Lord777
Professional
- Messages
- 2,578
- Reaction score
- 1,520
- Points
- 113
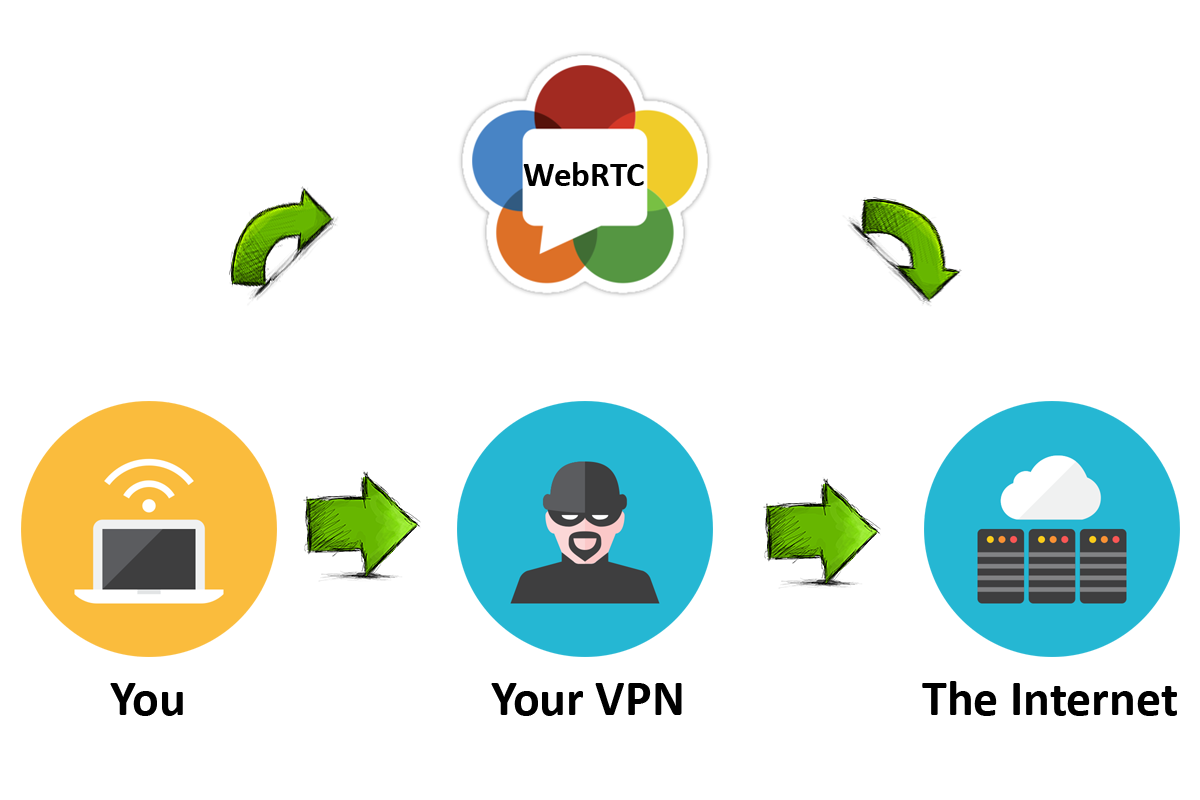
Today I want to touch on a now-dead topic, namely WebRTC. I won't tell you how to block it. There are many different plugins and ways to disable it manually.
This article is dedicated to people who need WebRTC while "working" or do not want to make sites angry with the plugin turned off. This article will focus on WebRTC deception.
Well that. Start.
To do this, we need to have:
A virtual machine running on Windows XP, 7, 8, 8.1.
The VPN (if any) must be on the main machine(only tunnels or socks on the virtual machine).
And a configured firewall.
The setup is divided into several parts.
PART ONE: INSTALLING AND CONFIGURING THE FIREWALL[UPD]
PART TWO: CONFIGURING THE LOOPBACK ADAPTER
SETUP FOR WINDOWS XP
A small update. Who has a Windows XP loopback adapter can be installed like this:
In Russian
In English
Spoiler alert
To find out the Default gateway, enter "ipconfig"in the command line. If the line is empty, look for the gateway address in the virtual machine network settings.
In my case, I enter in the command line
OPERATION ALGORITHM
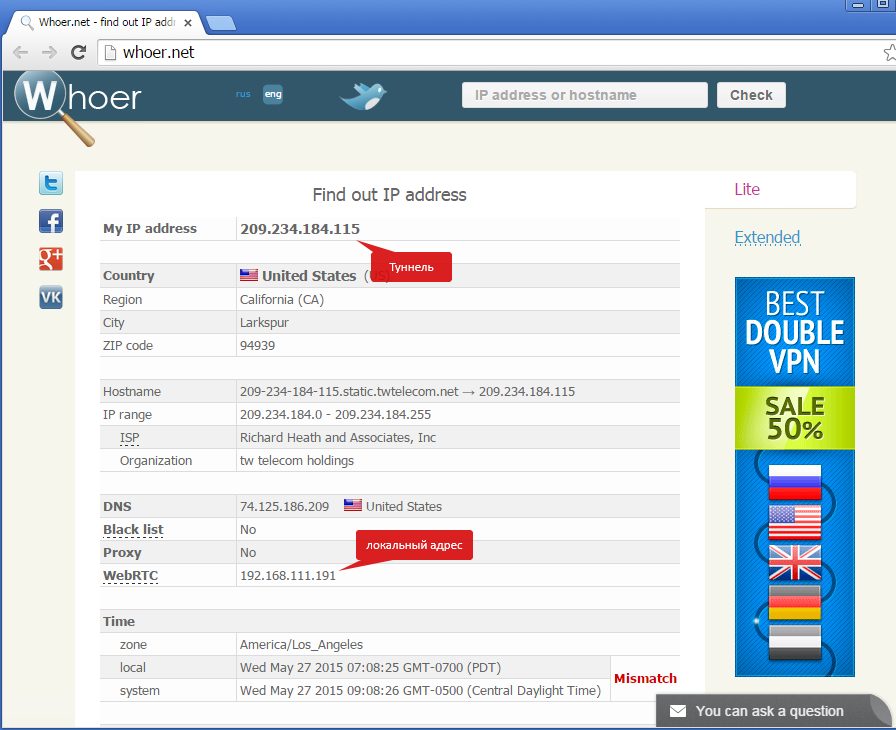
Specify the IP shown in Whoer in the adapter
Specify the IP shown in Whoer in the adapter
The result is the same:
Ready!
You can disable WebRTC in Chrome by using the "WebRTC Leak Prevent" app, which is available in the Chrome Web Store. To cheat, it is enough to raise the second NAT.
This article is dedicated to people who need WebRTC while "working" or do not want to make sites angry with the plugin turned off. This article will focus on WebRTC deception.

Well that. Start.
To do this, we need to have:
A virtual machine running on Windows XP, 7, 8, 8.1.
The VPN (if any) must be on the main machine(only tunnels or socks on the virtual machine).
And a configured firewall.
The setup is divided into several parts.
PART ONE: INSTALLING AND CONFIGURING THE FIREWALL[UPD]
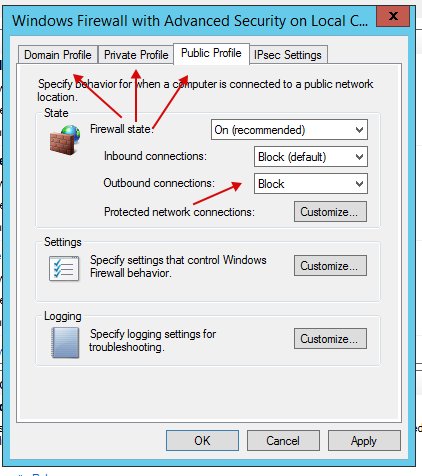
- Go to the control panel.

- Click on "Advanced settings".

- Next, click on "Windows Firewall Properties".

- Next, in all three tabs, specify in "Outbound connections: Block".

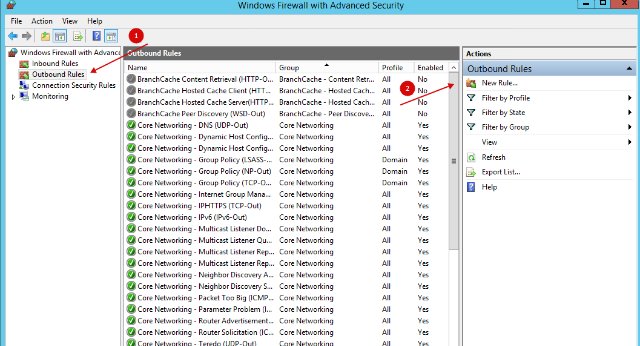
- Next, go to Outbound Rules and click on New Rule.

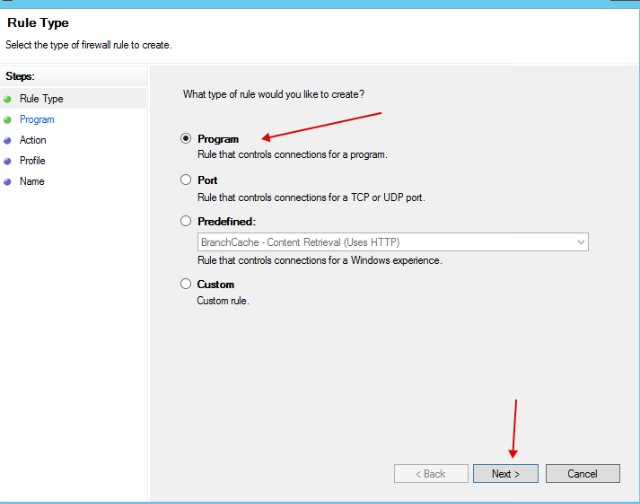
- Select "Program".

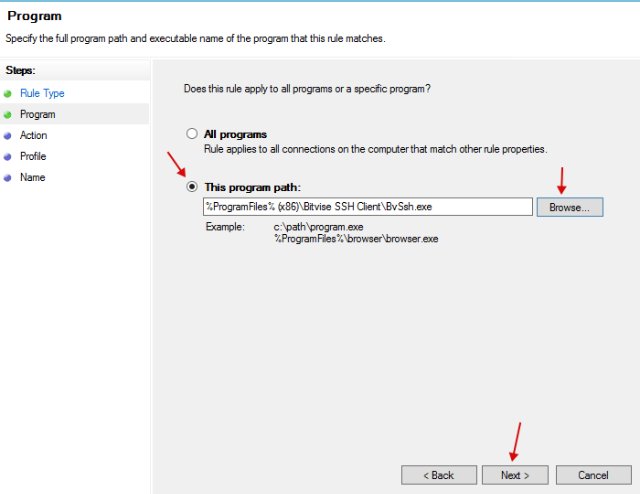
- We specify the application that should go online(Bitvise, proxyfier).

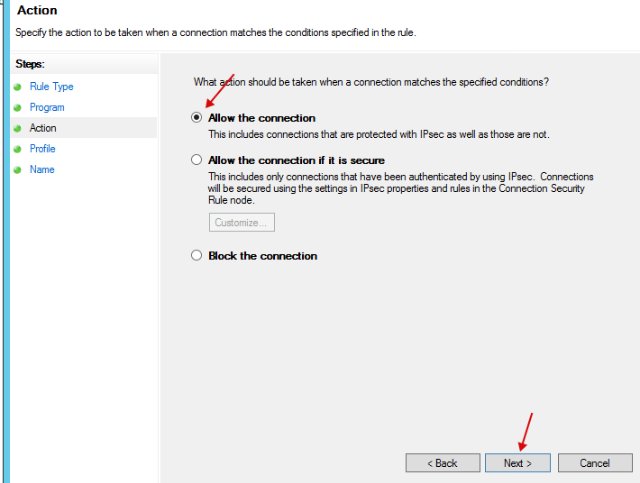
- Specify "Allow the connection".

- Next, set the network name and close the setting.
In our case, we are trying to connect to the Internet using "Bitvise" and tunnels.
If everything is done correctly, then WebRTC will only show us the internal network IP without an external one.

- If this is the case, then everything is fine. Now we need WebRTC to show us the IP address we need.
PART TWO: CONFIGURING THE LOOPBACK ADAPTER
SETUP FOR WINDOWS XP
A small update. Who has a Windows XP loopback adapter can be installed like this:
In Russian
In English
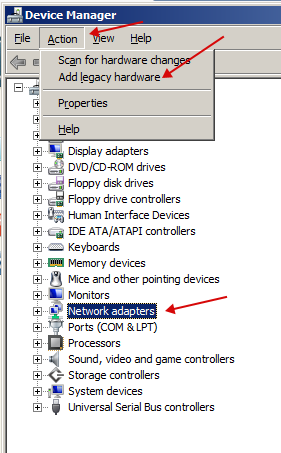
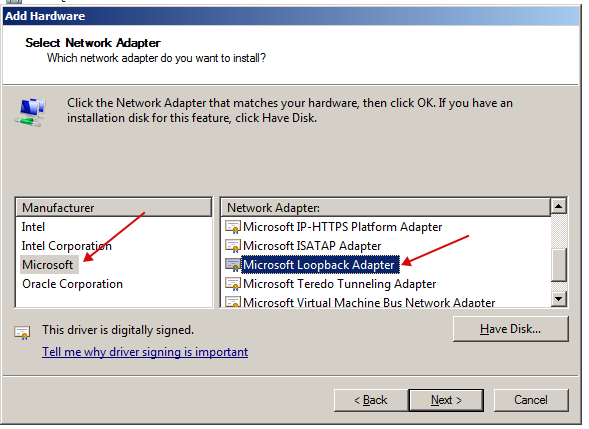
- Now we need to create a loopback adapter to fool WebRTC.To do this, go to the hardware manager and select "Add legacy hardware" in the "Action" menu by first clicking on the "Network adapters" section.

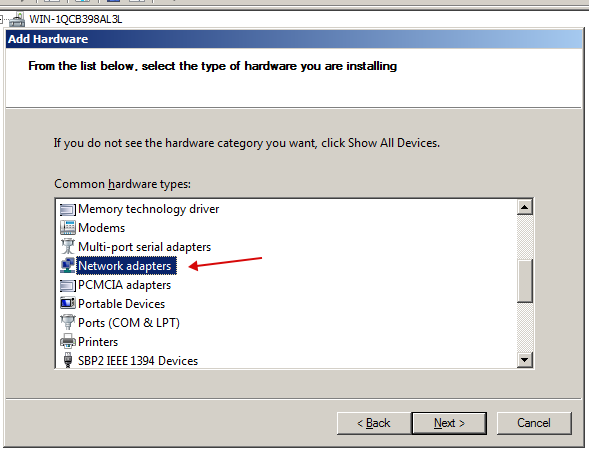
- Choose manual installation.
- Select "Network adapters".

- Select "Microsoft" and select "Microsoft Loopback Adapter".

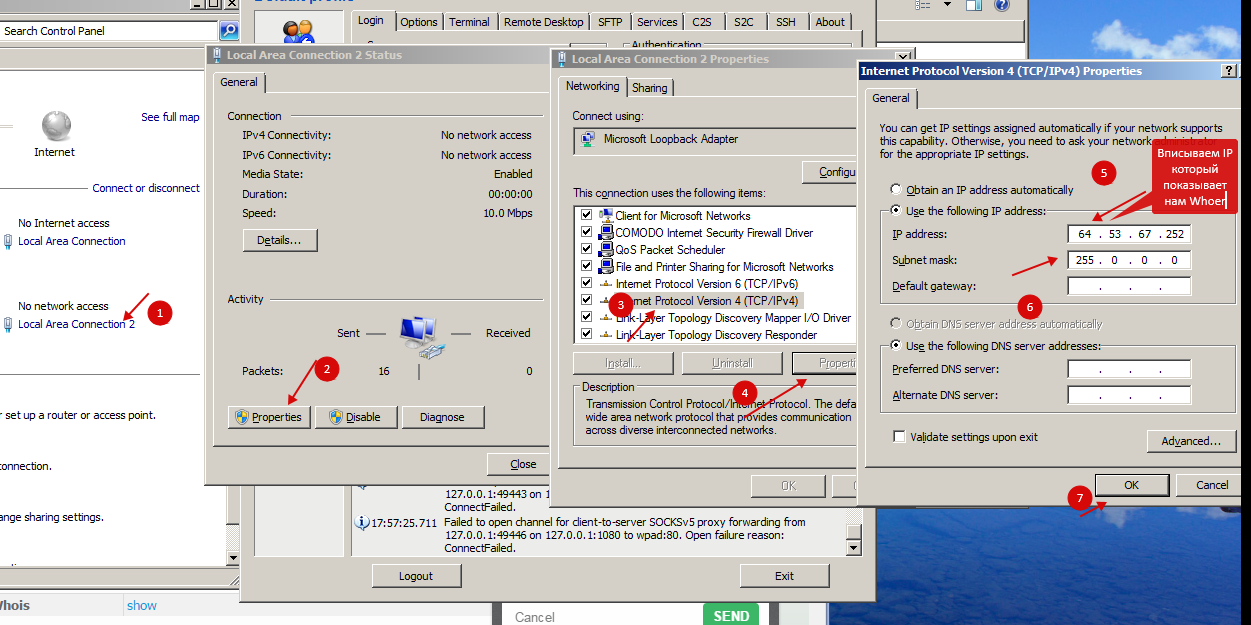
- After installation, go to the settings of this adapter. And specify in its properties the IP that showed us Whoer.
Spoiler alert
- Then save and run the command line.
In the command line, write the following:
Code:
routeadd ( )mask255.255.255.255 (defaultgateway) metric 1To find out the Default gateway, enter "ipconfig"in the command line. If the line is empty, look for the gateway address in the virtual machine network settings.
In my case, I enter in the command line
Code:
route add 64.53.67.252 mask 255.255.255.255 192.168.111.2 metric 1- If everything is OK, then the command line will respond =)
If you get an error with the text "The requested operation requires elevation", then run the command line as an administrator.
OPERATION ALGORITHM
- Delete the old rule with the command
Code:
routedelete ( )mask255.255.255.255 (defaultgateway) metric 1- You set a new rule with the command
Code:
routeadd ( )mask255.255.255.255 (defaultgateway) metric 1Specify the IP shown in Whoer in the adapter
Specify the IP shown in Whoer in the adapter

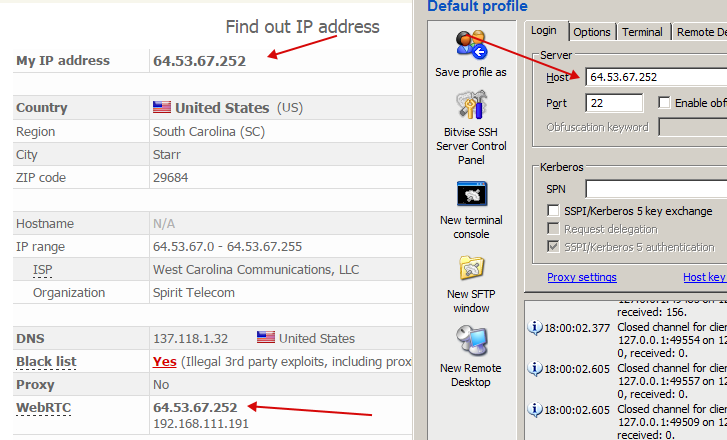
- Now we stomp on Whoer.net.
We refresh the page a couple of times and if everything is OK then the following will happen:

- We believe our eyes and go check in another place.
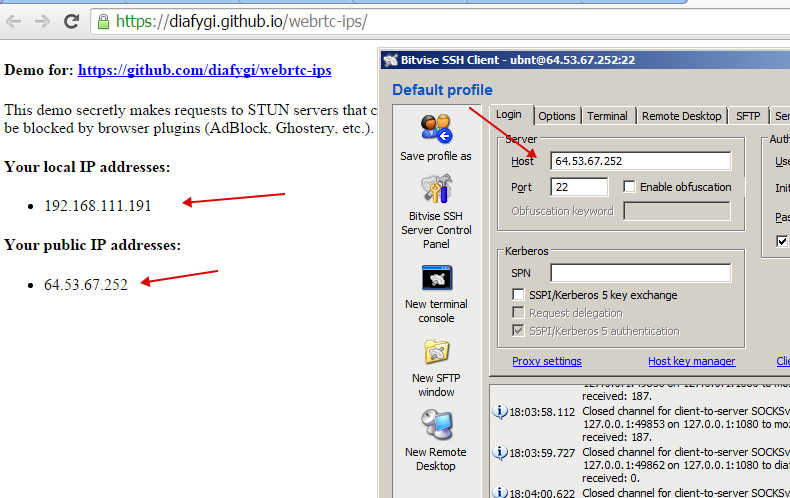
https://diafygi.github.io/webrtc-ips/
The result is the same:

Ready!
You can disable WebRTC in Chrome by using the "WebRTC Leak Prevent" app, which is available in the Chrome Web Store. To cheat, it is enough to raise the second NAT.
- Automatic replacement. I checked for Bitvise + Proxifier on three tunnels and always changed as it should. But it didn't work for me with the Proxifier Portable version, I twisted it in different ways, and for plinkera it is better to use it. Someone also identified the wrong address. Everything is individual and depends on the configuration of your system.
download http://rghost.ru/8GmDcMhf7 - Automatic replacement No.2. Redesigned an existing program using a different connection method. Using Proxifier, Portable already synced with the site to check the address and change it on the network adapter. I tested three tunnels, but for some reason I found the wrong address on one of them, but in the same subnet.
скачать https://www.sendspace.com/file/3tokwr - Semi-automatic replacement, with handles, but also in one click. In my case, this method was suitable, since I had practically used it before, only editing two bat files and entering everything manually. Well, there is no synchronization with the site, so you don't need to reinstall anything, work on your already configured clients.
Code:@Echo off title WebRTC Changer echo Enter SSH IP: set /p ip=^> cls @Echo on netsh interface ip set address "lan" static %ip% 255.255.255.0 route add %ip% mask 255.255.255.255 192.168.1.1 metric 1 echo Complete! pause
Download all in one archive: https://www.sendspace.com/file/de69b2
(c) https://cryptoworld.su/борьба-с-утечкой-ip-через-webrtc/
