Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The Glupteba botnet achieves stability using an unknown UEFI bootkit.
Experts from Palo Alto Networks Unit 42 found that the Glupteba botnet has acquired a new feature – an undocumented loader for the Unified Extensible Firmware Interface (UEFI), which significantly increases the stability and stealth of malware.
According to the researchers, the bootkit can interfere with and control the boot process of the operating system, allowing Glupteba to hide itself and create a hidden persistent environment that is extremely difficult to detect and remove.
Glupteba, described as a multifunctional malware, in addition to stealing information and using infected devices for mining, is capable of various fraudulent actions, including theft of credentials and credit card data, manipulation of advertising, and attacks on routers in order to gain remote access. One of its unique features is the use of the Bitcoin blockchain as a backup command and Control system (C2), which makes the backdoor resistant to blocking attempts.
Glupteba is distributed through complex infection chains that include several stages and the use of pay-per-install (PPI) services to distribute Glupteba. As noted by Sekoia, one of the PPI services was used to distribute malware through PrivateLoader as an intermediate stage, during which the SmokeLoader loader was delivered to victims under the guise of installation files of pirated software. The bootloader, in turn, launched RedLine Stealer and Amadey, the final stage of which was the Glupteba infection.
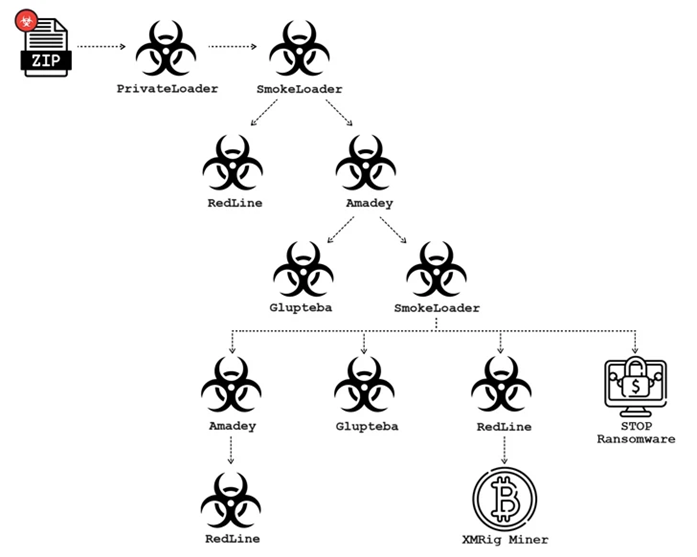
Glubteba Infection
As a sign that Glupteba continues to be actively monitored and updated, the developers have equipped it with a UEFI loader that includes a modified version of the open-source EfiGuard project, which is able to disable PatchGuard and Driver Signature Enforcement (DSE) during boot. It is worth noting that previous versions of Glubteba included installing the kernel driver as a rootkit to hide botnet actions and weaken the protection of infected devices.
The researchers emphasize that Glupteba continues to demonstrate the high degree of complexity and adaptability typical of modern cybercriminals. The discovery of a new UEFI bypass technique confirms malware's ability to innovate and evade detection. In addition, the use of the PPI ecosystem to distribute Glupteba highlights the collaboration and monetization strategies employed by cybercriminals for mass infection.
Experts from Palo Alto Networks Unit 42 found that the Glupteba botnet has acquired a new feature – an undocumented loader for the Unified Extensible Firmware Interface (UEFI), which significantly increases the stability and stealth of malware.
According to the researchers, the bootkit can interfere with and control the boot process of the operating system, allowing Glupteba to hide itself and create a hidden persistent environment that is extremely difficult to detect and remove.
Glupteba, described as a multifunctional malware, in addition to stealing information and using infected devices for mining, is capable of various fraudulent actions, including theft of credentials and credit card data, manipulation of advertising, and attacks on routers in order to gain remote access. One of its unique features is the use of the Bitcoin blockchain as a backup command and Control system (C2), which makes the backdoor resistant to blocking attempts.
Glupteba is distributed through complex infection chains that include several stages and the use of pay-per-install (PPI) services to distribute Glupteba. As noted by Sekoia, one of the PPI services was used to distribute malware through PrivateLoader as an intermediate stage, during which the SmokeLoader loader was delivered to victims under the guise of installation files of pirated software. The bootloader, in turn, launched RedLine Stealer and Amadey, the final stage of which was the Glupteba infection.

Glubteba Infection
As a sign that Glupteba continues to be actively monitored and updated, the developers have equipped it with a UEFI loader that includes a modified version of the open-source EfiGuard project, which is able to disable PatchGuard and Driver Signature Enforcement (DSE) during boot. It is worth noting that previous versions of Glubteba included installing the kernel driver as a rootkit to hide botnet actions and weaken the protection of infected devices.
The researchers emphasize that Glupteba continues to demonstrate the high degree of complexity and adaptability typical of modern cybercriminals. The discovery of a new UEFI bypass technique confirms malware's ability to innovate and evade detection. In addition, the use of the PPI ecosystem to distribute Glupteba highlights the collaboration and monetization strategies employed by cybercriminals for mass infection.

