BadB
Professional
- Messages
- 2,488
- Reaction score
- 2,533
- Points
- 113
In their work, computer criminologists regularly encounter cases when it is necessary to quickly unlock a smartphone. For example, the investigation needs data from the phone to understand the causes of a teenager's suicide. In other cases, they can help you track down a criminal group that is attacking long-distance drivers. There are, of course, cute stories parents forgot the password to the gadget, and there is a video with the first steps of their baby left on it, but unfortunately, there are only a few of them. But they also require a professional approach to the issue.
So, the most common method of restricting access to user information contained in the device is to lock the screen of the mobile device.
The fact that the US FBI paid a large sum to unlock the iPhone of terrorist Syed Farook, one of the participants in the terrorist attack in the California city of San Bernardino, shows how much the usual blocking of the screen of a mobile device prevents specialists from extracting data from it.
Methods for unlocking the mobile device screen
As a rule, to lock the screen of a mobile device, use:[
SmartBlock methods can also be used To unlock the screen of a number of mobile devices:
Social methods for unlocking a mobile device
In addition to purely technical ones, there are other ways to find out or overcome the PIN code, or the graphic code (pattern) of the screen lock. In some cases, social methods can be more effective than technical solutions, and help unlock devices that are not supported by existing technical developments.
This section will describe methods for unlocking the screen of a mobile device that do not require (or require only limited, partial) use of technical means.
To commit social attacks, you need to study the psychology of the owner of a blocked device as deeply as possible, and understand how they generate and store passwords or graphic patterns. Also, the researcher will need a drop of luck.
When using methods related to password selection, keep in mind that:
Method 1: ask for your password
It may seem strange, but you can find out the unlock password just by asking the device owner. Statistics show that approximately 70% of mobile device owners are willing to provide a password. Especially if it reduces the research time and, accordingly, the owner gets his device back faster. If you can't ask the owner for the password (for example, if the owner of the device has died) or they refuse to disclose it you can ask their close relatives for the password. As a rule, relatives know the password or can suggest possible options.
Method 2: pry the password
The password can be spied on while the owner is using the device. Even if you can only partially remember the password (either symbolic or graphical) — this will significantly reduce the number of possible options, which will allow you to find it faster.
A variant of this method is the use of video surveillance camera recordings, which show the owner unlocking the device using a graphic password. The algorithm described in the work "Cracking Android Pattern Lock in Five Attempts", by analyzing video recordings, allows you to assume options for a graphical password and unlock the device in a few attempts (as a rule, this requires no more than five attempts). According to the authors, "the more complex the graphic password, the easier it is to find it."
Method 3: find your password
The password can be found in the records of the device owner (files on the computer, in the diary, on fragments of paper lying in documents). If a person uses several different mobile devices and they have different passwords, then sometimes in the battery compartment of these devices or in the space between the smartphone case and the case, you can find scraps of paper with written passwords:

Method 4: fingerprinting (Smudge attack)
This method allows you to identify fat-burning handprints on the device's display. You can see them by treating the device screen with a light fingerprint powder (instead of a special forensic powder, you can use baby powder or other chemically inactive fine powder of white or light gray color) or by looking at the device screen in slanting light rays. By analyzing the relative position of handprints and having additional information about the device owner (for example, knowing their year of birth), you can try to choose a text or image password.

Method 5: artificial finger
If the device can be unlocked by a fingerprint, and the researcher has samples of the device owner's handprints, then a 3D printer can produce a three-dimensional copy of the owner's fingerprint and use it to unlock the device:
For a more complete imitation of the finger of a living person for example, when the fingerprint sensor of a smartphone is still detecting heat — the 3D model is put on (leaning) against the finger of a living person.
Even if the owner of the device forgets the screen lock password, they can unlock the device themselves using their fingerprint. This can be used in certain cases where the owner is unable to provide a password, but is nevertheless willing to help the researcher unlock their device.
The researcher should keep in mind the generations of sensors used in various models of mobile devices. Older models of sensors can be triggered almost at the touch of any finger that does not necessarily belong to the device owner. Modern ultrasound sensors, on the contrary, scan very deeply and clearly. In addition, a number of modern sub-screen sensors are simply CMOS cameras that cannot scan the depth of the image, which makes it much easier to deceive them.
Method 6: Mug attack)
This method is described by British police officers [4]. It consists of covert surveillance of a suspect. When the suspect unlocks his phone, the plainclothes agent snatches it out of the owner's hands and does not allow the device to be locked again until it is handed over to experts.
Method 7: errors in device management algorithms
In the news feeds of profile resources, you can often find messages that certain actions with the device unlock its screen. For example, the lock screen of a number of devices can be unlocked when an incoming call occurs. The disadvantage of this method is that the identified vulnerabilities are usually quickly fixed by manufacturers.
An example of an approach to unlocking mobile devices released earlier than 2016 is battery drain. If the battery is low, the device will unlock and prompt you to change the power settings. At the same time, you need to quickly go to the page with security settings and disable the screen lock.
Security tip: don't forget to update your device's OS in a timely manner, and if it's no longer supported, change your smartphone.
Method 8: vulnerabilities in third-party programs
Vulnerabilities identified in third-party programs installed on the device may also provide full or partial access to the data of the blocked device.
An example of such a vulnerability is the theft of data from the iPhone of Jeff Bezos, the main owner of Amazon. A vulnerability in the WhatsApp messenger, exploited by unknown people, led to the theft of confidential data stored in the device's memory.
Such vulnerabilities can be used by researchers to achieve their goals to extract data from locked devices or to unlock them.
Method 9: corporate phone number
Corporate mobile devices can be unlocked by company system administrators. For example, corporate Windows Phone devices are linked to a company's Microsoft Exchange account and can be unlocked by its administrators. For corporate Apple devices, there is a Mobile Device Management service similar to Microsoft Exchange. Its administrators can also unlock a corporate iOS device.
Method 10: information from sensors
By analyzing the information received from the device's sensors, you can choose a password for the device using a special algorithm. Adam J. Smith Aviv demonstrated the possibility of such attacks using data obtained by the smartphone's accelerometer. In the course of research, the scientist was able to correctly determine the character password in 43% of cases, and the graphic password-in 73%
Method 11: face unlock
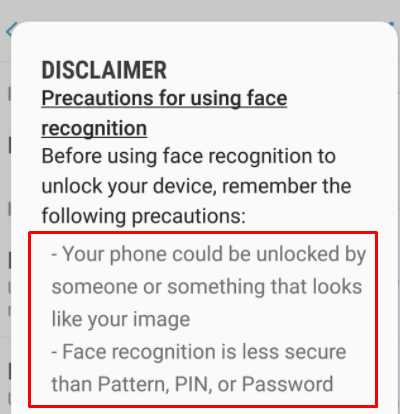
As with a fingerprint, the success of unlocking a device using FaceID technology depends on what sensors and what mathematical apparatus are used in a particular mobile device. So, in the work "Gezichtsherkenning op smartphone niet altijd veilig", researchers showed that some of the studied smartphones were unlocked simply by showing the smartphone camera a photo of the owner. This is possible when only one front-facing camera is used for unlocking, and it does not have the ability to scan image depth data.
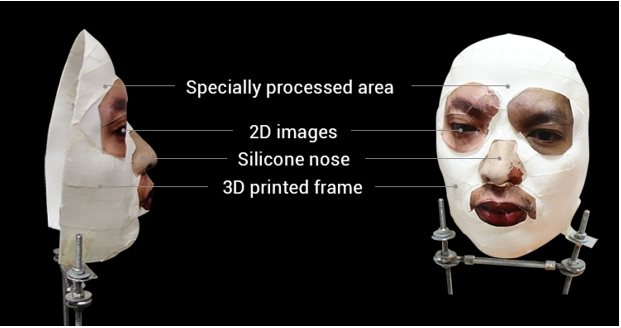
More advanced smartphone models can be unlocked by using a mask or self-learning device. For example, the iPhone X uses a special TrueDepth technology: the device's projector, using two cameras and an infrared emitter, projects a grid consisting of more than 30,000 dots on the owner's face. Such a device can be unlocked by using a mask, the contours of which mimic the contours of the owner's face. Mask for unlocking your iPhone:
Since such a system is very complex and does not work in ideal conditions (natural aging of the wearer occurs, changes in the configuration of the face due to the expression of emotions, fatigue, health status, etc.), it is forced to constantly self-study. Therefore, if another person holds the unlocked device in front of them, their face will be remembered as the face of the device owner, and in the future they will be able to unlock the smartphone using FaceID technology.
The main recommendation is not to look at the camera, just look away. Even if you close one eye the chance to unlock it drops dramatically, just like if you have hands on your face. In addition, to unlock by face (FaceID), only 5 attempts are given, after which you will need to enter a password code.
Method 12: using leaks
Databases of leaked passwords are a great way to understand the psychology of the device owner (provided that the researcher has information about the email addresses of the device owner). In this example, a search for the email address returned two similar passwords that the owner used. It can be assumed that the password 21454162 or its derivatives (for example, 2145 or 4162) could be used as a mobile device lock code.

Method 13: typical device lock passwords
As a rule, several mobile devices are confiscated from the owner, rather than one. There are often dozens of such devices. At the same time, you can choose a password for the vulnerable device and try to apply it to other smartphones and tablets seized from the same owner.
When analyzing data extracted from mobile devices, such data is displayed in forensic programs (often even when data is extracted from blocked devices using various types of vulnerabilities).
As you can see in the screenshot of part of the UFED Physical Analyzer working window, the device is locked with a rather unusual PIN code fgkl.
Do not neglect other user devices. For example, by analyzing passwords stored in the cache of the web browser of the mobile device owner's computer, you can understand the principles of password generation that the owner followed. You can view saved passwords on your computer using the NirSoft utility.
There may also be Lockdown files on the mobile device owner's computer (laptop) that can help you gain access to a locked Apple mobile device. This method will be discussed later.
Method 14: typical PIN codes
As noted earlier, users often use standard passwords: phone numbers, Bank cards, and PIN codes. You can use this information to unlock the provided device.
If all else fails you can use the following information: the researchers analyzed and found the most popular PIN codes (these PIN codes cover 26.83% of all passwords):

Applying this list of PIN codes to a locked device will allow you to unlock it with a probability of ~26%.
Method 15: typical graphic passwords
As described above, if you have data from surveillance cameras where the device owner tries to unlock it, you can select the unlock pattern from five attempts. In addition, just as there are standard PIN codes, there are also standard patterns that can be used to unlock blocked mobile devices.
Simple patterns
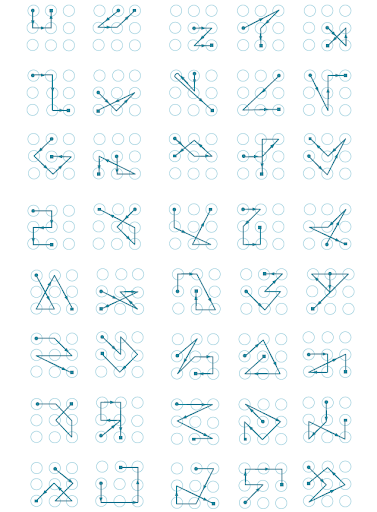
Patterns of medium difficulty

Complex patterns
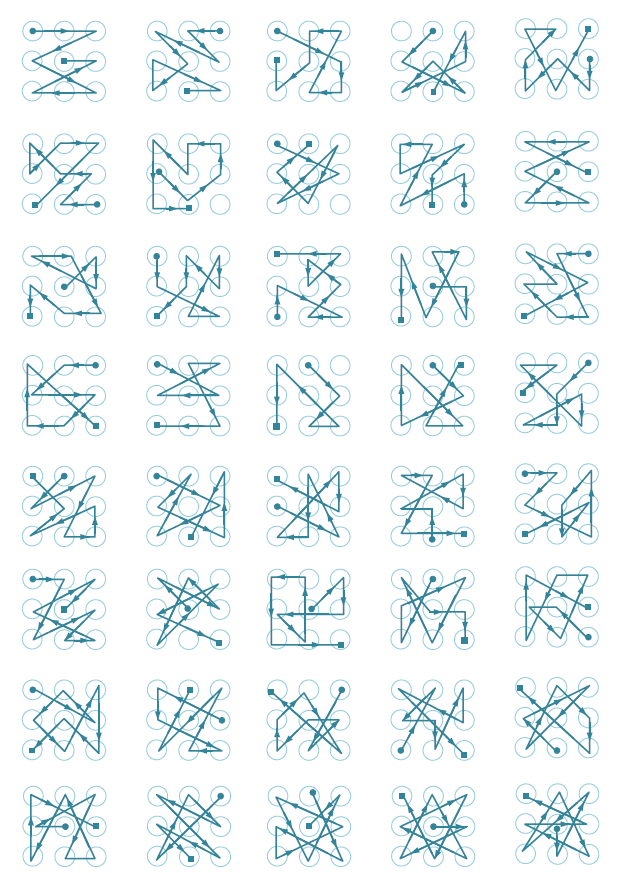
A list of the most popular graphic patterns according to researcher Jeremy Kirby.
On some mobile devices, in addition to the graphic code, an additional PIN code can be set. In this case, if the graphic code cannot be selected, the researcher can click on the Additional PIN (additional PIN) button after entering the wrong graphic code and try to select an additional PIN.
Method 16: alphanumeric passwords
If an alphanumeric password can be used on the device, then the owner could use the following popular passwords as a lock code:
Method 17: cloud or local storage
If it is not technically possible to remove data from a locked device, criminologists can search for its backup copies on the device owner's computers or in the corresponding cloud storage facilities.
Often, when owners of Apple smartphones connect them to their computers, they don't realize that a local or cloud backup of the device may be created at this time.
Google and Apple cloud storages can store not only data from devices, but also passwords saved by the device. Extracting these passwords can help you find the mobile device lock code.
From the Keychain stored in iCloud, you can extract the password for the backup copy of the device set by the owner, which, with a high degree of probability, will match the PIN code of the lock screen.
If law enforcement agencies contact Google and Apple, the companies can transfer the available data, which will probably greatly reduce the need to unlock the device, since law enforcement officers will already have the data.
For example, after the terrorist attack, copies of data stored in iCloud were transferred to the FBI. From the Apple statement:
Security tip: anything you send to the cloud in unencrypted form can and will be used against you.
Method 18: Google account
This method is suitable for removing a graphical password that blocks the screen of a mobile device running the Android operating system. To use this method, you need to know the user name and password from the Google account of the device owner. Second condition: the device must be connected to the Internet.
If you repeatedly enter the wrong graphic password several times in a row, the device will prompt you to restore the password. After that, you need to log in to the user's account, which will unlock the device screen.
Due to the variety of hardware solutions, Android operating systems, and additional security settings, this method is only applicable for a number of devices.
If the researcher doesn't have a password to the Google account of the device owner, you can try to restore it using standard methods for recovering passwords from similar accounts.
If the device is not connected to the Internet at the time of the study (for example, the SIM card is blocked or there is not enough money on it), then you can connect such a device to Wi-Fi using the following instructions:
Method 19: guest account
There can be multiple accounts on mobile devices running the Android 5 and higher operating system. Access to the data of an additional account may not be blocked by a PIN or graphic code. To switch, click on the account icon in the upper-right corner and select a different account:
For an additional account, access to some data or applications may be restricted.
Method 20: specialized services
Companies that develop specialized forensic software, including those that offer services for unlocking mobile devices and extracting data from them. The capabilities of such services are fantastic. You can use them to unlock top models of Android and iOS devices, as well as devices that are in recovery mode (which the device switches to after exceeding the number of attempts to enter the wrong password). The disadvantage of this method is the high cost.
A fragment of the Cellebrite website page that describes which devices they can extract data from. The device can be unlocked in the developer's lab (Cellebrite Advanced Service (CAS)):
For such a service, the device must be provided to the company's regional (or head) office. Possible departure of a specialist to the customer. As a rule, hacking the screen lock code takes one day.
habrastorage.org
In this article, you will learn about ways that allow forensic experts to bypass the smartphone lock.
So, the most common method of restricting access to user information contained in the device is to lock the screen of the mobile device.
The fact that the US FBI paid a large sum to unlock the iPhone of terrorist Syed Farook, one of the participants in the terrorist attack in the California city of San Bernardino, shows how much the usual blocking of the screen of a mobile device prevents specialists from extracting data from it.
Methods for unlocking the mobile device screen
As a rule, to lock the screen of a mobile device, use:[
- Symbolic password
- Graphic password
SmartBlock methods can also be used To unlock the screen of a number of mobile devices:
- Unlocking by fingerprint recognition
- Face recognition unblocking (FaceID technology)
- Unlocking a device based on iris recognition
Social methods for unlocking a mobile device
In addition to purely technical ones, there are other ways to find out or overcome the PIN code, or the graphic code (pattern) of the screen lock. In some cases, social methods can be more effective than technical solutions, and help unlock devices that are not supported by existing technical developments.
This section will describe methods for unlocking the screen of a mobile device that do not require (or require only limited, partial) use of technical means.
To commit social attacks, you need to study the psychology of the owner of a blocked device as deeply as possible, and understand how they generate and store passwords or graphic patterns. Also, the researcher will need a drop of luck.
When using methods related to password selection, keep in mind that:
- if you enter ten incorrect passwords on Apple mobile devices, the user's data may be erased. This depends on the security settings that the user has set;
- on mobile devices running the Android operating system, the Root of Trust technology can be used, which will lead to the fact that after entering 30 incorrect passwords, the user's data will either be unavailable or erased.
Method 1: ask for your password
It may seem strange, but you can find out the unlock password just by asking the device owner. Statistics show that approximately 70% of mobile device owners are willing to provide a password. Especially if it reduces the research time and, accordingly, the owner gets his device back faster. If you can't ask the owner for the password (for example, if the owner of the device has died) or they refuse to disclose it you can ask their close relatives for the password. As a rule, relatives know the password or can suggest possible options.
Security recommendation: Your phone password is a universal key for all data, including payment data. It's a bad idea to say, transmit, or write it in instant messengers.
Method 2: pry the password
The password can be spied on while the owner is using the device. Even if you can only partially remember the password (either symbolic or graphical) — this will significantly reduce the number of possible options, which will allow you to find it faster.
A variant of this method is the use of video surveillance camera recordings, which show the owner unlocking the device using a graphic password. The algorithm described in the work "Cracking Android Pattern Lock in Five Attempts", by analyzing video recordings, allows you to assume options for a graphical password and unlock the device in a few attempts (as a rule, this requires no more than five attempts). According to the authors, "the more complex the graphic password, the easier it is to find it."
Security recommendation: Using a graphic key is not a good idea. It is very difficult to see the alphanumeric password.
Method 3: find your password
The password can be found in the records of the device owner (files on the computer, in the diary, on fragments of paper lying in documents). If a person uses several different mobile devices and they have different passwords, then sometimes in the battery compartment of these devices or in the space between the smartphone case and the case, you can find scraps of paper with written passwords:

Security recommendation: don't keep a Notepad with passwords. This is a bad idea, except when all these passwords are obviously false, to reduce the number of attempts to unlock them.
Method 4: fingerprinting (Smudge attack)
This method allows you to identify fat-burning handprints on the device's display. You can see them by treating the device screen with a light fingerprint powder (instead of a special forensic powder, you can use baby powder or other chemically inactive fine powder of white or light gray color) or by looking at the device screen in slanting light rays. By analyzing the relative position of handprints and having additional information about the device owner (for example, knowing their year of birth), you can try to choose a text or image password.

Protection recommendation: As we said, a graphic password is not the best idea, and neither is glass with a poor oleophobic coating.
Method 5: artificial finger
If the device can be unlocked by a fingerprint, and the researcher has samples of the device owner's handprints, then a 3D printer can produce a three-dimensional copy of the owner's fingerprint and use it to unlock the device:

For a more complete imitation of the finger of a living person for example, when the fingerprint sensor of a smartphone is still detecting heat — the 3D model is put on (leaning) against the finger of a living person.
Even if the owner of the device forgets the screen lock password, they can unlock the device themselves using their fingerprint. This can be used in certain cases where the owner is unable to provide a password, but is nevertheless willing to help the researcher unlock their device.
The researcher should keep in mind the generations of sensors used in various models of mobile devices. Older models of sensors can be triggered almost at the touch of any finger that does not necessarily belong to the device owner. Modern ultrasound sensors, on the contrary, scan very deeply and clearly. In addition, a number of modern sub-screen sensors are simply CMOS cameras that cannot scan the depth of the image, which makes it much easier to deceive them.
Security recommendation: If the finger, then only an ultrasonic sensor. But do not forget that putting your finger against your will is much easier than putting your face.
Method 6: Mug attack)
This method is described by British police officers [4]. It consists of covert surveillance of a suspect. When the suspect unlocks his phone, the plainclothes agent snatches it out of the owner's hands and does not allow the device to be locked again until it is handed over to experts.
Protection recommendation: I Think that if such measures are going to be used against you, then it's bad. But here you need to understand that random blocking devalues this method. And, for example, repeatedly pressing the lock button on the iPhone triggers SOS mode, which in addition turns off FaceID and turns on the password code requirement.
Method 7: errors in device management algorithms
In the news feeds of profile resources, you can often find messages that certain actions with the device unlock its screen. For example, the lock screen of a number of devices can be unlocked when an incoming call occurs. The disadvantage of this method is that the identified vulnerabilities are usually quickly fixed by manufacturers.
An example of an approach to unlocking mobile devices released earlier than 2016 is battery drain. If the battery is low, the device will unlock and prompt you to change the power settings. At the same time, you need to quickly go to the page with security settings and disable the screen lock.
Security tip: don't forget to update your device's OS in a timely manner, and if it's no longer supported, change your smartphone.
Method 8: vulnerabilities in third-party programs
Vulnerabilities identified in third-party programs installed on the device may also provide full or partial access to the data of the blocked device.
An example of such a vulnerability is the theft of data from the iPhone of Jeff Bezos, the main owner of Amazon. A vulnerability in the WhatsApp messenger, exploited by unknown people, led to the theft of confidential data stored in the device's memory.
Such vulnerabilities can be used by researchers to achieve their goals to extract data from locked devices or to unlock them.
Protection recommendation: You need to update not only the operating system, but also the application programs that you use.
Method 9: corporate phone number
Corporate mobile devices can be unlocked by company system administrators. For example, corporate Windows Phone devices are linked to a company's Microsoft Exchange account and can be unlocked by its administrators. For corporate Apple devices, there is a Mobile Device Management service similar to Microsoft Exchange. Its administrators can also unlock a corporate iOS device.
Security recommendation: MDM is both evil and good in terms of security. An MDM administrator can always reset the device remotely. In any case, you should not store sensitive personal data on a corporate device.
Method 10: information from sensors
By analyzing the information received from the device's sensors, you can choose a password for the device using a special algorithm. Adam J. Smith Aviv demonstrated the possibility of such attacks using data obtained by the smartphone's accelerometer. In the course of research, the scientist was able to correctly determine the character password in 43% of cases, and the graphic password-in 73%
Security tip: keep a Close eye on which apps you grant permission to track various sensors.
Method 11: face unlock
As with a fingerprint, the success of unlocking a device using FaceID technology depends on what sensors and what mathematical apparatus are used in a particular mobile device. So, in the work "Gezichtsherkenning op smartphone niet altijd veilig", researchers showed that some of the studied smartphones were unlocked simply by showing the smartphone camera a photo of the owner. This is possible when only one front-facing camera is used for unlocking, and it does not have the ability to scan image depth data.

More advanced smartphone models can be unlocked by using a mask or self-learning device. For example, the iPhone X uses a special TrueDepth technology: the device's projector, using two cameras and an infrared emitter, projects a grid consisting of more than 30,000 dots on the owner's face. Such a device can be unlocked by using a mask, the contours of which mimic the contours of the owner's face. Mask for unlocking your iPhone:

Since such a system is very complex and does not work in ideal conditions (natural aging of the wearer occurs, changes in the configuration of the face due to the expression of emotions, fatigue, health status, etc.), it is forced to constantly self-study. Therefore, if another person holds the unlocked device in front of them, their face will be remembered as the face of the device owner, and in the future they will be able to unlock the smartphone using FaceID technology.
Protection recommendation: do not use photo unlocking only systems with full-fledged face scanners (Apple's FaceID and analogs on Android devices).
The main recommendation is not to look at the camera, just look away. Even if you close one eye the chance to unlock it drops dramatically, just like if you have hands on your face. In addition, to unlock by face (FaceID), only 5 attempts are given, after which you will need to enter a password code.
Method 12: using leaks
Databases of leaked passwords are a great way to understand the psychology of the device owner (provided that the researcher has information about the email addresses of the device owner). In this example, a search for the email address returned two similar passwords that the owner used. It can be assumed that the password 21454162 or its derivatives (for example, 2145 or 4162) could be used as a mobile device lock code.

Security advice: act proactively, track data about leaks, and change passwords detected in leaks in a timely manner!
Method 13: typical device lock passwords
As a rule, several mobile devices are confiscated from the owner, rather than one. There are often dozens of such devices. At the same time, you can choose a password for the vulnerable device and try to apply it to other smartphones and tablets seized from the same owner.
When analyzing data extracted from mobile devices, such data is displayed in forensic programs (often even when data is extracted from blocked devices using various types of vulnerabilities).
As you can see in the screenshot of part of the UFED Physical Analyzer working window, the device is locked with a rather unusual PIN code fgkl.
Do not neglect other user devices. For example, by analyzing passwords stored in the cache of the web browser of the mobile device owner's computer, you can understand the principles of password generation that the owner followed. You can view saved passwords on your computer using the NirSoft utility.
There may also be Lockdown files on the mobile device owner's computer (laptop) that can help you gain access to a locked Apple mobile device. This method will be discussed later.
Security recommendation: use different, unique passwords everywhere.
Method 14: typical PIN codes
As noted earlier, users often use standard passwords: phone numbers, Bank cards, and PIN codes. You can use this information to unlock the provided device.
If all else fails you can use the following information: the researchers analyzed and found the most popular PIN codes (these PIN codes cover 26.83% of all passwords):

Applying this list of PIN codes to a locked device will allow you to unlock it with a probability of ~26%.
Security tip: check your PIN code using the table above and even if it doesn't match, change it anyway, because 4 digits is too small by 2020 standards.
Method 15: typical graphic passwords
As described above, if you have data from surveillance cameras where the device owner tries to unlock it, you can select the unlock pattern from five attempts. In addition, just as there are standard PIN codes, there are also standard patterns that can be used to unlock blocked mobile devices.
Simple patterns

Patterns of medium difficulty

Complex patterns

A list of the most popular graphic patterns according to researcher Jeremy Kirby.
On some mobile devices, in addition to the graphic code, an additional PIN code can be set. In this case, if the graphic code cannot be selected, the researcher can click on the Additional PIN (additional PIN) button after entering the wrong graphic code and try to select an additional PIN.
Security recommendation: it is better not to use graphic keys at all.
Method 16: alphanumeric passwords
If an alphanumeric password can be used on the device, then the owner could use the following popular passwords as a lock code:
- 123456
- password
- 123456789
- 12345678
- 12345
- 111111
- 1234567
- sunshine
- qwerty
- iloveyou
- princess
- admin
- welcome
- 666666
- abc123
- football
- 123123
- monkey
- 654321
- !@#$%^&*
- charlie
- aa123456
- donald
- password1
- qwerty123
Security recommendation: use only complex, unique passwords with service characters and different cases. Make sure that you don't use one of the passwords listed above. If you use it, change it to a more reliable one.
Method 17: cloud or local storage
If it is not technically possible to remove data from a locked device, criminologists can search for its backup copies on the device owner's computers or in the corresponding cloud storage facilities.
Often, when owners of Apple smartphones connect them to their computers, they don't realize that a local or cloud backup of the device may be created at this time.
Google and Apple cloud storages can store not only data from devices, but also passwords saved by the device. Extracting these passwords can help you find the mobile device lock code.
From the Keychain stored in iCloud, you can extract the password for the backup copy of the device set by the owner, which, with a high degree of probability, will match the PIN code of the lock screen.
If law enforcement agencies contact Google and Apple, the companies can transfer the available data, which will probably greatly reduce the need to unlock the device, since law enforcement officers will already have the data.
For example, after the terrorist attack, copies of data stored in iCloud were transferred to the FBI. From the Apple statement:
"Within hours of the FBI's first request, on December 6, 2019, we provided a wide range of information related to the investigation. From December 7 to December 14, we received six additional legal requests and in response provided information, including iCloud backups, account information, and transactions for multiple accounts.
We responded to each request immediately, often within hours, exchanging information with the FBI offices in Jacksonville, Pensacola, and New York. At the request of the investigation, many gigabytes of information were received, which we passed on to the investigators."
Security tip: anything you send to the cloud in unencrypted form can and will be used against you.
Method 18: Google account
This method is suitable for removing a graphical password that blocks the screen of a mobile device running the Android operating system. To use this method, you need to know the user name and password from the Google account of the device owner. Second condition: the device must be connected to the Internet.
If you repeatedly enter the wrong graphic password several times in a row, the device will prompt you to restore the password. After that, you need to log in to the user's account, which will unlock the device screen.
Due to the variety of hardware solutions, Android operating systems, and additional security settings, this method is only applicable for a number of devices.
If the researcher doesn't have a password to the Google account of the device owner, you can try to restore it using standard methods for recovering passwords from similar accounts.
If the device is not connected to the Internet at the time of the study (for example, the SIM card is blocked or there is not enough money on it), then you can connect such a device to Wi-Fi using the following instructions:
- click the "Emergency call" icon»
- dial *#*#7378423#*#*
- select Service Test-Wlan
- connect to an available Wi-Fi network
Security recommendation: don't forget to use two factor authorization wherever you can, and in this case, it's better to link to the app, rather than using an SMS code.
Method 19: guest account
There can be multiple accounts on mobile devices running the Android 5 and higher operating system. Access to the data of an additional account may not be blocked by a PIN or graphic code. To switch, click on the account icon in the upper-right corner and select a different account:
For an additional account, access to some data or applications may be restricted.
Security recommendation: it is important to update the OS here. In modern versions of Android (9 and higher with security patches from July 2020), the guest account usually does not provide any features.
Method 20: specialized services
Companies that develop specialized forensic software, including those that offer services for unlocking mobile devices and extracting data from them. The capabilities of such services are fantastic. You can use them to unlock top models of Android and iOS devices, as well as devices that are in recovery mode (which the device switches to after exceeding the number of attempts to enter the wrong password). The disadvantage of this method is the high cost.
A fragment of the Cellebrite website page that describes which devices they can extract data from. The device can be unlocked in the developer's lab (Cellebrite Advanced Service (CAS)):

For such a service, the device must be provided to the company's regional (or head) office. Possible departure of a specialist to the customer. As a rule, hacking the screen lock code takes one day.
Protection recommendation: it is almost impossible to protect yourself, except for using a strong numeric-letter password and changing devices every year.
habrastorage.org

