Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
More and more hacker associations are using CVE-2023-46805 and CVE-2024-21887 in their attacks.
Earlier this month, we covered zero-day vulnerabilities in Ivanti products. A recent analysis by Mandiant revealed that attackers used 5 different malware families in their attacks, including Zipline, Thinspool Dropper, Wirefire, Lightwire, and Warpwire Harverster.
According to the latest data from Volexity specialists, on January 14 of this year, more than 1,700 compromised Connect Secure VPN devices were detected by the GIFFEDVISITOR web shell.
The list of victims includes public and private organizations around the world, including military institutions, national telecommunications companies, defense contractors, technology companies, banks, financial and accounting organizations, global consulting companies, as well as firms in the aerospace, aviation and engineering industries.
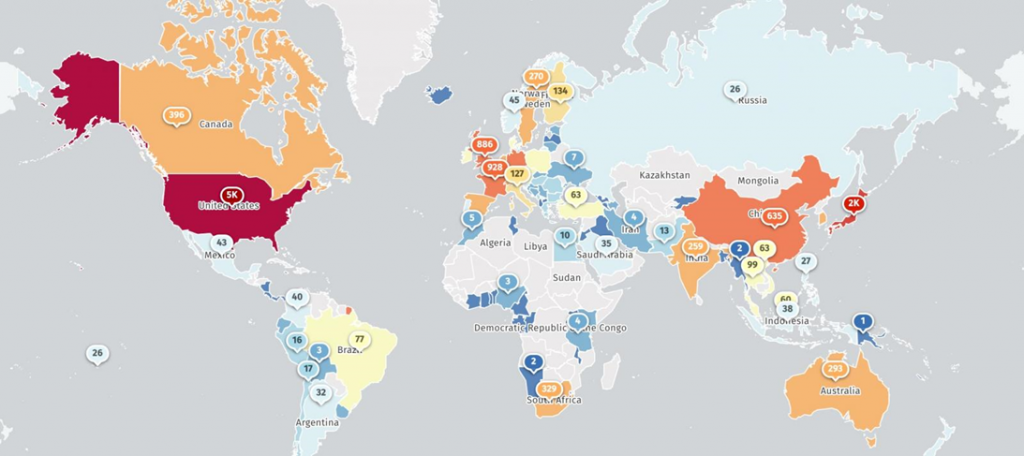
The Shadowserver threat monitoring service monitors more than 16,800 Connect Secure VPN devices around the world that are accessible from the Internet. Most of them (about 5,000) are located in the United States, but the threat is definitely global.
It is confirmed that attackers can execute arbitrary commands on all supported versions of VPN Connect Secure and Policy Secure devices, successfully combining two previously identified vulnerabilities CVE-2023-46805 and CVE-2024-21887 .
Meanwhile, in addition to previously suspected Chinese state hackers (UTA0178 or UNC5221), many new groups have joined the active exploitation of these vulnerabilities.
Ivanti has not yet released the necessary fixes, apparently the problem is more profound than it might have seemed earlier. Administrators are strongly encouraged to apply the mitigation measures provided by the company for all VPN devices on the network, as well as use the Ivanti Integrity Checker tool to detect signs of hacking.
Last July, two other Ivanti zero-day vulnerabilities ( CVE-2023-35078 and CVE-2023-35081 ) were used to hack several Norwegian government organizations, and a month later hackers began exploiting a third vulnerability ( CVE-2023-38035) in the Ivanti Sentry software to bypass API authentication.
Earlier this month, we covered zero-day vulnerabilities in Ivanti products. A recent analysis by Mandiant revealed that attackers used 5 different malware families in their attacks, including Zipline, Thinspool Dropper, Wirefire, Lightwire, and Warpwire Harverster.
According to the latest data from Volexity specialists, on January 14 of this year, more than 1,700 compromised Connect Secure VPN devices were detected by the GIFFEDVISITOR web shell.
The list of victims includes public and private organizations around the world, including military institutions, national telecommunications companies, defense contractors, technology companies, banks, financial and accounting organizations, global consulting companies, as well as firms in the aerospace, aviation and engineering industries.
The Shadowserver threat monitoring service monitors more than 16,800 Connect Secure VPN devices around the world that are accessible from the Internet. Most of them (about 5,000) are located in the United States, but the threat is definitely global.

It is confirmed that attackers can execute arbitrary commands on all supported versions of VPN Connect Secure and Policy Secure devices, successfully combining two previously identified vulnerabilities CVE-2023-46805 and CVE-2024-21887 .
Meanwhile, in addition to previously suspected Chinese state hackers (UTA0178 or UNC5221), many new groups have joined the active exploitation of these vulnerabilities.
Ivanti has not yet released the necessary fixes, apparently the problem is more profound than it might have seemed earlier. Administrators are strongly encouraged to apply the mitigation measures provided by the company for all VPN devices on the network, as well as use the Ivanti Integrity Checker tool to detect signs of hacking.
Last July, two other Ivanti zero-day vulnerabilities ( CVE-2023-35078 and CVE-2023-35081 ) were used to hack several Norwegian government organizations, and a month later hackers began exploiting a third vulnerability ( CVE-2023-38035) in the Ivanti Sentry software to bypass API authentication.

