Man
Professional
- Messages
- 3,221
- Reaction score
- 1,175
- Points
- 113
The non-obvious loophole is frightening in its simplicity.
Microsoft has fixed a vulnerability that allowed attackers to use the Microsoft 365 administrative portal to send sexually threatening emails by bypassing spam filters. This type of scam, which threatens to spread "compromising" material, was made possible due to data validation flaws on the server.
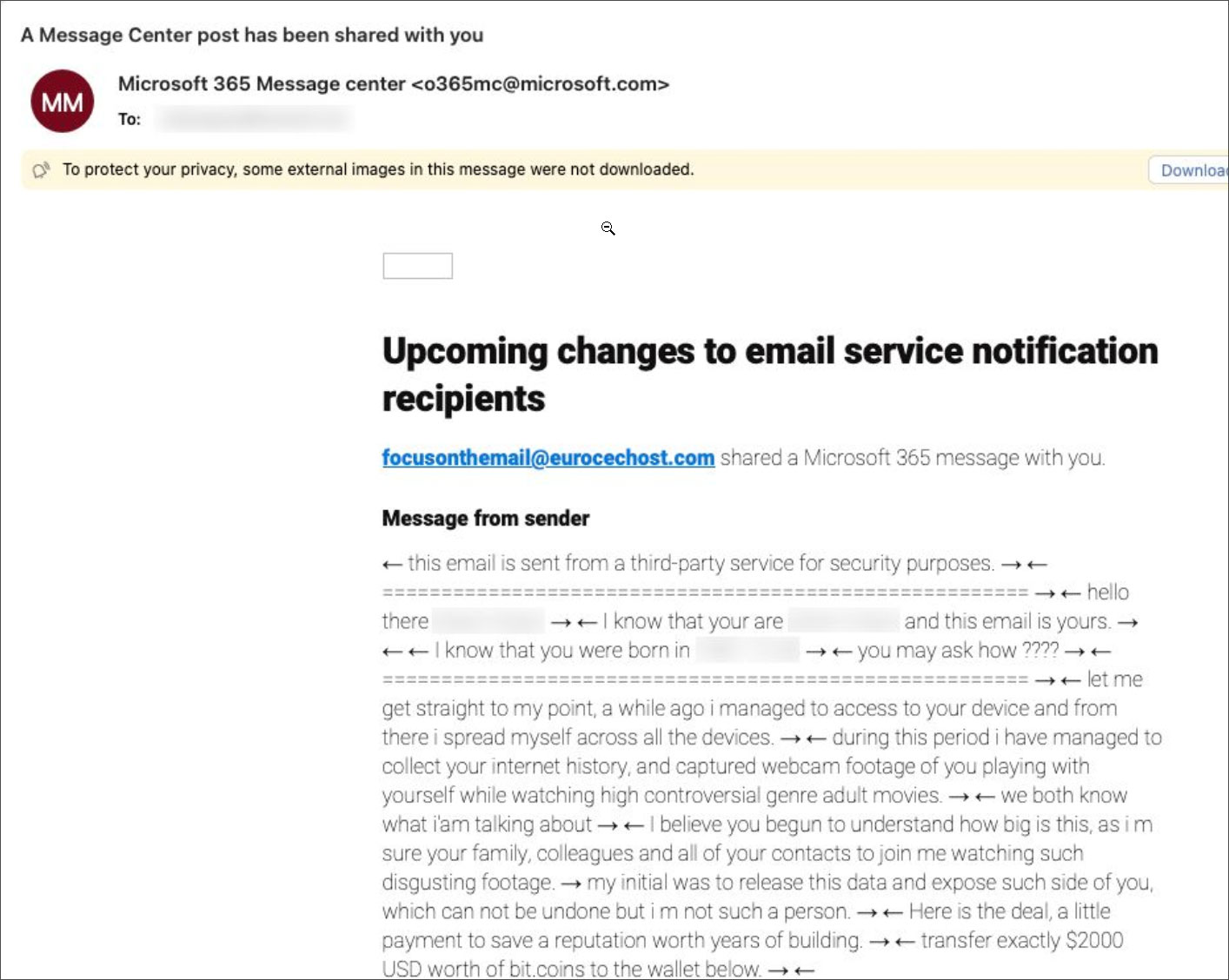
The letter says that someone took possession of the victim's browser history and private intimate videos
The messages were sent from a legitimate "o365mc@microsoft.com" address, which allowed them to bypass spam filters. To do this, the attackers used the "Private Message" feature in the Message Center section of the Microsoft 365 portal, where administrators can share notifications. However, the message field was limited to 1,000 characters, which did not allow long texts to be sent.
The circumvention of the restriction was implemented by changing the settings in the browser. The hackers manually increased the maximum allowable number of characters in the page's HTML code, which allowed the threat to send the full text. Moreover, the process was automated, which made it easier to send such emails in bulk.
LinkedIn users actively shared their observations about how such emails bypass spam filters and end up in the main inboxes. However, Microsoft responded promptly to the problem. The company said that it has made changes, and now the "Share" button opens the user's email client instead of sending messages through the portal.
Despite the reduced effectiveness of the attacks, such emails are very plausible and can still cause stress for people unfamiliar with their mechanism. Experts emphasize that such messages do not pose a real danger and should be deleted without any interaction.
Recent changes made by Microsoft to address the vulnerability underscore the importance of continuous monitoring and prompt remediation of security issues, especially in systems related to enterprise data protection. This case is a reminder of the need to implement more stringent server-side checks to prevent similar threats in the future.
Source
Microsoft has fixed a vulnerability that allowed attackers to use the Microsoft 365 administrative portal to send sexually threatening emails by bypassing spam filters. This type of scam, which threatens to spread "compromising" material, was made possible due to data validation flaws on the server.

The letter says that someone took possession of the victim's browser history and private intimate videos
The messages were sent from a legitimate "o365mc@microsoft.com" address, which allowed them to bypass spam filters. To do this, the attackers used the "Private Message" feature in the Message Center section of the Microsoft 365 portal, where administrators can share notifications. However, the message field was limited to 1,000 characters, which did not allow long texts to be sent.
The circumvention of the restriction was implemented by changing the settings in the browser. The hackers manually increased the maximum allowable number of characters in the page's HTML code, which allowed the threat to send the full text. Moreover, the process was automated, which made it easier to send such emails in bulk.
LinkedIn users actively shared their observations about how such emails bypass spam filters and end up in the main inboxes. However, Microsoft responded promptly to the problem. The company said that it has made changes, and now the "Share" button opens the user's email client instead of sending messages through the portal.
Despite the reduced effectiveness of the attacks, such emails are very plausible and can still cause stress for people unfamiliar with their mechanism. Experts emphasize that such messages do not pose a real danger and should be deleted without any interaction.
Recent changes made by Microsoft to address the vulnerability underscore the importance of continuous monitoring and prompt remediation of security issues, especially in systems related to enterprise data protection. This case is a reminder of the need to implement more stringent server-side checks to prevent similar threats in the future.
Source

