BitBrowser Anti - Detect
Professional
- Messages
- 374
- Reaction score
- 4
- Points
- 18
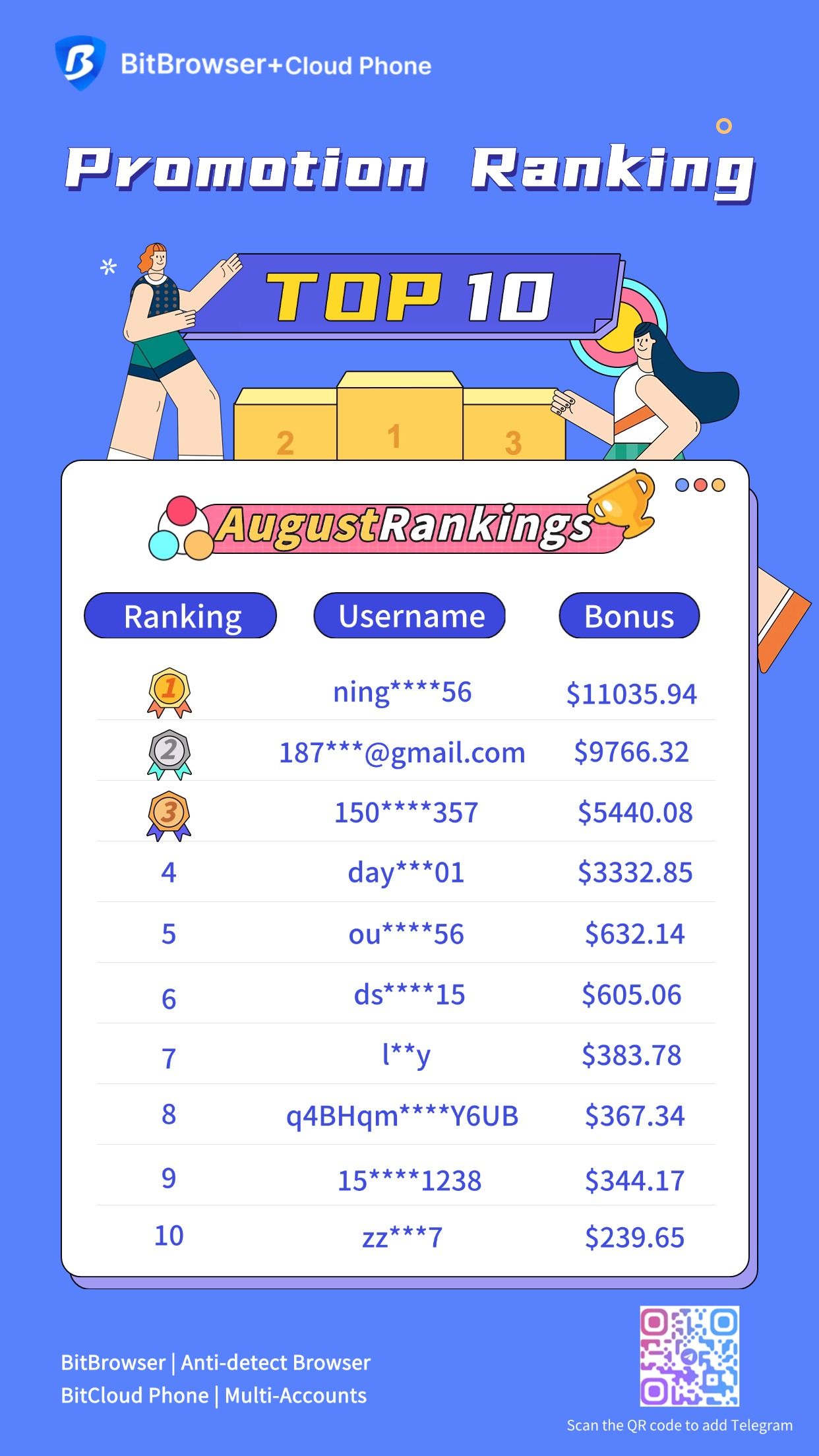
BitBrowser has now released the August Promoter Ranking List, where many users have earned considerable passive income through promotion activities. With "zero-threshold participation + long-term profit sharing" at its core, this program provides ordinary people with a low-risk, high-return side hustle option.
I. Why Are Promotion Earnings So Tempting?
According to the platform's policy, for each friend a promoter successfully invites to subscribe to a package, the promoter can receive a profit-sharing reward for 24 consecutive months, with a rate as high as 20% of the package fee. Taking the annual package of 1,200 yuan as an example, the promoter can earn 240 yuan in profit sharing per year, with a cumulative income of 480 yuan over two years. This "one-time promotion, long-term benefit" model turns each invited user into a stable source of income. More notably, the platform adopts a real-time settlement system — after a user completes the subscription via the exclusive link, the commission is credited immediately, with no need to wait for periodic settlement.
II. How Can Ordinary People Participate Easily?
1. Zero-Threshold Registration:
Simply complete membership registration on the BitBrowser official website, and the promotion permission will be activated automatically — no fees to pay or qualification verification to submit.2. Generate an Exclusive Link:
After logging into the Member Center, the system will automatically generate a promotion link with parameters or an invitation code, supporting one-click copying.3. Multi-Channel Distribution:
The link can be shared to social platforms such as WeChat groups, Weibo, and Douyin, or sent directly to targeted groups like cross-border e-commerce practitioners and social media operators.4. Real-Time Earnings Check:
The backend provides a detailed data dashboard, which displays key indicators such as the number of invited people, subscription amount, and cumulative commission in real time, making it easy for promoters to adjust their strategies.III. Why Choose BitBrowser as the Promotion Target?
As a professional fingerprint browser tool, its core advantages directly address the pain points of cross-border businesses:
Environment Isolation Technology: Creates independent fingerprint and IP environments for each account, simulates over 200 device parameters, and effectively reduces account ban rates by 35%. This feature is particularly suitable for scenarios such as social media multi-account management and ad testing.
Team Collaboration Function: Supports multi-person co-management of account matrices, and allows setting different levels of operation permissions to meet the collaboration needs of enterprise-level users.
Automated Operations: Built-in RPA process designer, which can record and repeatedly execute operations such as login, posting, and data collection, greatly improving operational efficiency.
Cloud Synchronization: User data is synchronized to the cloud in real time, supporting seamless switching across devices and enabling users to handle business anytime, anywhere.

IV. Exclusive Benefits for Participating in Promotion
To reward promoters, the platform has launched multiple incentive measures:
New User Benefits: Users who register via the promotion link can receive 10 permanent free windows, directly reducing usage costs.
Tiered Rewards: The top 10 promoters on the August ranking list can receive a BitBrowser + Cloud Phone combination package, and also enjoy an additional "permanent 20% + 10%" profit-sharing reward.
Limited-Time Event: During the August Carnival Season, participating in promotion gives you the chance to win valuable rewards such as cash red envelopes and exclusive benefits. The event entry has been launched simultaneously on the official website.
If you are a traffic site owner, influencer/blogger, e-commerce seller, or proxy IP practitioner, you might as well seize this opportunity. Simply share your exclusive link with users in need to start a long-term income channel. Click [Event Entry] to learn more details, or add customer service to consult specific rules, and turn every share into a sustainable source of income.