Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,324
- Points
- 113
The EvilVideo exploit allowed spreading viruses.
ESET researchers have discovered a zero-day exploit targeting Telegram for Android. An exploit called EvilVideo went on sale on an underground forum on June 6, 2024. Attackers used this vulnerability to spread malicious files through Telegram channels, groups, and chats, disguising them as multimedia files.
Experts were able to get an example of the exploit, which allowed us to analyze it and report the problem to Telegram on June 26. An update fixing the vulnerability was released on July 11, 2024 in Telegram versions 10.14.5 and higher.
The vulnerability allowed attackers to send malicious files that looked like videos in unprotected versions of Telegram for Android (10.14.4 and older). The exploit was found on an underground forum, where the seller demonstrated its work in a public Telegram channel. This allowed the researchers to obtain the malicious file and test it.
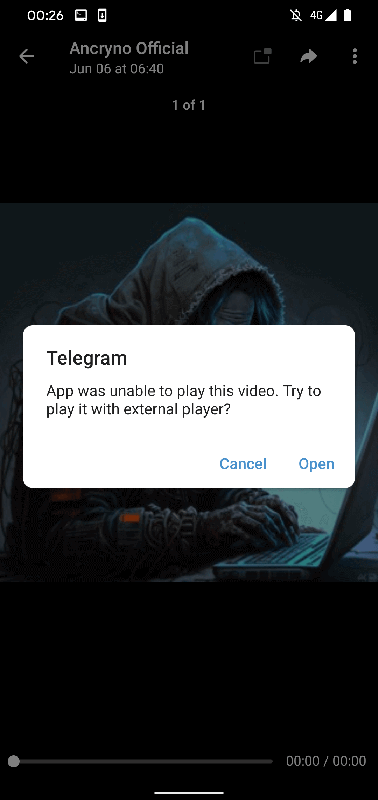
Telegram warns that it can't play "video"
Analysis showed that the exploit exploited the ability to create malicious files that were displayed as multimedia previews. When trying to play such a "video", Telegram reported that it could not play the file and suggested using an external player. When the "Open" button was clicked, the user was prompted to install a malicious application disguised as a player.

Telegram Web error message when an exploit is triggered
Telegram fixed the vulnerability in version 10.14.5. Now the preview of multimedia files correctly displays that the file is an application, and not a video.
The exploit was tested on the web version and the desktop client of Telegram for Windows, but it did not work. In both cases, the file was recognized as multimedia and did not pose a threat.
It also turned out that the seller of the exploit offered a cryptor service for Android, which makes malicious files invisible to antivirus programs. This service has been advertised on the same underground forum since January 2024.
After the vulnerability was discovered and reported in Telegram, the problem was fixed. Users are encouraged to update the app to the latest version to protect against potential threats.
Source
ESET researchers have discovered a zero-day exploit targeting Telegram for Android. An exploit called EvilVideo went on sale on an underground forum on June 6, 2024. Attackers used this vulnerability to spread malicious files through Telegram channels, groups, and chats, disguising them as multimedia files.
Experts were able to get an example of the exploit, which allowed us to analyze it and report the problem to Telegram on June 26. An update fixing the vulnerability was released on July 11, 2024 in Telegram versions 10.14.5 and higher.
The vulnerability allowed attackers to send malicious files that looked like videos in unprotected versions of Telegram for Android (10.14.4 and older). The exploit was found on an underground forum, where the seller demonstrated its work in a public Telegram channel. This allowed the researchers to obtain the malicious file and test it.

Telegram warns that it can't play "video"
Analysis showed that the exploit exploited the ability to create malicious files that were displayed as multimedia previews. When trying to play such a "video", Telegram reported that it could not play the file and suggested using an external player. When the "Open" button was clicked, the user was prompted to install a malicious application disguised as a player.

Telegram Web error message when an exploit is triggered
Telegram fixed the vulnerability in version 10.14.5. Now the preview of multimedia files correctly displays that the file is an application, and not a video.
The exploit was tested on the web version and the desktop client of Telegram for Windows, but it did not work. In both cases, the file was recognized as multimedia and did not pose a threat.
It also turned out that the seller of the exploit offered a cryptor service for Android, which makes malicious files invisible to antivirus programs. This service has been advertised on the same underground forum since January 2024.
After the vulnerability was discovered and reported in Telegram, the problem was fixed. Users are encouraged to update the app to the latest version to protect against potential threats.
Source

