Chapter 1: Windows 7 main, Must Have Soft, Carding Soft (Prepare your anus)
November 08, 2017
Let's start learning!
It is based on the idea of maximum simplicity and maximum money saving. If you are pinned to buy some software, services, or something else and you have extra money for it - the author is only happy for you. But newcomers do not have such an opportunity, given the current dollar exchange rate and the situation with work.Perhaps it will seem to someone that this article contains a lot of water, or unnecessary information.
In the article, we start from the maximum savings, but do not forget about the minimum security. There will be no purchases of VPN, Dedicated servers, software at first. We have no money for this. But we will have to buy cards, socks, SSH tunnels, since the extraction of this material will be discussed in another article. In the future, there will be articles about hacking a store, or about extracting SSH tunnels, soon such articles will appear here.
For the reader:
If you decide to take up carding, then you need a passable knowledge of the English language, computer skills at the level of an experienced user and, most importantly, a desire with patience. Good luck.
Part 1: Windows 7 main
The first thing to start with is creating a working machine. First, we need a laptop with at least an i3, 4gb Ram processor. It is a laptop, not a desktop PC, since a laptop is much safer than a PC for a number of reasons (more on that at the end of the article). If you don't have a laptop, that's okay, but get one.
We'll start by installing the original Windows 7 image, without any cracks or anything else. To do this, follow this link: http://rutracker.org/forum/viewtopic.php?t=4529698
Download Windows 7 Ultimate x64. Before proceeding with the installation, make sure to write all the necessary drivers for your device (on which you will install Windows) to any removable media.
Reinstalling Windows is necessary so that you have a clean system at your disposal and we set it up from scratch. From the moment you start installing Windows, your device will no longer be suitable for anything other than illegal work. If you work somewhere else where you need the Internet, buy another device, or forget about any social networks and so on.
The original image is needed so that in the future there are no problems with installing additional libraries that will be needed in the work. Leave the various assemblies to the students, as the assembly is often truncated, and various services are removed from it, which may be useful in the future. The authors of the assemblies add their software and utilities to these assemblies, which we do not need at the stage of work.
So format your hard drive and install fresh Windows and drivers and read on. If you are not able to install Windows on your laptop yourself, further reading will not help you. Go get some PC experience.
Part 2: Must Have Soft
After installation, any system requires minimal configuration and mandatory software, without which work is impossible. In our case, the set of software will be minimal.
Download Google Chrome immediately after installation. Not Firefox or Opera, but Google Chrome - https://www.google.ru/chrome/browser/
Now a little about setting up Windows itself (Chrome will wait).
Right-click on the Start bar and select Properties. Uncheck the checkbox: Use Aero Peek ..., click Apply, and then click the Notification Area -> Customize button and select the Always display checkbox ... This is necessary in order to see quickly and without problems what is running in the tray , and see instant notifications.
I also recommend choosing the settings in the Start panel settings: Use small icons and Taskbar buttons -> Do not group.
After downloading Chrome, go to the main software, which you need to download and install:
1. WinRar - http://www.rarlab.com/download.htm - software for working with archives. Must Have.
2. TotalCommander - http://www.ghisler.com/download.htm - file manager, as well as Must Have software for working with various information. Without it, no way in the future.
3. Notepad ++ - https://notepad-plus-plus.org/download/v6.8.3.html is the best text editor. After installing it, do the following:
Options - Settings - File Association and add files with extensions as in the screenshot to Registered. In the future, we will only use Notepad ++ for editing files and other things.
4.uTorrent - http://www.utorrent.com/intl/ - torrent rocking chair, without it anywhere.
Don't forget to uncheck the boxes:
5. KeePass - http://keepass.info/download.html is a useful program for storing passwords. It is important to use different passwords everywhere, and it is also better to generate them using the program itself. These passwords are harder to crack.
6. Oracle VM VirtualBox - https://www.virtualbox.org/wiki/Downloads - virtual machine for further work. There is a lot of debate about choosing VMWare or VirtualBox, but I prefer VirtualBox, so we will use it.
7. DAEMON Tools Lite 10 - http://www.daemon-tools.cc/rus/downloads - a program for working with images. An extremely useful thing.
This concludes with Must Have Soft. We put only this, do not forget to uncheck the suggestions for installing additional software. We don't use any keygens or cracks. In most cases, the software is free, or not very annoying with the offer to buy it. You don't need to put anything in addition, just this.
Part 3: Carding Soft (Prepare your anus)
After we have installed all the necessary software for minimal work with a PC, we switch to the software that we need to interact with the carding community. Since we use the homeless option and do not have extra money, we will create our security with minimal effort.
To visit forums and, in general, any platforms related to carding, download the Tor Browser - https://www.torproject.org/projects/torbrowser.html.en
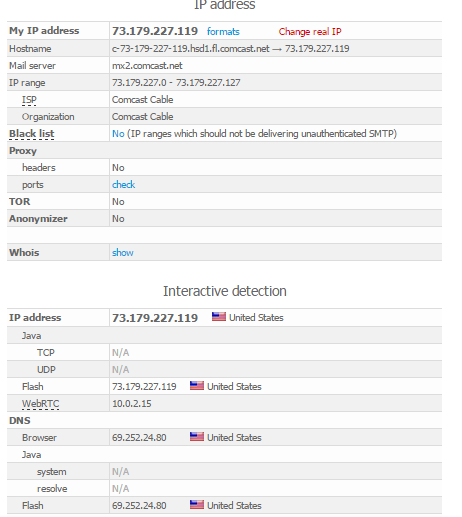
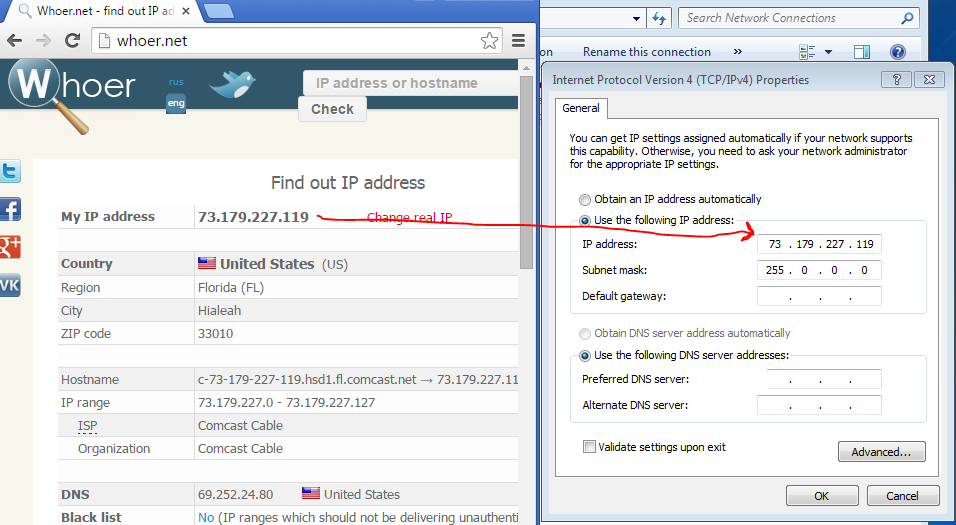
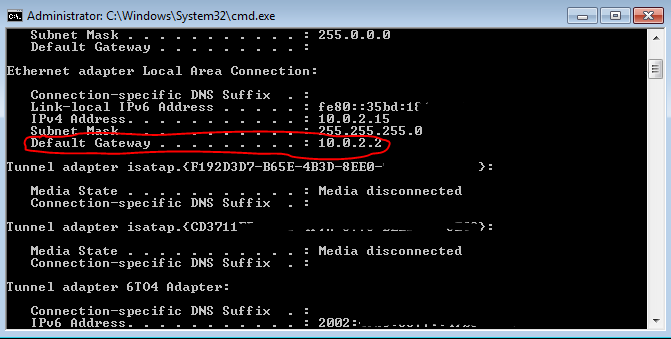
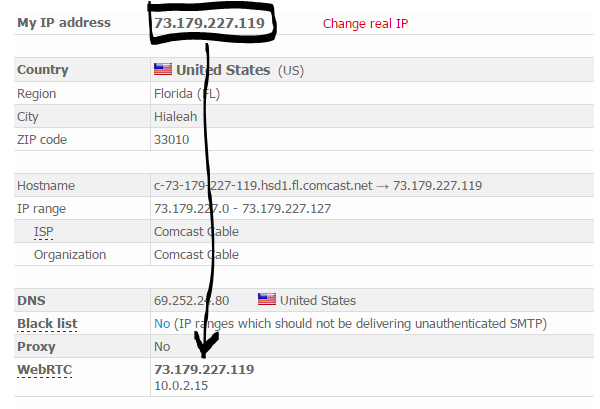
After installation, go to http://www.whoer.net and take a look. Should not be fired anywhere.
With the help of this browser, we register on all forums that we need, and use only it. Importantly, when registering, most forums ask you to enter your email address. Use the service directly from TOR Browser: https://10minutemail.com/10MinuteMail/index.html
This is a 10 minute email. In general, try to use it for any registrations. And in order not to forget your password, do not forget to generate and save passwords using the KeePass program that we downloaded earlier. The main thing is not to leave any traces about yourself on the forums. Even if the base is removed, all the hackers will have: MD5 hash of your complex password, some left email (which you also used with TOR Browser), and left IP addresses, again because of TOR Browsera.
Do not under any circumstances neglect using this browser to surf the internet if you are carding. Particularly smart ones who will shout that this browser is under FBI / CIA / MI6 / ETC ... send in the direction of santa claus pipiski. We do not give a fuck about who this browser is, we would not shine our IP yet. And since we are newbies, few people are interested in us.
Now let's move on to an equally important aspect - a means of communication. We will have to communicate with people. Jabber is best suited for this business. Forget about Skype, ICQ, Viber, Telegram and more. If the right person does not have Jabber, we don't need him, let him go to hell.
We use the Jabber client Psi + - http://psi-plus.com/wiki/ru:downloads#%D0%...D0%B2%D1%8B_psi - a handy thing with a bunch of useful plugins. Let's dwell on its setting in more detail.
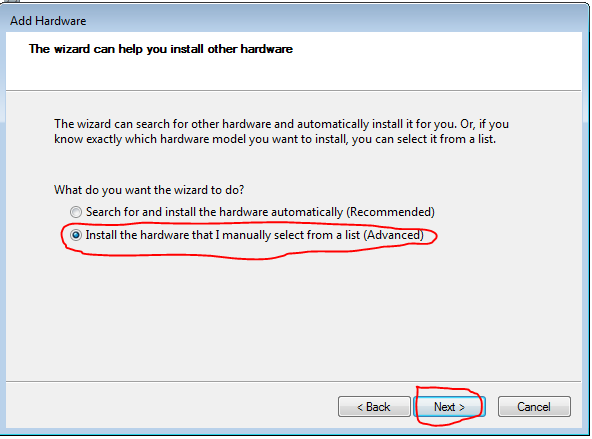
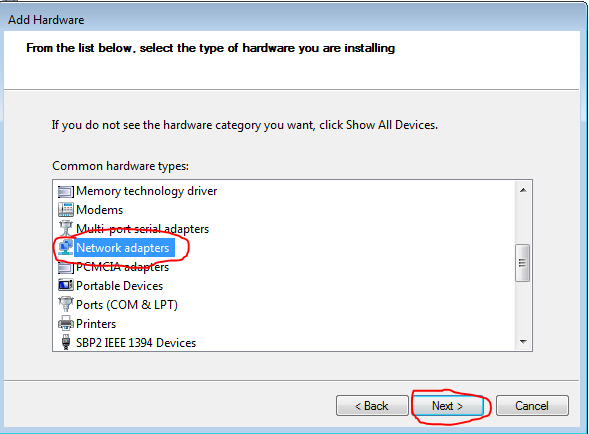
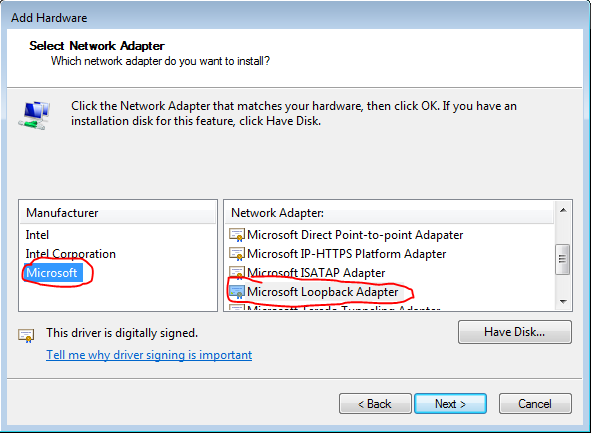
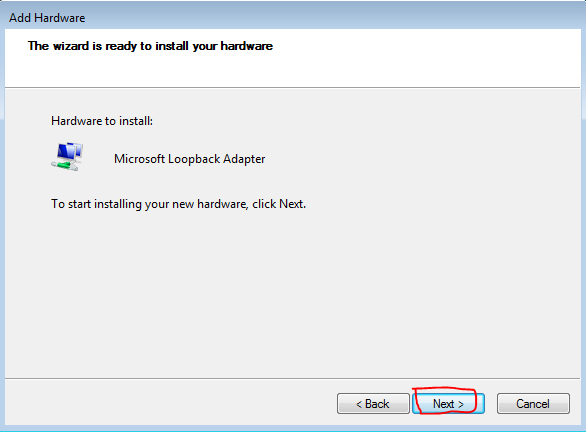
After installation, we need to create an account and select the server on which our account will run:
In the server field, specify - exploit.im
The choice falls on him, since at the moment he is the most relevant and reliable (in the opinion of the author).
Now let's move on to setting up.
The first thing we need to configure is OTR (Off-the-Record Messaging (OTR)), a cryptographic protocol for instant messaging systems created in 2004 by Nikita Borisov and Ian Goldberg.
Everything is simple here:
>> Settings -> Plugins -> Off-The-Record messaging plugin -> Activate the checkbox -> Click on the settings icon -> Generate a new key.
In the picture I have depicted everything, even a child can figure it out.
At this stage, we will not bother with PGP, in most cases few people use it. For now, enough OTR. To activate OTR, when working with a new contact, click on the icon:
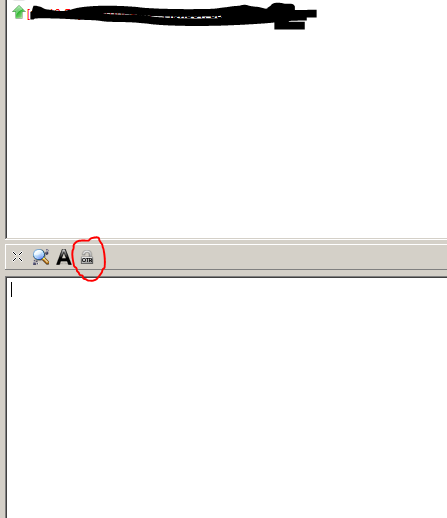
And choose Start Private Chat.
Oddly enough, before this is enough for work. Psi + and TorBrowser. VPN, TrueCrypt and so on, we will put in other articles, since now we have nothing to hide, and our first work will be connected only with electronic things and stuff. When we start hacking, uploading and muddying something else, then we'll talk about encryption in more detail. It's a waste of time for a beginner to bother with this.
Now let's configure a little more, turn off the virtual machine, and go to configure.
Go to the tab: General -> Advanced -> Shared Clipboard -> Bidirectional.
Go to the tab: System -> Processor -> Processors and select 2 cores
Go to the tab: Display -> Video -> Video memory -> change to 128MB. Also put the checkboxes Enable 2D acceleration and Enable 3D acceleration.
Go to the tab: Shared folders -> Click on add, also activate Auto-connect. Specify the folder on any disk, this will be a shared folder through which we will upload files to our virtual machine.
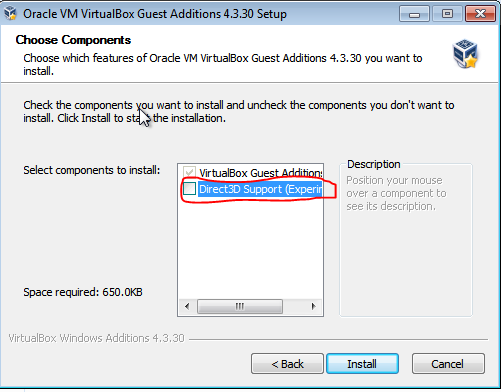
We also need to install the Guest OS Add-ons. To do this, click on Devices -> Connect ...
Just click Next -> Next, but don't forget to check DirectSupport 3D, then No -> Ok:
That's all for now, let's move on to the next chapter.