Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,245
- Points
- 113
How adware gets the highest privileges in Windows.
ESET has shed light on a module of the HotPage adware, which disguises itself as an ad blocker and allows attackers to execute arbitrary code with elevated privileges on Windows computers.
File HotPage.exe appeared on VirusTotal at the end of last year. Despite the fact that the file was signed by Microsoft and developed by a seemingly real company, antivirus products label it as adware. But the situation is even worse — instead of removing ads, HotPage introduces even more ads, intercepting web traffic and redirecting content in the victim's browsers.
During the display of advertising banners, HotPage collects system information for transmission to a remote server connected to the Chinese company Hubei Dunwang Network Technology Co., Ltd.
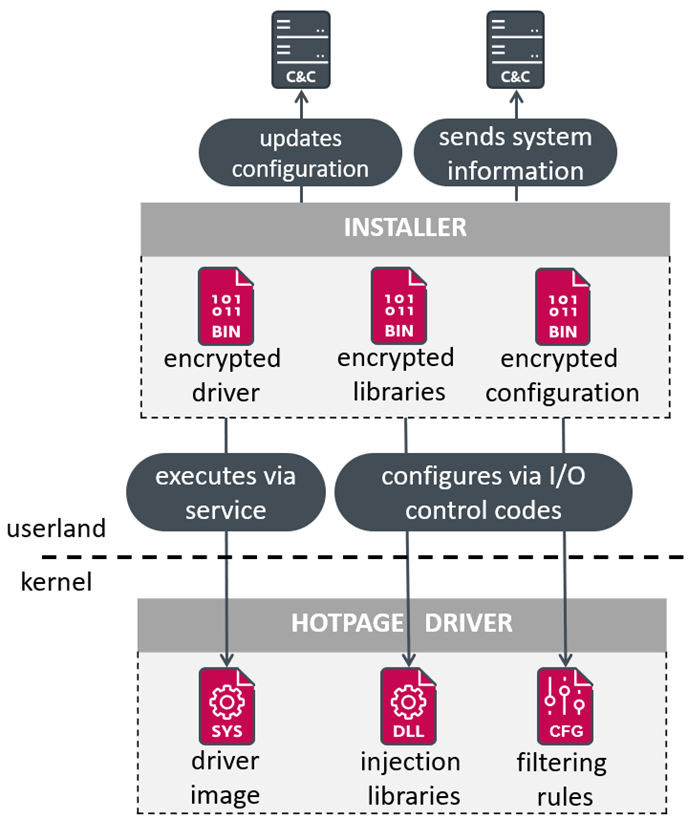
HotPage Installer Workflow
HotPage also installs a driver that can inject code into remote processes, which allows an attacker to execute malicious code with the highest privileges.
It is noteworthy that the built-in driver is signed by Microsoft. The Chinese company managed to pass the Microsoft requirements for obtaining an Extended Verification certificate (EV), which allowed the driver to avoid suspicion and bypass the Windows security mechanisms. However, as of May 1, 2024, the driver was removed from the Windows Server directory.
One of the most dangerous features of HotPage is the lack of Access Control Lists (ACLs) for the driver. In other words, a cybercriminal with normal user rights can get elevated privileges and execute code on behalf of the NT AUTHORITY\System system account.
The exact method of distribution of HotPage is still unknown, but experts found that HotPage was advertised as a solution for Internet cafes, allegedly designed to improve the user experience on the Internet by blocking ads.
Source
ESET has shed light on a module of the HotPage adware, which disguises itself as an ad blocker and allows attackers to execute arbitrary code with elevated privileges on Windows computers.
File HotPage.exe appeared on VirusTotal at the end of last year. Despite the fact that the file was signed by Microsoft and developed by a seemingly real company, antivirus products label it as adware. But the situation is even worse — instead of removing ads, HotPage introduces even more ads, intercepting web traffic and redirecting content in the victim's browsers.
During the display of advertising banners, HotPage collects system information for transmission to a remote server connected to the Chinese company Hubei Dunwang Network Technology Co., Ltd.

HotPage Installer Workflow
HotPage also installs a driver that can inject code into remote processes, which allows an attacker to execute malicious code with the highest privileges.
It is noteworthy that the built-in driver is signed by Microsoft. The Chinese company managed to pass the Microsoft requirements for obtaining an Extended Verification certificate (EV), which allowed the driver to avoid suspicion and bypass the Windows security mechanisms. However, as of May 1, 2024, the driver was removed from the Windows Server directory.
One of the most dangerous features of HotPage is the lack of Access Control Lists (ACLs) for the driver. In other words, a cybercriminal with normal user rights can get elevated privileges and execute code on behalf of the NT AUTHORITY\System system account.
The exact method of distribution of HotPage is still unknown, but experts found that HotPage was advertised as a solution for Internet cafes, allegedly designed to improve the user experience on the Internet by blocking ads.
Source
