Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,318
- Points
- 113
Criminologists recognize problems with access to modern smartphones.
In April 2024, mobile forensics company Cellebrite ran into a problem: a significant portion of modern iPhones were inaccessible to their hacking tools, according to leaked documents confirmed by 404 Media.
The documents show which Android smartphones and OS versions Cellebrite can access, and give a detailed view of the current state of mobile forensic technologies.
The analysis of the documents was carried out after the FBI announced that it was able to access the mobile phone of Thomas Matthew Crookes, a suspect in the attempted assassination of Donald Trump. The FBI did not specify which brand of phone Crookes used or how the device was unlocked.
The documents, titled "Cellebrite iOS Support Matrix" and " Cellebrite Android Support Matrix ", were sent to 404 Media by an anonymous source. In May, GrapheneOS, an Android-based operating system focused on privacy and security, previously published screenshots of the same documents, but they did not receive widespread attention outside the mobile forensics community.
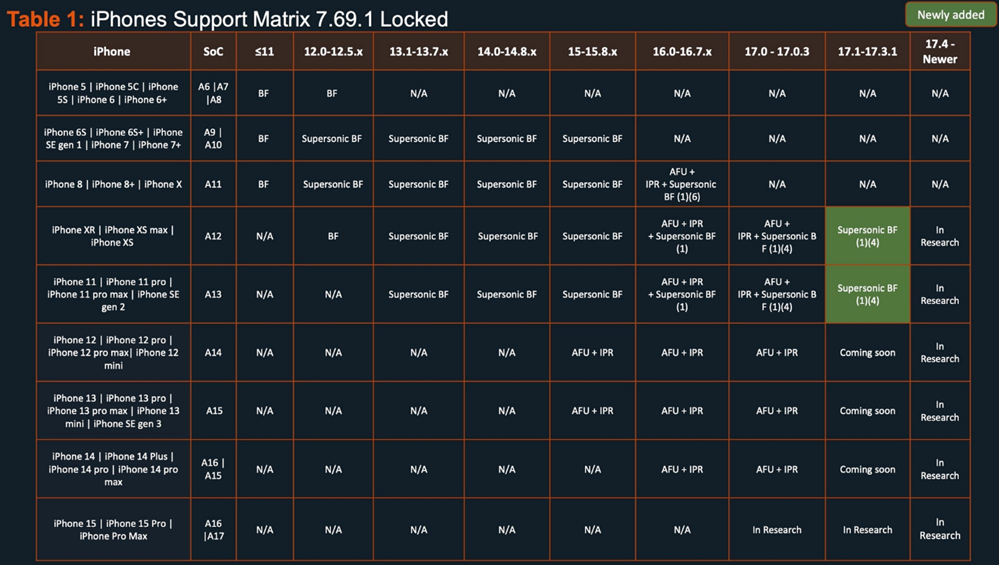
Table of supportedi Phones and versions
For all locked iPhones with iOS version 17.4 and later, Cellebrite documents indicate "In research", which means that models with this version cannot be unlocked using the company's tools.
For previous versions of iOS 17 (from 17.1 to 17.3.1), the iPhone XR and iPhone 11 models are supported. However, for iPhone 12 and later running on 17.1 – 17.3.1, it is marked "Coming soon", which means that support is"coming soon". Also for these versions of iOS, support for Supersonic BF (brute force) was recently added, which allows you to quickly access phones, according to the company.
According to Apple data for June, the majority of iPhone users upgraded to iOS 17 – 77% of all iPhones and 87% of iPhones released in the last 4 years are running on iOS 17.
Cellebrite offers a variety of tools for mobile forensics, including UFED, a hardware device that can extract data from a physically connected smartphone. UFED is widely used by the police. Cellebrite also sells Cellebrite Premium, a service that either provides UFED customers with more options, is processed in the Cellebrite cloud, or is offered as a standalone solution.
Cellebrite claims that Cellebrite Premium is able to get a password "for almost all modern mobile devices, including the latest versions of iOS and Android." However, leaked documents do not support this claim, showing that as of April 2024, Cellebrite could not access locked iPhones running iOS 17.4.
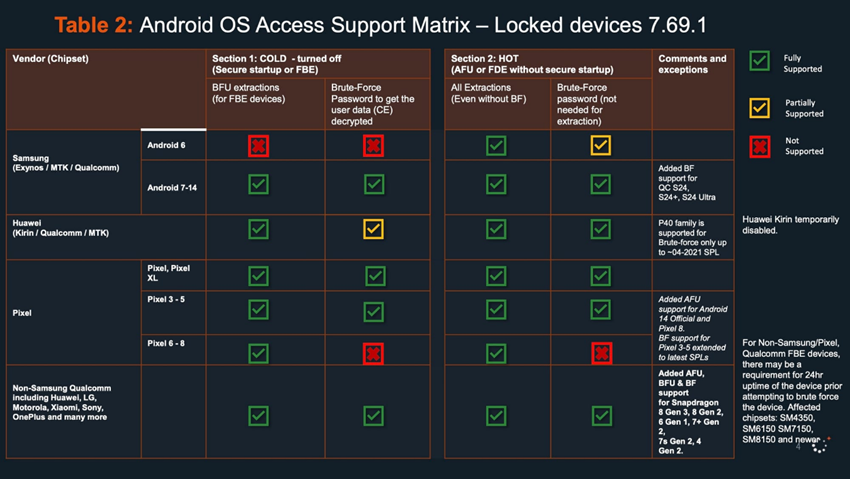
Table of supported Android devices
The second document shows that Cellebrite does not have full support for blocked Android devices, although it covers most of those listed. For example, Cellebrite can't apply brute force to Google Pixel 6, 7, or 8 if they are disabled.
Cellebrite confirmed the authenticity of the documents in an email to 404 Media. A company spokesperson said the documents are intended to help customers understand the capabilities of Cellebrite technologies when conducting ethical and legitimate investigations. The representative also noted that the company does not sell its products to countries that are under US, EU, UK or Israeli sanctions.
Cellebrite isn't the only company dedicated to mobile forensics. Grayshift makes a product called GrayKey, which was initially targeted at iOS devices and then expanded to Android. GrayKey's current capabilities are not clear. Magnet Forensics, which merged with Grayshift in 2023, did not respond to a request for comment.
The Cellebrite Android document also mentions GrapheneOS – a privacy - focused operating system. 404 Media specialists spoke to several people in the underground industry selling secure phones to criminals, who said that some of their customers have switched to using GrapheneOS in recent years. Google and Apple declined to comment on the situation.
Source
In April 2024, mobile forensics company Cellebrite ran into a problem: a significant portion of modern iPhones were inaccessible to their hacking tools, according to leaked documents confirmed by 404 Media.
The documents show which Android smartphones and OS versions Cellebrite can access, and give a detailed view of the current state of mobile forensic technologies.
The analysis of the documents was carried out after the FBI announced that it was able to access the mobile phone of Thomas Matthew Crookes, a suspect in the attempted assassination of Donald Trump. The FBI did not specify which brand of phone Crookes used or how the device was unlocked.
The documents, titled "Cellebrite iOS Support Matrix" and " Cellebrite Android Support Matrix ", were sent to 404 Media by an anonymous source. In May, GrapheneOS, an Android-based operating system focused on privacy and security, previously published screenshots of the same documents, but they did not receive widespread attention outside the mobile forensics community.

Table of supportedi Phones and versions
For all locked iPhones with iOS version 17.4 and later, Cellebrite documents indicate "In research", which means that models with this version cannot be unlocked using the company's tools.
For previous versions of iOS 17 (from 17.1 to 17.3.1), the iPhone XR and iPhone 11 models are supported. However, for iPhone 12 and later running on 17.1 – 17.3.1, it is marked "Coming soon", which means that support is"coming soon". Also for these versions of iOS, support for Supersonic BF (brute force) was recently added, which allows you to quickly access phones, according to the company.
According to Apple data for June, the majority of iPhone users upgraded to iOS 17 – 77% of all iPhones and 87% of iPhones released in the last 4 years are running on iOS 17.
Cellebrite offers a variety of tools for mobile forensics, including UFED, a hardware device that can extract data from a physically connected smartphone. UFED is widely used by the police. Cellebrite also sells Cellebrite Premium, a service that either provides UFED customers with more options, is processed in the Cellebrite cloud, or is offered as a standalone solution.
Cellebrite claims that Cellebrite Premium is able to get a password "for almost all modern mobile devices, including the latest versions of iOS and Android." However, leaked documents do not support this claim, showing that as of April 2024, Cellebrite could not access locked iPhones running iOS 17.4.

Table of supported Android devices
The second document shows that Cellebrite does not have full support for blocked Android devices, although it covers most of those listed. For example, Cellebrite can't apply brute force to Google Pixel 6, 7, or 8 if they are disabled.
Cellebrite confirmed the authenticity of the documents in an email to 404 Media. A company spokesperson said the documents are intended to help customers understand the capabilities of Cellebrite technologies when conducting ethical and legitimate investigations. The representative also noted that the company does not sell its products to countries that are under US, EU, UK or Israeli sanctions.
Cellebrite isn't the only company dedicated to mobile forensics. Grayshift makes a product called GrayKey, which was initially targeted at iOS devices and then expanded to Android. GrayKey's current capabilities are not clear. Magnet Forensics, which merged with Grayshift in 2023, did not respond to a request for comment.
The Cellebrite Android document also mentions GrapheneOS – a privacy - focused operating system. 404 Media specialists spoke to several people in the underground industry selling secure phones to criminals, who said that some of their customers have switched to using GrapheneOS in recent years. Google and Apple declined to comment on the situation.
Source

