Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,026
- Points
- 113
How the tandem of two services became a tool of blackmail.
CronUp specialists have discovered a series of attacks on GitHub repositories, during which attackers erase the contents of repositories and ask them to contact them via Telegram for further instructions. The new method of cyberattack was first noticed by Herman Fernandez of CronUp.
A campaign organizer operating under the Telegram alias Gitloker and posing as an incident analyst is likely using stolen credentials to compromise victims accounts.
Gitloker contact card in Telegram
After the hack, Gitloker claims that it stole data and created a backup copy of it, which can help restore deleted information. Then the repository is renamed and a file is added to it README.me with instructions for the victim.
"I hope this message finds you in good health. This is an urgent notification that your data has been compromised, and we have a backup copy" — such messages can be found in the notes.
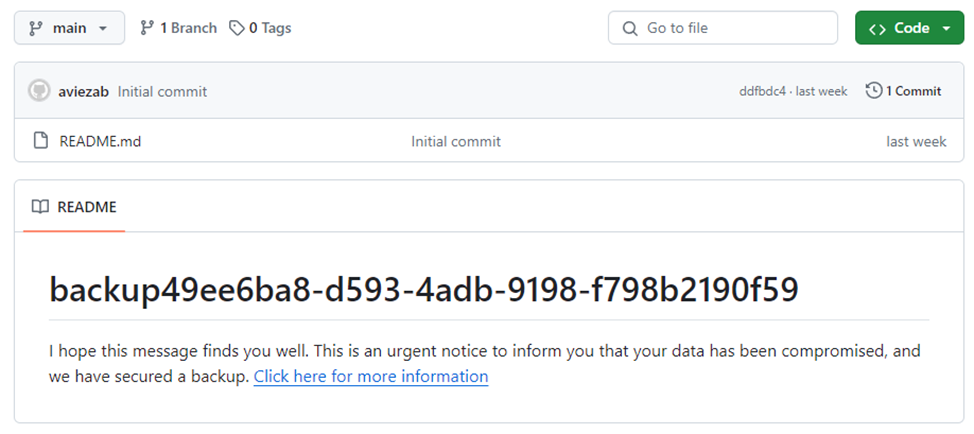
Example of a Gitloker message
At the moment, GitHub representatives have not provided comments on the campaign. However, GitHub previously advised users to change passwords and strengthen account protection to prevent unauthorized access. Measures include:
Attacks on GitHub accounts are not uncommon. In March 2020, hackers reported breaking into Microsoft repositories and stealing more than 500 GB of data. Although the stolen files mostly contained sample code and test projects, security experts expressed concerns that they might contain private API keys or passwords.
CronUp specialists have discovered a series of attacks on GitHub repositories, during which attackers erase the contents of repositories and ask them to contact them via Telegram for further instructions. The new method of cyberattack was first noticed by Herman Fernandez of CronUp.
A campaign organizer operating under the Telegram alias Gitloker and posing as an incident analyst is likely using stolen credentials to compromise victims accounts.

Gitloker contact card in Telegram
After the hack, Gitloker claims that it stole data and created a backup copy of it, which can help restore deleted information. Then the repository is renamed and a file is added to it README.me with instructions for the victim.
"I hope this message finds you in good health. This is an urgent notification that your data has been compromised, and we have a backup copy" — such messages can be found in the notes.

Example of a Gitloker message
At the moment, GitHub representatives have not provided comments on the campaign. However, GitHub previously advised users to change passwords and strengthen account protection to prevent unauthorized access. Measures include:
- Enabling two-factor authentication;
- Adding an access key for secure login without a password;
- Verifying and revoking unauthorized access to SSH keys, deployment keys, and authorized integrations;
- Checking all email addresses associated with the account;
- Analysis of account security logs to track changes in repositories;
- Managing webhooks in repositories;
- Checking and revoking new deployment keys;
- Regularly check the latest commits and collaborators of each repository.
Attacks on GitHub accounts are not uncommon. In March 2020, hackers reported breaking into Microsoft repositories and stealing more than 500 GB of data. Although the stolen files mostly contained sample code and test projects, security experts expressed concerns that they might contain private API keys or passwords.

