophisticated obfuscation and anti-debugging techniques, packaging its code with the Themida security module, and making changes to the Windows registry before encrypting files. It was also found that Kasseika clears system event logs after encryption with the command "wevutil.exe" to erase traces of their activities and complicate the analysis.
In the attacks seen by Trend Micro, victims were given 72 hours to deposit 50 bitcoins (about $2 million), and another $500 thousand was added every 24 hours of delay in resolving the problem. Victims are expected to post a screenshot of the payment confirmation in a closed Telegram group in order to get a decryptor, with the maximum time limit for this will be 120 hours (5 days).
Experts strongly recommend that organizations take a multi-level approach to protecting their systems, regularly update antivirus programs, back up important data, and train employees on Internet security.
Cybersecurity company Trend Micro has discovered that in 2023, the Kasseika ransomware group joined an increasing number of cybercrime groups using the BYOVD (Bring Your Own Vulnerable Driver) tactic, which allows attackers to disable the processes of antivirus programs to spread malware.
Kasseika is abusing the Martini driver (Martini.sys/viragt64.sys), which is part of TG Soft's VirtIT anti-virus agent system, to disable anti-virus products that protect the target system.
Analysis of the attack showed that Kasseika has similar indicators to the BlackMatter ransomware, including adding pseudo-random strings to file names and formatting a ransom note in the form of README.txt. It was discovered that the attack used most of the BlackMatter source code. This indicates a possible link between the Kasseika group and a larger and more experienced organization with access to the rare BlackMatter source code.
BlackMatter, in turn, originated from DarkSide and was used as the basis for ALPHV (BlackCat). Since BlackMatter's demise in 2021, other ransomware groups have started using similar techniques and tools, while a narrower circle of operators has access to the old code and uses it in new versions of ransomware.

Kasseika Attack Chain
In the case under investigation, Kasseika used targeted phishing to initially access and collect the credentials of one of the target company's employees. The group then used remote administration tools to gain privileged access and navigate the target's network.
Kasseika used the legitimate Windows tool PsExec to execute its malicious files and launch malicious ones remotely .bat files. The batch file checks for a process named "Martini.exe" and completes it to avoid interference. It then downloads the affected driver to the machine Martini.sys. The presence of a driver is crucial in the attack chain-if Martini.sys missing, the malware stops working.
Using the BYOVD attack, that is, using the flaws of the downloaded driver, malware gets the right to terminate 991 processes from a hard-coded list, many of which correspond to antivirus products, security tools, analysis tools, and system utilities.
Eventually Kasseika launches Martini.exe to complete the processes of antivirus programs, and then runs the main binary file of the ransomware program (smartscreen_protected.exe). After that, the " clear.bat " to remove traces of an attack.
Finally, Kasseika uses sophisticated obfuscation and anti-debugging techniques, packaging its code with the Themida security module, and making changes to the Windows registry before encrypting files. It was also found that Kasseika clears system event logs after encryption with the command "wevutil.exe" to erase traces of their activities and complicate the analysis.
In the attacks seen by Trend Micro, victims were given 72 hours to deposit 50 bitcoins (about $2 million), and another $500 thousand was added every 24 hours of delay in resolving the problem. Victims are expected to post a screenshot of the payment confirmation in a closed Telegram group in order to get a decryptor, with the maximum time limit for this will be 120 hours (5 days).
Experts strongly recommend that organizations take a multi-level approach to protecting their systems, regularly update antivirus programs, back up important data, and train employees on Internet security.

