Brother
Professional
- Messages
- 2,590
- Reaction score
- 531
- Points
- 113

Despite the fact that there have been numerous security incidents on Facebook over the years, many continue to use this social network. Moreover, the number of new users is constantly growing, which allows Facebook to set new records. As of December 31, 2017, the monthly audience on Facebook was 2.13 billion users, the average daily audience was about 1.4 billion.
Part of our life is spent on Facebook. We share our birthdays and anniversaries, talk about our vacation plans, and provide our current location. We share the dates of birthdays of our children and the dates of death of their parents. We tell you about the most pleasant events and difficult thoughts. In general, we disclose many aspects of our life. There are even entire books written by clinical psychologists detailing how powerful Facebook is to our emotions and relationships.
However, we often forget that we are being watched.
We use Facebook as a means of communicating with friends, but there are people who use this social network for malicious purposes. We disclose information that others can use against us. The intruders know when we are not at home and how long our absence will last. They know the answers to security questions and, in fact, can steal our personal data using the information that we voluntarily indicate in our public profile.

Figure 1: Facebook Login Page
The most unpleasant thing is that the more technological our life becomes, the more vulnerable we become to intruders. Even if we share incomplete information in the public domain, in case of urgent need, knowledgeable people can access our e-mail and Facebook account in order to fill information gaps regarding our personal data.
In fact, you don't even need to be a professional hacker to access someone else's Facebook account.
The process of gaining access to your account can be as difficult as installing the Firesheep extension. Moreover, on Facebook, you can access someone else's account even without knowing the password. You just need to choose three friends to send the code. Next, you enter the three received codes and get access to your account. It couldn't be easier.
In this article, I will show you several ways how hackers and ordinary people can access your Facebook account. After describing each method, there will be a method for protecting your account from a specific method.
Method 1: Reset password
The easiest way to gain access to someone else's Facebook account is to reset your password. It is easier to implement this method for those people who are on the list of friends of the person whose account is planned to be hacked.- The first step is to get the email used during authorization (for example, in the section with contacts in the profile). Hackers use utilities like TheHarvester. More information on this topic can be found in this guide .
- Click on the Forgotten account? Link and enter the victim's email address. After the account appears, click on This is my account.
- You will be asked if you want to recover your password via email. Since we will be accessing by other methods, click on No longer have access to these?
- You will be asked How can we reach you? Enter an email address that you have access to. This address should not be associated with any Facebook account.
- You will be asked to answer a question. If you know the victim well, you can probably answer this question. Otherwise, you can try to pick up the answer. If you find the correct answer, you can change your password. Next, you need to wait 24 hours to log into the victim's account.
- If you could not find the answer to the question, click on Recover your account with help from friends. Next, you will need to choose from 3 to 5 friends to whom a code will be sent so that you can restore access to your account.
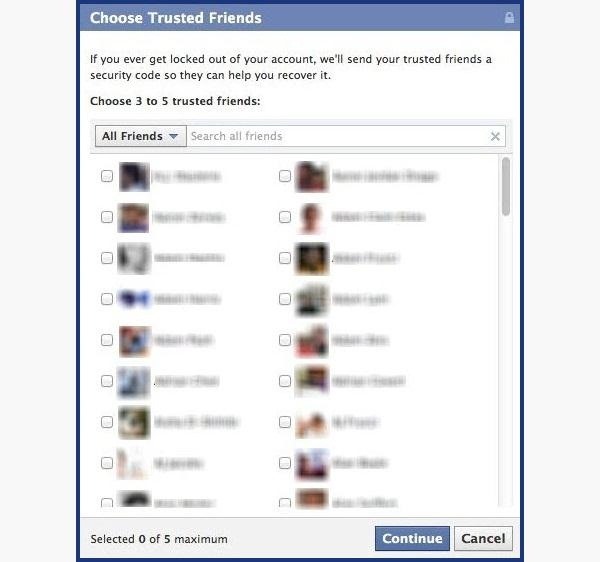
Figure 2: List of friends through whom you can restore access to your account
- The selected friends will be sent passwords to be entered on the next page. You can either create from 3 to 5 fake accounts and add as friends to the victim, or choose those friends who agree to share the password sent with you.
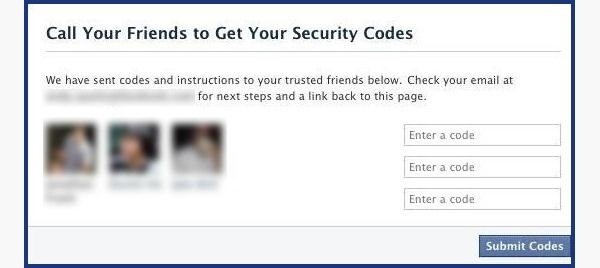
Figure 3: Page for entering passwords sent to selected friends
How to protect yourself
- Please use a separate and unlit email address when registering with Facebook.
- The secret question must be such that the answer cannot be picked up on the basis of information from the public profile. No animal names or anniversaries. Even the names of primary school teachers should not be used as this information can be found in the alumni album.
- Select three trusted friends to whom the password will be sent. This way, you can protect yourself from sending your password to random acquaintances who intend to gain access to your account.
Method 2: Using a Keylogger
Keylogger softwareKeylogger software is an application that reads all keystrokes on the keyboard without the user's knowledge. First, this application must be manually downloaded to the victim's computer. Keyloader then starts running in the background and intercepts all keystrokes. It can be configured so that all collected information is sent to email.
To get started, you can read the guide on how to install the keylogger on the target computer. If this method doesn't work for you, you can search for free keyloggers or try to write your own in C ++ .
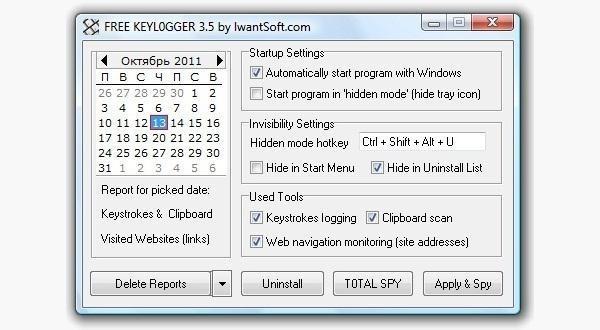
Figure 4: Parameters of one of the keyloggers
Hardware keylogger
Hardware keyloggers work exactly the same as software keyloggers, except that you need to connect a USB flash drive with software to the victim's computer, where all intercepted keystrokes will be saved. Subsequently, you only need to insert the USB flash drive into your computer and extract the collected information.There are several flavors of hardware keyloggers. Models like Keyllama must be connected to the victim's computer and can run on any operating system. In order to receive the collected information, you must have physical access to the device. Alternative option: Keylogger with Wi-Fi support. The collected information can be sent by email or downloaded via Wi-Fi.

Figure 5: Hardware Keyloggers
How to protect yourself
Use a firewall that monitors network activity and can track suspicious transactions, since keyloggers usually send collected information over the Internet.
- Install a password manager. Password managers will automatically fill out all important forms without using the keyboard, and keyloggers can only intercept keystrokes.
- Install updates in a timely manner. As soon as the development company learns that vulnerabilities have appeared in the application, work begins on the creation of patches. Older software versions can cause additional holes in your system.
- Change passwords. If you still don't feel secure, you can change your passwords every two weeks. At first glance, this approach seems too radical, but on the other hand, passwords stolen by cybercriminals will lose their relevance too quickly.
Method 3: Phishing
Although this scenario is much more difficult to implement than the previous two, phishing remains one of the most popular ways to gain access to someone else's account. The most popular type of phishing involves creating a fake login page. The link to this page is usually sent to the victim's mail and is no different from the real authorization form. One of the difficulties is that you need to create a web hosting account and, in fact, the fake page itself.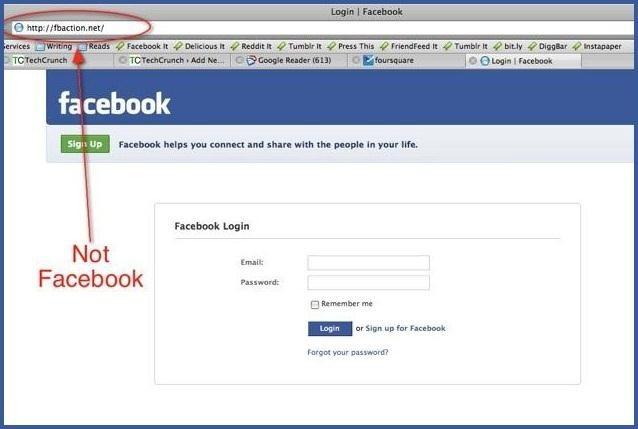
Figure 6: Fake Login Page
The easiest way to create a page like this is to read our website cloning guide. Then you will need to modify the form so that the information entered by the victim is stored somewhere. The implementation of this method is complicated by the fact that, on the one hand, users have become very careful, on the other hand, phishing filters in email services are constantly improving. However, nothing is impossible, especially if you are cloning Facebook entirely.
How to protect yourself
- Don't click on suspicious links in emails. If the letter asks you to go through authorization using a link, be careful. Check the URL first. If you still have doubts, log in directly to the Facebook website.
- Phishing is not necessarily done via email. Links can be distributed through websites, chat rooms, text messages, and so on. Even pop-up ads can be harmful. Never click on links that look suspicious, and especially those where you are asked to enter any confidential information.
- Use antivirus and web threat protection applications (Norton, McAfee, etc.).
Method 4: Man-in-the-Middle Attack
If you are near the target, you can provoke the victim to connect to a fake Wi-Fi network to steal accounts. Utilities like Wi-Fi Pumpkin allow you to create fake Wi-Fi networks based on your wireless network adapter and Raspberry Pi. After you get close to the target with the configured equipment and the victim connects to the fake network, you can analyze the traffic or redirect to the fake login page. You can even replace individual pages and leave the rest.
Figure 7: A small computer on the basis of which a clone of a wireless network was created to intercept traffic (photo by SADMIN / Null Byte)
Never connect to open (and unencrypted) Wi-Fi networks.
- Be especially careful with networks outside of public establishments. For example, a network named "Google Starbucks" should be suspicious if there is no Starbucks within a few miles. Since the hackers have already collected some data on you, your computer or phone will connect to a fake network, since the name of this network has already been used before.
- If you are having problems connecting to a Wi-Fi network, look at the list of nearby networks to see if there are copies of your network names.
- If your router asks you for a password to turn on the Internet to update the firmware, or shows you a page with many grammatical errors, it is very likely that you are connected to a fake hotspot and someone is trying to steal your account.
More advanced users can check out two more tutorials: Same Origin Policy Facebook hack and Facebook Password Extractor (the second method is a little simpler).
How to protect yourself
- In the Account Settings under Security, check the box next to Secure Browsing. Firesheep will not be able to intercept cookies if you work over a secure protocol (like HTTPS).
- Always enabled SSL. Use the HTTPS-Everywhere and Force-TLS Firefox extensions.
- After finishing work with the site, end the authorization session. Firesheep cannot support authorization if you logged out.
- Use only trusted Wi-Fi networks. A hacker may be sitting nearby in a Starbucks cafe and looking at your mail without your knowledge.
- Use a VPN. Since in this case all your traffic will be encrypted, even if an attacker intercepts information using fake Wi-Fi, he will not be able to extract anything useful.
Conclusion
Social media allows you to keep in touch with old friends and meet new people. You can create events in a few clicks, send greeting cards, confess your love to your parents and your second half.Even taking into account the existing possibilities of hacking your account, which we have considered, it is quite possible to use social networks and remain protected. One has only to take certain measures and think several times before you want to post something on your profile. The less information you publish, the more difficult it is for hackers to gain access to your account.
In the event that your Facebook account has been hacked, this guide will guide you through the steps to regain access to your account.
Author: Nelson Aguilar
www.securitylab.ru


