Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
One-click cashing helps you avoid detection and work from the shadows.
Human Security has uncovered a major scheme to monetize pirated content through ad networks. Attackers operating such sites place advertisements on pages with pirated content to generate income. Website visitors become a source of traffic that attracts advertisers who pay site owners a fee for displaying ads.
However, most advertisers and ad networks are reluctant to place their ads next to pirated content, so attackers are forced to hide their activities.
One of the striking examples of such a scheme is Operation Camu (from Portuguese "camouflage"). The scheme, based in Brazil, is a mechanism for cashing out the proceeds of pirated content. The essence of the operation is that users who want to get access to pirated films and TV shows get to a special site - a "cashed" domain. When users visit such domains directly, they see harmless blogs that do not arouse suspicion among advertisers. However, if a visitor arrives at the site through certain links, they are shown pirated content and a lot of advertisements.
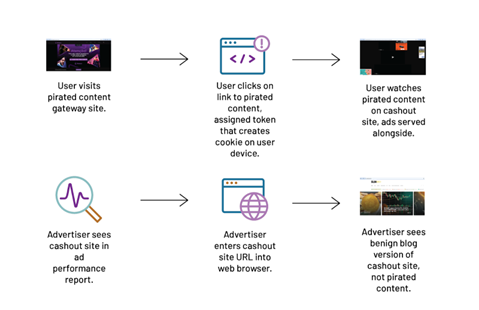
Deception scheme
At its peak, Camu processed up to 2.5 billion ad requests per day across 132 domains created specifically for the scheme. For comparison, this figure roughly corresponds to the daily activity of advertising queries in the cities of Atlanta or Sacramento in the United States. The efforts of specialists have led to the fact that the volume of queries on domains related to Camu has significantly decreased to 100 million per day in the last 9 months. The operation is still ongoing, remaining the largest cloaking scheme ever discovered.
One of the key features of Operation Camu is the domain masking technique. When a user lands on a site with pirated content, they are assigned a special token that goes through several redirect steps before reaching the target site. The token adds a cookie to the user's browser, and the presence or absence of this cookie allows the system to determine which version of the site to show — with pirated content or a regular blog.
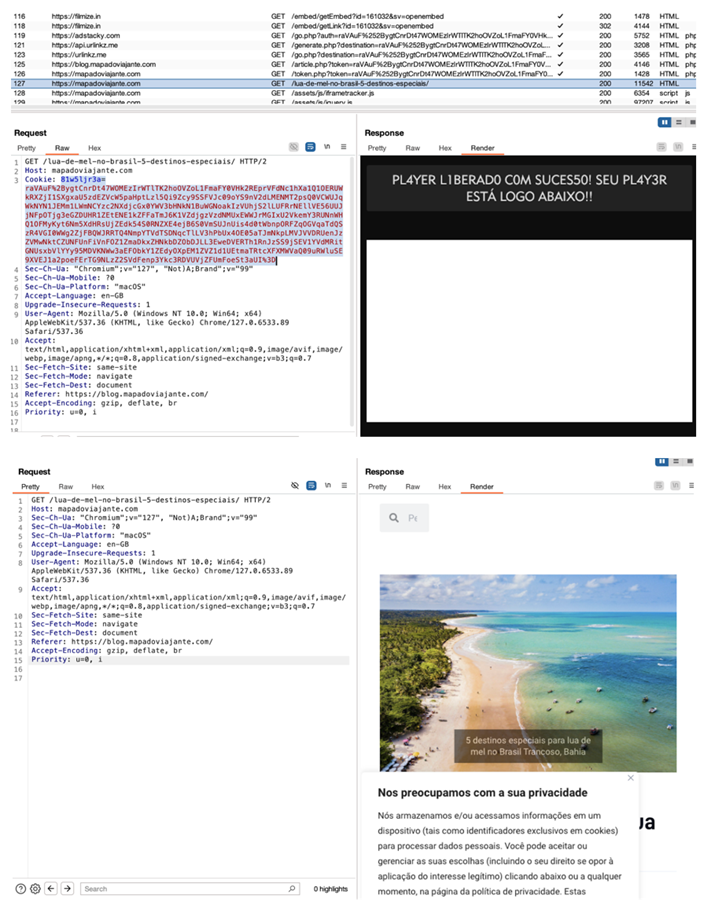
With the help of a cookie, pirated content is shown (at the top), and without a cookie, a regular blog is displayed (at the bottom)
Attackers also employ more sophisticated methods to trick ad networks by spoofing referral data, making the connection between pirate sites and ad domains less obvious. In some cases, instead of being redirected to a site with pirated content, users may be redirected to phishing sites or pages with malware.
Source
Human Security has uncovered a major scheme to monetize pirated content through ad networks. Attackers operating such sites place advertisements on pages with pirated content to generate income. Website visitors become a source of traffic that attracts advertisers who pay site owners a fee for displaying ads.
However, most advertisers and ad networks are reluctant to place their ads next to pirated content, so attackers are forced to hide their activities.
One of the striking examples of such a scheme is Operation Camu (from Portuguese "camouflage"). The scheme, based in Brazil, is a mechanism for cashing out the proceeds of pirated content. The essence of the operation is that users who want to get access to pirated films and TV shows get to a special site - a "cashed" domain. When users visit such domains directly, they see harmless blogs that do not arouse suspicion among advertisers. However, if a visitor arrives at the site through certain links, they are shown pirated content and a lot of advertisements.

Deception scheme
At its peak, Camu processed up to 2.5 billion ad requests per day across 132 domains created specifically for the scheme. For comparison, this figure roughly corresponds to the daily activity of advertising queries in the cities of Atlanta or Sacramento in the United States. The efforts of specialists have led to the fact that the volume of queries on domains related to Camu has significantly decreased to 100 million per day in the last 9 months. The operation is still ongoing, remaining the largest cloaking scheme ever discovered.
One of the key features of Operation Camu is the domain masking technique. When a user lands on a site with pirated content, they are assigned a special token that goes through several redirect steps before reaching the target site. The token adds a cookie to the user's browser, and the presence or absence of this cookie allows the system to determine which version of the site to show — with pirated content or a regular blog.

With the help of a cookie, pirated content is shown (at the top), and without a cookie, a regular blog is displayed (at the bottom)
Attackers also employ more sophisticated methods to trick ad networks by spoofing referral data, making the connection between pirate sites and ad domains less obvious. In some cases, instead of being redirected to a site with pirated content, users may be redirected to phishing sites or pages with malware.
Source

