Man
Professional
- Messages
- 3,222
- Reaction score
- 1,199
- Points
- 113
In late August, Human Security's Satori Threat Intelligence and Research Team discovered a new scam. Brazilian attackers laundered pirated content through ads using front-end sites, domain masking, and a complex content display system using tokens and cookies.
Contents
1. Camu mechanism
2. Camu and referrals
3. Problem for advertisers
4. Not just piracy
— Layout site
The user is taken to one of the scammers' front sites. It contains a button with a link to another scammers' resource. The user clicks on the button and is taken to a site to watch pirated videos.

- Your own piece of Cookie
The scammers developed a special scheme to select which content to display to different groups of users. The content display depended on a piece of a cookie file that was placed (or not placed) in the user's browser.
To do this, while the user was moving from the intermediary site to the final site, a special token was generated, after which a corresponding piece of cookie was embedded in the user's browser.

— A site with pirated content
If the user visited a front-end site before visiting the final site, a corresponding piece of cookie files was placed in their browser. The final site checked for this entry and displayed the corresponding content surrounded by advertising.
Here's what the content display looks like for a user who had this piece of code:

— Domain masking
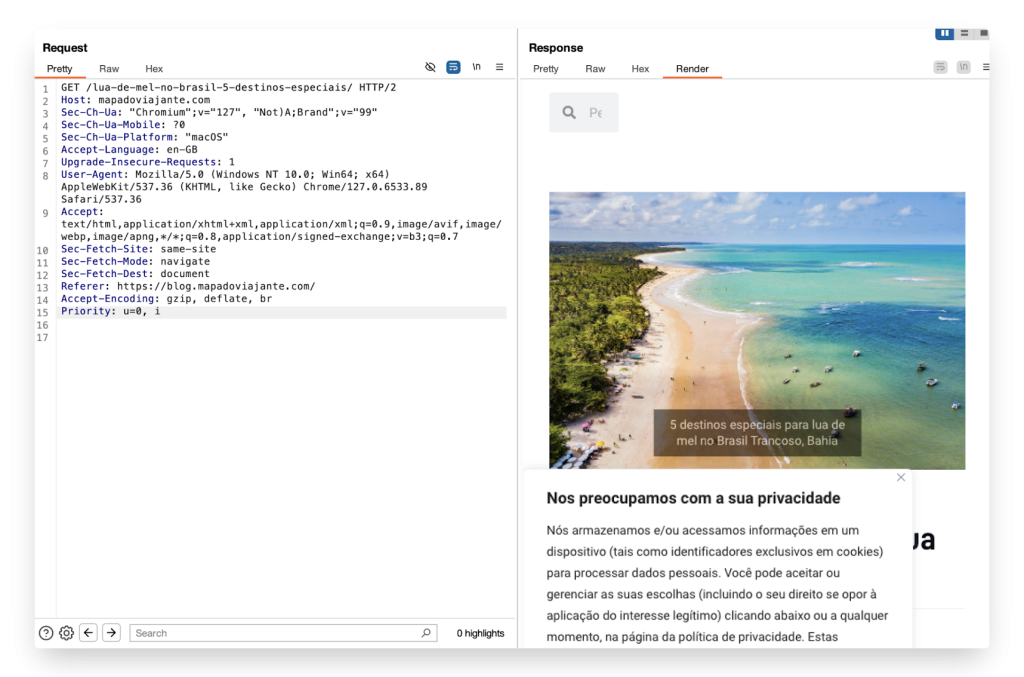
If the user had not previously visited the intermediary site, then when visiting the final site, he was shown completely ordinary content. For example, a blog about tourism and travel.
Here's what the site looked like for a user who didn't have the required cookie entry:
But in the case of Camu, the attackers decided to go even further: they decided to add false referral information to the URLs of some sites, as if the user had come to the blog, for example, from an organic search or from an authoritative site, and not from a pirate domain.
In this way, the attackers tried to mislead advertisers not only about the content on the cashout domain, but also about how users get to that cashout domain in the first place.
Masking of ads, domains, rewriting of referral links, etc. is a serious threat to the digital advertising industry. It is almost impossible to detect such fraudulent schemes manually. That is why advertising protection and invalid traffic blocking tools come to the rescue.
Source
Contents
1. Camu mechanism
2. Camu and referrals
3. Problem for advertisers
4. Not just piracy
Camu mechanism
The fraudulent scheme was named Camu. Experts called it an excellent example of cashing out pirated content.— Layout site
The user is taken to one of the scammers' front sites. It contains a button with a link to another scammers' resource. The user clicks on the button and is taken to a site to watch pirated videos.

- Your own piece of Cookie
The scammers developed a special scheme to select which content to display to different groups of users. The content display depended on a piece of a cookie file that was placed (or not placed) in the user's browser.
To do this, while the user was moving from the intermediary site to the final site, a special token was generated, after which a corresponding piece of cookie was embedded in the user's browser.

— A site with pirated content
If the user visited a front-end site before visiting the final site, a corresponding piece of cookie files was placed in their browser. The final site checked for this entry and displayed the corresponding content surrounded by advertising.
Here's what the content display looks like for a user who had this piece of code:

— Domain masking
If the user had not previously visited the intermediary site, then when visiting the final site, he was shown completely ordinary content. For example, a blog about tourism and travel.
Here's what the site looked like for a user who didn't have the required cookie entry:

Camu and referrals
Camu, like many other domain masking scams, covered their tracks and hid the connection between the two fraudulent domains by removing the redirect information from the front site to the laundering site.But in the case of Camu, the attackers decided to go even further: they decided to add false referral information to the URLs of some sites, as if the user had come to the blog, for example, from an organic search or from an authoritative site, and not from a pirate domain.
In this way, the attackers tried to mislead advertisers not only about the content on the cashout domain, but also about how users get to that cashout domain in the first place.
Problem for advertisers
Let's say you are an advertiser whose ad is placed on the specified site. You noticed suspicious activity or discrepancies in metrics and decided to check why. You went to the site, and it turned out that it was a completely harmless resource. In this way, fraudsters hid from advertisers the placement of ads on low-quality resources and inflated the indicators.Not just piracy
The attackers decided to go big and, in addition to redirecting users to pirate sites, sent them to phishing resources and sites that downloaded malware.Masking of ads, domains, rewriting of referral links, etc. is a serious threat to the digital advertising industry. It is almost impossible to detect such fraudulent schemes manually. That is why advertising protection and invalid traffic blocking tools come to the rescue.
Source

