Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
Greetings, friends. Not so long ago, attackers started placing malicious packages in the PyPI repository, disguising various malicious programs as legal components. This campaign has not yet been stopped, and the number of affected developers is currently unknown for sure.
This was not the end of it, the attack on PyPI gave rise to a new meta among the attackers, and this time the public NPM repository was affected.

NPM is a standard package manager that is automatically installed along with Node.js. It is used to download packages from the npm cloud server, or to upload packages to these servers.
However, the methodology of this campaign is slightly different from what we saw earlier: no one uploaded viruses directly to NPM, attackers took advantage of the high reputation of open source sources in search engines and promoted malicious sites, as well as utilities with malicious stuffing through this repository.
There are several vectors of attacks using NPM:
A DoS attack is a hacker attack on a computer system in order to bring it to failure, that is, creating conditions under which bona fide users of the system will not be able to access the provided system resources (servers), or this access will be difficult.
According to a report from Checkmarx, several hackers may be behind this campaign and their ultimate goal is to spread malware such as RedLine Stealer (80%), Glupteba (12%), Smoke Loader (5%) and XMRig (2%).
Redline is particularly dangerous due to a sharp increase in the number of infections, so today we will analyze and analyze it.
RedLine Stealer can steal the following information: usernames, passwords, autofill data, cookies, and credit card information from all web browsers. Cybercriminals can misuse this information to access various accounts (for example, social networks, email, bank accounts, cryptocurrency wallets).
The list of e-wallets targeted by the RedLine hijacker includes Armory, AtomicWallet, BitcoinCore, Bytecoin, DashCore, Electrum, Ethereum, LitecoinCore, Monero, Exodus, Zcash, and Jaxx. The target VPN clients are ProtonVPN, OpenVPN, and NordVPN.
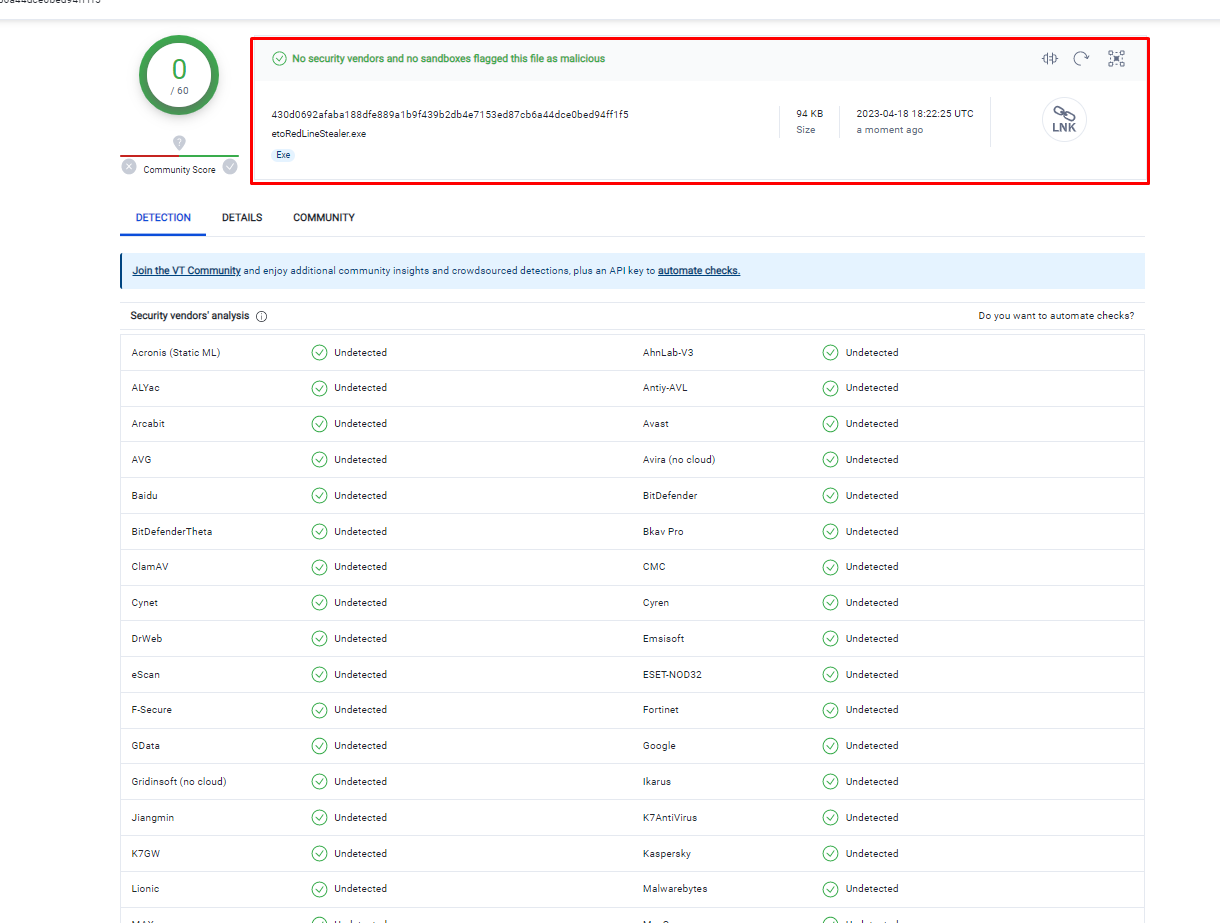
For analysis, we will use a sample dated April 14, 2023. On VirusTotal, it looks like this:
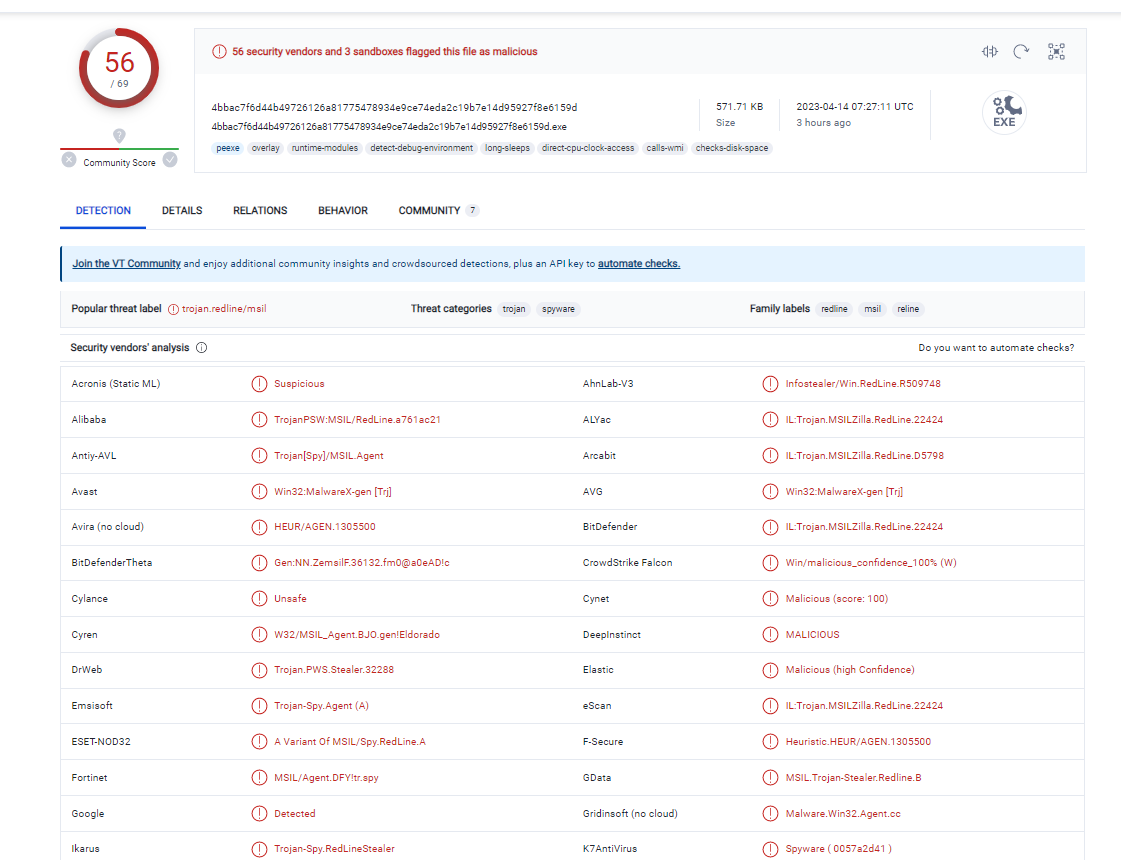
As you can see, there are no problems with detection here, which is good news. The external sample has an IPTV application icon and is presented as an SFX archive, but there is no other information. Let's move on to the analysis.
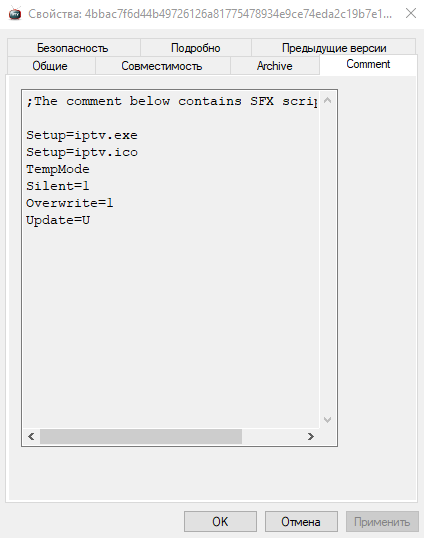
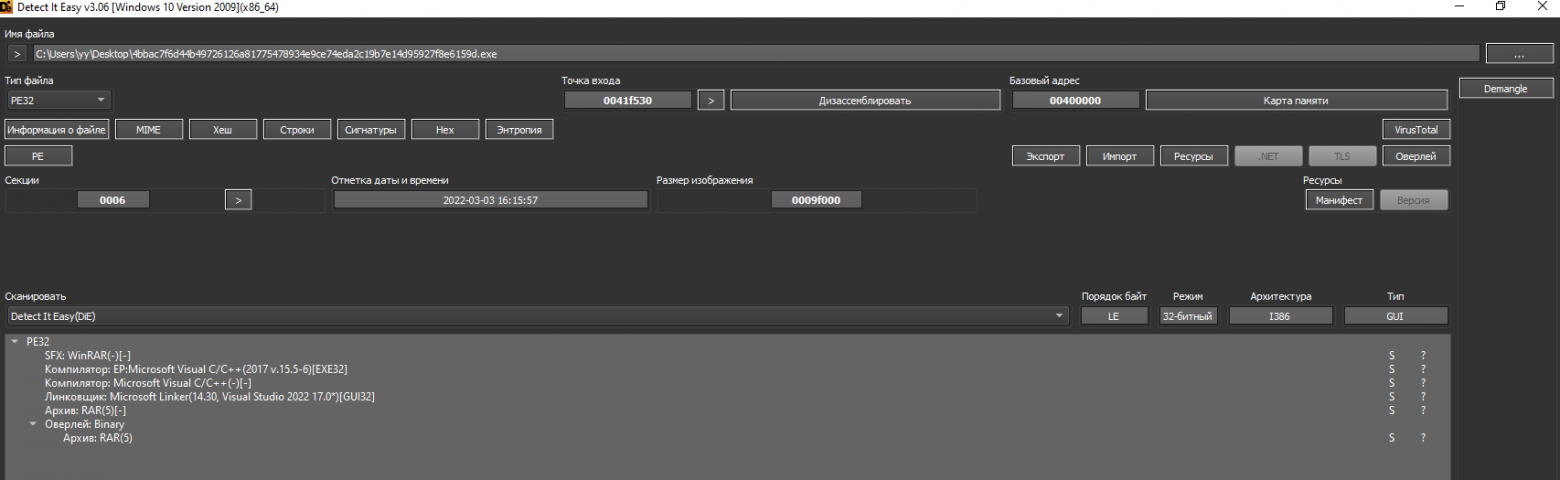
And as mentioned earlier, this is our SFX archive. I would not say that this method of packaging malware is something new and revolutionary. Similarly, in my school years, I packaged a variety of BAT files to make them look like executable. exe files.
A self-extracting or self-extracting archive (SFX) is a file or computer program that combines an archive and executable code for unpacking it. Such archives, unlike regular ones, do not require a separate program to unpack them, if the executable code can be executed in the specified operating system.
In principle, if it were launched now, the content would end up in the AppData folder, where a normal user would hardly find it. But we'll make things a little easier by simply opening .sfx using the archiver. Let's extract the file we are interested in and start parsing it.
IPTV.exe — this is the name of the extracted file, but it is much more interesting that even when viewing the properties, we can get some useful information, namely:
Approximate time of last modification, which is unlikely to be replaced, and the original file name — implossions.exe. When we try to search for this name through the search engine, we immediately see that it belongs to our stiller. The resulting sample weighs 95 KB. Let's go back to DIE for more information about the writing language and compiler of this miracle.
The exact date of creation is unknown, what we see is "Timestomping", and it is an anti-criminalistic method used to mislead the investigation and rapid response specialists.
We also see that the malware is a library .NET, and Microsoft Linker was used as the compiler.
Libraries .NET — in essence, they are the end result of compiling code in C#. Fortunately, we can easily decompile this sample using the dnSpy utility and analyze the clean source code, or at least something close to it. But if I were you, I wouldn't be happy about this, since such accessibility of the code can provoke the appearance of modifications from other attackers, and this already smacks of a full-fledged epidemic.
But first, let's use Tiny Tracer with advanced settings to clearly see what functions stiller uses. This will also display the malware's action plan.
First, it is worth noting that the malware creates an unknown child process by calling rtlCreateUserProcessParametersEx, then it decodes something from Unicode and by calling NtAllocateVirtualMemory allocates a section of memory where it writes something. The process is very similar to the one that we could already observe when analyzing the Magniber ransomware.
But all of a sudden, tracing was stopped because a process was created that Tiny couldn't trace, and I get the following error:

I do not know if this can be inserted into an article, but here is an example of live analytics. Everything is fair and uncut.
Well, since we have determined that the malware introduces some kind of shellcode and interrupts the main sample, I suggest that you first deal with it, and then go through the classical statistical analysis.
A shellcode is a part of the code embedded in a malicious program that allows you to get the command shell code after infecting the target system of the victim. Very often, shellcode is used as an exploit payload.
Shellcodes were detected in three processes: explorer.exe, dwm.exe and in searchapp.exe. Even one glance through the notebook is enough to understand that they are all the same and clearly left by our stiller.
Now let's use the previously described method and convert the captured shellcodes into executable files for further analysis. But I was a little disappointed, as it turned out that these shellcodes are copies of the source code of the malware with some edits.
The same dnSpy and its function responsible for this process will help us find the entry point of this virus. The entry point is the Program class. Let's move on to viewing it.
The Execute extension immediately catches your eye, pointing to the EntryPoint class, from which the following four parameters will be decrypted via the StringDecrypt.Decrypt class:" Message"," Key"," IP "and" ID".
Surprisingly, when we go to this class, we see absolutely unencrypted data and the very message that I was surprised at earlier. It seemed to me that this might be some kind of malicious error in this particular version of the malware, but when I downloaded the older one, I saw the same thing.
Apparently, the criminal was not particularly concerned that the IP address of his command server would be discovered by someone, if at all.

Attackers also collect information about whether this malware was previously run on the victim's machine. This check is done quite simply. Using the SeenBefore method, the presence of a folder at the following path is checked:
\AppData\Local\Yandex\YaAddon
If the folder was found, the method returns false. If it is not found, it will be created and the response will be true. These two values will be saved and sent to the command server.
Attackers may be interested in this for several reasons, but the most likely one is the following. If Redline was already running earlier on the victim's machine, then there is a chance that the account credentials were changed either by the user or by another attacker. Then the sale of stolen goods becomes a huge question mark.
To do this, a new key will be created in the Windows registry along the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000090250. The malware will also be added to normal Windows startup.
For example, an attacker purposefully wants to steal all possible data from the Chrome browser. In this case, the ScanChrome argument is used, which uses the C_H_R_O_M_E class.
Next, the ScanningArgs class defines the directory in which the search will be performed. In the case of the Chrome browser, it will look like this:

The directories and names of folders or files that the malware needs to search for are quite peculiar, this is the first time I've seen this and I assume that this is a primitive method of obfuscating the code.
After that, the following three methods can be used: ScanFills (steals autofill files), ScanCC (steals credit card information), and ScanCook (steals cookies). It is important to note that each of these methods is autonomous, meaning that an attacker can perform either one or all of them together, depending on their ultimate goals.
Let's take a closer look at the example using the ScanCC method, because I think it is the most relevant one. Since Chrome uses the SQLi table to store all data about saved bank cards, it is logical that the malware generates a query to this table using the ReadTable function. After reading this table, Redline decrypts the data, analyzes it, and writes it to the ScanResult file, which will then be sent to the command server.
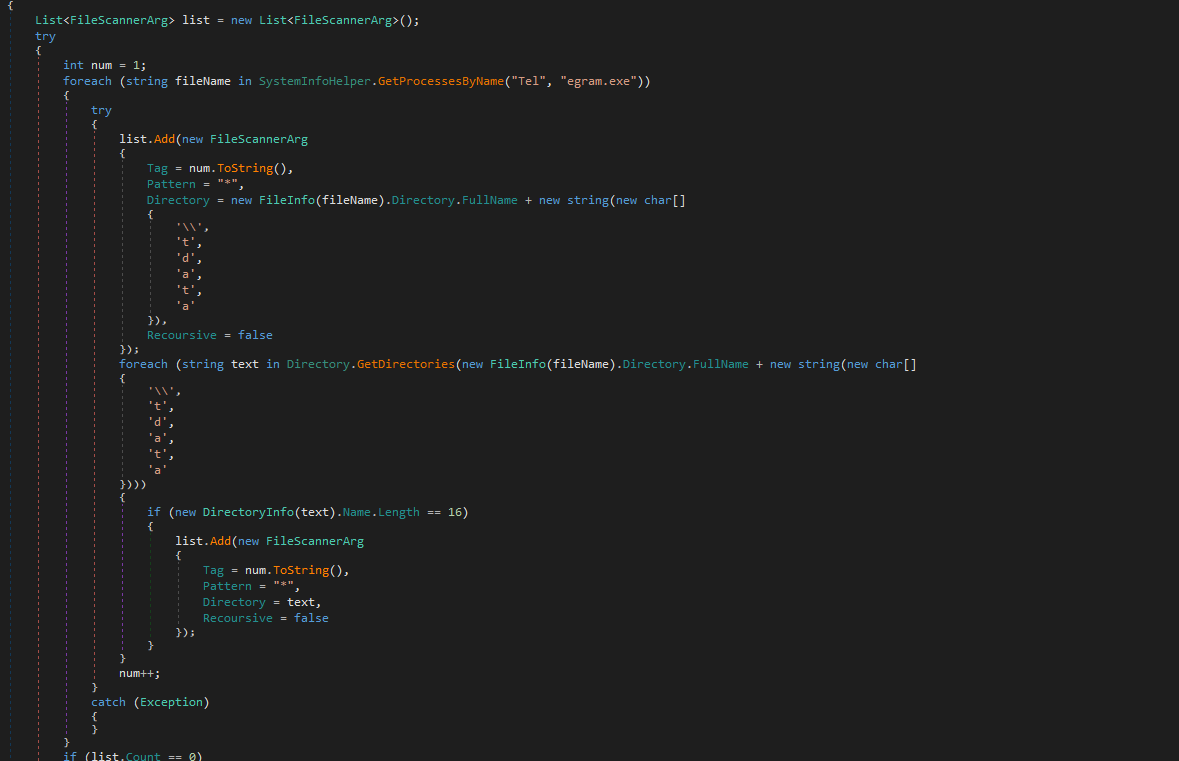
The thing is that by copying the tdata folder from one device and simply moving it to another, where the same version of messenger is installed, you will easily get into the account from the first device and Telegram will not require any additional checks.
Stealing this folder is a child function of stealing wallet.dat files, where seed phrases of crypto wallets are stored.The Cryptos class is responsible for this process.
First, use the same GetScanArgs method to set the directory where the necessary files will be searched. If they are detected, Redline uses the FileCopier class, namely one of its CopyFile methods, which simply copies the content and transfers it to the ScanResult file.
If the command server operator also wants to get Telegram accounts, then the DesktopMassengerRule class will be called, which will perform the same manipulations as the Cryptos class.
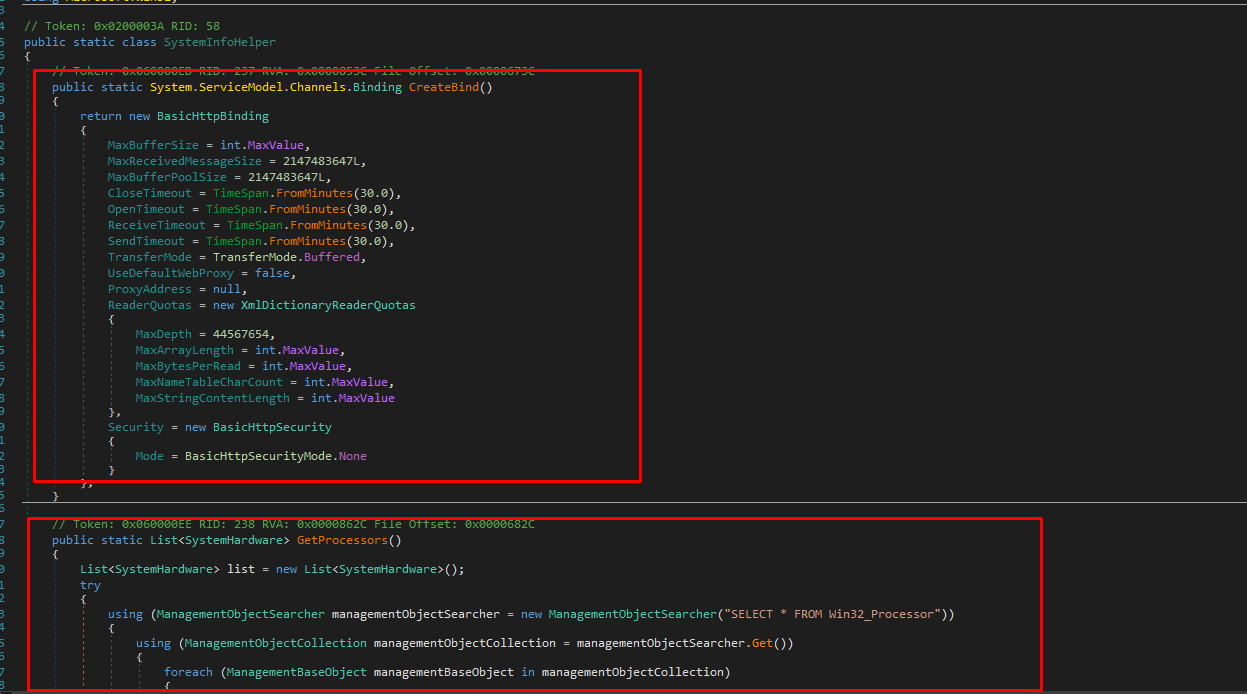
Their GetProcessors and GetGraphicCard methods are responsible for getting information about the hardware of the victim's device.
But more interesting is the GetFireWalls method, which uses the ManagementObjectSearcher system call and collects information about antivirus and antispyware programs, firewalls, and Windows security settings.
All this information will also be saved to the ScanResult file and transmitted to the command server.
The thing is that the creators of this stiller do not need to completely rewrite the code, but just change one variable or rename some method and after compiling this sample will have a completely different hash, which, alas, will no longer be in the antivirus databases. I did this simple manipulation — and here is the result:
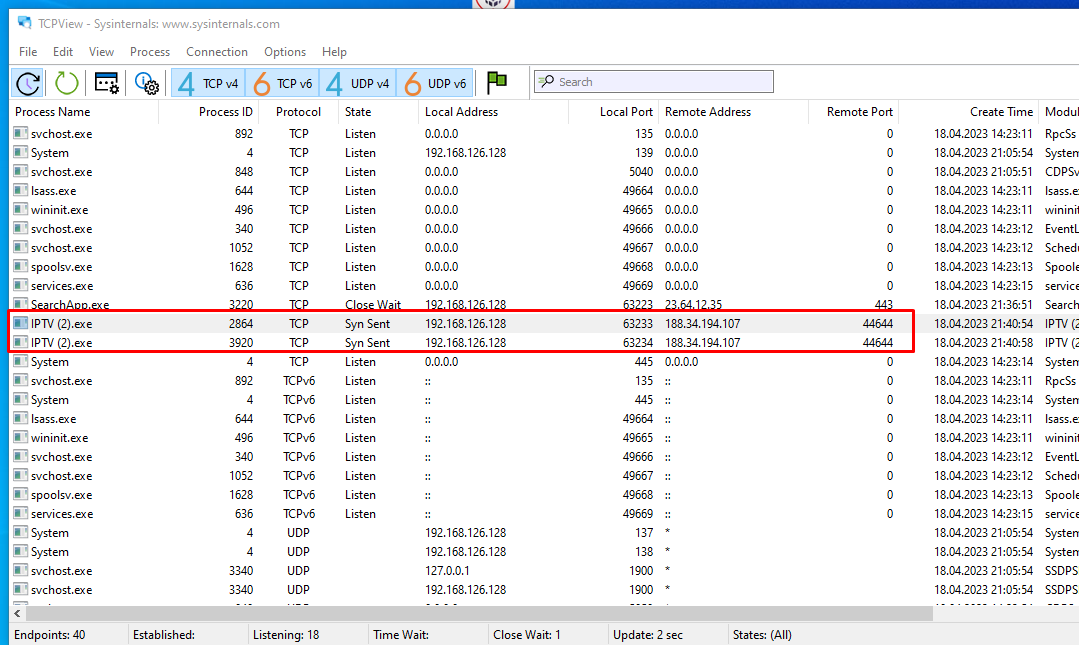
So, how do you know that your car is infected with Redline Stealer, and your personal data has long been sold on some underground forum:
It is worth noting that over time, the malware code has changed little and the sample from 2020 practically does not differ from the sample from 2023. Both can be detected by modern antivirus programs without any problems.
Since the Redline is very flexible, it is not known what will happen next. So be vigilant and keep your eyes open.
Only one thing is upsetting — the negligence of monitoring groups, the same Microsoft could easily stop the activity of the malware. The IP addresses of Stiller's command servers are very easy to track and block, thereby constantly limiting the capabilities of cybercriminals. But no one does this, allowing the malware to spread and harm ordinary users.
And that's all I have, come on.
Author of the article @DeathDay
This was not the end of it, the attack on PyPI gave rise to a new meta among the attackers, and this time the public NPM repository was affected.

NPM is a standard package manager that is automatically installed along with Node.js. It is used to download packages from the npm cloud server, or to upload packages to these servers.
However, the methodology of this campaign is slightly different from what we saw earlier: no one uploaded viruses directly to NPM, attackers took advantage of the high reputation of open source sources in search engines and promoted malicious sites, as well as utilities with malicious stuffing through this repository.
There are several vectors of attacks using NPM:
- The attacker creates his own website, where he places supposedly cracked applications for every taste, of course, they contain a variety of malware. Next, it uploads several hundred empty packages to NPM that contain only the file. Readme.md. This file consists of a link to the villain's website. I mentioned earlier that open source sources are well indexed by search engines, so these packages with a regular link inherit a good reputation and move up in search engines. This is so-called SEO Poisoning.
- The second option is a bit simpler and is based on the same method with the Readme file, but this time the attacker leaves a link to a fraudulent telegram channel, where he allegedly provides programs for configuring video cards for mining. This company was mainly focused on Russian users.
- Natural DoS attacks. No, you weren't imagining it. First, due to the growth in the number of packages and, as a result, an increase in traffic to the NPM site, a denial of service was caused. You can also consider the method when an attacker creates thousands of packets with a link to some victim resource, and then it is not difficult to guess what can happen, but this is only in theory and, most likely, very ineffective (but the site of an average school will not survive).
A DoS attack is a hacker attack on a computer system in order to bring it to failure, that is, creating conditions under which bona fide users of the system will not be able to access the provided system resources (servers), or this access will be difficult.
According to a report from Checkmarx, several hackers may be behind this campaign and their ultimate goal is to spread malware such as RedLine Stealer (80%), Glupteba (12%), Smoke Loader (5%) and XMRig (2%).
Redline is particularly dangerous due to a sharp increase in the number of infections, so today we will analyze and analyze it.
ReadLine Stealer: A quick overview
So, ReadLine Stealer is malware that is currently being sold on closed forums. Stiller is used by various attackers to steal data and upload other viruses to the victim's device. The exact date of its appearance is unknown, but the first malicious sample of the Redline appeared on VirusTotal in March 2020.RedLine Stealer can steal the following information: usernames, passwords, autofill data, cookies, and credit card information from all web browsers. Cybercriminals can misuse this information to access various accounts (for example, social networks, email, bank accounts, cryptocurrency wallets).
The list of e-wallets targeted by the RedLine hijacker includes Armory, AtomicWallet, BitcoinCore, Bytecoin, DashCore, Electrum, Ethereum, LitecoinCore, Monero, Exodus, Zcash, and Jaxx. The target VPN clients are ProtonVPN, OpenVPN, and NordVPN.
For analysis, we will use a sample dated April 14, 2023. On VirusTotal, it looks like this:

As you can see, there are no problems with detection here, which is good news. The external sample has an IPTV application icon and is presented as an SFX archive, but there is no other information. Let's move on to the analysis.

ReadLine Stealer: A brief statistical analysis
According to the classics, I present a setup of utilities for this article:- DIE-Detect it Easy: a multi-functional tool that has a huge arsenal. It will allow us to get ahead of the malware compiler type, language, libraries, and import/export tables with subsequent disassembly.
- PE Bear is a good tool for viewing and editing the components of a PE file.
- Tiny Tracer is a utility for dynamically tracking the execution of binary elements. The so-called tracer.
- IDA PRO is a tool for reverse engineering.
- Reko is a decompiler that is also familiar to us from previous articles.
- HollowHunter is a utility that detects and resets a lot of potentially malicious implants (replaced / implanted pes, shellcodes, interceptors, in-memory patches).

And as mentioned earlier, this is our SFX archive. I would not say that this method of packaging malware is something new and revolutionary. Similarly, in my school years, I packaged a variety of BAT files to make them look like executable. exe files.
A self-extracting or self-extracting archive (SFX) is a file or computer program that combines an archive and executable code for unpacking it. Such archives, unlike regular ones, do not require a separate program to unpack them, if the executable code can be executed in the specified operating system.
In principle, if it were launched now, the content would end up in the AppData folder, where a normal user would hardly find it. But we'll make things a little easier by simply opening .sfx using the archiver. Let's extract the file we are interested in and start parsing it.
IPTV.exe — this is the name of the extracted file, but it is much more interesting that even when viewing the properties, we can get some useful information, namely:
Approximate time of last modification, which is unlikely to be replaced, and the original file name — implossions.exe. When we try to search for this name through the search engine, we immediately see that it belongs to our stiller. The resulting sample weighs 95 KB. Let's go back to DIE for more information about the writing language and compiler of this miracle.
The exact date of creation is unknown, what we see is "Timestomping", and it is an anti-criminalistic method used to mislead the investigation and rapid response specialists.
We also see that the malware is a library .NET, and Microsoft Linker was used as the compiler.
Libraries .NET — in essence, they are the end result of compiling code in C#. Fortunately, we can easily decompile this sample using the dnSpy utility and analyze the clean source code, or at least something close to it. But if I were you, I wouldn't be happy about this, since such accessibility of the code can provoke the appearance of modifications from other attackers, and this already smacks of a full-fledged epidemic.
But first, let's use Tiny Tracer with advanced settings to clearly see what functions stiller uses. This will also display the malware's action plan.
First, it is worth noting that the malware creates an unknown child process by calling rtlCreateUserProcessParametersEx, then it decodes something from Unicode and by calling NtAllocateVirtualMemory allocates a section of memory where it writes something. The process is very similar to the one that we could already observe when analyzing the Magniber ransomware.
But all of a sudden, tracing was stopped because a process was created that Tiny couldn't trace, and I get the following error:

I do not know if this can be inserted into an article, but here is an example of live analytics. Everything is fair and uncut.
Well, since we have determined that the malware introduces some kind of shellcode and interrupts the main sample, I suggest that you first deal with it, and then go through the classical statistical analysis.
A shellcode is a part of the code embedded in a malicious program that allows you to get the command shell code after infecting the target system of the victim. Very often, shellcode is used as an exploit payload.
We open the hunt for ShellCode: what's inside?
To detect and capture it, we will use the Hollow Hunter utility with a single /shellc parameter.Shellcodes were detected in three processes: explorer.exe, dwm.exe and in searchapp.exe. Even one glance through the notebook is enough to understand that they are all the same and clearly left by our stiller.
Now let's use the previously described method and convert the captured shellcodes into executable files for further analysis. But I was a little disappointed, as it turned out that these shellcodes are copies of the source code of the malware with some edits.
Opening the ReadLine Stealer: start diving
So, let's skip the previous topic and let's immediately tell you about the algorithm of this malware:- Decryption of encoded strings and communication with the C&C server.
- Fixing the malware in the system.
- Directly stealing data or executing criminal commands.
Decryption of encoded strings and communication with the C&C server
It is worth noting that instant communication with the command server is a very unusual move for malicious applications. As part of the analysis, we already had several stillers, so they first steal data, and only then contact the server. Most likely, this is due to the fact that Redline does not have any instructions in its code, unlike others, "like steal this, but you don't need this", so it is important for the virus to get instructions from C&C and only then deploy its malicious activity.The same dnSpy and its function responsible for this process will help us find the entry point of this virus. The entry point is the Program class. Let's move on to viewing it.
The Execute extension immediately catches your eye, pointing to the EntryPoint class, from which the following four parameters will be decrypted via the StringDecrypt.Decrypt class:" Message"," Key"," IP "and" ID".
Surprisingly, when we go to this class, we see absolutely unencrypted data and the very message that I was surprised at earlier. It seemed to me that this might be some kind of malicious error in this particular version of the malware, but when I downloaded the older one, I saw the same thing.
Apparently, the criminal was not particularly concerned that the IP address of his command server would be discovered by someone, if at all.

Attackers also collect information about whether this malware was previously run on the victim's machine. This check is done quite simply. Using the SeenBefore method, the presence of a folder at the following path is checked:
\AppData\Local\Yandex\YaAddon
If the folder was found, the method returns false. If it is not found, it will be created and the response will be true. These two values will be saved and sent to the command server.
Attackers may be interested in this for several reasons, but the most likely one is the following. If Redline was already running earlier on the victim's machine, then there is a chance that the account credentials were changed either by the user or by another attacker. Then the sale of stolen goods becomes a huge question mark.
Pinning in the system
After these checks and establishing a connection with the server, it is vital for the virus to gain a foothold on the victim's machine in order to continue its stiller activity in the event of a reboot or other things.To do this, a new key will be created in the Windows registry along the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000090250. The malware will also be added to normal Windows startup.
Direct data theft
Stiller functionality:
- Theft of data such as:
- Autofill data and cookies from such web browsers as: Opera, Firefox, Google Chrome, Microsoft Edge, Internet Explorer,
- Discord tokens.
- copy of the tdata folder from Telegram Desktop,
- data from Filezilla-based FTP clients,
- Steam, Epic Games, and Origin credentials,
- keys to popular VPN services: NordVPN, OpenVPN, ProntonVPN,
- data from cryptocurrency wallets. There are a lot of them in the list, all of them were listed earlier.
- Collecting information about the victim's device: geolocation, hardware configuration, installed applications, and user name.
- It can be used as a dropper, delivering other malware to the infected machine.
- Output of windows with errors, the text of which is set by the attacker.
Briefly about data theft from the Chrome browser
After these simple and typical malware manipulations, Redline starts its main function-data theft. First, the virus receives commands from the C&C server operator that use the ScanningArgs class, which contains a list of plug-ins.For example, an attacker purposefully wants to steal all possible data from the Chrome browser. In this case, the ScanChrome argument is used, which uses the C_H_R_O_M_E class.
Next, the ScanningArgs class defines the directory in which the search will be performed. In the case of the Chrome browser, it will look like this:

The directories and names of folders or files that the malware needs to search for are quite peculiar, this is the first time I've seen this and I assume that this is a primitive method of obfuscating the code.
After that, the following three methods can be used: ScanFills (steals autofill files), ScanCC (steals credit card information), and ScanCook (steals cookies). It is important to note that each of these methods is autonomous, meaning that an attacker can perform either one or all of them together, depending on their ultimate goals.
Let's take a closer look at the example using the ScanCC method, because I think it is the most relevant one. Since Chrome uses the SQLi table to store all data about saved bank cards, it is logical that the malware generates a query to this table using the ReadTable function. After reading this table, Redline decrypts the data, analyzes it, and writes it to the ScanResult file, which will then be sent to the command server.
Briefly about stealing Telegram Desktop accounts
I think it is no longer a secret for many that the Telegram Desktop application has one such interesting vulnerability, which is difficult to name as such. But nevertheless, it is very popular in the circles of intruders.
The thing is that by copying the tdata folder from one device and simply moving it to another, where the same version of messenger is installed, you will easily get into the account from the first device and Telegram will not require any additional checks.
Stealing this folder is a child function of stealing wallet.dat files, where seed phrases of crypto wallets are stored.The Cryptos class is responsible for this process.
First, use the same GetScanArgs method to set the directory where the necessary files will be searched. If they are detected, Redline uses the FileCopier class, namely one of its CopyFile methods, which simply copies the content and transfers it to the ScanResult file.
If the command server operator also wants to get Telegram accounts, then the DesktopMassengerRule class will be called, which will perform the same manipulations as the Cryptos class.
Collecting information about the victim's device
The SystemInfoHelper and SystemHardware classes are used to collect most of the information about the victim's device.
Their GetProcessors and GetGraphicCard methods are responsible for getting information about the hardware of the victim's device.
But more interesting is the GetFireWalls method, which uses the ManagementObjectSearcher system call and collects information about antivirus and antispyware programs, firewalls, and Windows security settings.
All this information will also be saved to the ScanResult file and transmitted to the command server.
Behavioral factor of the malware carrier
There is no need for a full-fledged dynamic analysis here. Redline is simpler than a ballpoint pen in this respect. Therefore, I will simply list the main criteria by which you can determine whether your car is infected with this malware or not. I note that even though I advise you to use popular antivirus programs with a good reputation, they will not always help you.The thing is that the creators of this stiller do not need to completely rewrite the code, but just change one variable or rename some method and after compiling this sample will have a completely different hash, which, alas, will no longer be in the antivirus databases. I did this simple manipulation — and here is the result:

So, how do you know that your car is infected with Redline Stealer, and your personal data has long been sold on some underground forum:
- First, no matter how trivial my words may sound, pay attention to the workload of your system. Redline eats up a lot of RAM. The test sample somehow took up as much as 500 MB.
- Check for the above path in the Windows registry.
- Use the TCPView utility to see which processes are communicating with remote hosts without your knowledge.
- Check the AppData folder for strange executable files.

Conclusions
Redline Stealer is certainly a very powerful modular spyware that is used by many attackers. But at the moment, this virus is spreading mainly through Seo Poisoning and sites with pirated software using the public NPM repository.It is worth noting that over time, the malware code has changed little and the sample from 2020 practically does not differ from the sample from 2023. Both can be detected by modern antivirus programs without any problems.
Since the Redline is very flexible, it is not known what will happen next. So be vigilant and keep your eyes open.
Only one thing is upsetting — the negligence of monitoring groups, the same Microsoft could easily stop the activity of the malware. The IP addresses of Stiller's command servers are very easy to track and block, thereby constantly limiting the capabilities of cybercriminals. But no one does this, allowing the malware to spread and harm ordinary users.
And that's all I have, come on.
Author of the article @DeathDay

