Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,322
- Points
- 113
QakBot's successor now attacks users through Samba servers.
Specialists of Palo Alto Networks Unit 42 discovered the DarkGate campaign, which uses Samba file resources to distribute the Trojan. Activity was observed in March and April 2024, when DarkGate used public Samba servers hosting VBS and JavaScript files. The attacks targeted users in North America, Europe, and Asia.
The DarkGate malware, which first appeared in 2018, operates on the MaaS model for a limited number of clients. DarkGate has features for remote management of infected hosts, code execution, cryptocurrency mining, Reverse Shell launch, and delivery of additional payloads. In recent months, attacks using DarkGate have increased significantly after an international operation in which law enforcement agencies eliminated the QakBot infrastructure in August 2023.
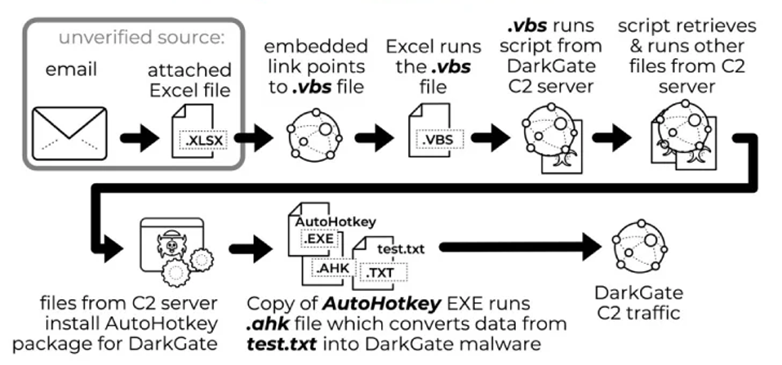
DarkGate Infection Chain
The detected DarkGate campaign starts by sending Microsoft Excel (.xlsx) files via email, which, when opened, prompt the user to click the "Open" button. After clicking the button, the VBS code hosted on Samba is executed. The VBS code loads a PowerShell script from the C2 server, which eventually loads the DarkGate package based on AutoHotkey. Alternative scripts use JavaScript instead of VBS to load and execute a subsequent PowerShell script.
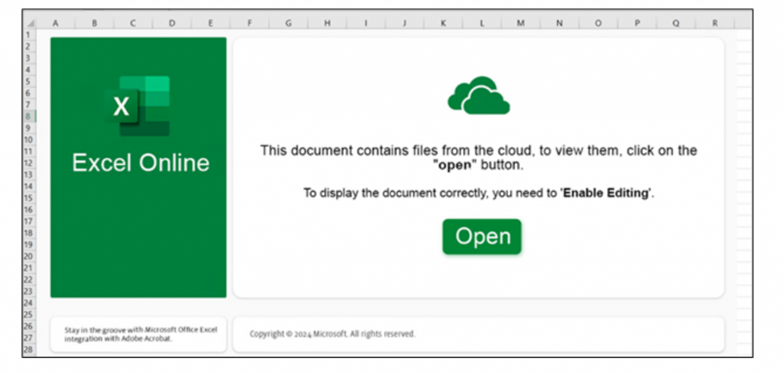
The Excel document prompts the victim to click the "Open" button to execute the script
One of DarkGate's antianalysis methods is to identify the target system's CPU. The Trojan checks whether it is running in a virtual environment or on a physical host. Checking allows you to stop working to avoid analysis in a controlled environment. Malware also examines running processes on the host to detect reverse engineering tools, debuggers, or virtualization programs.
In addition to checking CPU information, DarkGate also scans the system for a variety of other anti-malware programs. By detecting installed security software, DarkGate can avoid triggering detection mechanisms or even disable them to avoid further analysis.
Command and control (C2) traffic uses unencrypted HTTP requests, but the data is obfuscated and presented as Base64-encoded text. Experts stressed that DarkGate continues to evolve and improve methods of penetration and resistance to analysis, remaining a loud reminder of the need for reliable and proactive cybersecurity protection.
Source
Specialists of Palo Alto Networks Unit 42 discovered the DarkGate campaign, which uses Samba file resources to distribute the Trojan. Activity was observed in March and April 2024, when DarkGate used public Samba servers hosting VBS and JavaScript files. The attacks targeted users in North America, Europe, and Asia.
The DarkGate malware, which first appeared in 2018, operates on the MaaS model for a limited number of clients. DarkGate has features for remote management of infected hosts, code execution, cryptocurrency mining, Reverse Shell launch, and delivery of additional payloads. In recent months, attacks using DarkGate have increased significantly after an international operation in which law enforcement agencies eliminated the QakBot infrastructure in August 2023.

DarkGate Infection Chain
The detected DarkGate campaign starts by sending Microsoft Excel (.xlsx) files via email, which, when opened, prompt the user to click the "Open" button. After clicking the button, the VBS code hosted on Samba is executed. The VBS code loads a PowerShell script from the C2 server, which eventually loads the DarkGate package based on AutoHotkey. Alternative scripts use JavaScript instead of VBS to load and execute a subsequent PowerShell script.

The Excel document prompts the victim to click the "Open" button to execute the script
One of DarkGate's antianalysis methods is to identify the target system's CPU. The Trojan checks whether it is running in a virtual environment or on a physical host. Checking allows you to stop working to avoid analysis in a controlled environment. Malware also examines running processes on the host to detect reverse engineering tools, debuggers, or virtualization programs.
In addition to checking CPU information, DarkGate also scans the system for a variety of other anti-malware programs. By detecting installed security software, DarkGate can avoid triggering detection mechanisms or even disable them to avoid further analysis.
Command and control (C2) traffic uses unencrypted HTTP requests, but the data is obfuscated and presented as Base64-encoded text. Experts stressed that DarkGate continues to evolve and improve methods of penetration and resistance to analysis, remaining a loud reminder of the need for reliable and proactive cybersecurity protection.
Source

