Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
How did a well-known brand suddenly become a participant in a fraudulent scheme?
Cybersecurity researchers from Perception Point recently discovered a vulnerability on the website of the manufacturer of coffee machines and capsules Nespresso, which is actively used by fraudsters to redirect users to malicious sites.
The Open Redirect vulnerability allows attackers to redirect a user to a malicious site or even inject malicious content directly into a legitimate website.
Attackers are able to manipulate the URL value, creating links that seem to originate from Nespresso, but lead to malicious resources. One of these links starts with "t.uk.nespresso.com/r/?id [...]", but in the end redirects to the site of intruders.
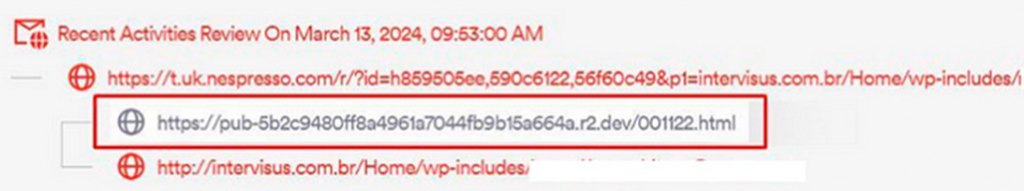
As mentioned above, this vulnerability is actively exploited. The attack begins with an email that disguises itself as a multi-factor authentication request from Microsoft, although the sender has nothing to do with it. The message is designed to appear to have been forwarded several times, and it looks like it's coming from Microsoft.
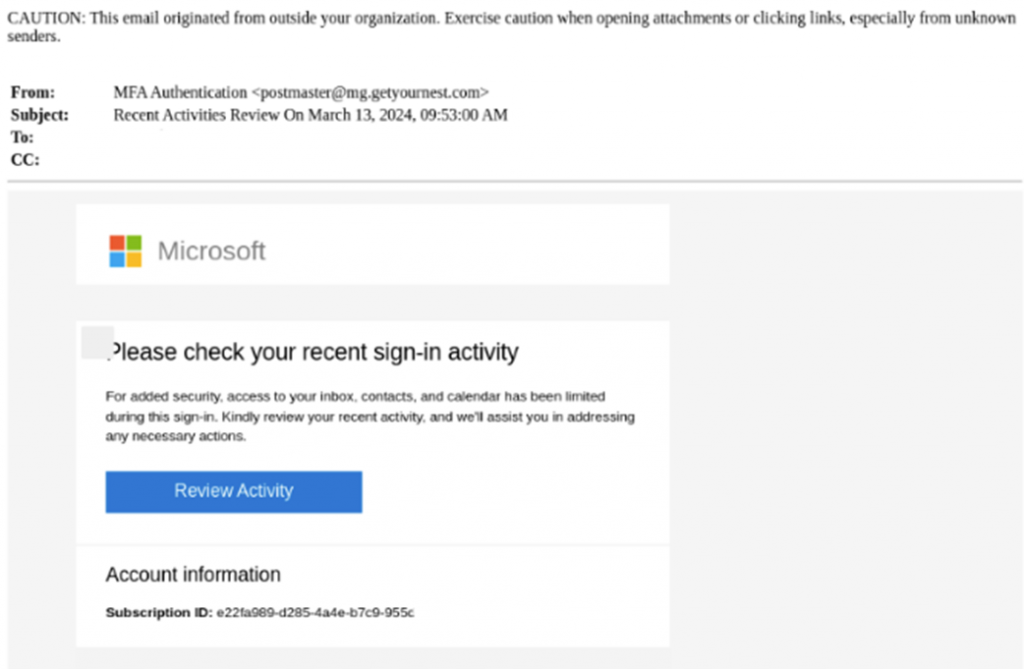
The message content encourages the recipient to check the activity of their last login. Clicking on the link in the browser opens a fake Microsoft login page that aims to steal your credentials.
Researchers emphasize that using a legitimate, trusted Nespresso domain allows you to bypass email spam filters and other security measures, since some security systems only check the initial link, without analyzing embedded or hidden links.
Perception Point noticed many attacks using the Nespresso domain, originating from various senders. In addition to emails about suspicious activity allegedly sent by Microsoft, researchers also recorded similar emails that mimic Bank of America.
As of April 18, that is, at the time the researchers published their article, the vulnerability was still open. The media is waiting for a response from the press service of Nespresso.
In fact, this type of attack using highly reputed domains is quite common. So, in January, we wrote that BMW was the victim of redirect attacks. Exploiting the flaw in her site led to long-term targeted phishing and active distribution of malware.
Users should be wary of clicking on suspicious links in their mail, even if the sender appears legitimate. Attackers have long had ways to fake both the sender and the links themselves inside the email, which is the flaw described above with open redirection.
Cybersecurity researchers from Perception Point recently discovered a vulnerability on the website of the manufacturer of coffee machines and capsules Nespresso, which is actively used by fraudsters to redirect users to malicious sites.
The Open Redirect vulnerability allows attackers to redirect a user to a malicious site or even inject malicious content directly into a legitimate website.
Attackers are able to manipulate the URL value, creating links that seem to originate from Nespresso, but lead to malicious resources. One of these links starts with "t.uk.nespresso.com/r/?id [...]", but in the end redirects to the site of intruders.

As mentioned above, this vulnerability is actively exploited. The attack begins with an email that disguises itself as a multi-factor authentication request from Microsoft, although the sender has nothing to do with it. The message is designed to appear to have been forwarded several times, and it looks like it's coming from Microsoft.

The message content encourages the recipient to check the activity of their last login. Clicking on the link in the browser opens a fake Microsoft login page that aims to steal your credentials.
Researchers emphasize that using a legitimate, trusted Nespresso domain allows you to bypass email spam filters and other security measures, since some security systems only check the initial link, without analyzing embedded or hidden links.
Perception Point noticed many attacks using the Nespresso domain, originating from various senders. In addition to emails about suspicious activity allegedly sent by Microsoft, researchers also recorded similar emails that mimic Bank of America.
As of April 18, that is, at the time the researchers published their article, the vulnerability was still open. The media is waiting for a response from the press service of Nespresso.
In fact, this type of attack using highly reputed domains is quite common. So, in January, we wrote that BMW was the victim of redirect attacks. Exploiting the flaw in her site led to long-term targeted phishing and active distribution of malware.
Users should be wary of clicking on suspicious links in their mail, even if the sender appears legitimate. Attackers have long had ways to fake both the sender and the links themselves inside the email, which is the flaw described above with open redirection.

