Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The case when it is better for employees not to know how much they earned last month…
Israeli cybersecurity company Perception Point revealed details of a new phishing campaign targeting American organizations. The attacks are aimed at introducing a remote access Trojan known as NetSupport RAT as part of an operation codenamed PhantomBlu.
A special feature of this operation is that hackers manipulate OLE templates, which allows malicious code to be executed without detection by using Microsoft Office documents.
NetSupport RAT is a malicious version of the legitimate remote desktop tool NetSupport Manager and allows attackers to collect sensitive data from an infected device.
The phishing attack begins with an email about salary allegedly sent by the accounting department. The message text encourages recipients to open the attached Word document to view the "monthly salary report".
The document contains instructions for entering a password from the email body and activating the edit mode. It also suggests double-clicking on the printer icon to view the salary schedule. Clicking on the printer launches a ZIP archive with a malicious shortcut inside. Running this shortcut ultimately results in NetSupport RAT being downloaded and executed on the target machine.
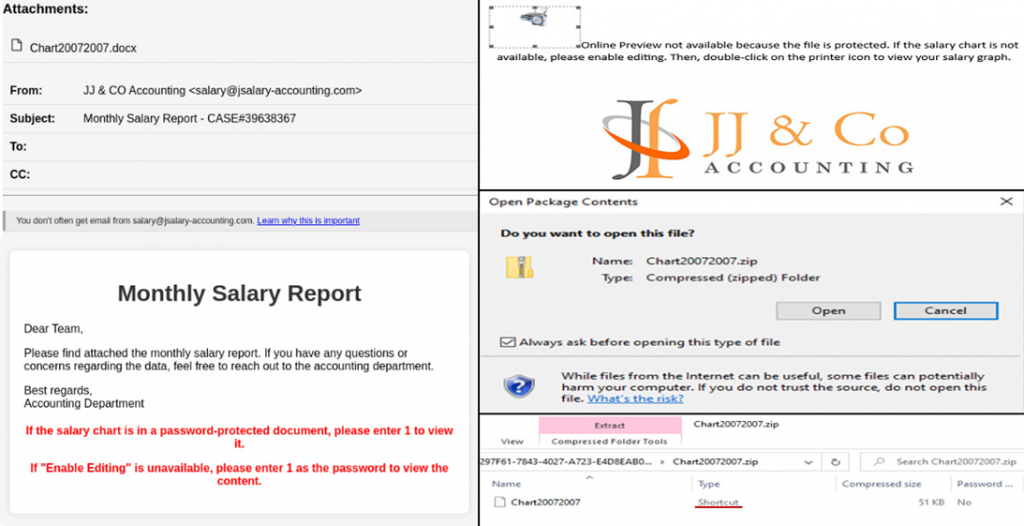
Email, decoy file, archive, and malicious shortcut
The researchers also note the growing misuse of cloud platforms and popular content delivery networks (CDNs) to create completely undetectable phishing links. Such links are usually created using special phishing kits that are offered by cybercriminals in Telegram for a subscription starting from $ 200 per month. Such solutions provide advanced anonymity and evasion of detection thanks to the built-in anti-bot protection.
Such innovations in phishing and malware distribution indicate a constant evolution in the methods of attackers, who adapt their malicious infrastructure to current security systems day by day to increase the probability of success of their malicious campaigns.
Israeli cybersecurity company Perception Point revealed details of a new phishing campaign targeting American organizations. The attacks are aimed at introducing a remote access Trojan known as NetSupport RAT as part of an operation codenamed PhantomBlu.
A special feature of this operation is that hackers manipulate OLE templates, which allows malicious code to be executed without detection by using Microsoft Office documents.
NetSupport RAT is a malicious version of the legitimate remote desktop tool NetSupport Manager and allows attackers to collect sensitive data from an infected device.
The phishing attack begins with an email about salary allegedly sent by the accounting department. The message text encourages recipients to open the attached Word document to view the "monthly salary report".
The document contains instructions for entering a password from the email body and activating the edit mode. It also suggests double-clicking on the printer icon to view the salary schedule. Clicking on the printer launches a ZIP archive with a malicious shortcut inside. Running this shortcut ultimately results in NetSupport RAT being downloaded and executed on the target machine.

Email, decoy file, archive, and malicious shortcut
The researchers also note the growing misuse of cloud platforms and popular content delivery networks (CDNs) to create completely undetectable phishing links. Such links are usually created using special phishing kits that are offered by cybercriminals in Telegram for a subscription starting from $ 200 per month. Such solutions provide advanced anonymity and evasion of detection thanks to the built-in anti-bot protection.
Such innovations in phishing and malware distribution indicate a constant evolution in the methods of attackers, who adapt their malicious infrastructure to current security systems day by day to increase the probability of success of their malicious campaigns.

