Man
Professional
- Messages
- 3,223
- Reaction score
- 1,199
- Points
- 113
1. Antifraud Riskified
Basically, fraud detectors work on the same principle, some have very bulky filter markers, while others have smaller ones. Somewhere the fraud points are set by the support staff themselves, and somewhere everything is done automatically. And also everyone has different machine learning (there will be a separate post about this).
Connection via API, there are also additional modules-extensions that are installed via the panel.
Getting to know the panel:

Riskified - even this fraud protection likes to cancel orders for regular users.

There are no fraud points here either - There are no fraud points shown here, only indicators.
Geo: Various explicit and implicit geographic data points in order and the distances between them.
Identity: Online presence and identity based on data points such as email address, names, and phone numbers, and the relationships between them.
Behavior: Shopper checkout behavior, including speed, basket contents, and shipping methods.
Network: Technology characteristics, including internet connection and devices used by the shopper when placing an order.
Linking: The links between all order items and each transaction on the Riskified network.
Even ordinary users are given a decline )))

Recommendations: Check the IP for cleanliness, take old mails (additionally checking for risks. Behave as slowly as possible like an ordinary person who came to choose a product in a shop. Well, you can think of the rest of the recommendations from the indicators above.
2. Antifraud NoFraud
NoFraud - The fraud detector itself is weaker. In this detector, all orders are sent for verification automatically, so we have no way of knowing how many points we got. The approximate time for checking orders is up to 24 hours.
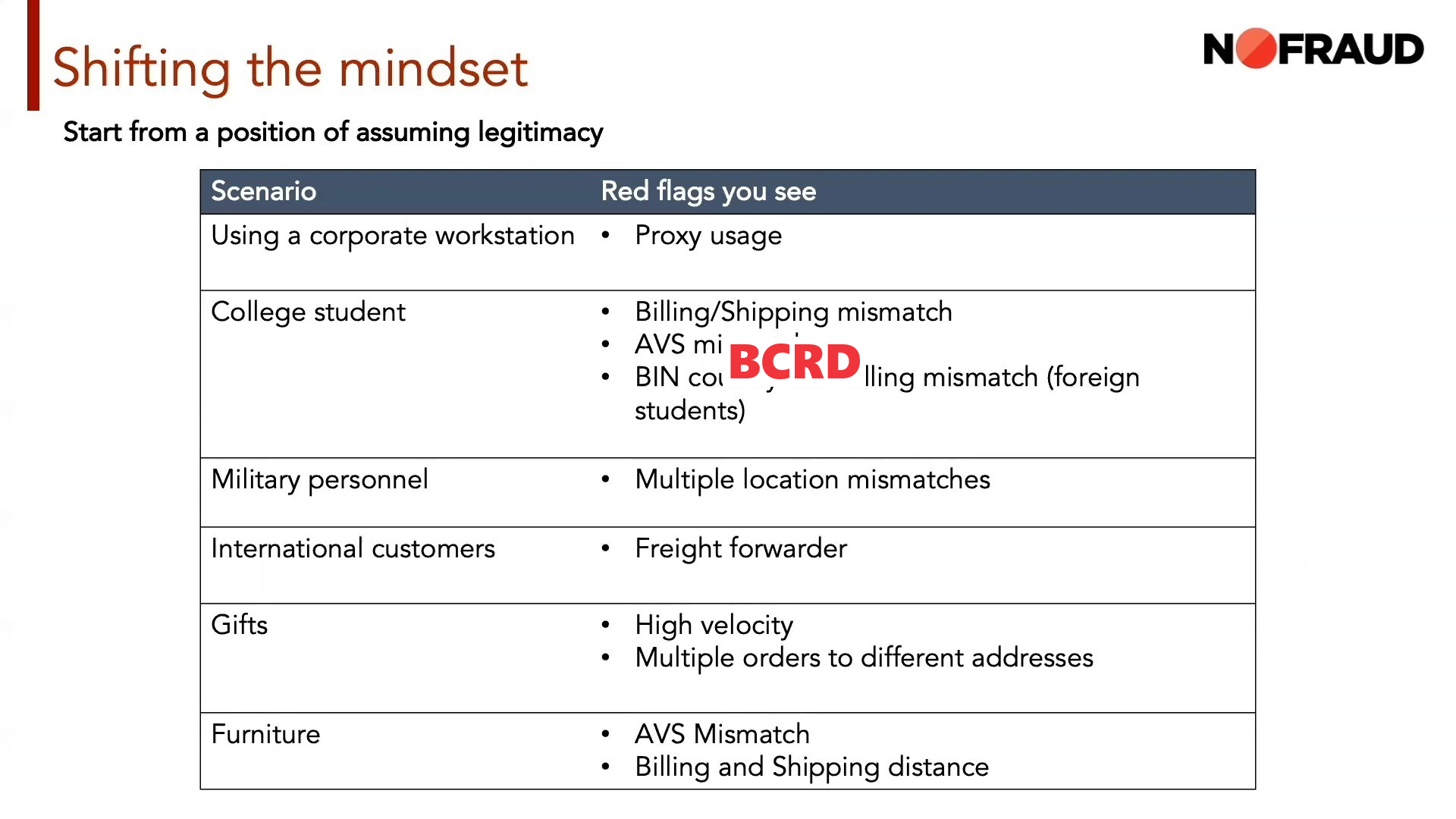
What is collected and analyzed:

Automatic risk scale:

Visual representation of the visualization/capture workflow - forms a flow chart.
Trust factors:
These are elements of an order that generally indicate that it is valid and safe to ship:
- The device is in close proximity to the billing address. This indicates that the customer's geolocation was near the address on file with the cardholder's bank, indicating that the actual cardholder (or their close associate/family member) placed the order.
- Observed normal device activity: The buyer's purchasing activity did not match the usual indicators of fraud (e.g. use of a proxy device, close proximity to the billing address, etc.).
- Transaction placed on first payment attempt: A common sign of fraud is when a customer makes multiple payment attempts before the order is finally approved. This trust factor indicates that this order was successfully placed on the first payment attempt.
- Card Verification Value (CVV) Match: This indicates that the CVV code provided by the customer matches the one on file with the cardholder's bank.
- Shipping to cardholder's address. This indicates that NoFraud was able to verify that the shipping address belongs to the actual cardholder and that the order is not being sent to an unconfirmed address.
- The email address has been active for a significant period of time: Scammers will typically create new email addresses for the specific purpose of placing a (fraudulent) order. This indicates that the email address used in that order has been in existence for a significant period of time.
- Customer has a long history of using the payment method: This customer has previously used the same payment method for past non-fraudulent orders.
- Issuing Bank Matches Billing Country: (mainly for orders outside the US) this indicates that the credit card was issued in the same country the order is being shipped to.
- Address Verification System (AVS) Match: The billing address provided by the customer exactly matches the address on file with the cardholder's bank.
Risk Factors:
These are elements of an order that typically indicate it may be fraudulent or require additional verification before shipping:
- Risky device activity detected: The critical characteristics of the device used to place the order raise suspicions (e.g. the buyer is hiding device information, the device's geolocation is far from the cardholder's address, etc.).
- Irregular device activity detected: Some characteristics of the device used to place the order are unusual or unexpected.
- Card issuing bank does not match billing country. The bank the customer uses is located in a country that does not match the country listed in their billing address.
- Proxy server detected: The client is using a proxy program to mask device information.
- IP Geolocation is Remote from Billing Address: The customer placed an order from a device located far from the cardholder's address.
- Address Verification System (AVS) Partial Match: The billing address provided by the customer only partially matches the cardholder's address on file with their issuing bank (e.g., zip code matches, but mailing address does not match).
- Total Address Verification System (AVS) Mismatch: The billing address provided by the customer does not match the cardholder's address on file with the issuing bank.
- Shipping address is different from the address confirmed by AVS: The shipping address is different from the address confirmed by the cardholder.
- Expedited shipping requested: Often scammers will request the expedited shipping option because a) they are not paying for the item/shipping and have nothing to lose, and b) they believe it will give the seller less time to recognize the scam and re-route or prevent the order from being delivered to them.
- Multiple card attempts in a short period of time: Many scammers will attempt to use multiple cards for the same order until one is approved. This indicates that the customer has made multiple attempts to pay with different cards before the order was successfully placed.
- Shipping to a Forwarder : Orders shipped to a forwarder are generally considered to be more risky than orders shipped directly to the customer/cardholder's home address.
- The email address has a bit of history: Fraudsters often create new email addresses (especially if they do not have access to the actual cardholder's email account) for the specific purpose of placing fraudulent orders. So a completely new email address is considered a risk factor.
Recommendations: You can work from any device (provided there is only one protection), check IP, email, DNS in advance. Check billing on CC. Carefully check the data when entering.
3. Antifraud Fraud Forter
Today we will briefly consider the fraud detector Forter. What parameters does it pay attention to, how to adjust? Where on which shops is it installed? Etc.

Here is an example of a shop. The Wapalayzer extension shows us that there are 3 protections at once. But you shouldn't be convinced that this is really so. We haven't looked at the code itself through the f12 sniffer or the hhtp tracker or fidler software yet.
- Forter - we'll analyze it below. PremeterX - I won't consider it, if you're interested in what it is, you can analyze it yourself.
- Onetrust - Here the protection is based on cookies, you are identified with other sites, etc.

Makes schedules - which delivery services you use.

Here the user hid his identity. Manipulated his IP address so that it matched the CC (stolen, bought in the CC shop) and changed the geo so that it was close to the address of the CC holder. That is, the nearest socks under the CC zip. There is also a connection here that this IP has already been seen on the network (fraud detector forter) But there is also one solution - calling the shop.
You can hire a caller after the order, so to speak, for confirmation. And then the SAPs in the shop will be able to make a note - that is, put the order through manually.
They check the IP - check the IP for cleanliness.
Mail - there are of course hidden markers also, what social networks the soap is registered to where it is not registered.
Billing location. Of course, shipping here = billing
But the device - the IP of another city - this is immediately visible. It is better to take the IP directly from the same zip.
AVS - it is here. It passed on AVS.
The fraud detector itself works in real time. Machine learning changes to different parameters each time.

These are transaction details - but here, as in riskfield, there is a connection between transactions, if this person has already appeared somewhere in the forter network - then your order will be cancelled. And it works across the entire network where there is a forter.

The red dots are rejected transactions that were already in their network.

Here are the parameters of communication.
Name, device, billing, shipping, behavioral factors, IP, etc. - everything is taken into account.
There is a hidden parameter - mail reputation check.
That is, to bypass this detector we need:
High rep mail, clean IP exactly under zip SS. It is also better to indicate phone numbers KH (you can take old ones from BG)
Behavior in the shop, in the browser.
Device (some antidetects are more likely to be detected, you need to try)
I met in shops where there is Cashstar merch, giftcards, wgiftcard, gap and other complex merch, and also saw in intranets (simple shops).

