Many of us have experienced bank card fraud or problems conducting transactions from abroad. How many other vulnerabilities does this flawed card payment system conceal? Is there an alternative, but reliable and convenient replacement for it? What about a blockchain based system? To answer these questions, you should consider and compare transaction execution schemes, as well as the security and ease of use of cryptocurrency and card payment systems.
Some useful definitions:
Card network policies vary greatly from country to country.
Issuing banks are banks that create cards. Each card has the name of the bank: this is the issuer.
Acquiring banks are banks that represent merchants.
To simplify the description, I assume that the seller is the recipient and the customer is the payer.
A multisig wallet is a wallet with a special type of digital signatures that allows two or more users to sign documents together as a group.
In this comparison, I'm assuming the use of lightning wallets.
We'll dive into the differences between each aspect of networking.
It should be taken into account that most of the information on card networks is not publicly available and is not subject to disclosure. But the comparison below gives a good overview of the topic.
There are three participants in any banking transaction:
How the transaction happens:
Why is the Lightning Network being considered? Because it is based on off-chain technology. Thanks to this approach, transactions are much faster, fees are reduced, and the size of the blockchain is reduced.
This payment protocol is a network of payment channels, which are ordinary multi-SIG wallets.
What is a multisig wallet?
As a simple analogy, we can imagine a secure locker with two locks and two keys. One key is with Alice, and the other is with Boris. The only way they can open the box is to provide both of their keys at the same time, so one person cannot open the box without the other's consent.
To open a channel, the parties create a multisig wallet and send funds to it. The received amount becomes the balance of the channel and all further transactions between channel participants are carried out outside the blockchain. The channel can be closed by either party at any time, in which case the last off-chain transaction that determines the balance of the channel will be sent to the network, rendering all previous transactions invalid, since they all spend the same 'output'. Thus, we only need one transaction to open a channel and another to close it, and all intermediate transactions are carried out instantly, without being recorded in the blockchain.
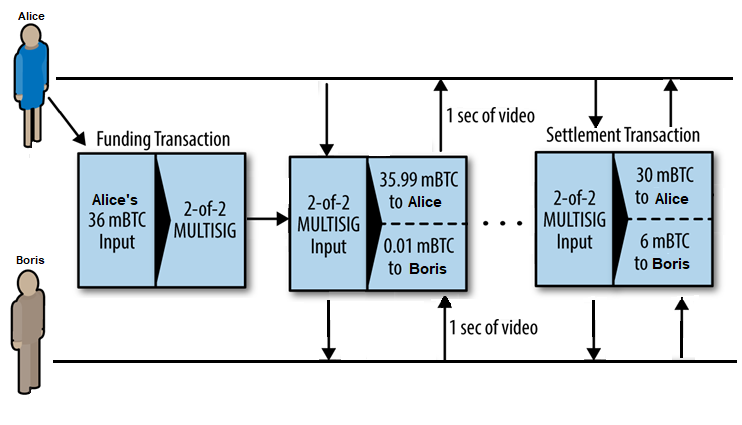
Example:
Watch video. 2 participants.
Alisa and Boris use a special program that allows them to work with both the payment channel and video. Alice runs this program in the browser, Boris on his server. The program has the functionality of a regular Bitcoin wallet and can create and sign transactions. The entire mechanism of the payment channel is hidden from the user; all they see is how the video is paid every second.
Now let's look at how this will work. To create a channel, Alice and Boris must create a multisig address with the condition two out of two. On the user’s side, the program creates a P2SH address (multi-sig wallet) and asks to top it up with the amount for 1 hour of viewing. Alice deposits 0.036 BTC into it, and this becomes the 'opening' transaction.
Once the 'opening' transaction is confirmed and the channel is open, video streaming begins. At the 1st second, the user side creates and signs a commit transaction that changes the channel balance: 0.00001 BTC to Boris and 0.03599 to Alice. The transaction uses the output of the opening transaction at 0.36 and contains the 2 new ones described just now. The program on the service side receives this transaction and also signs it, after which it sends it back along with the 1st second of the video. The parties now have a commit transaction, signed by both parties, representing the latest state of the channel, which they can push to the network if necessary.
At the 2nd second, another commit transaction is created using the same output as the previous one, and the new outputs are now 0.00002 to Boris and 0.03598 to Alice. This transaction is a payment for 2 seconds of video downloaded. Then it goes to the second side, etc.
Let's say Alice watched 10 minutes of the video and got tired of it, she stopped watching. During this time, 600 commit transactions were sent and signed (600 seconds of viewing). The last of them has 2 outputs: 0.03 for Alice and 0.006 for Boris. Alice closes the channel by sending this commit transaction to the network, making it 'close'. Thus, only 2 transactions were included in the blockchain.
Let's look at the security measures and vulnerabilities in these payment systems.
Threat: E-commerce and remote payment scams
Methods of protection:
The message is delivered directly via email, text message or mobile banking app to alert registered cardholders of suspicious activity on their account.
An additional layer of analytics, intelligence and password security to protect your e-commerce transactions.
Threat: Fake Fraud
Methods of protection:
Matches the cardholder's mobile phone location with the Visa transaction location.
Threat: Lost and Stolen Fraud
Methods of protection:
The specification supports "match-on-card" authentication, where biometric data is verified by the EMV chip card and is never disclosed or stored in any central databases. Issuers can optionally verify biometric data in their secure systems for transactions occurring in their own environments, such as their own ATMs.
Below are a few more options for possible threats with cards.
Threat: Stolen credit/debit or prepaid card details (e.g. PAN, CVV, card expiry date) can either be monetized (e.g. sold on underground market forums) or used for fraudulent payments.
Threat: Compromise between services and token service provider servers.
Token service providers (TSPs) provide token management services such as tokenization (creating a token from a credit card PAN), decontokenization (retrieving a PAN from a token store), and token data integrity verification and token initiation, as well as verification using cryptograms. If the token service provider has been compromised, attackers will likely attempt to obtain token lookup tables that provide tokens for PAN, CVV, and expiration mappings. This would be a highly valuable target for an attacker, as it would provide them with easy-to-use and monetizable information. Other possible attacks against the tagging and detagging process could include exploiting vulnerabilities in PAN extraction software used for transaction authorization, credit card identification and verification, and clearing and settlement. Attacks against domain restrictions imposed by the TSP, which may allow an attacker to bypass the time, place, and digital channel markers of the restriction.
Threat: Compromise of the payment authorization process.
One of the main threats to card issuers is the processes that verify the cardholder's data and issue payment authorization to the buyer. An internal attacker at the card issuer's bank or an external attacker with access to critical servers could attempt to bypass fraud controls (for example, changing card payment limits on authorized compromised credit cards registered for mobile payment transactions).
Below are your fraud protection options.
Example:
To ensure that funds do not get stuck in the channel, along with the opening transaction, Alice creates a refund transaction that uses the outputs of her opening transaction. First, she sends this transaction to Boris and as soon as he signs it and returns it, Alice sends the opening transaction to the network, creating a channel.
The refund transaction becomes the 1st commit transaction and its timer sets the upper limit of the life of the channel. Let's say Alice sets a timer for 30 days (4320 blocks/transactions). All subsequent commit transactions will have a shorter timer so that they can be sent to the network sooner.
Now Alice can safely open a channel, knowing that if Boris disappears, after 30 days she will be able to return her funds (if this was a bidirectional channel and Boris introduced some funds, he could also create a return transaction on his part).
Example:
Alisa and Boris create a channel. They both sent 5 bitcoins to the channel, which constitutes the initial balance of the channel. Now, instead of a standard commit transaction that they both must sign, Boris and Alice create 2 different asymmetric commit transactions.
Let's look at an example of how this works. Let's say Alice wants to send Boris 2 bitcoins. To do this, they need to update the state of the channel by creating a new commit transaction. They both create asymmetric commit transactions and before signing them, they exchange undo keys from previous commit transactions, thus 'undoing' them. In this case, Boris is interested in the latest state of the channel balance, but for Alice the previous state is more profitable (since 2 more bitcoins have not been sent). She could try to send her previous commit transaction to the network, but Boris already has the cancellation key from it and if he notices that the transaction has been sent, he will have 1000 blocks to take the entire balance of the channel (yes, 'cancellation' is not will happen automatically, Boris must notice that Alice sent her commit transaction to the network and use the key).
Thus, implementing channels using asymmetric reversible commit transactions is much more efficient since it does not limit either the lifetime of the channel or the number of transactions that can be sent to it.
Crypto wallets
Lightning wallets also provide protection for your funds.
Almost every crypto enthusiast has a fear of losing their private keys because they give full access to funds. Once lost, the keys cannot be recovered and you will no longer have control over your savings, so you will not be able to regain access to your wallet. Such wallets are called non-custodial.
On the other hand, if your private keys are stored on any wallet or third-party servers, no one guarantees protection from hacking. This is the hidden danger of every wallet service that does not provide you with private keys. These wallets are called centralized (custodial).
If someone else holds your keys, you do not have full control over your funds. When third party data gets hacked, your money is at high risk of being stolen.
Custodial
A centralized Bitcoin wallet is a wallet in which your private keys are stored by a third party. Thus, you do not have full control over your funds, which makes these wallets a questionable choice.
However, they also have some advantages :
Flaws :
For example, hackers stole about 700 BTC from one of the most famous centralized Bitcoin wallets: Blockchain.Info
The same is true for centralized exchanges, as they are also susceptible to hacker attacks. Exchanges control your assets and can freeze your account without KYC/AML confirmation (KYC - Know Your Customer, AML - Anti Money Laundering).
Non custodial
Non-custodial wallets give you complete control over your funds and provide serverless solutions in most cases. Keys are stored encrypted on the user's device and never leave it. Your money is under your control, but there is a downside. If you lose your private key, you will never be able to regain access to your funds.
Much of the security in this network stems from the fact that a financial institution must be a member to participate in it, so security is provided in a “walled garden” manner. The method of connecting to this network is not publicly disclosed.
Unlike card payment processors, Lightning is an open network.
First, it means that the specifications are publicly available (open source).
Secondly, it means that anyone can join or leave the network at any time.
This aspect of the schedule creates a unique set of challenges for Lightning, as nodes currently must be aware of the entire schedule before they can initiate a payment. Some solutions, such as trampoline payments, can help reduce this burden, especially for mobile phones that are intermittently connected to the Internet.
The concept of a graph is not common in card networks because each network member has only a few static connection points, typically to the card network's mainframe server. Card networks act like giant routers.
The participant does not need to know about other network participants. It receives every message from the central server of the payment network. For example, the acquiring bank only needs to know about the merchant they are dealing with and the payment network they are connected to (Visa, MasterCard, etc.), but they don't need to know anything about the card issuing bank.
In the card space, payments are rejected for a variety of reasons: if there are insufficient funds in the bank account, or if the payment is considered fraudulent, or, rarely, if the host is offline
In Lightning, the message flow is not structured like it is for a card system. Anyone can be a merchant, payer or intermediary.
Given the open nature of the Lightning Network, it makes extensive use of cryptography:
The purpose of PCI-DSS is to limit fraud in the industry, especially as more and more breaches occur exposing millions of card numbers.
The downside is the enormous cost of this program, which could total $24.6 billion by 2022.
Lightning, like Bitcoin, does not contain mandatory technical requirements. However, this does not mean that safety is not of utmost importance. Lightning is a hot wallet, so customers must do some work to protect their funds.
Card networks carry out settlement transactions on a net basis. The network aggregates all transactions over a period of, say, 24 hours (the period is extended on weekends), and then calculates how much each member bank owes each other.
But to simplify payments and accounting, card networks act as intermediaries, so that banks that owe money send it to the card network bank, and banks that are owed money receive it from the card network bank.
Why is it important? Because MasterCard assumes the solvency risk associated with everyone in their network.
Since MasterCard takes on the counterparty risk associated with members of their network, they want to make sure those members are well funded. But since MasterCard operates in over 160 countries, what's the best way to do this? Partnership with banks! Banks are among the most regulated organizations in the world, and using the banking system allows MasterCard and other card networks to scale across the number of countries in which they operate, while providing confidence that their members will continue to remain solvent.
This is why card payment networks are, by their very nature, “walled gardens.”
There are many other financial risks in card networks, but credit risk is worth mentioning. This risk is borne not by the card network, but by the issuer.
Lightning is very different in this regard because, for the first time in history, payments can be made instantly, without counterparty risk, around the world. Thus, there is no such thing as counterparty risk.
But instead, Lightning is exposed to technology risks. A software error could cause funds to be lost through a hack, or the error could simply make the money untrustworthy. However, since Lightning is open source, there is good reason to believe that this risk will be dramatically reduced over time.
The problem is this: in order to be able to pay, the client must have outgoing liquidity. To receive payment, the seller needs incoming liquidity. Each channel has a certain amount of money divided between incoming and outgoing liquidity. Each Lightning node carries a certain amount of liquidity: how much money can be transferred through it is based on how much money the node operator has locked in the channel.
At a high level, the problem is that the funds must be blocked.
The reason for this scam is the multiple flows of the card network. Most of this fraud occurs with either online or magnetic stripe transactions, neither of which are protected by the EVM's cryptographic components and are therefore easy to counterfeit.
The reason why Lightning can quickly and exponentially gain popularity is because it is open source and entirely software-based. Every smartphone can become a point of sale or payment device by simply installing a mobile application. This is different from cards, which still rely heavily on certain types of hardware. Even Google Pay or Apple Pay relies on an NFC receiver, requiring costly upgrades to point-of-sale systems.
Streaming payments
Think about the fact that you can pay for your electricity in real time, every few seconds while you use it.
Confidentiality, KYC (KYC – Know Your Customer) is optional
Does a restaurant have to know the name of every lunch and dinner customer? Today, everyone who pays with a card reveals their identity. Cash is still available for most places, but in countries like Sweden or China where cash is quickly disappearing, using a privacy-focused payment system is valuable. The recent protests in Hong Kong are a great example of why this is important. To avoid revealing their identities, protesters lined up to purchase transit passes in cash rather than using digital payment methods.
But there are still inefficiencies and costs underlying the apparent ease of card swiping, which amount to hundreds of billions of dollars a year. These costs are ultimately paid by the consumer.
Like Bitcoin, Lightning gives control back to individuals. But with great power comes great responsibility. Users may lose funds if they do not manage their keys correctly. And we need to learn before billions of people can confidently manage their keys.
However, the potential benefits of Lightning are enormous.
First, it allows Bitcoin to be a medium of exchange. The Bitcoin blockchain processes about 5 transactions per second, with completion times ranging from 10 to 60 minutes and costs ranging from $0.50 to $5 per transaction.
Secondly, it allows for new payment options. While some of the "obvious" ideas have been listed above, many new applications are unimaginable.
But Lightning is still a new technology, with possible implementation errors, and Visa is a time-tested system.
(c) Ivanova Natalya,
Junior Information Security Consultant,
Cross Technologies
Sources:
 www.visa.ca
www.visa.ca
Some useful definitions:
Card network policies vary greatly from country to country.
Issuing banks are banks that create cards. Each card has the name of the bank: this is the issuer.
Acquiring banks are banks that represent merchants.
To simplify the description, I assume that the seller is the recipient and the customer is the payer.
A multisig wallet is a wallet with a special type of digital signatures that allows two or more users to sign documents together as a group.
In this comparison, I'm assuming the use of lightning wallets.
We'll dive into the differences between each aspect of networking.
It should be taken into account that most of the information on card networks is not publicly available and is not subject to disclosure. But the comparison below gives a good overview of the topic.
Transactions on networks
Card payment system
How does the transaction proceed?There are three participants in any banking transaction:
- The bank accepting the payment. For example, one that serves the POS terminal in a store and to which they apply their card. This is the acquiring bank.
- Bank, your card. The bank that owns your card. This is the issuing bank.
- A payment system that acts as an intermediary channel between the banks proposed above. The most popular ones today are Visa, MasterCard, MIR.
How the transaction happens:
- We insert/attach the card into the ATM or terminal, or log into Sberbank Online.
- We swipe the card through the POS terminal. At this time, the device reads all the information available to it from the card, embedded on a magnetic tape or chip.
- Information from the device is sent in encrypted form to the acquiring bank - who owns the reader.
- The acquiring bank transmits all this data to the data processing center (DPC) of the payment system. He will be responsible for withdrawing and transferring money. The data center checks the card for fraud. By the way, such checks can be carried out by the banks themselves.
- From the data center, the information is transferred to the issuing bank, which makes final checks including checking the balance, PIN code, daily limits and debits money from the account. At the transaction endpoint, currency conversion is possible for cross-border transfers.
- After the write-off, information is distributed back: from the issuing Bank to the data center, from the data center to the acquiring bank, and the latter then transmits information about the successful transaction to you on the check.
Lightning Network
Lightning Network is a decentralized off-chain technology that allows tens of thousands of transactions per second, as Visa allows, for example.Why is the Lightning Network being considered? Because it is based on off-chain technology. Thanks to this approach, transactions are much faster, fees are reduced, and the size of the blockchain is reduced.
This payment protocol is a network of payment channels, which are ordinary multi-SIG wallets.
What is a multisig wallet?
As a simple analogy, we can imagine a secure locker with two locks and two keys. One key is with Alice, and the other is with Boris. The only way they can open the box is to provide both of their keys at the same time, so one person cannot open the box without the other's consent.
To open a channel, the parties create a multisig wallet and send funds to it. The received amount becomes the balance of the channel and all further transactions between channel participants are carried out outside the blockchain. The channel can be closed by either party at any time, in which case the last off-chain transaction that determines the balance of the channel will be sent to the network, rendering all previous transactions invalid, since they all spend the same 'output'. Thus, we only need one transaction to open a channel and another to close it, and all intermediate transactions are carried out instantly, without being recorded in the blockchain.
Example:
Watch video. 2 participants.
Alisa and Boris use a special program that allows them to work with both the payment channel and video. Alice runs this program in the browser, Boris on his server. The program has the functionality of a regular Bitcoin wallet and can create and sign transactions. The entire mechanism of the payment channel is hidden from the user; all they see is how the video is paid every second.
Now let's look at how this will work. To create a channel, Alice and Boris must create a multisig address with the condition two out of two. On the user’s side, the program creates a P2SH address (multi-sig wallet) and asks to top it up with the amount for 1 hour of viewing. Alice deposits 0.036 BTC into it, and this becomes the 'opening' transaction.
Once the 'opening' transaction is confirmed and the channel is open, video streaming begins. At the 1st second, the user side creates and signs a commit transaction that changes the channel balance: 0.00001 BTC to Boris and 0.03599 to Alice. The transaction uses the output of the opening transaction at 0.36 and contains the 2 new ones described just now. The program on the service side receives this transaction and also signs it, after which it sends it back along with the 1st second of the video. The parties now have a commit transaction, signed by both parties, representing the latest state of the channel, which they can push to the network if necessary.
At the 2nd second, another commit transaction is created using the same output as the previous one, and the new outputs are now 0.00002 to Boris and 0.03598 to Alice. This transaction is a payment for 2 seconds of video downloaded. Then it goes to the second side, etc.
Let's say Alice watched 10 minutes of the video and got tired of it, she stopped watching. During this time, 600 commit transactions were sent and signed (600 seconds of viewing). The last of them has 2 outputs: 0.03 for Alice and 0.006 for Boris. Alice closes the channel by sending this commit transaction to the network, making it 'close'. Thus, only 2 transactions were included in the blockchain.

Let's look at the security measures and vulnerabilities in these payment systems.
Threats and security in payment systems
Visa Security
Threat: E-commerce and remote payment scams
Methods of protection:
- Tokenization of payments.
- Alert on consumer transactions.
The message is delivered directly via email, text message or mobile banking app to alert registered cardholders of suspicious activity on their account.
- Dynamic password code.
- Analytics and password security check.
An additional layer of analytics, intelligence and password security to protect your e-commerce transactions.
- Encryption during transaction processing.
- Device identification to recognize suspicious transactions.
Threat: Fake Fraud
Methods of protection:
- EMV chip.
- Geolocation.
Matches the cardholder's mobile phone location with the Visa transaction location.
- Marking of chip cards.
- Consumer Transaction Alerts.
Threat: Lost and Stolen Fraud
Methods of protection:
- Biometrics for owner identification.
The specification supports "match-on-card" authentication, where biometric data is verified by the EMV chip card and is never disclosed or stored in any central databases. Issuers can optionally verify biometric data in their secure systems for transactions occurring in their own environments, such as their own ATMs.
- Behavior analytics.
Below are a few more options for possible threats with cards.
Threat: Stolen credit/debit or prepaid card details (e.g. PAN, CVV, card expiry date) can either be monetized (e.g. sold on underground market forums) or used for fraudulent payments.
Threat: Compromise between services and token service provider servers.
Token service providers (TSPs) provide token management services such as tokenization (creating a token from a credit card PAN), decontokenization (retrieving a PAN from a token store), and token data integrity verification and token initiation, as well as verification using cryptograms. If the token service provider has been compromised, attackers will likely attempt to obtain token lookup tables that provide tokens for PAN, CVV, and expiration mappings. This would be a highly valuable target for an attacker, as it would provide them with easy-to-use and monetizable information. Other possible attacks against the tagging and detagging process could include exploiting vulnerabilities in PAN extraction software used for transaction authorization, credit card identification and verification, and clearing and settlement. Attacks against domain restrictions imposed by the TSP, which may allow an attacker to bypass the time, place, and digital channel markers of the restriction.
Threat: Compromise of the payment authorization process.
One of the main threats to card issuers is the processes that verify the cardholder's data and issue payment authorization to the buyer. An internal attacker at the card issuer's bank or an external attacker with access to critical servers could attempt to bypass fraud controls (for example, changing card payment limits on authorized compromised credit cards registered for mobile payment transactions).
Lightning Security
Since fraud is not a weak point of the Lightning Network due to the blockchain at its core and the relative newness of the technology, there are two types of fraud: sending a better transaction to the network and getting funds stuck with the opening transaction.Below are your fraud protection options.
- Using timers in commit transactions works with Smart Contract (HTLC).
Example:
To ensure that funds do not get stuck in the channel, along with the opening transaction, Alice creates a refund transaction that uses the outputs of her opening transaction. First, she sends this transaction to Boris and as soon as he signs it and returns it, Alice sends the opening transaction to the network, creating a channel.
The refund transaction becomes the 1st commit transaction and its timer sets the upper limit of the life of the channel. Let's say Alice sets a timer for 30 days (4320 blocks/transactions). All subsequent commit transactions will have a shorter timer so that they can be sent to the network sooner.
Now Alice can safely open a channel, knowing that if Boris disappears, after 30 days she will be able to return her funds (if this was a bidirectional channel and Boris introduced some funds, he could also create a return transaction on his part).
- Using the undo key.
Example:
Alisa and Boris create a channel. They both sent 5 bitcoins to the channel, which constitutes the initial balance of the channel. Now, instead of a standard commit transaction that they both must sign, Boris and Alice create 2 different asymmetric commit transactions.
Let's look at an example of how this works. Let's say Alice wants to send Boris 2 bitcoins. To do this, they need to update the state of the channel by creating a new commit transaction. They both create asymmetric commit transactions and before signing them, they exchange undo keys from previous commit transactions, thus 'undoing' them. In this case, Boris is interested in the latest state of the channel balance, but for Alice the previous state is more profitable (since 2 more bitcoins have not been sent). She could try to send her previous commit transaction to the network, but Boris already has the cancellation key from it and if he notices that the transaction has been sent, he will have 1000 blocks to take the entire balance of the channel (yes, 'cancellation' is not will happen automatically, Boris must notice that Alice sent her commit transaction to the network and use the key).
Thus, implementing channels using asymmetric reversible commit transactions is much more efficient since it does not limit either the lifetime of the channel or the number of transactions that can be sent to it.
Crypto wallets
Lightning wallets also provide protection for your funds.
Almost every crypto enthusiast has a fear of losing their private keys because they give full access to funds. Once lost, the keys cannot be recovered and you will no longer have control over your savings, so you will not be able to regain access to your wallet. Such wallets are called non-custodial.
On the other hand, if your private keys are stored on any wallet or third-party servers, no one guarantees protection from hacking. This is the hidden danger of every wallet service that does not provide you with private keys. These wallets are called centralized (custodial).
If someone else holds your keys, you do not have full control over your funds. When third party data gets hacked, your money is at high risk of being stolen.
Custodial
A centralized Bitcoin wallet is a wallet in which your private keys are stored by a third party. Thus, you do not have full control over your funds, which makes these wallets a questionable choice.
However, they also have some advantages :
- You can manage your funds very quickly and anytime you have an Internet connection;
- There is no chance of losing your private key and losing access to your money.
Flaws :
- A third party has control over your money;
- Your crypto coins may be confiscated by court order;
- If your wallet is hacked, your coins may go missing.
For example, hackers stole about 700 BTC from one of the most famous centralized Bitcoin wallets: Blockchain.Info
The same is true for centralized exchanges, as they are also susceptible to hacker attacks. Exchanges control your assets and can freeze your account without KYC/AML confirmation (KYC - Know Your Customer, AML - Anti Money Laundering).
Non custodial
Non-custodial wallets give you complete control over your funds and provide serverless solutions in most cases. Keys are stored encrypted on the user's device and never leave it. Your money is under your control, but there is a downside. If you lose your private key, you will never be able to regain access to your funds.
Comparison
Visa Inc., the payment network operator, has an agreement with each member of the Visa network.Much of the security in this network stems from the fact that a financial institution must be a member to participate in it, so security is provided in a “walled garden” manner. The method of connecting to this network is not publicly disclosed.
Unlike card payment processors, Lightning is an open network.
First, it means that the specifications are publicly available (open source).
Secondly, it means that anyone can join or leave the network at any time.
Communications center
Lightning has the concept of payment schedules, which is how nodes connect to each other. Using graph theory terminology, nodes are vertices and channels are edges.This aspect of the schedule creates a unique set of challenges for Lightning, as nodes currently must be aware of the entire schedule before they can initiate a payment. Some solutions, such as trampoline payments, can help reduce this burden, especially for mobile phones that are intermittently connected to the Internet.
The concept of a graph is not common in card networks because each network member has only a few static connection points, typically to the card network's mainframe server. Card networks act like giant routers.
The participant does not need to know about other network participants. It receives every message from the central server of the payment network. For example, the acquiring bank only needs to know about the merchant they are dealing with and the payment network they are connected to (Visa, MasterCard, etc.), but they don't need to know anything about the card issuing bank.
Isolation
In Lightning, payments will be rejected if, for example, there is not enough liquidity in any channel along the way.In the card space, payments are rejected for a variety of reasons: if there are insufficient funds in the bank account, or if the payment is considered fraudulent, or, rarely, if the host is offline
In Lightning, the message flow is not structured like it is for a card system. Anyone can be a merchant, payer or intermediary.
Cryptography
The card system uses legacy cryptography, unlike Lightning. Online transactions are especially not secure.Given the open nature of the Lightning Network, it makes extensive use of cryptography:
- Payments are currently based on the SHA256 hash function;
- Accounts are signed using an elliptic curve (same as for Bitcoin, secp256k1);
- Nodes are identified by public keys using the same secp256k1;
- Communication between each node is encrypted using ChaCha20 and handshakes are performed using noise protocol;
- Onion routing reduces the chances of recognizing the sender and recipient.
Technical Compliance
To help prevent fraud, the card industry has worked with the Payment Card Industry (PCI) Security Standards Council to develop the PCI-DSS compliance program. The goal is to ensure that every organization on earth that processes card transactions was bound by strict rules that, for example, ensure that card numbers are not stored in clear text and are only accessible to people who have business reason for accessing these figures, etc.The purpose of PCI-DSS is to limit fraud in the industry, especially as more and more breaches occur exposing millions of card numbers.
The downside is the enormous cost of this program, which could total $24.6 billion by 2022.
Lightning, like Bitcoin, does not contain mandatory technical requirements. However, this does not mean that safety is not of utmost importance. Lightning is a hot wallet, so customers must do some work to protect their funds.
Currency
The important point is that there is no overlap between the currencies that card networks operate and the currencies that the Lightning Network can handle. In other words, card networks are not located in cryptography, and crypto networks cannot “interoperate” with card networks. Cards that allow you to spend crypto today do currency conversion outside the card network, typically by selling BTC and "loading" US dollars.Financial risks
Liquidity and solvency are key aspects.Card networks carry out settlement transactions on a net basis. The network aggregates all transactions over a period of, say, 24 hours (the period is extended on weekends), and then calculates how much each member bank owes each other.
But to simplify payments and accounting, card networks act as intermediaries, so that banks that owe money send it to the card network bank, and banks that are owed money receive it from the card network bank.
Why is it important? Because MasterCard assumes the solvency risk associated with everyone in their network.
Since MasterCard takes on the counterparty risk associated with members of their network, they want to make sure those members are well funded. But since MasterCard operates in over 160 countries, what's the best way to do this? Partnership with banks! Banks are among the most regulated organizations in the world, and using the banking system allows MasterCard and other card networks to scale across the number of countries in which they operate, while providing confidence that their members will continue to remain solvent.
This is why card payment networks are, by their very nature, “walled gardens.”
There are many other financial risks in card networks, but credit risk is worth mentioning. This risk is borne not by the card network, but by the issuer.
Lightning is very different in this regard because, for the first time in history, payments can be made instantly, without counterparty risk, around the world. Thus, there is no such thing as counterparty risk.
But instead, Lightning is exposed to technology risks. A software error could cause funds to be lost through a hack, or the error could simply make the money untrustworthy. However, since Lightning is open source, there is good reason to believe that this risk will be dramatically reduced over time.
Liquidity
For Lightning, liquidity is likely the biggest hurdle that needs to be overcome before the network can truly take off.The problem is this: in order to be able to pay, the client must have outgoing liquidity. To receive payment, the seller needs incoming liquidity. Each channel has a certain amount of money divided between incoming and outgoing liquidity. Each Lightning node carries a certain amount of liquidity: how much money can be transferred through it is based on how much money the node operator has locked in the channel.
At a high level, the problem is that the funds must be blocked.
Fraud
If liquidity is Lightning's Achilles heel, Fraud is card networks' weakness. According to the Nilson Report, fraud prevention operations are very expensive, but fraud itself is in the $100 billion range. This is approximately 0.07% of card transaction volume.The reason for this scam is the multiple flows of the card network. Most of this fraud occurs with either online or magnetic stripe transactions, neither of which are protected by the EVM's cryptographic components and are therefore easy to counterfeit.
Adoption and use cases
Although it could be argued that the potential use of Lightning today is still speculative, given the fact that there are very few merchants accepting Lightning today, compared to the 46 million merchants accepting the 3.3 billion cards issued for the Visa network alone.The reason why Lightning can quickly and exponentially gain popularity is because it is open source and entirely software-based. Every smartphone can become a point of sale or payment device by simply installing a mobile application. This is different from cards, which still rely heavily on certain types of hardware. Even Google Pay or Apple Pay relies on an NFC receiver, requiring costly upgrades to point-of-sale systems.
Streaming payments
Think about the fact that you can pay for your electricity in real time, every few seconds while you use it.
Confidentiality, KYC (KYC – Know Your Customer) is optional
Does a restaurant have to know the name of every lunch and dinner customer? Today, everyone who pays with a card reveals their identity. Cash is still available for most places, but in countries like Sweden or China where cash is quickly disappearing, using a privacy-focused payment system is valuable. The recent protests in Hong Kong are a great example of why this is important. To avoid revealing their identities, protesters lined up to purchase transit passes in cash rather than using digital payment methods.
Conclusion
Card networks such as Visa are very mature and, from a consumer perspective, perform very well.But there are still inefficiencies and costs underlying the apparent ease of card swiping, which amount to hundreds of billions of dollars a year. These costs are ultimately paid by the consumer.
Like Bitcoin, Lightning gives control back to individuals. But with great power comes great responsibility. Users may lose funds if they do not manage their keys correctly. And we need to learn before billions of people can confidently manage their keys.
However, the potential benefits of Lightning are enormous.
First, it allows Bitcoin to be a medium of exchange. The Bitcoin blockchain processes about 5 transactions per second, with completion times ranging from 10 to 60 minutes and costs ranging from $0.50 to $5 per transaction.
Secondly, it allows for new payment options. While some of the "obvious" ideas have been listed above, many new applications are unimaginable.
But Lightning is still a new technology, with possible implementation errors, and Visa is a time-tested system.
(c) Ivanova Natalya,
Junior Information Security Consultant,
Cross Technologies
Sources:
Credit Card Purchase Protection | Visa
Learn about our Zero Liability policy and the layers of security Visa has developed to help protect you from unauthorized credit card purchases.
