BitBrowser Anti - Detect
Professional
- Messages
- 316
- Reaction score
- 4
- Points
- 18

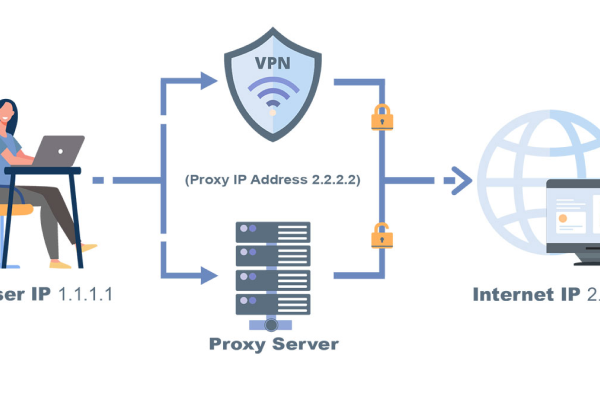
In the digital age, network privacy and security are more important than ever. Static residential proxy IP refers to a type of proxy service that can provide a fixed IP address in the process of network communication. Unlike dynamic proxy IP, static proxy IP provides a persistent and constant IP address. It is precisely because of this stability that static proxy IP plays a vital role in those situations where a stable network identity needs to be maintained for a long time, such as account maintenance in cross-border e-commerce, account cultivation in social media, network monitoring and management, brand protection, long-term data capture and other businesses. In this article, BitBrowser Proxy IP Unlimited Anti-Detection Browser introduces the precautions before using static proxy IP.
1. Detect the reliability of static proxy IP
Security and privacy protection are key points that users pay close attention to. With the help of static proxy IP, the user's original real IP address can be hidden, and then in an anonymous state in the Internet world. In this way, whether users are browsing the web, collecting data, or engaging in online transactions, their security can be significantly improved, while greatly reducing the possibility of being attacked by hackers and the outflow of personal information. Highly concealed static residential proxy IP not only relies on masking the real IP address to avoid network attacks and surveillance threats for users, but also ensures the reliability of data transmission through encryption of the communication process. For those users who urgently need to maintain a high degree of anonymity and ensure security in the network environment, the importance of this is self-evident. In order to effectively protect their own privacy and sensitive data, before deciding to use it, you should connect to the network to verify whether it has truly achieved anonymity. By importing the proxy into the BitBrowser, you can check whether its anonymity meets the standard, or you can use the anonymity detection website to complete this step.
2. Detect IP protocol and compatibility
Another important aspect that cannot be ignored is the protocol category it adapts to. The protocol category directly affects the adaptability of the static proxy IP, covering the matching with various operating systems, network conditions and applications. Common proxy protocols such as HTTP, HTTPS, SOCKS5, etc., each of which has a unique application scope and advantages. For example, HTTP proxy is more suitable for regular web browsing, while SOCKS5 proxy supports a wider range of network protocols and can cope with complex network requirements such as VoIP calls or P2P connections. Static residential proxy IPs generally support a wide range of protocols including HTTP, HTTPS, SOCKS4 and SOCKS5. A static residential proxy IP with a wide range of protocols can ensure the adaptability between existing network configurations and applications, and can carry out various network activities without hindrance, without worrying about the troubles caused by protocol mismatches. If the protocol switching function provided by the proxy service provider is smooth and natural, it can improve the efficiency of business development.
3. Detect the network speed of static proxy IP
Fast response allows users to experience smooth browsing and data interaction, and stable connection is the key to maintaining uninterrupted network connection for a long time. If the connection is unstable, it is likely to cause data transmission interruption, which may bring great risks for real-time monitoring or applications that need to maintain the same network identity for a long time. You can test it through the speed test website and try it in real business scenarios for a period of time to make sure that the availability of the proxy meets the demand effect before using it in large quantities. However, it should be noted that the network speed is not only determined by the performance of the proxy, but also by factors such as the local network status and the distance from the server. Comprehensive and objective considerations should be made.4. Static proxy IP price difference
The price of the proxy IP is not single and fixed, but is determined by many factors. Its type plays a key role. For example, the price of a high-anonymous proxy IP is usually higher than that of an ordinary anonymous proxy IP because it can provide better privacy protection and security. Stability and speed cannot be ignored. Those proxy IPs with strong stability and fast speed require more technical investment and resource support, so the price is relatively high. The reputation and service quality of the supplier will also affect the price. Well-known and excellent suppliers often set higher prices based on their good reputation and reliable technical guarantees. The purchase quantity also affects the unit price. Bulk purchases often enjoy price discounts. In addition, the supply and demand relationship in the market will also cause price fluctuations. When demand is strong and supply is limited, the price may rise, and vice versa. In short, the formation of proxy IP prices is the result of the combined effect of multiple factors, and users need to weigh them in combination with their own needs and budgets.
5. Combined with Proxy IP Unlimited Anti-Detection Browser
When dealing with multiple online accounts, it is crucial to ensure that each account will not be blocked due to association issues. In today's digital age, whether it is in the field of social media marketing, e-commerce business, or advertising work, it is very common to have many online accounts. However, with this comes a difficult problem: how can these accounts be managed efficiently to prevent them from being banned by the platform because of mutual association? Proxy IP Unlimited Anti-Detection Browser is a tool specially designed to solve this problem. Its outstanding advantage is that it can isolate different browser environments and effectively avoid mutual association between accounts.In Proxy IP Unlimited Anti-Detection Browser, each environment can personalize the browser fingerprint, which includes information on user agents, fonts, plug-ins, time zones, languages, screen resolutions, and many other aspects. This means that users can create a completely independent browser environment for each account, as if each account is operating on a brand new, unrelated device. When this feature is combined with the proxy IP, it will greatly improve the security of account management and the efficiency of operation. Users no longer have to worry about other accounts being implicated by improper operation of a certain account.
So, how can we ensure that each account uses a different IP address? After purchasing a suitable proxy service, users can set and manage a dedicated online proxy IP for each account in the proxy IP unlimited anti-detection browser. This means that no matter how many accounts the user operates at the same time, each account will use a different IP address when accessing the Internet. The advantages of this approach are obvious: first, it can effectively hide the real IP address and improve the anonymity and security of the account; second, it can avoid the risk of association caused by different accounts using the same IP address. In many cases, the platform will determine whether there is an association between accounts by analyzing the IP address. If multiple accounts use the same IP address, the risk of them being identified as associated accounts will increase significantly. By using the proxy IP unlimited anti-detection browser and proxy IP, users can easily avoid this risk.
Especially in social media marketing, e-commerce or advertising, using different IP addresses can significantly reduce the probability of platform accounts being identified and blocked. This is undoubtedly a great advantage for users who rely on multiple accounts to conduct business operations. They can conduct marketing activities more safely without worrying about being blocked by the platform due to account association. At the same time, Proxy IP Unlimited Anti-Detection Browser also provides a series of other functions, such as automated operations, batch management, etc., which further improves the work efficiency of users.
Summary:
In short, static IP plays a key role in the management of e-commerce, social media and the protection of online privacy. At the same time, in addition to static IP, tools such as BitBrowser can also provide strong support when dealing with the difficulties of managing multiple accounts. With the comprehensive and complete answers given in this article, I believe you can have a deeper understanding of static IP.