Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113

Last month, FireEye specialists said that two hack groups were exploiting a zero-day vulnerability in Pulse Secure VPN to attack the networks of US defense contractors and government organizations around the world.
According to FireEye, the hacks began back in August 2020, when the first hack group, which the company tracks as UNC2630, targeted US defense contractors and European organizations.
In October 2020, a second group of hackers joined the attacks, which FireEye assigned the identifier UNC2717, but almost nothing was known about it.
In both cases, the attackers installed web shells on vulnerable devices, and then used them to get into the victims ' internal networks, from where they stole credentials, emails, and confidential documents.
Now, in a new report, FireEye writes that further investigation of these attacks revealed something strange: at least one of the groups involved in the incidents began removing their malware from infected networks three days before the disclosure.
"Between April 17 and 20, 2021, Mandiant experts observed UNC2630 gaining access to dozens of compromised devices and removing web shells such as ATRIUM and SMALLPULSE," the analysts write.
The actions of the attackers look suspicious and raise questions, for example, whether hackers could have known about the interest from FireEye. Of course, the removal of malware may have been a coincidence, but if the UNC2630 participants were aware that FireEye was investigating some of the networks they hacked, it turns out that the hackers deliberately retreated and deleted the evidence to protect other operations from researchers.
FireEye also reports that it has discovered new details about this hacking campaign. So, experts found four additional strains of malware (in addition to the 12 described earlier).
In addition, FireEye continues to work on identifying compromised devices and their owners, together with the developers of Pulse Secure. This work allowed analysts to learn more about the attackers targets. So, according to new data, most of the victims are organizations based in the United States (the rest are located in European countries). While it was previously thought that the attacks targeted defense contractors and government organizations, it is now clear that the attackers also targeted companies operating in the telecommunications, finance, and transportation sectors.
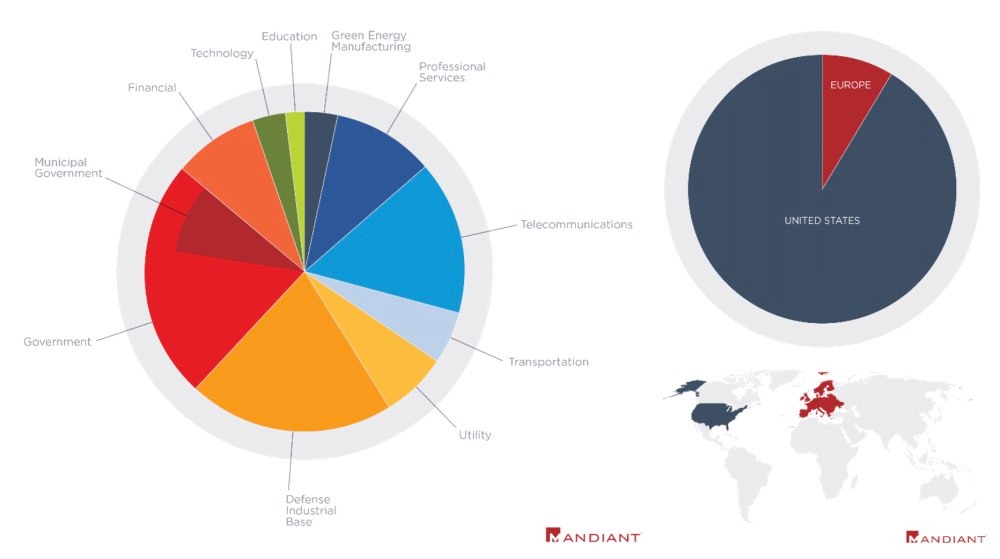
While earlier FireEye analysts wrote that only UNC2630 could have ties to the Chinese government, they now believe that both groups are engaged in cyber espionage and "support the key priorities of the Chinese government."

