Man
Professional
- Messages
- 3,222
- Reaction score
- 1,215
- Points
- 113
Canadian system administrator Daniel Milisic discovered that the firmware of the T95 Android set-top box he bought on Amazon was infected with complex malware right out of the box.
The malware was found in the firmware of the T95 set-top box with the AllWinner H616 processor, which is sold on Amazon, AliExpress and other large marketplaces in different countries. Such set-top boxes go through a completely unclear path from production in China to the shelves of virtual stores. In many cases, the devices are sold under different brands and names, and there are simply no clear indications of their origin.
Additionally, since such devices typically pass through many hands, vendors and resellers have many opportunities to load custom ROMs onto them, including potentially malicious ones.
The researcher says that the T95 device he examined used a ROM based on Android 10, signed with test keys, and ADB (Android Debug Bridge) exposed over Ethernet and Wi-Fi. This configuration may already raise concerns, since ADB can be used to connect to devices, have unrestricted access to the file system, execute commands, install software, change data, and remotely control the device. But since most consumer devices are protected by a firewall, attackers are unlikely to be able to remotely connect to them via ADB.
Milisic writes that he initially purchased the device to run Pi-hole, a DNS sinkhole that protects devices from unwanted content, ads, and malicious sites without installing additional software. However, after analyzing Pi-hole's DNS requests, the researcher noticed that the device was attempting to connect to multiple IP addresses associated with active malware.
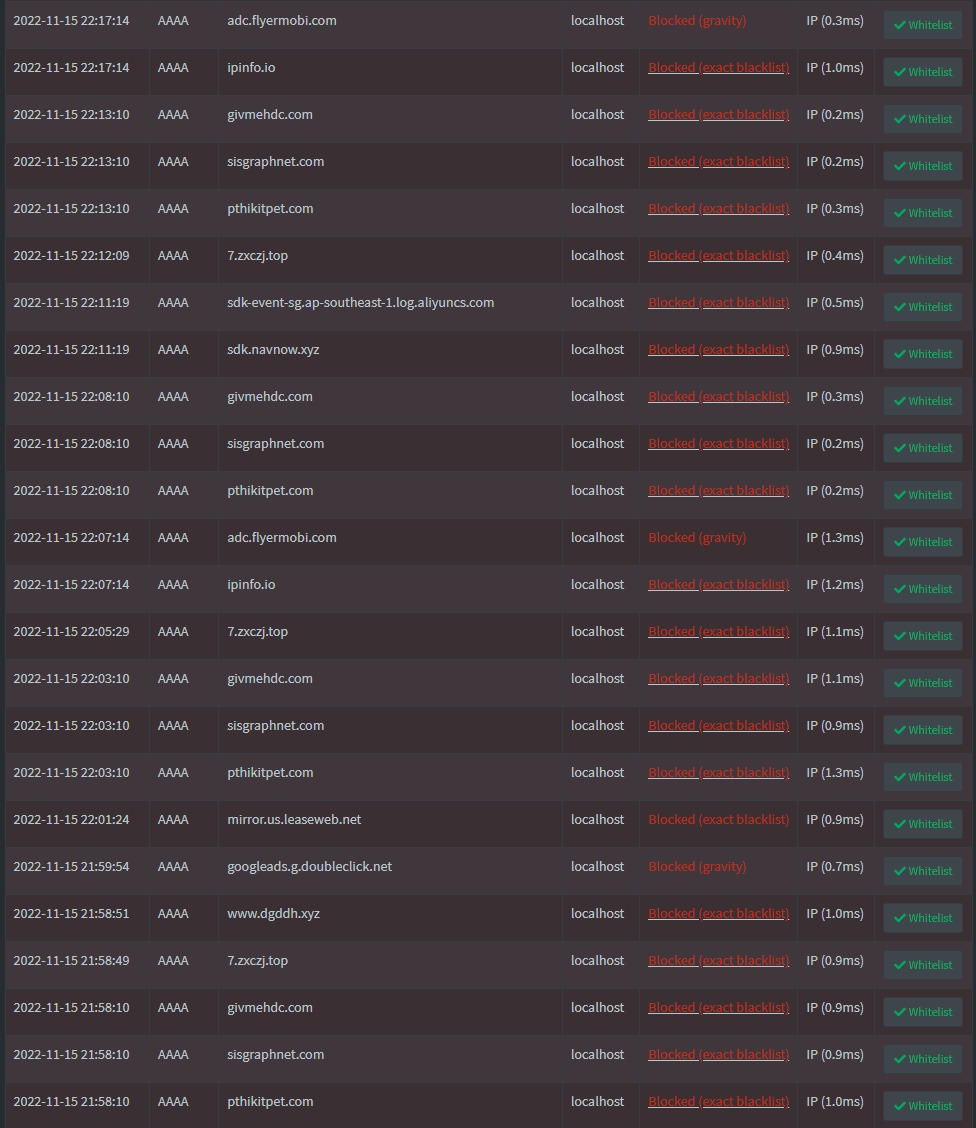
Milisic believes that the malware installed on the device is the sophisticated Android malware CopyCat, first discovered by experts from Check Point in 2017. Even then, analysts believed that the malware had infected more than 14 million devices worldwide, gained root access to 8 million of them, and earned its authors about $1.5 million in just two months.
It turned out that the malware was trying to get additional payloads from the sites ycxrl[.]com, cbphe[.]com, and cbpheback[.]com. Since it was difficult to create a clean firmware to replace the malware, Milisic decided to change the C&C DNS to route requests through the Pi-hole web server and block them.
The researcher writes that he does not know how many Android boxes of this model on Amazon are infected with malware, nor does he know how exactly this happened, but he recommends that all T95 users follow two simple steps to accurately clean their device and neutralize malware that may be running on it:
To make sure that the malware is neutralized, you should run it adb logcat | grep Corejavaand make sure that the command chmod fails.
Given that such devices are quite inexpensive, the researcher notes that perhaps a more sensible solution would be to stop using them altogether.
Source
The malware was found in the firmware of the T95 set-top box with the AllWinner H616 processor, which is sold on Amazon, AliExpress and other large marketplaces in different countries. Such set-top boxes go through a completely unclear path from production in China to the shelves of virtual stores. In many cases, the devices are sold under different brands and names, and there are simply no clear indications of their origin.
Additionally, since such devices typically pass through many hands, vendors and resellers have many opportunities to load custom ROMs onto them, including potentially malicious ones.
The researcher says that the T95 device he examined used a ROM based on Android 10, signed with test keys, and ADB (Android Debug Bridge) exposed over Ethernet and Wi-Fi. This configuration may already raise concerns, since ADB can be used to connect to devices, have unrestricted access to the file system, execute commands, install software, change data, and remotely control the device. But since most consumer devices are protected by a firewall, attackers are unlikely to be able to remotely connect to them via ADB.
Milisic writes that he initially purchased the device to run Pi-hole, a DNS sinkhole that protects devices from unwanted content, ads, and malicious sites without installing additional software. However, after analyzing Pi-hole's DNS requests, the researcher noticed that the device was attempting to connect to multiple IP addresses associated with active malware.

Milisic believes that the malware installed on the device is the sophisticated Android malware CopyCat, first discovered by experts from Check Point in 2017. Even then, analysts believed that the malware had infected more than 14 million devices worldwide, gained root access to 8 million of them, and earned its authors about $1.5 million in just two months.
“I found layers on top of the malware using tcpflow and nethogs to monitor traffic, and traced the malware to the offending process/APK, which was then removed from the ROM,” the researcher explains. “But the last piece of malware that I couldn’t trace injects the system_server process and appears to be deeply integrated into the ROM.”
It turned out that the malware was trying to get additional payloads from the sites ycxrl[.]com, cbphe[.]com, and cbpheback[.]com. Since it was difficult to create a clean firmware to replace the malware, Milisic decided to change the C&C DNS to route requests through the Pi-hole web server and block them.
The researcher writes that he does not know how many Android boxes of this model on Amazon are infected with malware, nor does he know how exactly this happened, but he recommends that all T95 users follow two simple steps to accurately clean their device and neutralize malware that may be running on it:
- reboot the device in recovery mode or perform a factory reset via the menu;
- After rebooting, connect to ADB via USB or WiFi-Ethernet and run the script it created .
To make sure that the malware is neutralized, you should run it adb logcat | grep Corejavaand make sure that the command chmod fails.
Given that such devices are quite inexpensive, the researcher notes that perhaps a more sensible solution would be to stop using them altogether.
Source
