Friend
Professional
- Messages
- 2,677
- Reaction score
- 1,096
- Points
- 113
The story of "J. P. Morgan" stretches from an elite hacker to a prime suspect.
In Spain, Maxim Silnikov was arrested and extradited to the United States, who is accused of creating a Ransom Cartel ransomware distribution campaign and organizing a large-scale malicious advertising scheme that operated from 2013 to 2022.
Maxim Silnikov, 38, who goes by the pseudonyms "J. P. Morgan", "xxx" and "lansky" on hacker forums, has attracted the attention of intelligence agencies for his involvement in major cyber attacks. According to the UK intelligence services, Silnikov and his accomplices are elite cybercriminals who used strict measures to ensure their own security on the network in order to avoid capture.
In the latest case, Silnikov is accused of creating and managing the Ransomware-as-a-Service (RaaS) scheme, which was actively used to attack companies and individuals. Silnikov's important role was played by negotiating with Initial Access Brokers (IAB), which provided access to compromised corporate networks, as well as managing communications with victims and processing ransoms. Silnikov was involved in laundering money from ransoms through cryptocurrency mixers to hide traces of financial transactions and complicate the work of law enforcement agencies.
In addition, Silnikov was responsible for creating Reveton, a Trojan that blocked access to Windows and demanded a ransom for unlocking it. The malware posed as a tool of law enforcement agencies. The Trojan blocked the computer under the pretext of detecting child pornography and copyrighted materials. From its launch in 2011 to 2014, Reveton brought in about $400,000 a day to various cybercriminals.
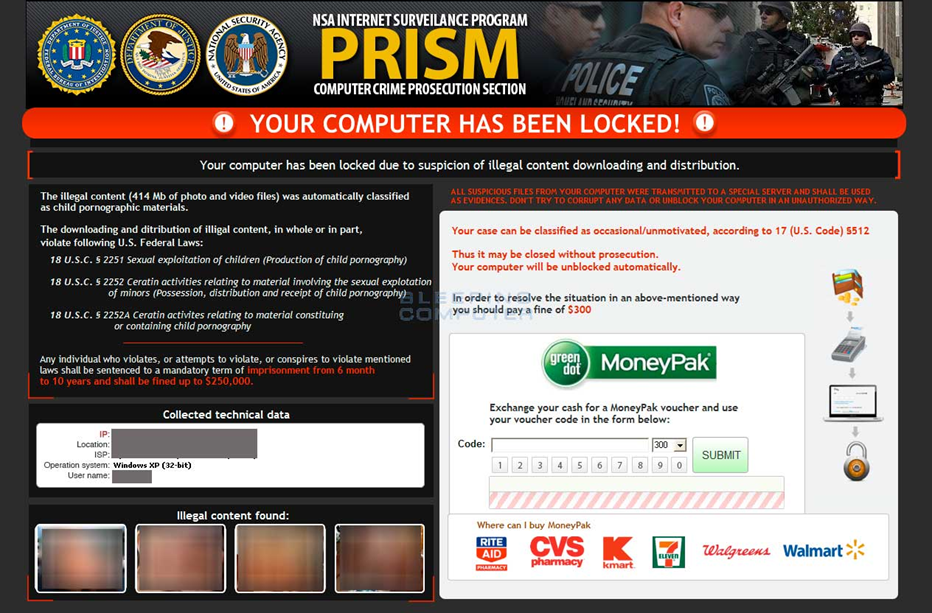
Example of blocking access to a computer under the guise of the NSA
Silnikov's malvertising activities (from October 2013 to March 2022) also proved to be large-scale and disruptive. Silnikov's task was to develop and distribute malicious ads that seemed harmless, but in fact redirected users to sites with viruses and malware.
The following tools were used in the malvertising campaign:
At its peak, the Angler Exploit Kit accounted for 40% of all exploit infections in the world and brought criminals about $34 million a year. More than 500 million users worldwide became victims of the attacks.
Silnikov also participated in the development and maintenance of a technical infrastructure, a traffic distribution system (TDS), to better manage and detect malicious campaigns.
During the international operation, NCA employees, together with colleagues from Ukraine, Portugal and Singapore, conducted searches, seized more than 50 terabytes of data and installed the infrastructure used to manage ransomware. The collected data will be used for further investigations and prosecution of other members of the criminal group.
Maxim Silnikov faces a sentence for fraud, computer crimes, identity theft and other crimes. If convicted on all charges, Silnikov could face up to 100 years in prison, although the actual sentence is likely to be shorter due to the possibility of serving multiple sentences at the same time.
Operation Ransom Cartel, launched in December 2021, shares many similarities with the REvil grouping code. Palo Alto Networks specialists reported a suspicious connection between Ransom Cartel and REvil. According to the study, Ransom Cartel started its operations just 2 months after the collapse of REvil. Then experts noted that Ransom Cartel operators have access to the source code of the REvil cryptographer, but they do not have an obfuscation mechanism in their arsenal, which is used to encrypt strings and hide API calls.
In 2019, a member of the cybercrime group that distributed the Reveton ransomware was sentenced in the UK to 6 years in prison and a fine of $355,000. According to the investigation, the 25-year-old student has been associated with the notorious Lurk group for 6 years.
Source
In Spain, Maxim Silnikov was arrested and extradited to the United States, who is accused of creating a Ransom Cartel ransomware distribution campaign and organizing a large-scale malicious advertising scheme that operated from 2013 to 2022.
Maxim Silnikov, 38, who goes by the pseudonyms "J. P. Morgan", "xxx" and "lansky" on hacker forums, has attracted the attention of intelligence agencies for his involvement in major cyber attacks. According to the UK intelligence services, Silnikov and his accomplices are elite cybercriminals who used strict measures to ensure their own security on the network in order to avoid capture.
In the latest case, Silnikov is accused of creating and managing the Ransomware-as-a-Service (RaaS) scheme, which was actively used to attack companies and individuals. Silnikov's important role was played by negotiating with Initial Access Brokers (IAB), which provided access to compromised corporate networks, as well as managing communications with victims and processing ransoms. Silnikov was involved in laundering money from ransoms through cryptocurrency mixers to hide traces of financial transactions and complicate the work of law enforcement agencies.
In addition, Silnikov was responsible for creating Reveton, a Trojan that blocked access to Windows and demanded a ransom for unlocking it. The malware posed as a tool of law enforcement agencies. The Trojan blocked the computer under the pretext of detecting child pornography and copyrighted materials. From its launch in 2011 to 2014, Reveton brought in about $400,000 a day to various cybercriminals.

Example of blocking access to a computer under the guise of the NSA
Silnikov's malvertising activities (from October 2013 to March 2022) also proved to be large-scale and disruptive. Silnikov's task was to develop and distribute malicious ads that seemed harmless, but in fact redirected users to sites with viruses and malware.
The following tools were used in the malvertising campaign:
- Angler Exploit Kit (AEK): designed to exploit vulnerabilities in web browsers and plug-ins installed in them in order to deliver additional payloads to compromised devices.
- Locker malware: A "lightweight" ransomware program that prevents the victim from accessing their data, often requiring a fee to restore access.
- Scareware: They bombard the victim's computer with fake alerts, prompting the user to download malware or provide personal information to cybercriminals.
At its peak, the Angler Exploit Kit accounted for 40% of all exploit infections in the world and brought criminals about $34 million a year. More than 500 million users worldwide became victims of the attacks.
Silnikov also participated in the development and maintenance of a technical infrastructure, a traffic distribution system (TDS), to better manage and detect malicious campaigns.
During the international operation, NCA employees, together with colleagues from Ukraine, Portugal and Singapore, conducted searches, seized more than 50 terabytes of data and installed the infrastructure used to manage ransomware. The collected data will be used for further investigations and prosecution of other members of the criminal group.
Maxim Silnikov faces a sentence for fraud, computer crimes, identity theft and other crimes. If convicted on all charges, Silnikov could face up to 100 years in prison, although the actual sentence is likely to be shorter due to the possibility of serving multiple sentences at the same time.
Operation Ransom Cartel, launched in December 2021, shares many similarities with the REvil grouping code. Palo Alto Networks specialists reported a suspicious connection between Ransom Cartel and REvil. According to the study, Ransom Cartel started its operations just 2 months after the collapse of REvil. Then experts noted that Ransom Cartel operators have access to the source code of the REvil cryptographer, but they do not have an obfuscation mechanism in their arsenal, which is used to encrypt strings and hide API calls.
In 2019, a member of the cybercrime group that distributed the Reveton ransomware was sentenced in the UK to 6 years in prison and a fine of $355,000. According to the investigation, the 25-year-old student has been associated with the notorious Lurk group for 6 years.
Source

