Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
Victim screening and anti-scanner filtering play an important role in spreading the virus.
Malwarebytes announces a new scam campaign that uses the Google Ads platform to distribute the BatLoader malware. The attackers, allegedly based in Mexico, create fake advertisements for Cisco's Webex video conferencing program, which is widely used by corporations and organizations around the world.
How the attack works
The fraudulent ad mimics the official Webex download portal and takes the highest position in the Google search results for the query "webex". The ad looks completely legitimate: it uses the real Webex logo and displays a legitimate URL "webex.com" as a destination when clicked.
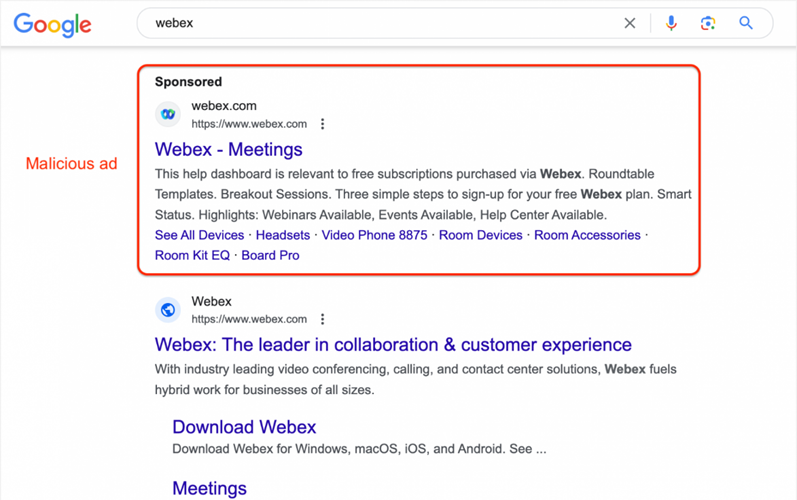
Fake ads in search results
Attackers exploit a loophole in the Google Ads tracking system that allows them to redirect users to other sites without violating Google's policies. Cybercriminals use the URL on the Firebase platform ("trixwe. page. link") as a tracking template, with the final URL " https://www.webex.com".
When an ad is clicked, the user is redirected to "trixwe. page [.] link", which filters visits coming from researchers and automated crawlers. If the user is the target victim, they are redirected to the site "monoo3at [.] com", where additional checks are performed. As a result, targeted victims are redirected to the site "webexadvertisingoffer [.] com", where their computers are infected with malware.
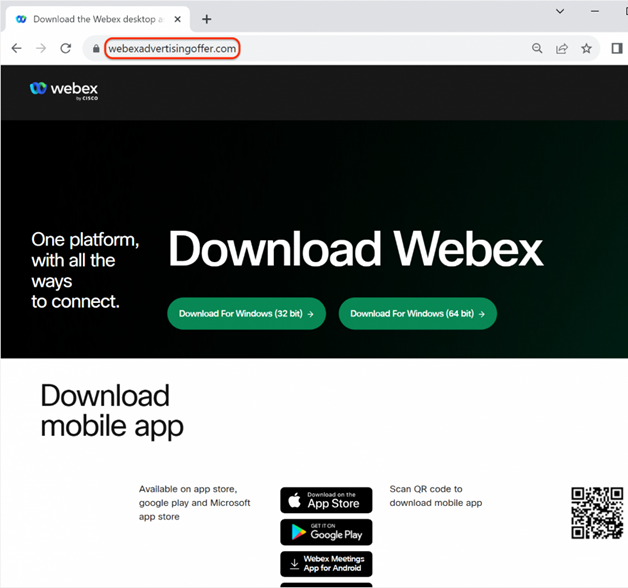
Malicious site
Consequences of the attack
Visitors to the fake Webex site who click on the download buttons download an MSI installer that runs several processes and executes PowerShell commands to install the BatLoader malware. The virus eventually downloads and decrypts the DanaBot add-on module — a modular banking Trojan that can steal passwords, take screenshots, load ransomware modules, and provide direct access to compromised hosts.
Safety recommendations
The best practice when searching for software is to ignore the promoted results in Google and download programs only from official developer sites or well-known and reliable sources.
Recall that recently, cybersecurity experts Malwarebytes discovered a new phishing campaign aimed at American citizens, during which attackers placed a fake page of the US Postal Service (USPS) in the top of Google search results. The purpose of the attack was to obtain the victims ' credentials to log in to online banking services, as well as complete personal and financial information.
Malwarebytes announces a new scam campaign that uses the Google Ads platform to distribute the BatLoader malware. The attackers, allegedly based in Mexico, create fake advertisements for Cisco's Webex video conferencing program, which is widely used by corporations and organizations around the world.
How the attack works
The fraudulent ad mimics the official Webex download portal and takes the highest position in the Google search results for the query "webex". The ad looks completely legitimate: it uses the real Webex logo and displays a legitimate URL "webex.com" as a destination when clicked.

Fake ads in search results
Attackers exploit a loophole in the Google Ads tracking system that allows them to redirect users to other sites without violating Google's policies. Cybercriminals use the URL on the Firebase platform ("trixwe. page. link") as a tracking template, with the final URL " https://www.webex.com".
When an ad is clicked, the user is redirected to "trixwe. page [.] link", which filters visits coming from researchers and automated crawlers. If the user is the target victim, they are redirected to the site "monoo3at [.] com", where additional checks are performed. As a result, targeted victims are redirected to the site "webexadvertisingoffer [.] com", where their computers are infected with malware.

Malicious site
Consequences of the attack
Visitors to the fake Webex site who click on the download buttons download an MSI installer that runs several processes and executes PowerShell commands to install the BatLoader malware. The virus eventually downloads and decrypts the DanaBot add-on module — a modular banking Trojan that can steal passwords, take screenshots, load ransomware modules, and provide direct access to compromised hosts.
Safety recommendations
The best practice when searching for software is to ignore the promoted results in Google and download programs only from official developer sites or well-known and reliable sources.
Recall that recently, cybersecurity experts Malwarebytes discovered a new phishing campaign aimed at American citizens, during which attackers placed a fake page of the US Postal Service (USPS) in the top of Google search results. The purpose of the attack was to obtain the victims ' credentials to log in to online banking services, as well as complete personal and financial information.

