Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,231
- Points
- 113
The mysterious RDGA algorithm creates an army of malicious domains.
Trend Micro discovered a new version of the Play ransomware (Balloonfly, PlayCrypt), which is now targeting VMware ESXi. The new Linux version indicates an expansion of the group's attacks, which increases the number of potential victims and increases the likelihood of successful ransom negotiations.
First introduced in June 2022, the Play virus is known for its double extortion tactics. The ransomware program encrypts systems after extracting confidential data, demanding a ransom for the decryption key. It is estimated that by October 2023, about 300 organizations have become victims of Play.
According to Trend Micro, in the first 7 months of 2024, the United States accounted for the largest number of Play virus victims, followed by Canada, Germany, the United Kingdom and the Netherlands. The affected industries include manufacturing, professional services, construction, IT, retail, financial services, transportation, media, legal services, and real estate.
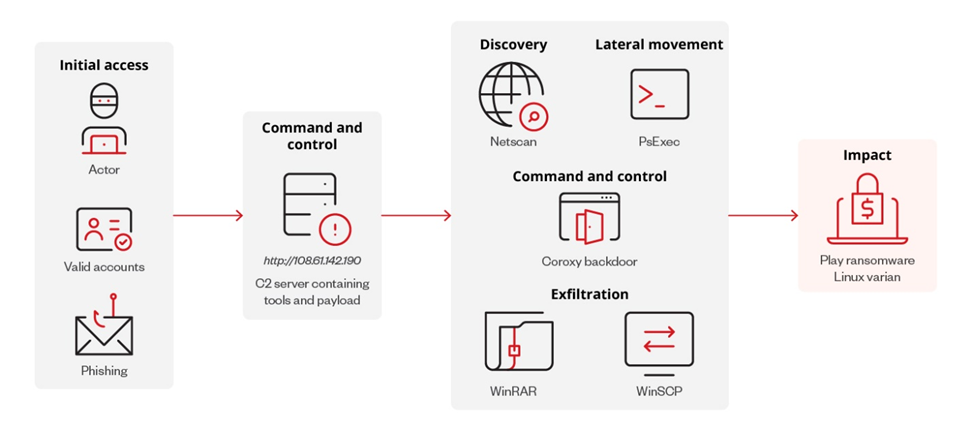
Play Ransomware Linux variant infection Chain
Analysis of the new version of the Play virus for Linux is based on a RAR file located at the IP address (108.61.142[.]190). The archive also contains other tools previously used in attacks, such as PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
Although no cases of infection have been reported yet, the C2 server hosts common tools that Play uses in its attacks. This may mean that the Linux version uses similar tactics, methods, and procedures (TTPs).
At startup, the virus runs in an ESXi environment, and then starts encrypting VM files, including disk, configuration files, and metadata, and adds the ".PLAY" extension to them. Then a ransom note is placed in the root directory.
Additional analysis revealed that the Play group likely uses services and infrastructure provided by Prolific Puma, which offers illegal link shortening services to other cybercriminals to bypass detection when malware is distributed.
Particularly notable is the use of the Registered Domain Generation Algorithm (RDGA) to create new domain names, a mechanism that is increasingly being used by several attackers, including VexTrio Viper and Revolver Rabbit, for phishing, spam, and malware distribution.
For example, Revolver Rabbit registered more than 500,000 domains in the ".bond " zone for a total of about $ 1 million, using the domains as active and false C2 servers for the XLoader styler (FormBook). Revolver Rabbit's typical RDGA pattern includes one or more dictionary words followed by a five-digit number, with each word or number separated by a hyphen. Domains are easy to read and often focus on specific topics or regions, for example: "ai-courses-17621 [.] bond".
RDGA is more difficult to detect and protect against than traditional DGA, as RDGA allows you to generate multiple domain names for registration and use in the infrastructure-either immediately or gradually.
In RDGA, the algorithm is a secret known only to the attacker, and the hacker registers all domain names. In a traditional DGA, the algorithm is contained in the malware itself, and it can be detected, but most domain names will not be registered. While DGA's are used exclusively for connecting to a malware controller, RDGA's are used for a wide range of malicious activities.
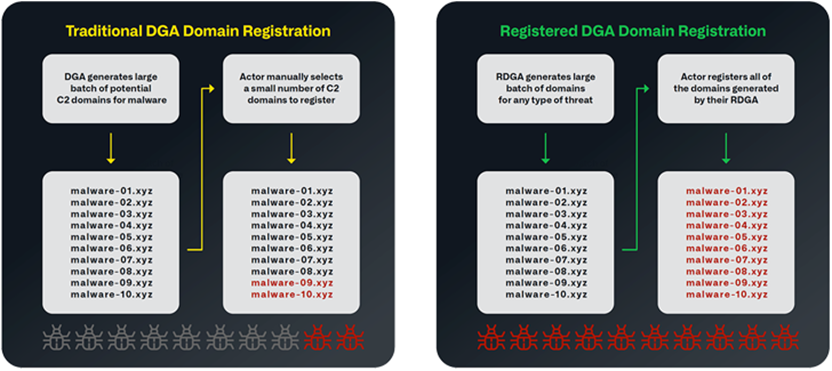
Comparison betweenDGA andRDGA
Recent evidence points to possible collaboration between the two cybercrime groups, suggesting that Play operators are taking steps to circumvent security protocols by using Prolific Puma services. ESXi environments are high-value targets for ransomware attacks due to their critical role in business operations. The efficiency of encrypting multiple virtual machines simultaneously and the value of the data that the machines store make them particularly attractive to cybercriminals.
Source
Trend Micro discovered a new version of the Play ransomware (Balloonfly, PlayCrypt), which is now targeting VMware ESXi. The new Linux version indicates an expansion of the group's attacks, which increases the number of potential victims and increases the likelihood of successful ransom negotiations.
First introduced in June 2022, the Play virus is known for its double extortion tactics. The ransomware program encrypts systems after extracting confidential data, demanding a ransom for the decryption key. It is estimated that by October 2023, about 300 organizations have become victims of Play.
According to Trend Micro, in the first 7 months of 2024, the United States accounted for the largest number of Play virus victims, followed by Canada, Germany, the United Kingdom and the Netherlands. The affected industries include manufacturing, professional services, construction, IT, retail, financial services, transportation, media, legal services, and real estate.

Play Ransomware Linux variant infection Chain
Analysis of the new version of the Play virus for Linux is based on a RAR file located at the IP address (108.61.142[.]190). The archive also contains other tools previously used in attacks, such as PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
Although no cases of infection have been reported yet, the C2 server hosts common tools that Play uses in its attacks. This may mean that the Linux version uses similar tactics, methods, and procedures (TTPs).
At startup, the virus runs in an ESXi environment, and then starts encrypting VM files, including disk, configuration files, and metadata, and adds the ".PLAY" extension to them. Then a ransom note is placed in the root directory.
Additional analysis revealed that the Play group likely uses services and infrastructure provided by Prolific Puma, which offers illegal link shortening services to other cybercriminals to bypass detection when malware is distributed.
Particularly notable is the use of the Registered Domain Generation Algorithm (RDGA) to create new domain names, a mechanism that is increasingly being used by several attackers, including VexTrio Viper and Revolver Rabbit, for phishing, spam, and malware distribution.
For example, Revolver Rabbit registered more than 500,000 domains in the ".bond " zone for a total of about $ 1 million, using the domains as active and false C2 servers for the XLoader styler (FormBook). Revolver Rabbit's typical RDGA pattern includes one or more dictionary words followed by a five-digit number, with each word or number separated by a hyphen. Domains are easy to read and often focus on specific topics or regions, for example: "ai-courses-17621 [.] bond".
RDGA is more difficult to detect and protect against than traditional DGA, as RDGA allows you to generate multiple domain names for registration and use in the infrastructure-either immediately or gradually.
In RDGA, the algorithm is a secret known only to the attacker, and the hacker registers all domain names. In a traditional DGA, the algorithm is contained in the malware itself, and it can be detected, but most domain names will not be registered. While DGA's are used exclusively for connecting to a malware controller, RDGA's are used for a wide range of malicious activities.

Comparison betweenDGA andRDGA
Recent evidence points to possible collaboration between the two cybercrime groups, suggesting that Play operators are taking steps to circumvent security protocols by using Prolific Puma services. ESXi environments are high-value targets for ransomware attacks due to their critical role in business operations. The efficiency of encrypting multiple virtual machines simultaneously and the value of the data that the machines store make them particularly attractive to cybercriminals.
Source
