Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,095
- Points
- 113
Researchers link the attacks to a mysterious group called Crazy Evil.
Security researchers at Moonlock have discovered a new wave of activity in the AMOS malware, also known as Atomic Stealer. Attackers allegedly linked to the hacker group Crazy Evil spread malware through fake advertising campaigns in Google Ads, posing it as the popular macOS screen recording app Loom.
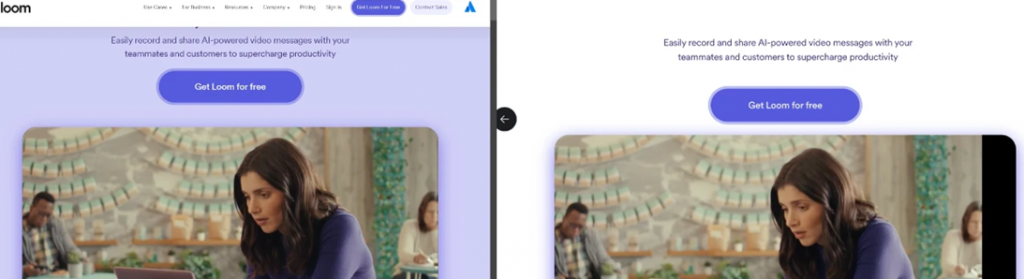
Real (left) and fake one (right)
According to the investigation, cybercriminals create fake sites that mimic the real Loom site. Users who click through ads get to these fake resources, where they download the updated version of AMOS Stealer. This software can steal data from browsers, accounts, passwords, and also empty cryptocurrency wallets.
The new version of AMOS Stealer has unique features, including replacing the legitimate Ledger Live app with a malicious copy of it. Ledger Live provides access to cryptocurrencies, NFTs, and DeFi, making it an attractive target for attackers. The researchers also found fake versions of other popular apps, such as Figma and TunnelBlick.
Hackers use this tactic to bypass the Apple App Store's security mechanisms that prevent malicious apps from being downloaded. Cloning apps after a device is compromised allows cybercriminals to move in a new direction, adapting to existing security measures.
The gaming audience that actively uses cryptocurrencies and digital assets is particularly vulnerable. Cybercriminals often post fake jobs and offers on gaming platforms, deceiving users using social engineering.
Moonlock Lab researchers linked the Crazy Evil group to this campaign through an analysis of the darknet, where they found recruitment ads for a team using the same AMOS Stealer. The group actively uses Telegram to communicate with the outside world, as well as to recruit new members.
Apple users are advised to be extra careful when downloading the software. Checking URLs and downloading apps only from the official App Store will help you avoid infection. Gamers should be especially attentive to suggestions from strangers on gaming platforms.
AMOS Stealer continues to evolve, posing a serious threat to users. The Moonlock Lab report will help raise awareness and prevent new devices from becoming infected.
Source
Security researchers at Moonlock have discovered a new wave of activity in the AMOS malware, also known as Atomic Stealer. Attackers allegedly linked to the hacker group Crazy Evil spread malware through fake advertising campaigns in Google Ads, posing it as the popular macOS screen recording app Loom.

Real (left) and fake one (right)
According to the investigation, cybercriminals create fake sites that mimic the real Loom site. Users who click through ads get to these fake resources, where they download the updated version of AMOS Stealer. This software can steal data from browsers, accounts, passwords, and also empty cryptocurrency wallets.
The new version of AMOS Stealer has unique features, including replacing the legitimate Ledger Live app with a malicious copy of it. Ledger Live provides access to cryptocurrencies, NFTs, and DeFi, making it an attractive target for attackers. The researchers also found fake versions of other popular apps, such as Figma and TunnelBlick.
Hackers use this tactic to bypass the Apple App Store's security mechanisms that prevent malicious apps from being downloaded. Cloning apps after a device is compromised allows cybercriminals to move in a new direction, adapting to existing security measures.
The gaming audience that actively uses cryptocurrencies and digital assets is particularly vulnerable. Cybercriminals often post fake jobs and offers on gaming platforms, deceiving users using social engineering.
Moonlock Lab researchers linked the Crazy Evil group to this campaign through an analysis of the darknet, where they found recruitment ads for a team using the same AMOS Stealer. The group actively uses Telegram to communicate with the outside world, as well as to recruit new members.
Apple users are advised to be extra careful when downloading the software. Checking URLs and downloading apps only from the official App Store will help you avoid infection. Gamers should be especially attentive to suggestions from strangers on gaming platforms.
AMOS Stealer continues to evolve, posing a serious threat to users. The Moonlock Lab report will help raise awareness and prevent new devices from becoming infected.
Source

