How to protect corporate networks from attacks and unauthorized access.
Check Point reported that attackers targeted Check Point Remote Access VPN devices as part of an ongoing campaign to hack corporate networks.
Remote access is integrated into all Check Point network firewalls. It can be configured as a client-to-network VPN for accessing corporate networks via VPN clients, or configured as an SSL VPN for Internet access. Hackers are interested in infiltrating organizations ' networks through remote access settings in order to search for vulnerabilities and try to detect enterprise assets and users.
According to Check Point, cybercriminals target security gateways with outdated local accounts that use insecure password-only authentication. This technique requires a combination of certificate authentication to prevent violations. The company said that by May 24, it had identified 3 attempts to log in to the system, including the systems of various information security solution providers and Check Point customers.
To protect against ongoing attacks, Check Point encouraged customers to check for vulnerable accounts in the Quantum Security Gateway and CloudGuard Network Security products, as well as in the Mobile Access and Remote Access VPN software blades. Clients are advised to change the user authentication method to more secure options or delete vulnerable local accounts from the Security Management Server database.
The company also released a Security Gateway patch that blocks password authentication for all local accounts. After installing the patch, local accounts with weak authentication will not be able to log in to Remote Access VPN. The affected local account will be blocked after the patch is installed.
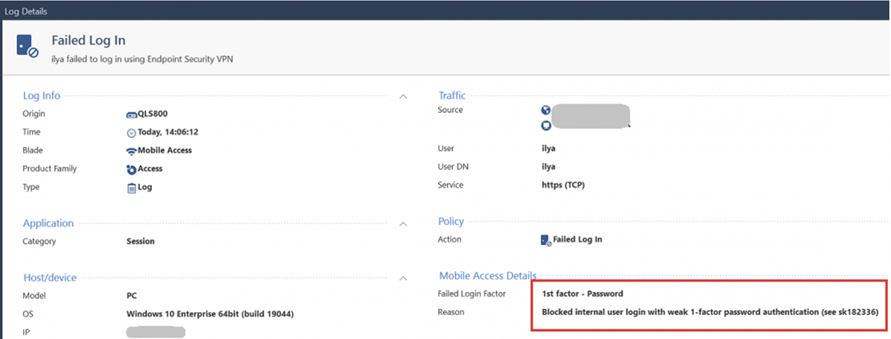
Vulnerable local account is blocked after installing the patch
Customers can find more information about improving the security of their VPNs in the support article, which also provides recommendations for responding to unauthorized access attempts.
Check Point is not the only company that has been attacked on VPN devices in recent months. In April, international cybersecurity was under threat after experts from Cisco Talos discovered a large-scale credential matching campaign targeting VPN and SSH services of devices from companies such as Cisco, Check Point, Fortinet, SonicWall and Ubiquiti.
At the end of March 2024, Cisco already warned about a wave of attacks aimed at remote VPN access services on Cisco Secure Firewall devices. These attacks are particularly effective against weak password policies, as attackers use a small set of frequently occurring passwords for multiple usernames.
Check Point reported that attackers targeted Check Point Remote Access VPN devices as part of an ongoing campaign to hack corporate networks.
Remote access is integrated into all Check Point network firewalls. It can be configured as a client-to-network VPN for accessing corporate networks via VPN clients, or configured as an SSL VPN for Internet access. Hackers are interested in infiltrating organizations ' networks through remote access settings in order to search for vulnerabilities and try to detect enterprise assets and users.
According to Check Point, cybercriminals target security gateways with outdated local accounts that use insecure password-only authentication. This technique requires a combination of certificate authentication to prevent violations. The company said that by May 24, it had identified 3 attempts to log in to the system, including the systems of various information security solution providers and Check Point customers.
To protect against ongoing attacks, Check Point encouraged customers to check for vulnerable accounts in the Quantum Security Gateway and CloudGuard Network Security products, as well as in the Mobile Access and Remote Access VPN software blades. Clients are advised to change the user authentication method to more secure options or delete vulnerable local accounts from the Security Management Server database.
The company also released a Security Gateway patch that blocks password authentication for all local accounts. After installing the patch, local accounts with weak authentication will not be able to log in to Remote Access VPN. The affected local account will be blocked after the patch is installed.

Vulnerable local account is blocked after installing the patch
Customers can find more information about improving the security of their VPNs in the support article, which also provides recommendations for responding to unauthorized access attempts.
Check Point is not the only company that has been attacked on VPN devices in recent months. In April, international cybersecurity was under threat after experts from Cisco Talos discovered a large-scale credential matching campaign targeting VPN and SSH services of devices from companies such as Cisco, Check Point, Fortinet, SonicWall and Ubiquiti.
At the end of March 2024, Cisco already warned about a wave of attacks aimed at remote VPN access services on Cisco Secure Firewall devices. These attacks are particularly effective against weak password policies, as attackers use a small set of frequently occurring passwords for multiple usernames.
