What do cybercriminals plan to do with the information they receive?
Security researchers at Proofpoint have discovered that a hacker group allegedly operating in the interests of China is using a new version of the SugarGh0st RAT malware to steal information from artificial intelligence experts in American private companies, government agencies and academia.
The malware campaign, dubbed "UNK_SweetSpecter," was first spotted by researchers earlier this month. So, according to a report published on May 16, attackers use phishing emails with AI topics to distribute a remote access trojan (RAT) called SugarGh0st to a narrow circle of specialists.
According to Proofpoint, the campaign under review targeted fewer than 10 people, all of whom had direct connections to a leading American AI organization (the name of the organization was not disclosed). The researchers suggest that the purpose of the attack was to obtain private information about generative artificial intelligence.
Cisco Talos researchers first discovered SugarGh0st RAT in November last year, when it was allegedly used by a Chinese hacking group to conduct cyber espionage and surveillance of government officials in Uzbekistan and South Korea. Analysis showed that this is a modified version of Gh0st RAT, which first appeared in 2008, when the Chinese hacker group "C. Rufus Security Team" made its source code publicly available.
SugarGh0st RAT differs from the original in a number of improved features, such as detection of specific ODBC registry keys for data exfiltration and lateral movement capabilities. Another new feature is the ability to download and execute malicious code from files with specific extensions and function names. The malware also provides remote operators with the ability to execute user commands via the C2 interface.
During the "UNK_SweetSpecter" campaign, attackers sent emails with AI-related content and an attached archive to their targets. The text indicated that the sender encountered problems using a certain AI tool and asked for help in solving these issues or forwarding them to technical personnel.
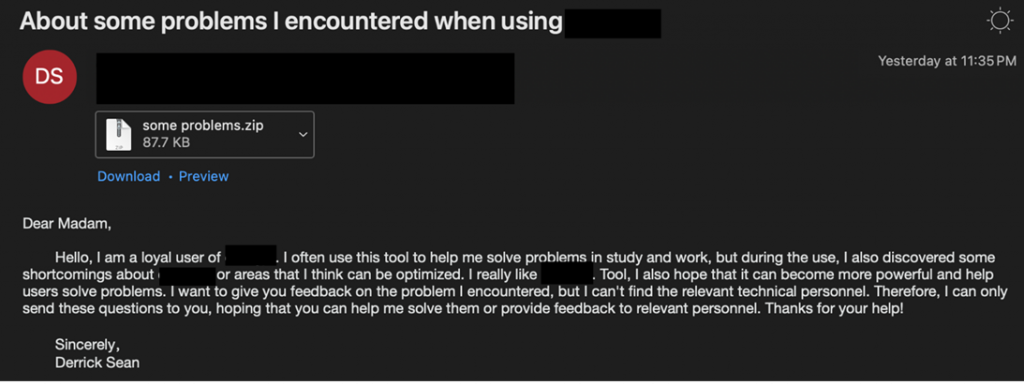
Phishing email with a ZIP archive
When you run the archive, you can find a malicious shortcut inside, similar to what was previously detected by Cisco Talos. This shortcut expands a JavaScript dropper that contains a decoy document, an ActiveX tool for sideloading, and an encrypted binary file. As a result of running the shortcut, SugarGh0st is installed on the compromised system, which communicates with the attackers ' C2 server.
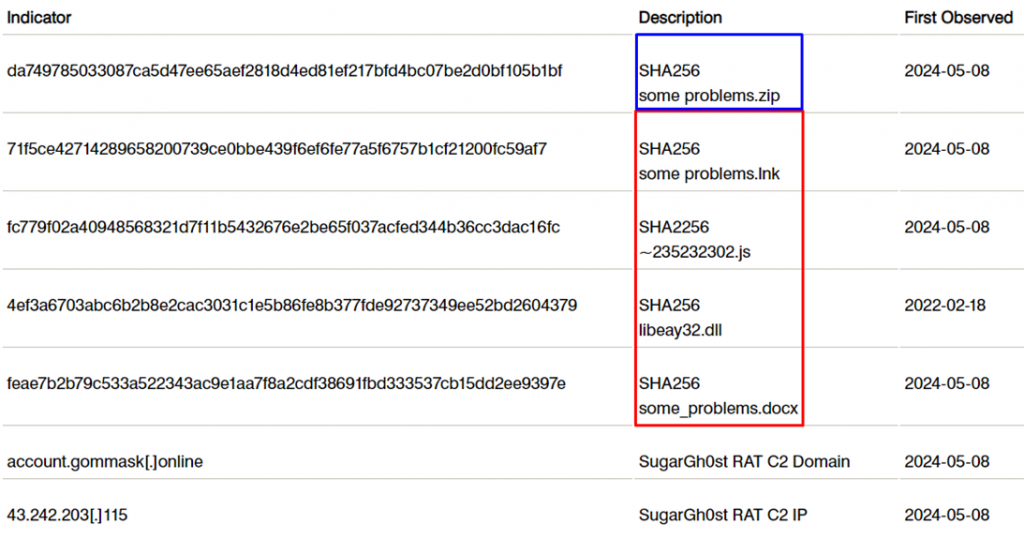
Campaign compromise indicators that include the ZIP archive and its contents
Proofpoint suggests that this campaign is aimed at stealing the secrets of generative AI. This area is now very tasty for intruders, so they are trying their best to get bits of valuable information out of large companies.
So, at the beginning of the year, the US Department of Justice accused a Google engineer of stealing AI secrets and trying to use them in two Chinese technology companies, one of which he himself founded.
Thus, the considered malicious campaign highlights the growing threat of cyber espionage in the field of advanced technologies, such as artificial intelligence. Companies and researchers need to raise awareness of such threats and take enhanced security measures to protect their developments and confidential information from cyber attacks.
As AI penetrates more deeply into a wide variety of industries and becomes increasingly important, the protection of intellectual property in this area is becoming a critical task for both private companies and entire states.
Security researchers at Proofpoint have discovered that a hacker group allegedly operating in the interests of China is using a new version of the SugarGh0st RAT malware to steal information from artificial intelligence experts in American private companies, government agencies and academia.
The malware campaign, dubbed "UNK_SweetSpecter," was first spotted by researchers earlier this month. So, according to a report published on May 16, attackers use phishing emails with AI topics to distribute a remote access trojan (RAT) called SugarGh0st to a narrow circle of specialists.
According to Proofpoint, the campaign under review targeted fewer than 10 people, all of whom had direct connections to a leading American AI organization (the name of the organization was not disclosed). The researchers suggest that the purpose of the attack was to obtain private information about generative artificial intelligence.
Cisco Talos researchers first discovered SugarGh0st RAT in November last year, when it was allegedly used by a Chinese hacking group to conduct cyber espionage and surveillance of government officials in Uzbekistan and South Korea. Analysis showed that this is a modified version of Gh0st RAT, which first appeared in 2008, when the Chinese hacker group "C. Rufus Security Team" made its source code publicly available.
SugarGh0st RAT differs from the original in a number of improved features, such as detection of specific ODBC registry keys for data exfiltration and lateral movement capabilities. Another new feature is the ability to download and execute malicious code from files with specific extensions and function names. The malware also provides remote operators with the ability to execute user commands via the C2 interface.
During the "UNK_SweetSpecter" campaign, attackers sent emails with AI-related content and an attached archive to their targets. The text indicated that the sender encountered problems using a certain AI tool and asked for help in solving these issues or forwarding them to technical personnel.

Phishing email with a ZIP archive
When you run the archive, you can find a malicious shortcut inside, similar to what was previously detected by Cisco Talos. This shortcut expands a JavaScript dropper that contains a decoy document, an ActiveX tool for sideloading, and an encrypted binary file. As a result of running the shortcut, SugarGh0st is installed on the compromised system, which communicates with the attackers ' C2 server.

Campaign compromise indicators that include the ZIP archive and its contents
Proofpoint suggests that this campaign is aimed at stealing the secrets of generative AI. This area is now very tasty for intruders, so they are trying their best to get bits of valuable information out of large companies.
So, at the beginning of the year, the US Department of Justice accused a Google engineer of stealing AI secrets and trying to use them in two Chinese technology companies, one of which he himself founded.
Thus, the considered malicious campaign highlights the growing threat of cyber espionage in the field of advanced technologies, such as artificial intelligence. Companies and researchers need to raise awareness of such threats and take enhanced security measures to protect their developments and confidential information from cyber attacks.
As AI penetrates more deeply into a wide variety of industries and becomes increasingly important, the protection of intellectual property in this area is becoming a critical task for both private companies and entire states.
