BitBrowser Anti - Detect
Professional
- Messages
- 374
- Reaction score
- 4
- Points
- 18
Web scraping Google Maps can offer a wide range of valuable advantages. Google Maps is a vast repository of information, including details about businesses, locations, and customer reviews. By extracting these data through web scraping, businesses can gain insights and use the information in various beneficial ways. If you want to learn more about the significance of using Google Maps for web scraping, keep on reading.
1. Competitive Analysis
Web scraping Google Maps allows you to gather data on your competitors. For example, if you are a restaurant owner, you can scrape information about your nearby restaurants such as their operating hours, customer ratings, and the types of cuisine they offer. This data can be used to identify gaps in the market and analyze their strengths and weaknesses.
By comparing your own offerings and performance metrics with those of your competitors, you can formulate strategies to gain a competitive edge.
2. Location - Based Insights
For companies with a physical presence or those targeting specific geographical areas, Google Maps scraping provides location - based intelligence.
For example, real - estate agencies can scrape property listings, including details such as price, size, and amenities. This data can be helpful for understanding the real - estate market trends in different neighborhoods.
3. Customer Sentiment Analysis
Customer reviews scraped from Google Maps are a goldmine for understanding customer sentiment. By analyzing the language and sentiment of reviews, businesses can identify areas of customer satisfaction and dissatisfaction.
For example, a hotel can analyze reviews to find out what guests appreciate most about their stay and what needs improvement. This feedback can be used to improve services and enhance the overall customer experience.
4. Market Trends
When it comes to getting information about trends in specific locations, Google Maps is extremely helpful. Staying abreast of trends will boost your efficiency and improve your strategic decisions.
Step 1: Understanding the Legal Aspect
Before starting data collection, you must make sure that you understand and are adhering to Google's Terms of Service. This will help you avoid bans and restrictions.
Step 2: Selecting Your Tools
Selecting tools for web scraping is crucial. The appropriate tools will make your process more convenient and less burdensome. You must pick the programming language and libraries that you will utilize during web scraping.
Step 3: Creating the Scraper
After installing the essential tools, determine the data you want to scrape and build a library to manage dynamic content. You must ensure that your scraper will fully load the elements.
Step 4: Storing the Collected Data
Once you have collected the relevant data, it is essential to store it in a structured format. You can employ formats such as CSV or a database for further analysis.
Step 1: Establish a Google Cloud Project
You can initiate a new project by accessing the Google Cloud Console.
Step 2: Activate the Google Maps API
After creating a project, you must enable the APIs you require, such as the Places API, Geocoding API, and others.
Step 3: Acquire an API Key and Make API Requests
You must generate an API key for authentication purposes and make requests according to your specific needs.
Step 4: Manage Data and Adhere to Usage Limits
You must handle the responses returned by the API. Keep in mind to be aware of the usage limits and pricing related to the API.
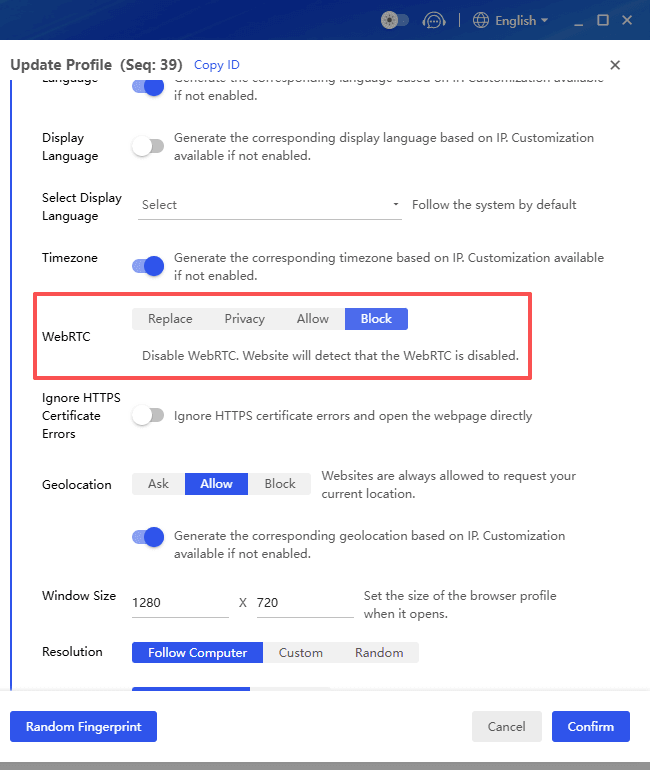
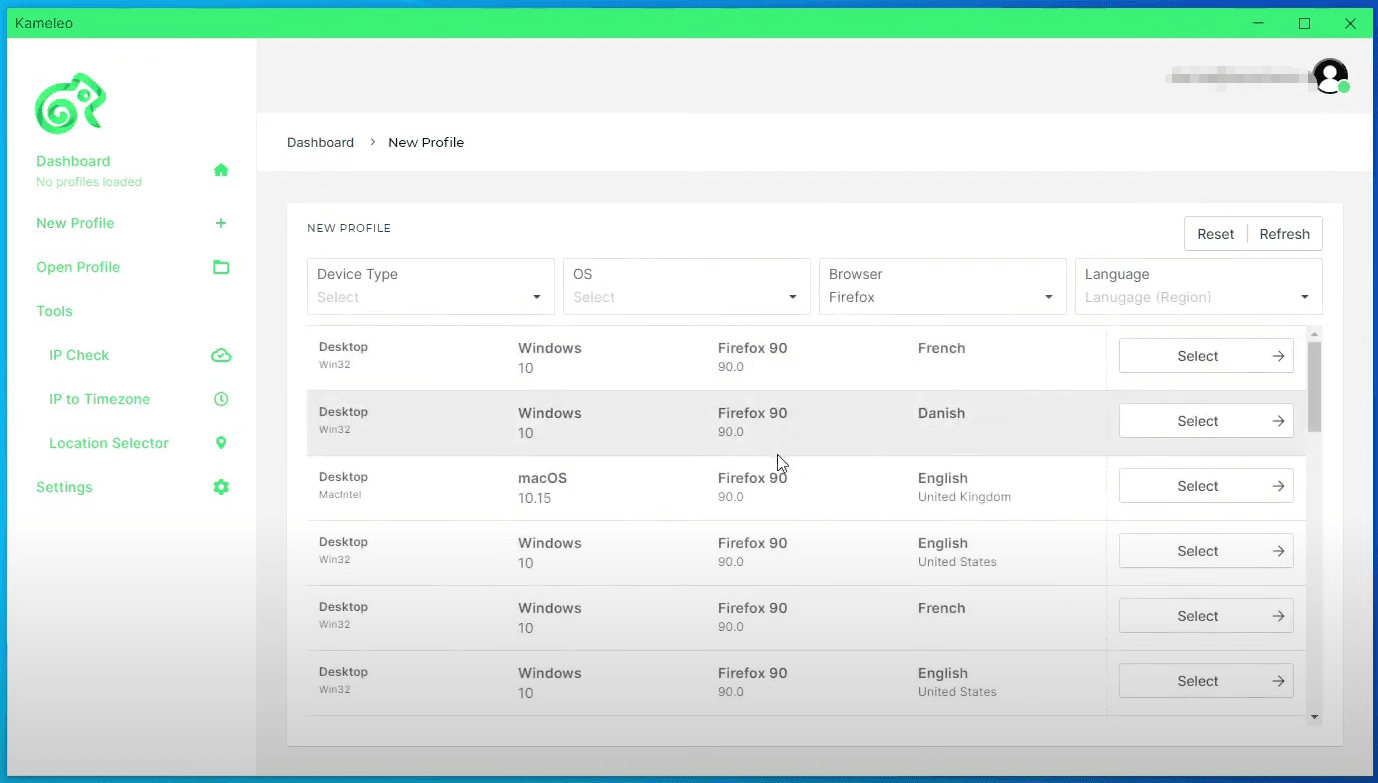
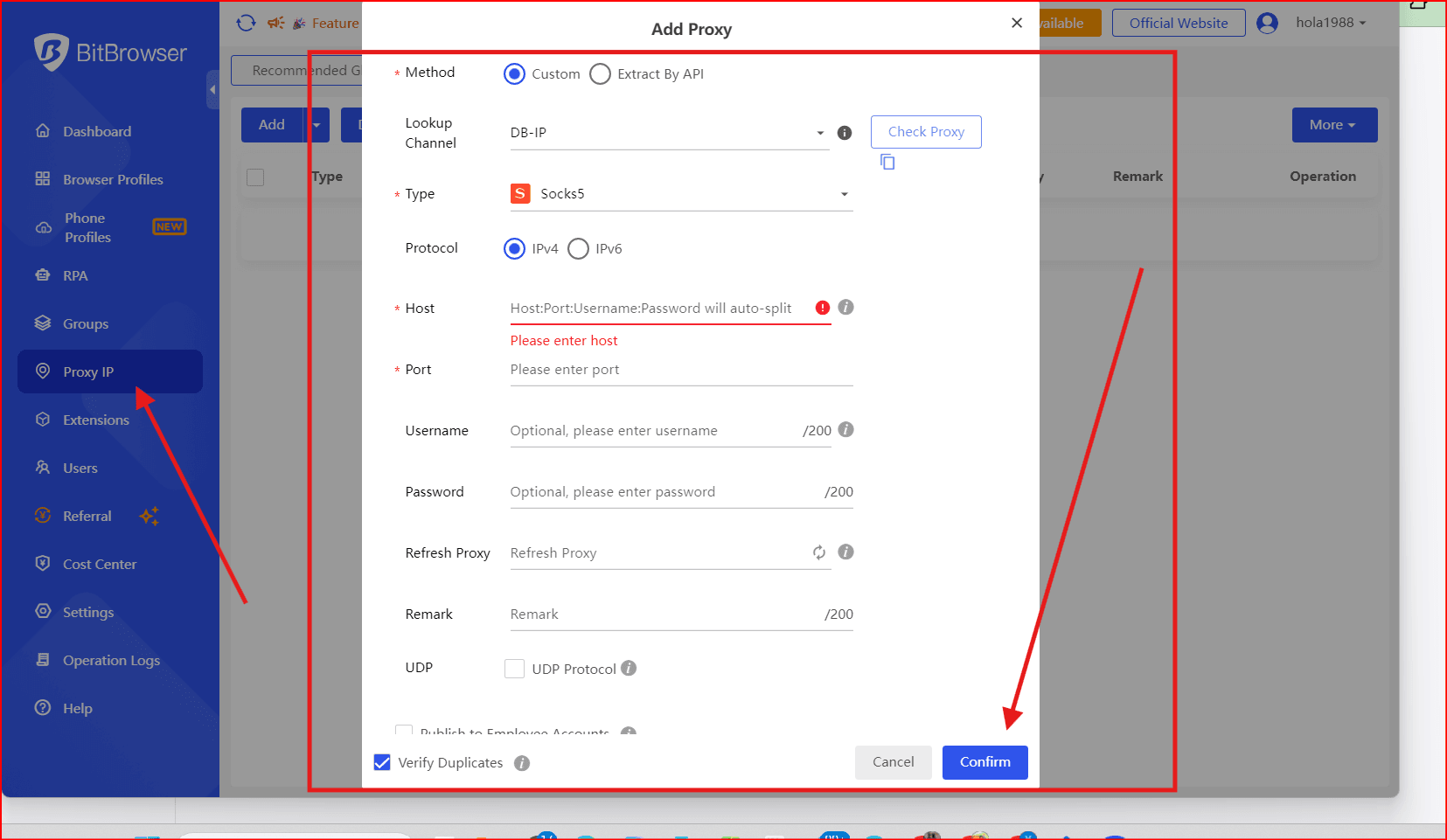
Users can use BitBrowser to mask their IP addresses and user agent. It generates unique fingerprints for each profile and guarantees that your activities are untraceable. This fingerprinting technology modifies browser fingerprints in order to avoid detection.
BitBrowser enables users to create multiple accounts, thus diversifying their scraping activities. The collaborative management feature allows businesses to understand their performance and share results with their teams.
In addition, BitBrowser supports all your proxies seamlessly. With BitBrowser, you can bypass API rate limits. Unique digital identities and IP addresses provide you with the ability to remain undetectable and gather data without being banned.
As recommended, scraping Google Maps should be done cautiously and moderately. Always take into account the implications of data collection methods and pay close attention to ethical practices in any data-driven project.
Benefits of Web Scraping Google Maps
Web scraping Google Maps is widely employed by various businesses. Here's why.1. Competitive Analysis
Web scraping Google Maps allows you to gather data on your competitors. For example, if you are a restaurant owner, you can scrape information about your nearby restaurants such as their operating hours, customer ratings, and the types of cuisine they offer. This data can be used to identify gaps in the market and analyze their strengths and weaknesses.
By comparing your own offerings and performance metrics with those of your competitors, you can formulate strategies to gain a competitive edge.
2. Location - Based Insights
For companies with a physical presence or those targeting specific geographical areas, Google Maps scraping provides location - based intelligence.
For example, real - estate agencies can scrape property listings, including details such as price, size, and amenities. This data can be helpful for understanding the real - estate market trends in different neighborhoods.
3. Customer Sentiment Analysis
Customer reviews scraped from Google Maps are a goldmine for understanding customer sentiment. By analyzing the language and sentiment of reviews, businesses can identify areas of customer satisfaction and dissatisfaction.
For example, a hotel can analyze reviews to find out what guests appreciate most about their stay and what needs improvement. This feedback can be used to improve services and enhance the overall customer experience.
4. Market Trends
When it comes to getting information about trends in specific locations, Google Maps is extremely helpful. Staying abreast of trends will boost your efficiency and improve your strategic decisions.
Getting Started to Scrap Data from Google Maps
Once you understand the significance of web scraping Google Maps, you can follow this step-by-step guide.Step 1: Understanding the Legal Aspect
Before starting data collection, you must make sure that you understand and are adhering to Google's Terms of Service. This will help you avoid bans and restrictions.
Step 2: Selecting Your Tools
Selecting tools for web scraping is crucial. The appropriate tools will make your process more convenient and less burdensome. You must pick the programming language and libraries that you will utilize during web scraping.
Step 3: Creating the Scraper
After installing the essential tools, determine the data you want to scrape and build a library to manage dynamic content. You must ensure that your scraper will fully load the elements.
Step 4: Storing the Collected Data
Once you have collected the relevant data, it is essential to store it in a structured format. You can employ formats such as CSV or a database for further analysis.
How to Scrap Google Maps?
Extracting data from Google Maps using Google Maps API is recommended. Here’s how to do it.Step 1: Establish a Google Cloud Project
You can initiate a new project by accessing the Google Cloud Console.
Step 2: Activate the Google Maps API
After creating a project, you must enable the APIs you require, such as the Places API, Geocoding API, and others.
Step 3: Acquire an API Key and Make API Requests
You must generate an API key for authentication purposes and make requests according to your specific needs.
Step 4: Manage Data and Adhere to Usage Limits
You must handle the responses returned by the API. Keep in mind to be aware of the usage limits and pricing related to the API.
How Antidetect Browsers Help with Web Scraping Google Maps?
Automated tasks such as scraping are usually blocked or flagged by websites. At this point, anti-detect browsers like BitBrowser come in to help. Without using this tool, web scraping Google Maps can trigger CAPTCHAs, and the risk of your IP address being blocked is increasing significantly.Users can use BitBrowser to mask their IP addresses and user agent. It generates unique fingerprints for each profile and guarantees that your activities are untraceable. This fingerprinting technology modifies browser fingerprints in order to avoid detection.
BitBrowser enables users to create multiple accounts, thus diversifying their scraping activities. The collaborative management feature allows businesses to understand their performance and share results with their teams.
In addition, BitBrowser supports all your proxies seamlessly. With BitBrowser, you can bypass API rate limits. Unique digital identities and IP addresses provide you with the ability to remain undetectable and gather data without being banned.
Conclusion
Google Maps has been the go-to web mapping platform for everyone. The crucial role it plays in people's digital and real lives is the reason why Google Maps holds billions of data that can be scraped.As recommended, scraping Google Maps should be done cautiously and moderately. Always take into account the implications of data collection methods and pay close attention to ethical practices in any data-driven project.