The built-in Remote Desktop Connection (RDP) Windows client (mstsc.exe) saves its name (or ip address) and the name of the user under which the logon was logged on each time it successfully connects to a remote computer. The next time the RDP client starts, it prompts the user to select one of the connections that he has already used before. The user can select the name of the remote RDP / RDS server from the list, and the client automatically substitutes the username used previously for logging in.
This is convenient from an end-user perspective, but not secure. Especially when you connect to your RDP server from a public or untrusted computer.
Information about all RDP sessions is stored individually for each computer user in the registry, i.e. a regular user (not an administrator) will not be able to view the remote connection history of another user.
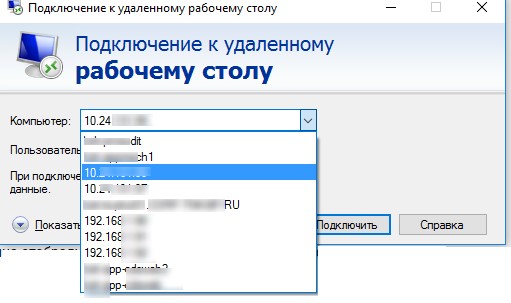
mstsc.exe displays rdp connection history
In this article, we will show you where Windows stores the history of remote desktop connections and saved passwords, and how you can clear this history.
Content:
Deleting the RDP Connection Log from the System Registry
Information about all RDP connections is stored in the registry of each user. You will not be able to remove the computer (s) from the list of RDP connections history using standard Windows tools. You will have to manually delete parameters from the system registry.
Script for clearing the history (logs) of RDP connections
Above, we showed how to manually clear the RDP connection history in Windows. However, doing it manually (especially on several computers) is a rather long task. Therefore, we offer a small script (bat-file) that allows you to automatically clear the history of connections to remote desktops.
To automate the cleaning of RDP history, this script can be placed at startup, or distributed to users' computers using the Group Policy logo script.
Let's analyze all the script commands one by one:
Alternatively, you can clear your RDP connection history using the following PowerShell script:
Get-ChildItem "HKCU:\Software\Microsoft\Terminal Server Client" -Recurse | Remove-ItemProperty -Name UsernameHint -Ea 0
Remove-Item -Path 'HKCU:\Software\Microsoft\Terminal Server Client\servers' -Recurse 2>&1 | Out-Null
Remove-ItemProperty -Path 'HKCU:\Software\Microsoft\Terminal Server Client\Default' 'MR*' 2>&1 | Out-Null
$docsfoldes = [environment]::getfolderpath("mydocuments") + '\Default.rdp'
remove-item $docsfoldes -Force 2>&1 | Out-Null
Note. By the way, the RDC log cleaning function is built into many system and registry cleaners, such as CCCleaner, etc.
How to prevent Windows from saving RDP connection history?
If you want Windows not to save the history of RDP connections, you need to disable writing to the HKCU \ Software \ Microsoft \ Terminal Server Client registry key for all accounts, including System. First, disable inheritance of permissions on the specified branch (Permissions -> Advanced -> Disable inheritance). Then change the ACL to the branch, ticking Deny for users (but, you should understand that this is already an unsupported configuration ...).
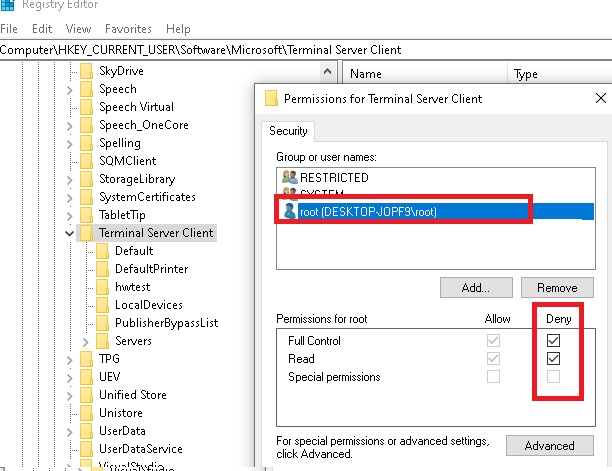
Prevent windows from saving rdp connection history in the registry
As a result, mstsc simply will not be able to write information about the RDP connection to the registry.
Clearing the RDP Bitmap cache
The Remote Desktop Connection client provides persistent bitmap caching functionality. The RDP client, when connected, stores rarely changing portions of the remote screen as a bitmap cache. This allows the mstsc.exe client to download portions of the screen from the local cache that have not changed since the last drawing. This RDP caching mechanism reduces the amount of data transferred over the network.
The RDP cache is represented by two types of files in a directory %LOCALAPPDATA%\Microsoft\Terminal Server Client\Cache:
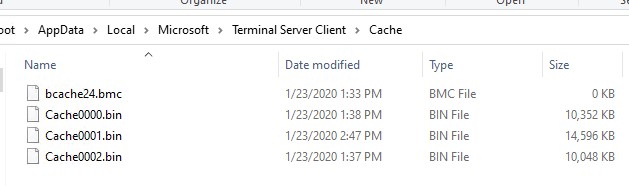
Terminal server client cached images for rdp connection
These files store raw RDP screen bitmaps in 64x64 pixel tiles. Using simple PowerShell or Python scripts (easily searched for by the RDP Cached Bitmap Extractor), you can get PNG files with pieces of the desktop screen and use them to get confidential information. The size of the tiles is small, but large enough to provide useful information for a student of the RDP cache.
RDP Cached Bitmap Extractor
You can prevent the RDP client from saving the screen image to the cache by turning off the Persistent bitmap caching option on the Advanced tab.
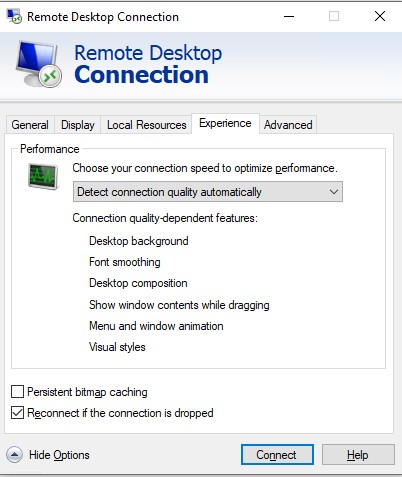
Disable persistent bitmap caching in rdp session
Several times when using the RDP cache, I encountered its corruption:
Bitmap Disk Cache Failure. Your disk is full or the cache directory is missing or corrupted. Some bitmaps may not appear.
In this case, you need to clear the RDP cache directory or disable the Bitmap Caching option.
Deleting saved RDP passwords
If, when establishing a remote RDP connection, before entering the password, the user checked the Remember Me checkbox, then the username and password will be saved in the system password manager (Credential Manager). The next time you connect to the same computer, the RDP client automatically uses the previously saved password for authorization on the remote computer.
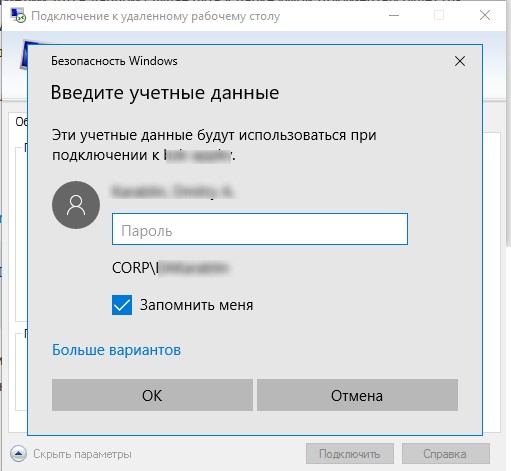
RDP client offers to save user password
You can delete the saved password directly from the mstsc.exe client window. Select the same connection in the list of connections, and click the Delete button. Next, confirm the deletion of the saved password.
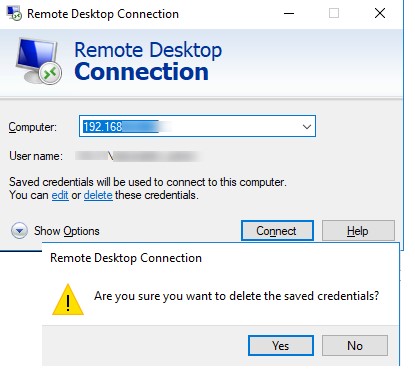
mstsc - delete saved rdp connection password
Alternatively, you can delete the saved password directly from the Windows password manager. Go to the following Control Panel section: Control Panel \ User Accounts \ Credential Manager. Select Manage Windows Credentials and find the computer name (in format TERMSRV/192.168.1.100) in the list of saved passwords. Expand the found item and click the Remove button.
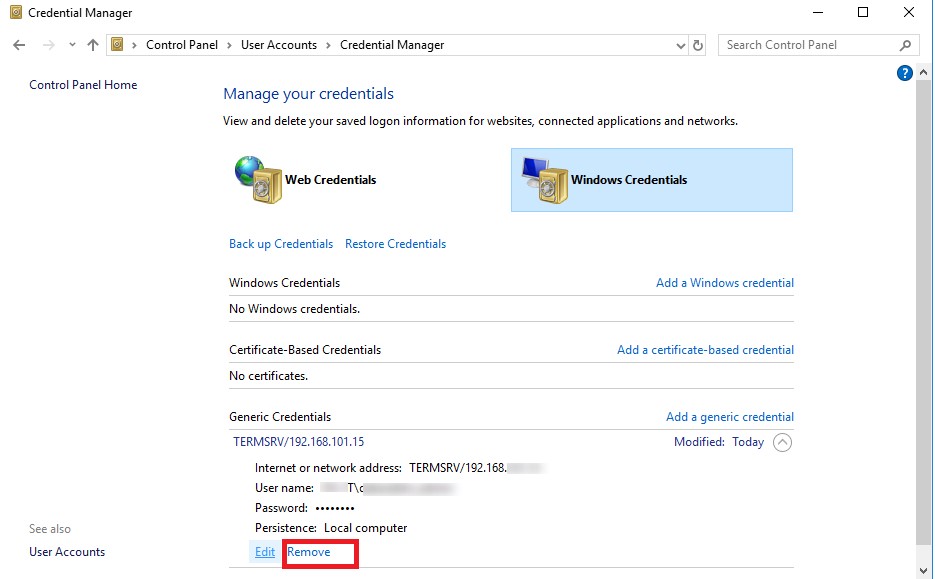
Delete saved rdp password in password manager
In a domain environment, you can prevent storing passwords for RDP connections using the Network access policy: Do not allow storage of passwords and credentials for network authentication.
Clearing RDP logs on the server
Connection logs are also kept on the RDP / RDS server side. You can find information about RDP connections in Event Viewer logs:
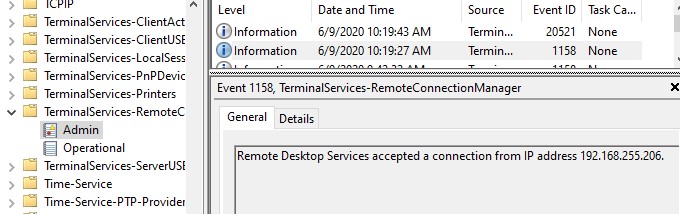
RDP logs in the TerminalServices - RemoteConnectionManager event log
This is convenient from an end-user perspective, but not secure. Especially when you connect to your RDP server from a public or untrusted computer.
Information about all RDP sessions is stored individually for each computer user in the registry, i.e. a regular user (not an administrator) will not be able to view the remote connection history of another user.

mstsc.exe displays rdp connection history
In this article, we will show you where Windows stores the history of remote desktop connections and saved passwords, and how you can clear this history.
Content:
- Deleting the RDP Connection Log from the System Registry
- Script for clearing the history (logs) of RDP connections
- How to prevent Windows from saving RDP connection history?
- Clearing the RDP Bitmap cache
- Deleting saved RDP passwords
- Clearing RDP logs on the server
Deleting the RDP Connection Log from the System Registry
Information about all RDP connections is stored in the registry of each user. You will not be able to remove the computer (s) from the list of RDP connections history using standard Windows tools. You will have to manually delete parameters from the system registry.
- Open the registry editor regedit.exe and go to the HKEY _ CURRENT _ USER \ Software \ Microsoft \ Terminal Server Client branch;
- Inside this section, we are interested in two branches: Default (keeps a history of the last 10 RDP connections) and Servers (contains a list of all RDP servers and usernames previously used to log in);
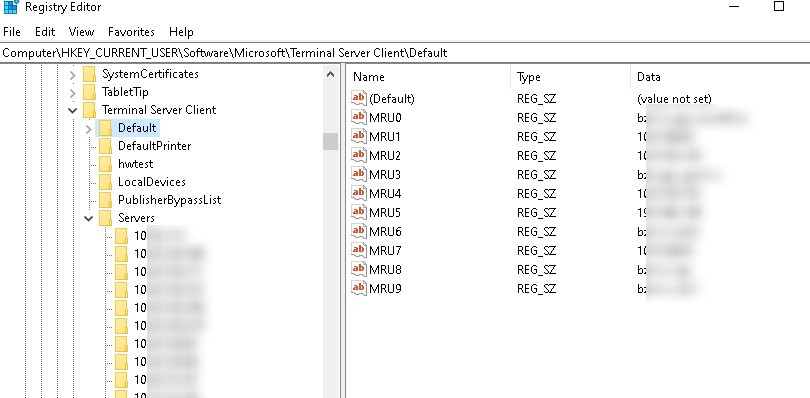
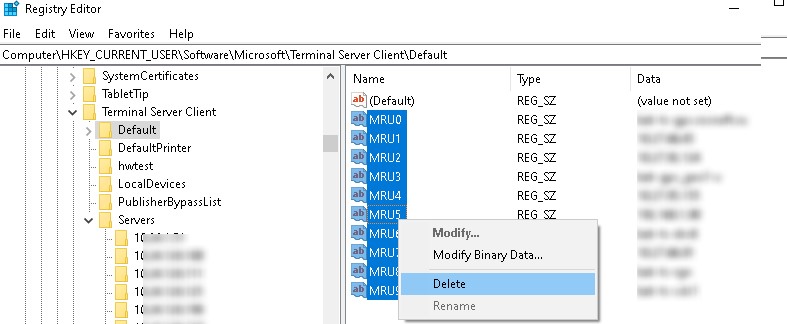
Terminal Server Client MRU registry branch with the latest RDP connections - Expand the registry branch HKEY_CURRENT_USER \ Software \ Microsoft \ Terminal Server Client \ Default, which contains a list of 10 most recently used addresses or names of remote computers (MRU). The name (IP address) of the remote server is stored in the MRU * key value. To clear the history of the last RDP connections, select all keys named MRU 0- MRU 9 , right-click and select Delete;
Clearing rdp history in the registry - Now expand the branch HKEY_CURRENT_USER \ Software \ Microsoft \ Terminal Server Client \ Servers. It contains a list of all RDP connections that were previously used by this user. Expand the branch with the name (IP address) of any host. Note the value of the UsernameHint parameter. It contains the username used to connect to the RDP / RDS host. It is this username that will be substituted in the mstsc.exe client window the next time you try to connect to this host. In addition, the CertHash variable contains the fingerprint of the RDP server certificate (see the article on configuring trusted TLS / SSL certificates for RDP);
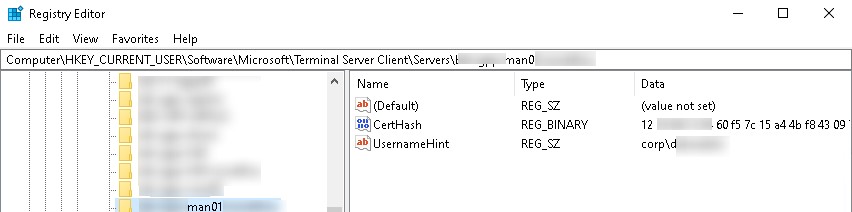
Saved rdp server data in windows registry - To clear the history of all RDP connections and saved usernames, you need to clear the contents of the Servers registry branch. Because you won't be able to select all nested branches, the easiest way is to delete the entire Servers branch and then recreate it manually;
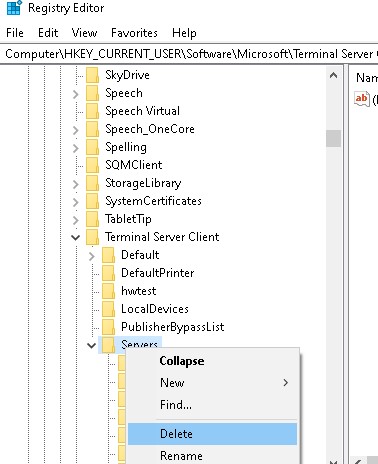
Delete rdp connection history - In addition to the above parameters and registry branches, you need to delete the default RDP connection file Default.rdp. This file stores information about the most recent RDP connection. The file is hidden and located in the Documents directory;
- Windows also keeps a history of RDP connections in jump lists. If you type in the Windows 10 search box mstsc, the previously used RDP connections will appear in the list. You can disable fast navigation history by using the Start _ TrackDocs registry entry dword in the branch HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced, or you can clear the Resent Items lists by deleting files in the directory %AppData%\Microsoft\Windows\Recent\AutomaticDestinations.
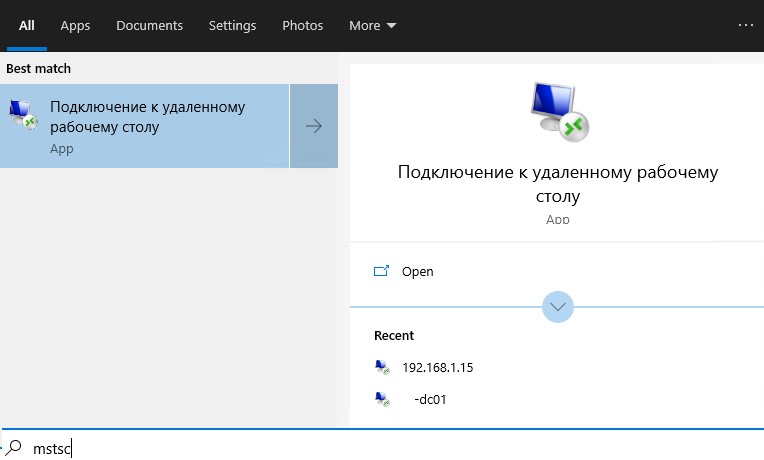
mstsc.exe rdp recent items
Script for clearing the history (logs) of RDP connections
Above, we showed how to manually clear the RDP connection history in Windows. However, doing it manually (especially on several computers) is a rather long task. Therefore, we offer a small script (bat-file) that allows you to automatically clear the history of connections to remote desktops.
To automate the cleaning of RDP history, this script can be placed at startup, or distributed to users' computers using the Group Policy logo script.
Code:
@echo off
reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /f
reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f
reg add "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers"
attrib -s -h %userprofile%\documents\Default.rdp
del %userprofile%\documents\Default.rdp
del /f /s /q /a %AppData%\Microsoft\Windows\Recent\AutomaticDestinationsLet's analyze all the script commands one by one:
- Disabled output of information to the console;
- Deleting all parameters in the HKCU \ Software \ Microsoft \ Terminal Server Client \ Default branch (clearing the list of the last 10 RDP connections);
- Deleting the HKCU \ Software \ Microsoft \ Terminal Server Client \ Servers branch along with attached elements (clearing the list of all RDP connections and saved usernames);
- Re-create the Servers registry branch;
- Remove the Hidden and System attributes from the default.rdp file in the current user's profile directory;
- Deleting the default.rdp file;
- Clearing Recent Items.
Alternatively, you can clear your RDP connection history using the following PowerShell script:
Get-ChildItem "HKCU:\Software\Microsoft\Terminal Server Client" -Recurse | Remove-ItemProperty -Name UsernameHint -Ea 0
Remove-Item -Path 'HKCU:\Software\Microsoft\Terminal Server Client\servers' -Recurse 2>&1 | Out-Null
Remove-ItemProperty -Path 'HKCU:\Software\Microsoft\Terminal Server Client\Default' 'MR*' 2>&1 | Out-Null
$docsfoldes = [environment]::getfolderpath("mydocuments") + '\Default.rdp'
remove-item $docsfoldes -Force 2>&1 | Out-Null
Note. By the way, the RDC log cleaning function is built into many system and registry cleaners, such as CCCleaner, etc.
How to prevent Windows from saving RDP connection history?
If you want Windows not to save the history of RDP connections, you need to disable writing to the HKCU \ Software \ Microsoft \ Terminal Server Client registry key for all accounts, including System. First, disable inheritance of permissions on the specified branch (Permissions -> Advanced -> Disable inheritance). Then change the ACL to the branch, ticking Deny for users (but, you should understand that this is already an unsupported configuration ...).

Prevent windows from saving rdp connection history in the registry
As a result, mstsc simply will not be able to write information about the RDP connection to the registry.
Clearing the RDP Bitmap cache
The Remote Desktop Connection client provides persistent bitmap caching functionality. The RDP client, when connected, stores rarely changing portions of the remote screen as a bitmap cache. This allows the mstsc.exe client to download portions of the screen from the local cache that have not changed since the last drawing. This RDP caching mechanism reduces the amount of data transferred over the network.
The RDP cache is represented by two types of files in a directory %LOCALAPPDATA%\Microsoft\Terminal Server Client\Cache:
- * .bmc
- bin

Terminal server client cached images for rdp connection
These files store raw RDP screen bitmaps in 64x64 pixel tiles. Using simple PowerShell or Python scripts (easily searched for by the RDP Cached Bitmap Extractor), you can get PNG files with pieces of the desktop screen and use them to get confidential information. The size of the tiles is small, but large enough to provide useful information for a student of the RDP cache.

RDP Cached Bitmap Extractor
You can prevent the RDP client from saving the screen image to the cache by turning off the Persistent bitmap caching option on the Advanced tab.

Disable persistent bitmap caching in rdp session
Several times when using the RDP cache, I encountered its corruption:
Bitmap Disk Cache Failure. Your disk is full or the cache directory is missing or corrupted. Some bitmaps may not appear.
In this case, you need to clear the RDP cache directory or disable the Bitmap Caching option.
Deleting saved RDP passwords
If, when establishing a remote RDP connection, before entering the password, the user checked the Remember Me checkbox, then the username and password will be saved in the system password manager (Credential Manager). The next time you connect to the same computer, the RDP client automatically uses the previously saved password for authorization on the remote computer.

RDP client offers to save user password
You can delete the saved password directly from the mstsc.exe client window. Select the same connection in the list of connections, and click the Delete button. Next, confirm the deletion of the saved password.

mstsc - delete saved rdp connection password
Alternatively, you can delete the saved password directly from the Windows password manager. Go to the following Control Panel section: Control Panel \ User Accounts \ Credential Manager. Select Manage Windows Credentials and find the computer name (in format TERMSRV/192.168.1.100) in the list of saved passwords. Expand the found item and click the Remove button.

Delete saved rdp password in password manager
In a domain environment, you can prevent storing passwords for RDP connections using the Network access policy: Do not allow storage of passwords and credentials for network authentication.
Clearing RDP logs on the server
Connection logs are also kept on the RDP / RDS server side. You can find information about RDP connections in Event Viewer logs:
- Security;
- Applications and Services Logs -> Microsoft -> Windows -> TerminalServices-RemoteConnectionManager -> Operational;
- TerminalServices-LocalSessionManager -> Admin.

RDP logs in the TerminalServices - RemoteConnectionManager event log
