Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
The malware is able to auto-start and self-distribute, all in the best traditions of network worms from zero.
Cybersecurity specialists from the company McAfee discovered a new version of the malicious software XLoader, which is able to automatically run on infected Android smartphones after installation. This discovery puts users from the US, UK, Germany, France, Japan, South Korea and Taiwan at risk.
XLoader (aka MoqHao), formerly known as one of the most dangerous types of malware for Android, can now run in the background, extracting sensitive data including photos, text messages, contact lists, and device hardware information.
The malware is distributed through fraudulent links sent in text messages. These links lead to APKs for installing apps that bypass Google Play, which increases the risk of malware infection.
It is worth noting that Google has recently been actively fighting this method of spreading malware, introducing Google Play Protect scanning and permission control even for third-party APK files.
Returning to the current XLoader campaign, it is important to know that in order to deceive victims and gain access to additional permissions on the smartphone, the malware disguises itself as Google Chrome, offering users to install itself as the main SMS application to prevent spam.
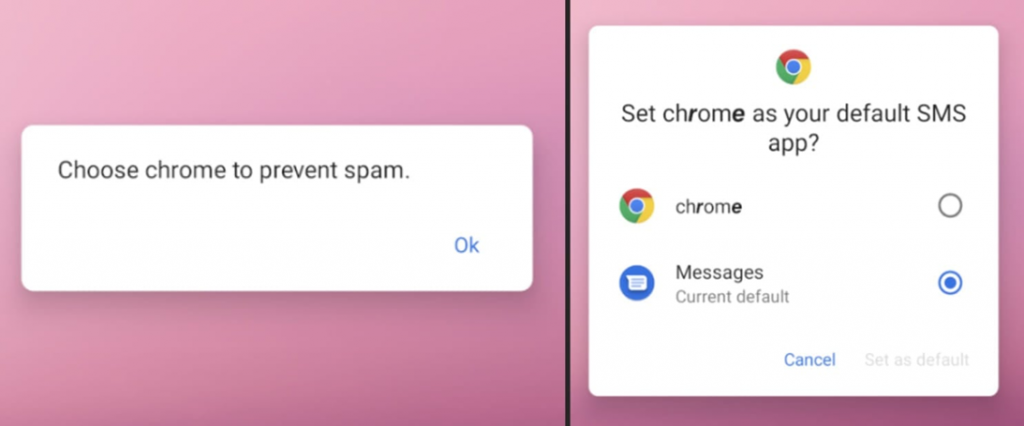
At the same time, the malware is adapted for several countries at once and uses different languages for pop-up messages to appear more convincing.
In addition, as noted above, the new XLoader has an autorun function after installation. That is, the very fact of installing an application on a device already becomes fatal for its owner, since the malware starts itself and starts its malicious activity. At the same time, most other malware programs need to be started manually to start the infection chain.
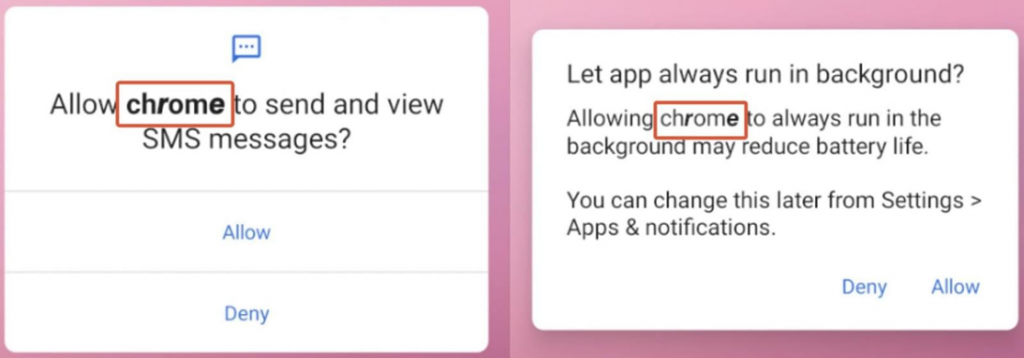
In addition to the above-mentioned functions, XLoader is also able to self-distribute, sending SMS with short links to its installation to all contacts from the victim's phone book.
Since its introduction to the mobile threat market in 2015, XLoader has consistently improved its attack methodologies, increasing its stealth capabilities and effectiveness. McAfee warns that the latest versions of XLoader can be particularly effective because they require minimal user interaction.
To protect yourself from malware on Android, you need to avoid installing apps from unofficial sources, avoid opening URLs from SMS messages (even from familiar recipients) , and pay close attention to the permissions granted to apps. We also recommend limiting the number of installed apps and using only those developed by trusted developers.
Cybersecurity specialists from the company McAfee discovered a new version of the malicious software XLoader, which is able to automatically run on infected Android smartphones after installation. This discovery puts users from the US, UK, Germany, France, Japan, South Korea and Taiwan at risk.
XLoader (aka MoqHao), formerly known as one of the most dangerous types of malware for Android, can now run in the background, extracting sensitive data including photos, text messages, contact lists, and device hardware information.
The malware is distributed through fraudulent links sent in text messages. These links lead to APKs for installing apps that bypass Google Play, which increases the risk of malware infection.
It is worth noting that Google has recently been actively fighting this method of spreading malware, introducing Google Play Protect scanning and permission control even for third-party APK files.
Returning to the current XLoader campaign, it is important to know that in order to deceive victims and gain access to additional permissions on the smartphone, the malware disguises itself as Google Chrome, offering users to install itself as the main SMS application to prevent spam.

At the same time, the malware is adapted for several countries at once and uses different languages for pop-up messages to appear more convincing.
In addition, as noted above, the new XLoader has an autorun function after installation. That is, the very fact of installing an application on a device already becomes fatal for its owner, since the malware starts itself and starts its malicious activity. At the same time, most other malware programs need to be started manually to start the infection chain.

In addition to the above-mentioned functions, XLoader is also able to self-distribute, sending SMS with short links to its installation to all contacts from the victim's phone book.
Since its introduction to the mobile threat market in 2015, XLoader has consistently improved its attack methodologies, increasing its stealth capabilities and effectiveness. McAfee warns that the latest versions of XLoader can be particularly effective because they require minimal user interaction.
To protect yourself from malware on Android, you need to avoid installing apps from unofficial sources, avoid opening URLs from SMS messages (even from familiar recipients) , and pay close attention to the permissions granted to apps. We also recommend limiting the number of installed apps and using only those developed by trusted developers.

