Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
Botnet cyberattacks target routers and IoT devices from well-known manufacturers.
Last week, the agencies of the Five Eyes alliance, which includes the United States, the United Kingdom, Canada, Australia and New Zealand, issued a joint warning about cyberattacks related to the People's Republic of China. The document describes the actions of the Flax Typhoon cyber group, which uses vulnerabilities in routers and Internet of Things (IoT) devices to create a botnet aimed at attacking critical infrastructure.
According to the report, Flax Typhoon is actively exploiting 66 known vulnerabilities to compromise routers, IoT devices, and other web applications. Among the main manufacturers whose products are under attack are:
Organizations using equipment from these companies are advised to immediately scan their systems and remediate identified vulnerabilities.
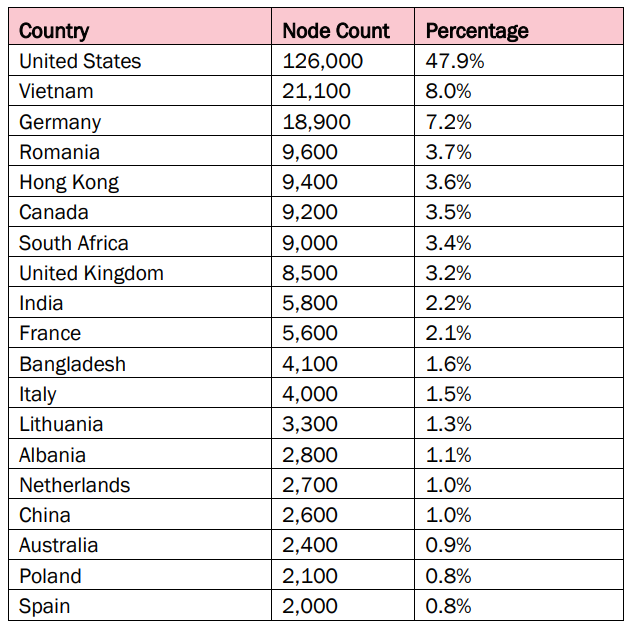
According to the analysis, 47.9% of infected devices are located in the United States, indicating a serious threat to the country's critical infrastructure. Other significant targets of the attack are Vietnam (8%), Germany (7.2%) and a number of other countries, including Canada, the UK and India.
At the time of the warning, 41 of the 66 vulnerabilities had already been included in the VulnCheck KEV database. Notably, only 27 of these vulnerabilities were included in CISA's catalog of known exploitable vulnerabilities (KEVs). Since the warning was issued, VulnCheck has updated its resource to include all 66 vulnerabilities, and CISA is expected to update its directory soon, as well.
To protect against attacks by the Flax Typhoon Botnet and other similar threats, the FBI recommends the following actions:
Experts emphasize the need for a comprehensive approach to vulnerability management. It is important to consider not only the presence of vulnerabilities, but also evidence of their active exploitation, the context of the environment, and additional risk factors. Leveraging up-to-date threat intelligence enables organizations to make informed decisions to prioritize vulnerabilities and effectively mitigate risk.
Source
Last week, the agencies of the Five Eyes alliance, which includes the United States, the United Kingdom, Canada, Australia and New Zealand, issued a joint warning about cyberattacks related to the People's Republic of China. The document describes the actions of the Flax Typhoon cyber group, which uses vulnerabilities in routers and Internet of Things (IoT) devices to create a botnet aimed at attacking critical infrastructure.
According to the report, Flax Typhoon is actively exploiting 66 known vulnerabilities to compromise routers, IoT devices, and other web applications. Among the main manufacturers whose products are under attack are:
- Apache (10 vulnerabilities)
- Cisco (5 vulnerabilities)
- Zyxel (3 vulnerabilities)
- QNAP (3 vulnerabilities)
- Fortinet (3 vulnerabilities)
- Draytek (3 vulnerabilities)
- WordPress (2 vulnerabilities)
- IBM (2 vulnerabilities)
- F5 (2 vulnerabilities)
Organizations using equipment from these companies are advised to immediately scan their systems and remediate identified vulnerabilities.
According to the analysis, 47.9% of infected devices are located in the United States, indicating a serious threat to the country's critical infrastructure. Other significant targets of the attack are Vietnam (8%), Germany (7.2%) and a number of other countries, including Canada, the UK and India.

At the time of the warning, 41 of the 66 vulnerabilities had already been included in the VulnCheck KEV database. Notably, only 27 of these vulnerabilities were included in CISA's catalog of known exploitable vulnerabilities (KEVs). Since the warning was issued, VulnCheck has updated its resource to include all 66 vulnerabilities, and CISA is expected to update its directory soon, as well.
To protect against attacks by the Flax Typhoon Botnet and other similar threats, the FBI recommends the following actions:
- Disable unused services and ports to reduce the attack surface.
- Implement network segmentation to limit the spread of the threat in the event of a compromise.
- Monitoring for a high volume of network traffic that may indicate botnet activity.
- Timely application of patches and updates to fix known vulnerabilities.
- Replace default passwords with strong, unique passwords for each device.
- Regular scheduling of device reboots, which can help in removing malware from RAM.
- Replacement of obsolete hardware that is no longer supported by the manufacturer.
Experts emphasize the need for a comprehensive approach to vulnerability management. It is important to consider not only the presence of vulnerabilities, but also evidence of their active exploitation, the context of the environment, and additional risk factors. Leveraging up-to-date threat intelligence enables organizations to make informed decisions to prioritize vulnerabilities and effectively mitigate risk.
Source

