Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,323
- Points
- 113
Experts reveal the strategy of a blitz attack against developers.
Over the past year, Phylum has been actively monitoring the actions of North Korean hackers who attack open source developers. The new report shows the case of an npm package that was published and removed from the site in 1.5 hours. The incident highlights that although hackers methods are being updated, the main attack patterns remain unchanged.
Call-blockflow, which briefly appeared on npm, is a modified version of the popular call-bind package (about 45 million weekly downloads). The new version retains all the main elements of the original, but changes the package file.json and new files have been added, which allows you to run malicious code when installing the package.
These actions were made possible by changes in the configuration file and the use of special scripts that are executed automatically and then deleted without leaving any traces.
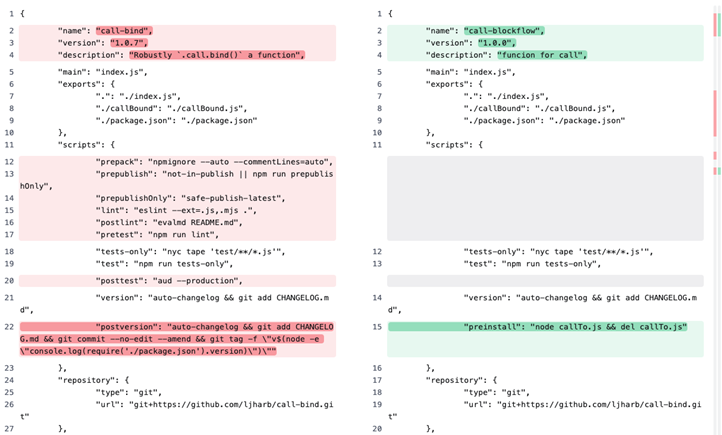
Package differences.json in the legitimate call-bind package (left) and malicious call-blockflow (right)
A key new feature in the attack is a script that runs in the Windows_NT environment and creates temporary files to execute malicious commands, after which these files are deleted. This approach helps hackers to remain undetected and enhances the stealth of the attack.
In addition to the technical aspects, it is important to note that although the "call-blockflow" package copies the trusted "call-bind" package, it does not pose a threat to users of the latter. npm and Phylum security systems respond quickly to such threats, blocking malicious packages before they can cause harm.
The malicious package "call-blockflow" was quickly removed from NPM, which corresponds to the quick publish and delete pattern used in this campaign. This tactic allows attackers to minimize the possibility of detecting and analyzing a malicious package.
The detected campaign is part of a broader strategy in which hackers either pose as legitimate developers of popular packages, or create new fake packages to distribute malware. By cloning already existing trusted repositories, attackers get an almost unlimited supply of trusted packages, which increases the probability of success of their attacks.
Source
Over the past year, Phylum has been actively monitoring the actions of North Korean hackers who attack open source developers. The new report shows the case of an npm package that was published and removed from the site in 1.5 hours. The incident highlights that although hackers methods are being updated, the main attack patterns remain unchanged.
Call-blockflow, which briefly appeared on npm, is a modified version of the popular call-bind package (about 45 million weekly downloads). The new version retains all the main elements of the original, but changes the package file.json and new files have been added, which allows you to run malicious code when installing the package.
These actions were made possible by changes in the configuration file and the use of special scripts that are executed automatically and then deleted without leaving any traces.

Package differences.json in the legitimate call-bind package (left) and malicious call-blockflow (right)
A key new feature in the attack is a script that runs in the Windows_NT environment and creates temporary files to execute malicious commands, after which these files are deleted. This approach helps hackers to remain undetected and enhances the stealth of the attack.
In addition to the technical aspects, it is important to note that although the "call-blockflow" package copies the trusted "call-bind" package, it does not pose a threat to users of the latter. npm and Phylum security systems respond quickly to such threats, blocking malicious packages before they can cause harm.
The malicious package "call-blockflow" was quickly removed from NPM, which corresponds to the quick publish and delete pattern used in this campaign. This tactic allows attackers to minimize the possibility of detecting and analyzing a malicious package.
The detected campaign is part of a broader strategy in which hackers either pose as legitimate developers of popular packages, or create new fake packages to distribute malware. By cloning already existing trusted repositories, attackers get an almost unlimited supply of trusted packages, which increases the probability of success of their attacks.
Source

