Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
Phishing
The bottom line is that the thief registers a domain that is almost identical to the domain in the bitcoin wallet.
We open it, and we are automatically redirected to a phishing site. The resource looks no different from the official one, only the domain has changed the three letters "kch" to "rcn". Instead of "blockchain.com" — "blockrcnain.com":
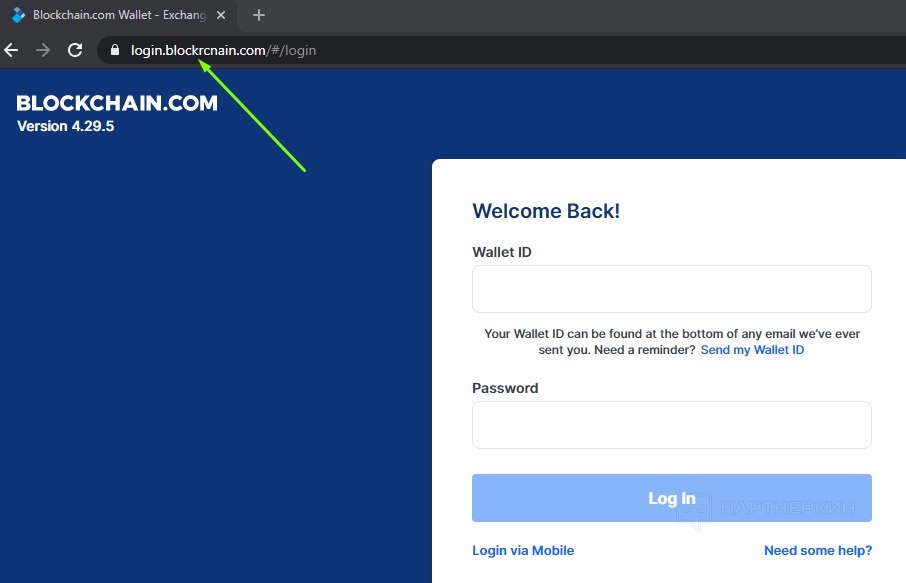
If you enter your ID and password on such a site, an attacker can easily write off all funds.
In order not to fall for this method of divorce, it will be enough to store all the sites in bookmarks or in notes.)
Mobile apps
The bottom line is that an attacker creates an app and uploads it to the GOOGLE MARKET. The user finds it through a search, then enters all their data and sends it to the thief. Here is an example of such applications:

And here are the reviews about them.
In order not to fall for such tricks, you need to search not in the app search, but follow links from the official site. In the same Blockchain, there are only 2 links, one to Google Play, the other to the App Store. I wouldn't risk installing other apps, even if they have a 5-star rating and all the reviews are positive. Now everything can be screwed up, so this is not an indicator.
Browser Extensions
The bottom line is that the thief creates extensions with the same interface as in the Trezor, Metamask, or Ledger cryptocurrency wallet. The main goal is to get a person to highlight their seed phrase. You can use this phrase to restore access to your wallet and withdraw the crypt. For example, if you go to the Chrome web store and enter "Metamask" in the search, we see 3 wallets, 1 real and 2 more from unknown authors, which I would not install.
Despite the fact that Google employees regularly remove fraudulent extensions, new ones still appear
QR Code theft
Crypto wallets have a QUAR code that looks like this.

If an attacker scans it, they can easily withdraw money from your wallet. On the vast expanses of the Internet, there are a lot of schemes for how to lure it out (enable C) NEVER SHOW IT TO ANYONE!
Clipper
Clipper-a program that replaces wallet addresses in the clipboard. For example, if you need to transfer money, you copy your wallet number, and
Clipper automatically replaces it with the fraudster's wallet.
Once a person wrote to me in a social network, introduced himself as my referral and said that he had an error in the project, so I looked at the screen. But instead of a screen, it gave me a link to
download an unknown program. As it turned out, it was exactly the same Clipper Ship. It's a pity the correspondence wasn't saved, as I blocked it and deleted the program. For myself, I decided that if someone gives some links, it is better not to click on them. Also, before sending cryptocurrency, I check the first and last digits of the wallet.
Exchange fraud
There are good exchanges where people earn money on commissions. But there are sites that work and at one point throw everyone and take your money (and not just yours, but the entire site). And the site bursts like a soap bubble.
In order not to lose crypto on fraudulent exchanges, you need to trade on large platforms that have been operating for years. It is also better not to store money on exchanges. Hardware wallets are suitable for storage.
Replacing the SIM card
There have already been several cases of hackers stealing money by replacing the SIM card.
In order not to lose the crypt in this way, it is better to buy a separate SIM card for all important wallets and not give anyone a phone number.
Here you have learned about several ways to steal bitcoins, and these are not all ways.
The bottom line is that the thief registers a domain that is almost identical to the domain in the bitcoin wallet.
We open it, and we are automatically redirected to a phishing site. The resource looks no different from the official one, only the domain has changed the three letters "kch" to "rcn". Instead of "blockchain.com" — "blockrcnain.com":

If you enter your ID and password on such a site, an attacker can easily write off all funds.
In order not to fall for this method of divorce, it will be enough to store all the sites in bookmarks or in notes.)
Mobile apps
The bottom line is that an attacker creates an app and uploads it to the GOOGLE MARKET. The user finds it through a search, then enters all their data and sends it to the thief. Here is an example of such applications:

And here are the reviews about them.
In order not to fall for such tricks, you need to search not in the app search, but follow links from the official site. In the same Blockchain, there are only 2 links, one to Google Play, the other to the App Store. I wouldn't risk installing other apps, even if they have a 5-star rating and all the reviews are positive. Now everything can be screwed up, so this is not an indicator.
Browser Extensions
The bottom line is that the thief creates extensions with the same interface as in the Trezor, Metamask, or Ledger cryptocurrency wallet. The main goal is to get a person to highlight their seed phrase. You can use this phrase to restore access to your wallet and withdraw the crypt. For example, if you go to the Chrome web store and enter "Metamask" in the search, we see 3 wallets, 1 real and 2 more from unknown authors, which I would not install.
Despite the fact that Google employees regularly remove fraudulent extensions, new ones still appear
QR Code theft
Crypto wallets have a QUAR code that looks like this.

If an attacker scans it, they can easily withdraw money from your wallet. On the vast expanses of the Internet, there are a lot of schemes for how to lure it out (enable C) NEVER SHOW IT TO ANYONE!
Clipper
Clipper-a program that replaces wallet addresses in the clipboard. For example, if you need to transfer money, you copy your wallet number, and
Clipper automatically replaces it with the fraudster's wallet.
Once a person wrote to me in a social network, introduced himself as my referral and said that he had an error in the project, so I looked at the screen. But instead of a screen, it gave me a link to
download an unknown program. As it turned out, it was exactly the same Clipper Ship. It's a pity the correspondence wasn't saved, as I blocked it and deleted the program. For myself, I decided that if someone gives some links, it is better not to click on them. Also, before sending cryptocurrency, I check the first and last digits of the wallet.
Exchange fraud
There are good exchanges where people earn money on commissions. But there are sites that work and at one point throw everyone and take your money (and not just yours, but the entire site). And the site bursts like a soap bubble.
In order not to lose crypto on fraudulent exchanges, you need to trade on large platforms that have been operating for years. It is also better not to store money on exchanges. Hardware wallets are suitable for storage.
Replacing the SIM card
There have already been several cases of hackers stealing money by replacing the SIM card.
In order not to lose the crypt in this way, it is better to buy a separate SIM card for all important wallets and not give anyone a phone number.
Here you have learned about several ways to steal bitcoins, and these are not all ways.

