Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
Properly written emails allowed hackers to deploy their tools.
IBM X-Force reports on a series of phishing campaigns by the ITG05 group, during which fake documents are sent on behalf of government and non-governmental organizations in Europe, Transcaucasia, Central Asia, and North and South America.
The IBM report highlights the use of a variety of documents — both internal and publicly available, as well as probably created by the attackers themselves-related to finance, critical infrastructure, interaction with managers, cybersecurity, maritime security, healthcare, business and manufacturing in the defense industry.
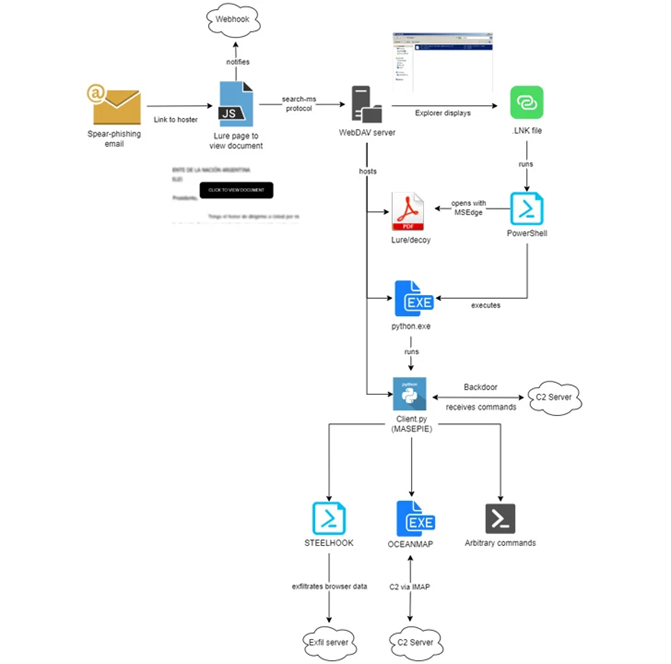
ITG05 infection Chain
The report pays special attention to the use of a URI protocol handler called search-ms, which allows applications and HTML links to run a customized search on the device. Cybercriminals abuse search-ms to trick victims into downloading malware from a WebDAV server.
It also points to the possible use of compromised Ubiquiti routers as servers for phishing and malware distribution. Recall that at the end of February, federal agencies in the United States and other countries urged users to pay attention to the risks of using Ubiquiti EdgeRouter routers, which can be used to collect credentials, redirect traffic and create phishing pages.
Cybercriminals in their emails pose as organizations from certain countries-Argentina, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the United States. The emails use a combination of genuine publicly available government and non-governmental decoy documents to activate the infection chain. Free hosting providers are used as hosting services, which allows you to prepare payloads for current operations.
The chain of infections ends with the deployment of MASEPIE, OCEANMAP, and STEELHOOK programs designed to steal files, execute arbitrary commands, and steal data from browsers.
The researchers conclude that ITG05 is able to adapt to changing capabilities by providing new infection methodologies and using commercially available infrastructure, while consistently developing malware capabilities.
IBM X-Force reports on a series of phishing campaigns by the ITG05 group, during which fake documents are sent on behalf of government and non-governmental organizations in Europe, Transcaucasia, Central Asia, and North and South America.
The IBM report highlights the use of a variety of documents — both internal and publicly available, as well as probably created by the attackers themselves-related to finance, critical infrastructure, interaction with managers, cybersecurity, maritime security, healthcare, business and manufacturing in the defense industry.

ITG05 infection Chain
The report pays special attention to the use of a URI protocol handler called search-ms, which allows applications and HTML links to run a customized search on the device. Cybercriminals abuse search-ms to trick victims into downloading malware from a WebDAV server.
It also points to the possible use of compromised Ubiquiti routers as servers for phishing and malware distribution. Recall that at the end of February, federal agencies in the United States and other countries urged users to pay attention to the risks of using Ubiquiti EdgeRouter routers, which can be used to collect credentials, redirect traffic and create phishing pages.
Cybercriminals in their emails pose as organizations from certain countries-Argentina, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the United States. The emails use a combination of genuine publicly available government and non-governmental decoy documents to activate the infection chain. Free hosting providers are used as hosting services, which allows you to prepare payloads for current operations.
The chain of infections ends with the deployment of MASEPIE, OCEANMAP, and STEELHOOK programs designed to steal files, execute arbitrary commands, and steal data from browsers.
The researchers conclude that ITG05 is able to adapt to changing capabilities by providing new infection methodologies and using commercially available infrastructure, while consistently developing malware capabilities.

