Carder
Professional
- Messages
- 2,620
- Reaction score
- 2,043
- Points
- 113
This article is educational in nature, we do not call for anything or oblige. The information is presented for informational purposes only.
What do we need for brutus
I will not delve into the terminology, all concepts are obvious and can be easily found in Google. I'll tell you only about the main things:- Proxy;
- Base;
- Soft (checker).
Proxy
The quality of your brut largely depends on them. Using a proxy is a must, otherwise you will just kill your base.Where to get proxies from?
- Buy;
- Find on giveaways.
However, you can live with proxies from the distribution.
There is such software, Proxy Checker from Starley, it allows you to search for valid proxies for your purposes.
- Download the file from the proxy.
- We select the type of proxy.
- We select the service for which you need to select valid proxies.
- We set the timeout and the number of threads (I personally set it as on the screen).
- We press the button "START".
Base
A text document that contains data.Basic database formats:
- mail: password
- login: password
- number: password
Where to get the bases?
- Can be taken from giveaways;
- You can dump yourself;
- You can buy.
What are the best bases?
The bases can be divided into:
1) Valid is a database in which the password matches the soap (login, number) and according to these data you can go to any website / mail.
2) Invalid - hence the databases, according to which it will not be possible to enter the site \ mail, since the password has already been changed, or never matched at all.
3) Privat is a database that has not been leaked to the public, it is unique.
4) Public - a base that other people have already used for their own purposes, most likely they have already squeezed everything out of it.
Obviously, private validbases are most appreciated. Getting these on the free giveaways is a great success.
Software
In short, these are programs that will process your databases.There are a bunch of types of software, a bunch of software itself, I will dwell only on a few.
Checkers
Standard software that allows you to check your database for validity for a specific service. That is, for example, you load the database into the Steam checker - at the output you get accounts that have valid data, you can log in to them and may even take an account for yourself. The checker can also show data from accounts (friends, watch, level, rank, games, gifts, etc.)
Retrievers
A software that performs the function of a checker, but with advanced functions. Unbinding \ rebinding of mails, deleting data, removing protection. Roughly speaking, everything that needs to be done manually after checkers is mostly allowed by retrievers.
Antipublik
Software that compares your database with all databases that have ever merged into this software. Therefore, antipublic gives out the private percentage of your base. for example, you have a base of 1000 lines. Of these, 500 lines have already been merged into an anti-public. This means that the private of your base is 50%.
It is important to understand that for each service you need to use certain software. There is no one program that will check your base for Steam, VK, Instagram, Origin, etc. accounts. For each request - its own software.
How to brute?
Let's analyze the main stages using my personal example.- We have a base, we have a proxy. We run the database through the antipublic, I use MYRZ. Antipublik searches for private in your database. You work with this private chat first.
- If you have a mail: pass database, you can check it to validate the mailboxes themselves. You can use the All-In-One Checker for this.
- We load the base and proxies, select the type of proxies there.
- We set the number of threads (the more threads, the faster the base is checked, but the load on the computer is stronger).
- You can set requests (the checker will look for letters from senders in the mail, or with the content that you specify to him).
- Results are given. Hoods are valid mails, bads are invalid. The results are saved in the folder with the software.
- Of course, it is better to buy a private letter checker, here are the two most popular options - AIO private or a letter checker from Starley. Private software is better than a crack, faster, produces fewer errors and is less likely to infect your computer with some kind of stylus.
Steam Machine
A very convenient, simple and cool checker, albeit a public one.
If you have a login: pass database, then we simply load the database, proxies, set the streams, put the necessary checkboxes (what you want to check in the database), check the "checker" box and run it. If you have a mail: pass base - just put a tick "delete domains" and the checker will independently turn all mails into logins.
Starley's Steam Retriever
Perhaps one of the best Steam software. Explaining what and how it takes too long, there are a bunch of manuals, there is a vidos on the same site, so just know.
Wish Checker by Prince Jack
Nice software, public. Checks Wish accounts. Even with free proxies and with a base from the distribution, I found about 10k accounts with balances with it.

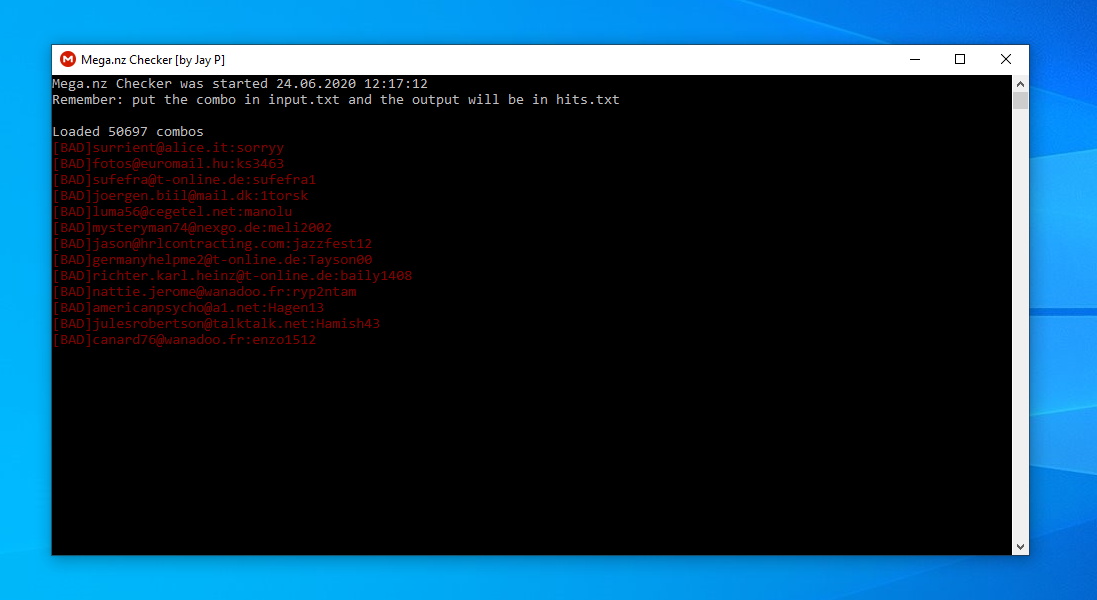
Mega Checker [byJayP]
A good mega checker, albeit very slow. In principle, checking mega is straightforward if you have nothing to do. But for someone else's purpose, it may fit.
VkBrute by DarkSHA
Not a bad VK checker, but demanding on proxies.

That is, in general, all the software that I regularly use.
I hope I was able to convey to you the most important basics for starting. Further it is just a matter of experience and further training. Develop - and soon you will start doing it automatically.

