Brother
Professional
- Messages
- 2,590
- Reaction score
- 483
- Points
- 83
The largest hacker network has been gaining momentum for 6 years. Why can't anyone stop it?
A recent study by Infoblox revealed the existence of a large-scale "criminal affiliate program" involving well-known cybercrime groups ClearFake, SocGholish and dozens of others. The main partner of this program is VexTrio, which is described as "the largest intermediary of malicious traffic in the history of cybersecurity."
The activity of VexTrio began approximately in 2017. The group uses a dictionary-based domain generation algorithm (DDGA) to distribute fraudulent and spyware programs, adware, potentially unwanted programs, and pornographic content. So, in 2022, hackers successfully distributed the Glupteba malware, despite Google's attempts to eliminate a significant part of their infrastructure in December 2021.
In August 2023, VexTrio launched a large-scale attack using the aforementioned DDGA algorithm and compromised WordPress sites redirecting visitors to intermediate C2 domains. A special feature of these infections is the use of the DNS protocol to obtain redirection URLs, which allows the grouping to act as a DNS-based traffic distribution system (DTDS).
VexTrio is estimated to operate a network of more than 70,000 domains and interact with approximately 60 affiliates, including the aforementioned ClearFake and SocGholish. Renee Burton of Infoblox said that the methods of recruiting affiliates are still unknown, but it is assumed that VexTrio can advertise its services on dark forums.
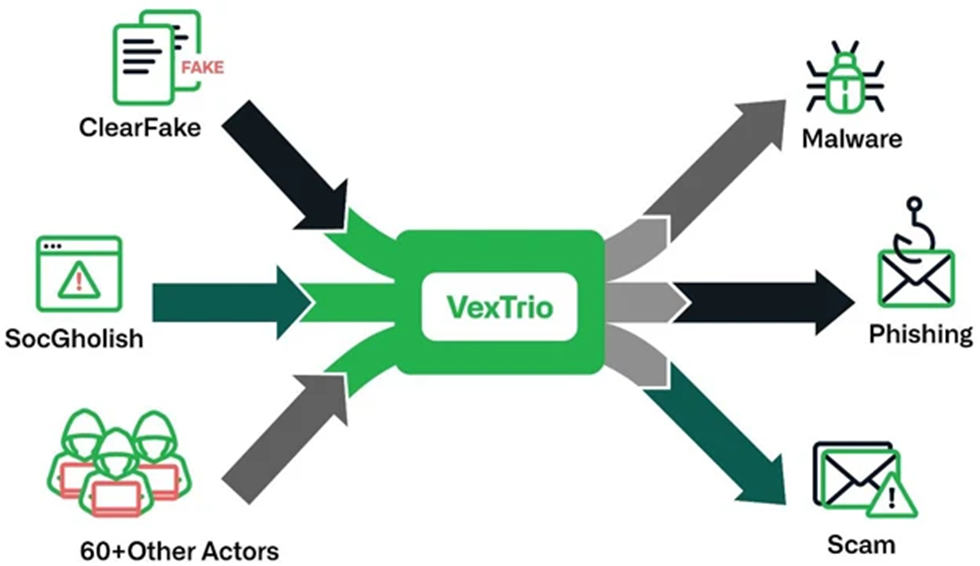
VexTrio collaboration scheme with affiliates
The VexTrio network uses TDS to receive and sell web traffic. Their TDS is a large and complex server cluster that manages thousands of domains. The VexTrio system operates in two versions: HTTP-based and DNS-based, with the latter starting in July 2023.
According to Palo Alto Networks, another TDS system, Parrot, has been active since October 2021, although it may not exist at all since August 2019. Websites with Parrot TDS inject malicious scripts into existing JavaScript code, which allows them to redirect victims browsers to fraudulent sites.
The main vector of VexTrio attacks is websites running on a vulnerable version of WordPress with malicious JavaScript embedded in their HTML code. Infoblox emphasizes that VexTrio is "a key player in the field of cybercrime affiliations."
Due to the complex structure and interconnected nature of the affiliate network, accurate classification and attribution of VexTrio is difficult, which has contributed to their prosperity for more than six years, while remaining unrecognizable to the cybersecurity industry.
Renee Burton described VexTrio as "the king of cybercrime affiliations," emphasizing that "global consumer cybercrime is thriving as these traffic intermediaries go unnoticed."
A recent study by Infoblox revealed the existence of a large-scale "criminal affiliate program" involving well-known cybercrime groups ClearFake, SocGholish and dozens of others. The main partner of this program is VexTrio, which is described as "the largest intermediary of malicious traffic in the history of cybersecurity."
The activity of VexTrio began approximately in 2017. The group uses a dictionary-based domain generation algorithm (DDGA) to distribute fraudulent and spyware programs, adware, potentially unwanted programs, and pornographic content. So, in 2022, hackers successfully distributed the Glupteba malware, despite Google's attempts to eliminate a significant part of their infrastructure in December 2021.
In August 2023, VexTrio launched a large-scale attack using the aforementioned DDGA algorithm and compromised WordPress sites redirecting visitors to intermediate C2 domains. A special feature of these infections is the use of the DNS protocol to obtain redirection URLs, which allows the grouping to act as a DNS-based traffic distribution system (DTDS).
VexTrio is estimated to operate a network of more than 70,000 domains and interact with approximately 60 affiliates, including the aforementioned ClearFake and SocGholish. Renee Burton of Infoblox said that the methods of recruiting affiliates are still unknown, but it is assumed that VexTrio can advertise its services on dark forums.

VexTrio collaboration scheme with affiliates
The VexTrio network uses TDS to receive and sell web traffic. Their TDS is a large and complex server cluster that manages thousands of domains. The VexTrio system operates in two versions: HTTP-based and DNS-based, with the latter starting in July 2023.
According to Palo Alto Networks, another TDS system, Parrot, has been active since October 2021, although it may not exist at all since August 2019. Websites with Parrot TDS inject malicious scripts into existing JavaScript code, which allows them to redirect victims browsers to fraudulent sites.
The main vector of VexTrio attacks is websites running on a vulnerable version of WordPress with malicious JavaScript embedded in their HTML code. Infoblox emphasizes that VexTrio is "a key player in the field of cybercrime affiliations."
Due to the complex structure and interconnected nature of the affiliate network, accurate classification and attribution of VexTrio is difficult, which has contributed to their prosperity for more than six years, while remaining unrecognizable to the cybersecurity industry.
Renee Burton described VexTrio as "the king of cybercrime affiliations," emphasizing that "global consumer cybercrime is thriving as these traffic intermediaries go unnoticed."
