Mutt
Professional
- Messages
- 1,459
- Reaction score
- 1,105
- Points
- 113
A modern metropolis is a gigantic and complex organism, permeated through and through with information flows. Information makes it more efficient, but at the same time creates potential privacy problems for its inhabitants, who are often unaware of surveillance.
This article is about what data is collected, in what ways and how to protect yourself from it.
Why bother with your privacy and anonymity at all? I often hear statements like "I have no one to hide from" or "I have nothing to fear."
There are three main reasons:
1. Information
Who owns the information - he owns the world. The custodian of information (for example, the state or a private data operator) has an additional leverage over a person, which can be used at the right time. It is extremely important if you are a political or social activist, or if your business is of interest to someone.
2. Human factor
No matter how the data operator assures you that all data is completely safe, people work with this data in one way or another, and sometimes these people do not disdain illegal part-time work - the so-called "breakthrough". This is how a black market for data arises, where you can now buy information for almost any person. Anyone can do this, be it another scammer or a neighbor who harbors a grudge against you.
3. Identification errors
If the face recognition system mistakes you for a wanted person, you are likely to get into trouble - at least, you will be detained. Despite the extremely small percentage of false recognitions, precedents happen periodically.
This article describes only the methods of the so-called global or mass surveillance, which is directed against an unlimited number of people, and does not consider methods of targeted surveillance. If youparanoid follow all the recommendations, this does not mean that you are not being followed at all, you may be of targeted interest to someone.
Go!
Chapter 1. Face recognition systems
At the moment, one of the largest face recognition systems operates in Moscow, based on almost 200 thousand cameras connected to a single system.
Cameras are installed on streets, crowded places, courtyards, entrances, metro stations and even turnstiles.
Many of them now have a face recognition system, the main developer of which is the Russian company NtechLab, which became famous in its time for the FindFace project - a site for finding people in social networks by photography, which was closed for public access in 2018. In addition to NTechLab, algorithms from Visionlabs are also used.
The algorithm is based on a neural network.
Since FindFace used a database of faces downloaded from Vkontakte several years ago, it is logical to assume that this database is now also used in the Moscow face recognition system. So if you've ever uploaded your photo to your profile, then it could have ended up in their dataset.
In addition, there are other databases that can be used to match your face with your personal data. One of these bases is the Passport system. It contains scanned photographs that you submitted with the application form for obtaining a passport of a citizen of the Russian Federation. Curiously, there are photographs in this database even from the 90s (if you then received a passport).
An example of an entry in this system

It is not known whether the Moscow face recognition system is connected to this database, but such a possibility certainly exists.
It is reliably known that the Moscow face recognition system works on the following cameras:
Installed on turnstiles ("turrets" with an indicator at the face level). The installation of these cameras began in 2019 from the Oktyabrskoye Pole station; now they are equipped with all stations of the Moscow metro. These cameras work in conjunction with tablets at police stations at stations - a notification is sent there if a wanted person is found.
They look like this:


Installed on turnstiles at the entrance and exit.
Access cameras (reminiscent of a video intercom, equipped with IR illumination for working at night, they are also usually attached at face level). In addition to entrances, they are found at the entrances to some public institutions (schools, clinics).
There is an official map of their locations.
These cameras come in three flavors from different manufacturers: Beward, Hikvision, and Dahua.
They look like this:

For some reason, two cameras from different manufacturers were installed at once.
The doors of some subway cars. In the summer of 2020, a tender was announced to install cameras with facial recognition on Thursdays for all subway cars. Cameras are installed near each doorway, either above the doors or on the side of the opening.
Like this

The lower chamber is, in this case, most likely a connection with the driver (intercom), but in nature there were also cameras installed in the same way.
The cameras themselves are not engaged in face recognition - they only broadcast the video stream, recognition takes place centrally, on special servers occupying 19 racks in the data center of the ECDC. The total storage capacity was 28 Petabytes for 2019.
There are also servers that host databases and front-end systems.
This is how the web interface for accessing the data of the face recognition system looks like
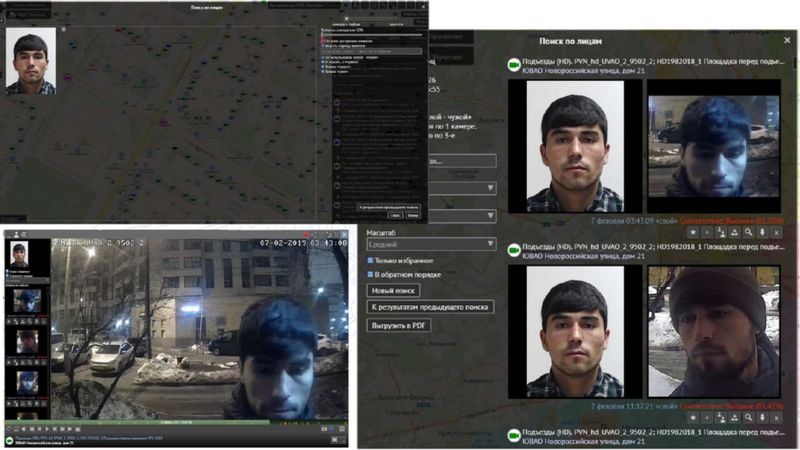
The Moscow face recognition system not only recognizes faces, but also stores information in a database about the place and time of a face's appearance - in fact, all movements. The system knows when you enter your entrance or the subway, who you do it with and how often. Based on this data, the friend-or-foe function works (on access cameras). The data is available for at least 30 days and is freely available on the darknet.
An example of displaying the results of a query about human movements

Of course, this system also has advantages - for example, it helps to detain persons on the federal wanted list. But is it worth depriving everyone else of privacy for the sake of this? Already today, this system is used to persecute public activists and political figures (you can read about different cases here). In addition, using the face recognition system, they are looking for participants in uncoordinated actions - the system even has a separate category for active participants in rallies. And in the spring of 2020, the system was used to control quarantined Muscovites, and fines came even for taking out the garbage if a person got into the lens of an entrance video camera.
What to do?
Sign the petition. Just Roskomsvoboda was created by the project BanCam, the purpose of which is to ban the use of face recognition technology. I advise you to take a look at the site - there are many interesting materials on the topic.
In the meantime, the technology is still in use, you can do a few simple things that will greatly complicate its work:
Chapter 2. Mobile communications
The advent of mobile phones not only simplified communication, but also became a great gift for the intelligence services. It became possible not only to track the movements of a contact person, but also to get a list of people who were once at the right moment in the past within the line of sight of a particular cell tower.
Location accuracy depends on the density of cell towers (or more scientifically, base stations, BSs). Outside the city, the density is low, and the accuracy can be up to several (tens) kilometers, and in the city center, on the contrary, with a large number of towers, it is in the area of several hundred meters. There are also more accurate methods for determining the location (the so-called Trilateration - determining the distance by the time the signal travels between three points), but they already require active intervention in the operator's network, and fortunately are not massive in nature, but are used in a targeted manner.
A mobile operator keeps a log of his movements in a special database for each subscriber, namely CellID (BS identifier) and the time of presence in the reception area of this station. The storage period for such data (probably) can be from six months or more.
Now in Russia they can pass a law according to which it will be possible to obtain such data even without a court decision, which means thatpenetrations will fall in price all and sundry will have access to them.
What to do?[/BHEADING]
Ideally, do not use a mobile phone. But for many, this option is unacceptable, so the trade-offs will be listed below.
Chapter 3. Payment systems
What to do?
Try to use non-cash payments only where you cannot do without them, no matter how convenient it may seem. Well, if you really want to, I recommend keeping a supply of cash in a safe place in case of blocking or losing the card.
Chapter 4. Transport
It is very difficult to travel anonymously these days, especially when it comes to long distance travel. And if with international crossings (flights) everything is obvious - border control is required, then with intercity movements there are less obvious ways of tracking.
In the spring of 2020, at the height of the coronavirus pandemic, electronic passes were introduced in Moscow. As conceived by the creators, transport could only be used if the transport card was tied to a pass, which again contained the passport data of its owner. But as usual, something went wrong, and many Troika cards that were not tied to passes worked, but tied social cards did the opposite.
So if you tied the card to this pass, hand it over to the cashier. I also recommend not to tie the transport card to the phone number, top up only in cash and change it periodically.
Chapter 5. Other methods of surveillance
Tracking via Wi-Fi or Bluetooth.
There is a Wi-Fi network for transport in Moscow. In order to use this network, you need to bind a phone number to the device. The network operator actively cooperates with the Moscow authorities and advertising companies.
Data is collected about the actions of users on the network, the services used, as well as geolocation.
Moscow authorities plan to start monitoring citizens through special software and hardware systems that will collect MAC addresses of devices that have appeared in their area of operation. It is not entirely clear how they are going to do this, if MAC randomization is enabled by default in modern versions of Android and IOS.
In addition to city authorities, private companies, such as 2wifi, also collect geolocation data via Wi-Fi .
What to do?
Do not use the city Wi-Fi network, since mobile Internet now works at all subway stations and even in some sections.
P.S
There is always a balance between privacy and comfort. It is impossible to get them in full at the same time, you have to sacrifice one thing for the sake of the other. It is important to observe the measure that everyone determines for himself.
The megalopolis, which is described in the article, is Moscow, however, the article may be relevant for other cities as well.
All information in this article is collected from open sources and articles, links to which are given in the text.
For those who have read to the end
There is an Easter egg in the first picture, who found it
If you know something that is not in this article, write to the comments, and I will try to supplement it.
Protect your privacy and do not break the law.
habrastorage.org
This article is about what data is collected, in what ways and how to protect yourself from it.
Why bother with your privacy and anonymity at all? I often hear statements like "I have no one to hide from" or "I have nothing to fear."
There are three main reasons:
1. Information
Who owns the information - he owns the world. The custodian of information (for example, the state or a private data operator) has an additional leverage over a person, which can be used at the right time. It is extremely important if you are a political or social activist, or if your business is of interest to someone.
2. Human factor
No matter how the data operator assures you that all data is completely safe, people work with this data in one way or another, and sometimes these people do not disdain illegal part-time work - the so-called "breakthrough". This is how a black market for data arises, where you can now buy information for almost any person. Anyone can do this, be it another scammer or a neighbor who harbors a grudge against you.
3. Identification errors
If the face recognition system mistakes you for a wanted person, you are likely to get into trouble - at least, you will be detained. Despite the extremely small percentage of false recognitions, precedents happen periodically.
This article describes only the methods of the so-called global or mass surveillance, which is directed against an unlimited number of people, and does not consider methods of targeted surveillance. If youparanoid follow all the recommendations, this does not mean that you are not being followed at all, you may be of targeted interest to someone.
Go!
Chapter 1. Face recognition systems
At the moment, one of the largest face recognition systems operates in Moscow, based on almost 200 thousand cameras connected to a single system.
Cameras are installed on streets, crowded places, courtyards, entrances, metro stations and even turnstiles.
Many of them now have a face recognition system, the main developer of which is the Russian company NtechLab, which became famous in its time for the FindFace project - a site for finding people in social networks by photography, which was closed for public access in 2018. In addition to NTechLab, algorithms from Visionlabs are also used.
The algorithm is based on a neural network.
Since FindFace used a database of faces downloaded from Vkontakte several years ago, it is logical to assume that this database is now also used in the Moscow face recognition system. So if you've ever uploaded your photo to your profile, then it could have ended up in their dataset.
In addition, there are other databases that can be used to match your face with your personal data. One of these bases is the Passport system. It contains scanned photographs that you submitted with the application form for obtaining a passport of a citizen of the Russian Federation. Curiously, there are photographs in this database even from the 90s (if you then received a passport).
An example of an entry in this system

It is not known whether the Moscow face recognition system is connected to this database, but such a possibility certainly exists.
It is reliably known that the Moscow face recognition system works on the following cameras:
Installed on turnstiles ("turrets" with an indicator at the face level). The installation of these cameras began in 2019 from the Oktyabrskoye Pole station; now they are equipped with all stations of the Moscow metro. These cameras work in conjunction with tablets at police stations at stations - a notification is sent there if a wanted person is found.
They look like this:


Installed on turnstiles at the entrance and exit.
Access cameras (reminiscent of a video intercom, equipped with IR illumination for working at night, they are also usually attached at face level). In addition to entrances, they are found at the entrances to some public institutions (schools, clinics).
There is an official map of their locations.
These cameras come in three flavors from different manufacturers: Beward, Hikvision, and Dahua.
They look like this:

For some reason, two cameras from different manufacturers were installed at once.
The doors of some subway cars. In the summer of 2020, a tender was announced to install cameras with facial recognition on Thursdays for all subway cars. Cameras are installed near each doorway, either above the doors or on the side of the opening.
Like this

The lower chamber is, in this case, most likely a connection with the driver (intercom), but in nature there were also cameras installed in the same way.
- Land Transport
In the summer of 2020, a tender was announced for the purchase of video analytics equipment for Moscow trams. - It is planned to launch the system on some multimedia screens at stations that have not yet been installed. There is also an assumption that the face recognition system works on some outdoor cameras (especially in places of rallies), as well as new cameras at stations and subway crossings. In addition, at some public events, there were mobile video surveillance systems - a PTZ camera mounted on a high mast of a police car - perhaps the system works with them as well.
The cameras themselves are not engaged in face recognition - they only broadcast the video stream, recognition takes place centrally, on special servers occupying 19 racks in the data center of the ECDC. The total storage capacity was 28 Petabytes for 2019.
There are also servers that host databases and front-end systems.
This is how the web interface for accessing the data of the face recognition system looks like

The Moscow face recognition system not only recognizes faces, but also stores information in a database about the place and time of a face's appearance - in fact, all movements. The system knows when you enter your entrance or the subway, who you do it with and how often. Based on this data, the friend-or-foe function works (on access cameras). The data is available for at least 30 days and is freely available on the darknet.
An example of displaying the results of a query about human movements

Of course, this system also has advantages - for example, it helps to detain persons on the federal wanted list. But is it worth depriving everyone else of privacy for the sake of this? Already today, this system is used to persecute public activists and political figures (you can read about different cases here). In addition, using the face recognition system, they are looking for participants in uncoordinated actions - the system even has a separate category for active participants in rallies. And in the spring of 2020, the system was used to control quarantined Muscovites, and fines came even for taking out the garbage if a person got into the lens of an entrance video camera.
What to do?
Sign the petition. Just Roskomsvoboda was created by the project BanCam, the purpose of which is to ban the use of face recognition technology. I advise you to take a look at the site - there are many interesting materials on the topic.
In the meantime, the technology is still in use, you can do a few simple things that will greatly complicate its work:
- When entering the metro, be sure to wear a face mask (besides, there is a pandemic in the yard).
- A mask alone may not be enough - it is worth complementing it with a cap.
- Bend your head down when passing through a camera-equipped turnstile. The larger the angle between the face and the camera, the worse the recognition accuracy. And if the lower part of the face is covered with a mask, and the eyes are hidden under the visor of the cap, there is nothing left to recognize.
- When entering a porch equipped with a face recognition camera, follow the same rules.
Chapter 2. Mobile communications
The advent of mobile phones not only simplified communication, but also became a great gift for the intelligence services. It became possible not only to track the movements of a contact person, but also to get a list of people who were once at the right moment in the past within the line of sight of a particular cell tower.
Location accuracy depends on the density of cell towers (or more scientifically, base stations, BSs). Outside the city, the density is low, and the accuracy can be up to several (tens) kilometers, and in the city center, on the contrary, with a large number of towers, it is in the area of several hundred meters. There are also more accurate methods for determining the location (the so-called Trilateration - determining the distance by the time the signal travels between three points), but they already require active intervention in the operator's network, and fortunately are not massive in nature, but are used in a targeted manner.
A mobile operator keeps a log of his movements in a special database for each subscriber, namely CellID (BS identifier) and the time of presence in the reception area of this station. The storage period for such data (probably) can be from six months or more.
Now in Russia they can pass a law according to which it will be possible to obtain such data even without a court decision, which means thatpenetrations will fall in price all and sundry will have access to them.
What to do?[/BHEADING]
Ideally, do not use a mobile phone. But for many, this option is unacceptable, so the trade-offs will be listed below.
- Do not register a SIM card for calls to your own name. A good option is to divide the SIM cards into "white" - the one that is registered to you, you can link to it, for example, banking or government services, and "gray" - the one with which you will call and indicate on online shopping sites. Bonus - if a gray SIM card is called from the bank's security service, you will immediately know what's what.
- The SIM card for calls can be changed periodically - the more often, the less data the operator can collect about you. When changing a SIM card, you need to remember that the operator retains the IMEI phone number is a unique modem number that is transmitted when registering on the network. If the phone is designed for two SIM cards, then it will have two different IMEIs (which sometimes can differ by only one digit - you need to look in the settings). Some phones allow you to change it. If you put a gray SIM card in the phone (or slot) where the white one was before, you can say goodbye to anonymity. Also, for those who have data on the location of all subscribers of a cell tower, it will not be difficult to compare two SIM cards operating simultaneously in different base stations, so it is better to keep the "white" SIM card off and turn it on as needed.
- You have outwitted everyone and are using a "gray" SIM card. However, you can, if you wish, identify you by comparing the list of your contacts and their data (contacts mean the subscribers you call most often). The solution is not to call or send SMS via the mobile network, but to use instant messengers for this. Do not forget that through the mobile operator calls and SMS are sent in unencrypted form, and according to the "Yarovaya Law" are stored for 6 months. In addition, according to this law, all your traffic should be stored, but in fact, storing encrypted TLS traffic (and now there is almost no unencrypted traffic) does not make sense, metadata is saved for analysis. In some rare cases, a person can be identified through them.
- Well, in some cases, you can still turn off the phone (in advance, so that the last communication tower that "remembered" you is far from the place that you want to visit anonymously. This is especially true for some public events where communication is jammed (intentionally or overloaded network) - you will not be able to call, and the location will be exposed.
- Probably, it is worth mentioning here GetContact - a service that allows you to find out how you are recorded in other people's address books. So you can find out your real data and much more, if someone from your contacts had the imprudence to install this application on their phone, and their phone book leaked to the GetContact server. In combination with a database of telephone numbers tied to the city Wi-Fi network, this service can theoretically be used for mass de-anonymization.
Chapter 3. Payment systems
- Data security.
It is no secret that any transactions with accounts (be it a bank card or an electronic wallet) are saved forever and are available for viewing in your personal account. Often, in addition to the obligation to transfer this data at any time at the request of the law enforcement agencies, the bank or payment system has the right to process this data, and even transfer it to third parties for processing (usually, such an item is spelled out in the client agreement, and is active by default). - Safety of money.
Your card or e-wallet can be blocked at any time if the security service thinks that something is wrong with your wallet. And if unlocking in the bank takes a couple of days and your money is guaranteed to become available to you again, then in the case of payment systems you can lose it forever. If you inadvertently repost memes on social networks, then you risk getting on the list of Rosfinmonitoring. The mechanism is as follows: first, a criminal case is initiated, then you are entered into the register of extremists and terrorists, and you can get there even without a court decision - a decision on recognizing a person as a suspect under some articles of the Criminal Code is enough. After being included in this list, banks are required to block all your accounts (you can only withdraw some money per month). Here you can read a couple of stories about how people live with it.
What to do?
Try to use non-cash payments only where you cannot do without them, no matter how convenient it may seem. Well, if you really want to, I recommend keeping a supply of cash in a safe place in case of blocking or losing the card.
Chapter 4. Transport
It is very difficult to travel anonymously these days, especially when it comes to long distance travel. And if with international crossings (flights) everything is obvious - border control is required, then with intercity movements there are less obvious ways of tracking.
- Cars.
Each vehicle has a so-called state number, which is unique and by which you can easily identify the person or legal entity to which it is registered.
License plates are standardized and adapted for automatic recognition by video recording complexes (or, in other words, traffic cameras). These cameras are installed at all exits from the city. Some of them are used not only to control speed, but also to collect statistics on the movements of vehicles, and not only those on the wanted list, but generally all in a row. One of these control systems is the Web system. - Airplanes, trains and intercity buses. It is now impossible to purchase a ticket for these types of transport without entering the passport data. These data are used not only to identify the passenger, but also enter a special system called "Search-Magistral", and the information appears there even at the stage of booking a ticket. The storage period for information about trips in this database is unknown.
- Local transport - metro, electric trains and regular buses. Since travel for cash (buying tickets for one trip) is now not profitable in the city - there are higher fares (except for electric trains), everyone mostly uses transport cards.
When passing through the turnstile, the number and time of the transport card are sent by the turnstile to the server, so it is logical to assume that data on movements is collected. Now it is also possible to compare this data with a photograph taken by a camera on the turnstile. If you use a Muscovite social card, then the carrier already has your passport data (including a photo), so it's silly to talk about any privacy of trips here.
In the spring of 2020, at the height of the coronavirus pandemic, electronic passes were introduced in Moscow. As conceived by the creators, transport could only be used if the transport card was tied to a pass, which again contained the passport data of its owner. But as usual, something went wrong, and many Troika cards that were not tied to passes worked, but tied social cards did the opposite.
So if you tied the card to this pass, hand it over to the cashier. I also recommend not to tie the transport card to the phone number, top up only in cash and change it periodically.
Chapter 5. Other methods of surveillance
Tracking via Wi-Fi or Bluetooth.
There is a Wi-Fi network for transport in Moscow. In order to use this network, you need to bind a phone number to the device. The network operator actively cooperates with the Moscow authorities and advertising companies.
Data is collected about the actions of users on the network, the services used, as well as geolocation.
Moscow authorities plan to start monitoring citizens through special software and hardware systems that will collect MAC addresses of devices that have appeared in their area of operation. It is not entirely clear how they are going to do this, if MAC randomization is enabled by default in modern versions of Android and IOS.
In addition to city authorities, private companies, such as 2wifi, also collect geolocation data via Wi-Fi .
What to do?
Do not use the city Wi-Fi network, since mobile Internet now works at all subway stations and even in some sections.
P.S
There is always a balance between privacy and comfort. It is impossible to get them in full at the same time, you have to sacrifice one thing for the sake of the other. It is important to observe the measure that everyone determines for himself.
The megalopolis, which is described in the article, is Moscow, however, the article may be relevant for other cities as well.
All information in this article is collected from open sources and articles, links to which are given in the text.
For those who have read to the end
There is an Easter egg in the first picture, who found it
If you know something that is not in this article, write to the comments, and I will try to supplement it.
Protect your privacy and do not break the law.
habrastorage.org
